One of our analysts recently identified a new Mal.Metrica redirect scam on compromised websites, but one that requires a little bit of effort on the part of the victim. It’s another lesson for web users to be careful what they click on, and to be wary of anything suspicious that pops up in their browser — even if it’s coming from a website that they would otherwise trust.
Please verify that you are a human
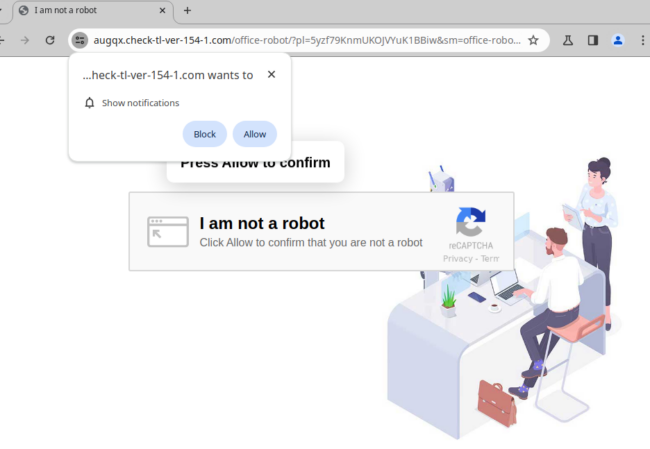
When visiting an infected website we are prompted with a (fake) human verification prompt:
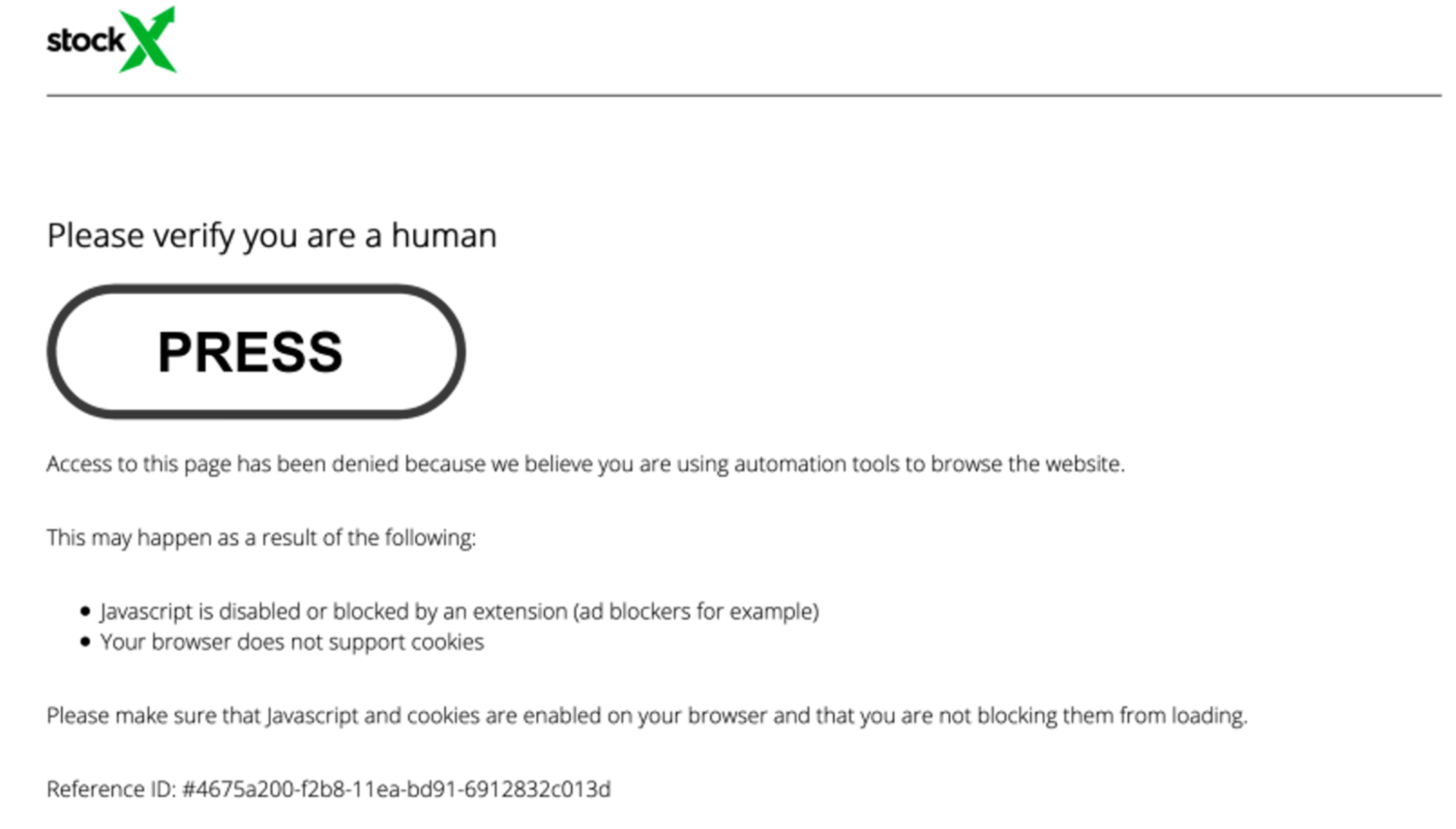
These prompts are quite common on the web these days, and most users would probably not think twice about clicking on it. After all, many of us have long since forgotten how much time has been spent clicking on fire hydrants, buses, and traffic lights in Google CAPTCHA verification prompts to prove that we are human.
While this prompt seems like a routine human-verification check it is actually completely fake — and is instead trying to trick the user into clicking the button thereby initiating a redirect to malicious and scammy websites.
Simple image overlay links to malicious domain
Let’s take a quick look at the backend to see what is displaying this “verification prompt”:
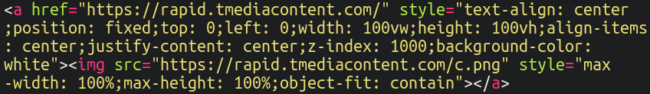
Rather than injecting JavaScript into the website code (which is very common for malware injections), the infection simply creates an image overlay with a link to the malicious domain rapid.tmediacontent[.]com.
Here we can see the redirect chain in the browser developer tools:
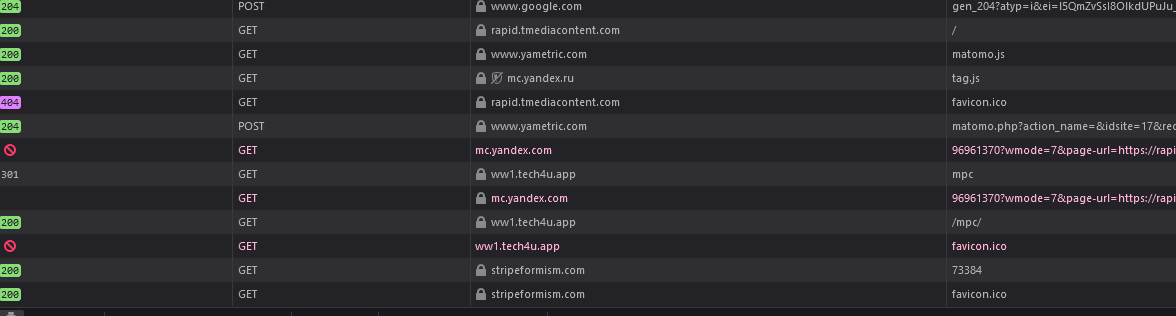
Lodged within the footer-copyright column of the wp_options table, it’s a simple link initiated by clicking on an image loaded from the same domain.
Mal.Metrica domain names
Judging by the domain names, it looks like this is likely a new campaign by the threat actors behind the Mal.Metrica campaign, which are behind quite a few other malicious domains:
content.streamfastcdn[.]com content.gorapidcdn[.]com cdn.metricastats[.]com gll.metricaga[.]com go.syndcloud[.]com cloud.edgerapidcdn[.]com ga.cdzanalytics[.]com syndication.gcdnanalytics[.]com cdn.metricastats[.]com gll.metricaga[.]com synd.edgecdnc[.]com host.gsslcloud[.]com fast.quickcontentnetwork[.]com static.rapidglobalorbit[.]com secure.globalultracdn[.]com metrics.gocloudmaps[.]com cache.cloudswiftcdn[.]com host.cloudsonicwave[.]com secure.gdcstatic[.]com
What is Mal.Metrica?
Mal.Metrica is a massive malware campaign targeting known vulnerabilities in popular WordPress plugins. Similar to Balada Injector, Mal.Metrica takes advantage of recently disclosed vulnerabilities to inject external scripts that utilize domain names resembling some CDN or web analytics services. The malware is known to inject Yandex.Metrica scripts to track performance of their injections.
This group has been actively exploiting vulnerabilities in tagDiv Composer, Popup Builder, WP Go Maps and Beautiful Cookie Consent Banner since at least 2023. We’ve detected this malware on a total of 17,449 compromised websites so far in 2024.
Mal.Metrica’s threat actors were recently identified in PatchStack’s latest State of WordPress security report, which we collaborated on to help pinpoint the relationship between vulnerability exploits and massive malware infections.
Unauthorized injection in vulnerable WordPress theme
The compromised websites which had the bogus link injected into the foot-copyright column were using a vulnerable version of the popular WordPress theme “Responsive”. The vulnerability, identified in March with a CVS rating of 7.5 (high), allows for unauthorised changes of the footer text. This, along with another vulnerability in the theme, was recently patched — which we can observe in the changelog.txt file:
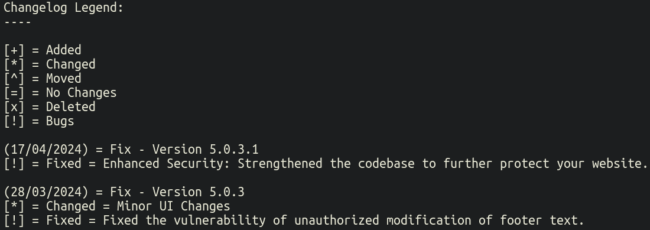
Now that some time has passed since this issue was released, we can observe how attackers have exploited it.
Fake captcha redirects to scam sites
You might remember this friendly character from previous Sign1 malware infections that we have written about on our blog:
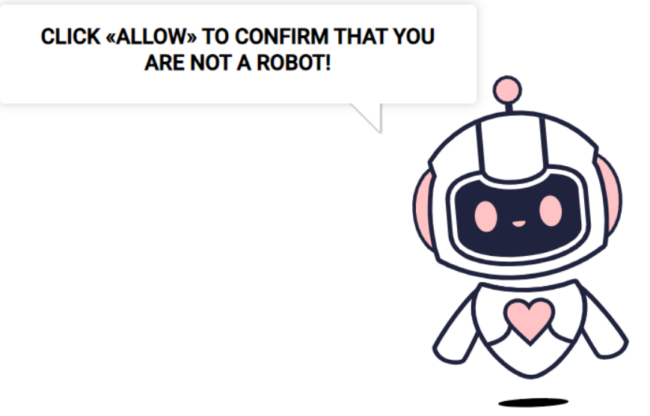
This little guy will pop up on your screen after “verifying” that you are not a robot. Other fake verification prompts may appear too, such as this one here:
These are, of course, fake, and are designed to get you to click on the browser notification prompt, thereby initiating even more redirects to scammy and otherwise undesirable websites which prompt you to download scammy software and fake antivirus programs:
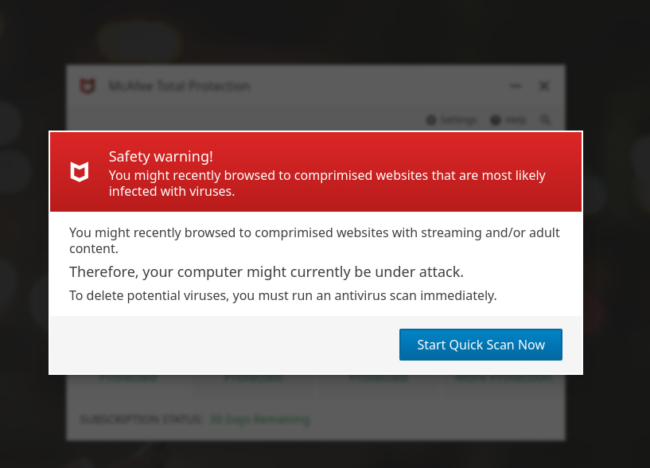
Or enter in personal information:
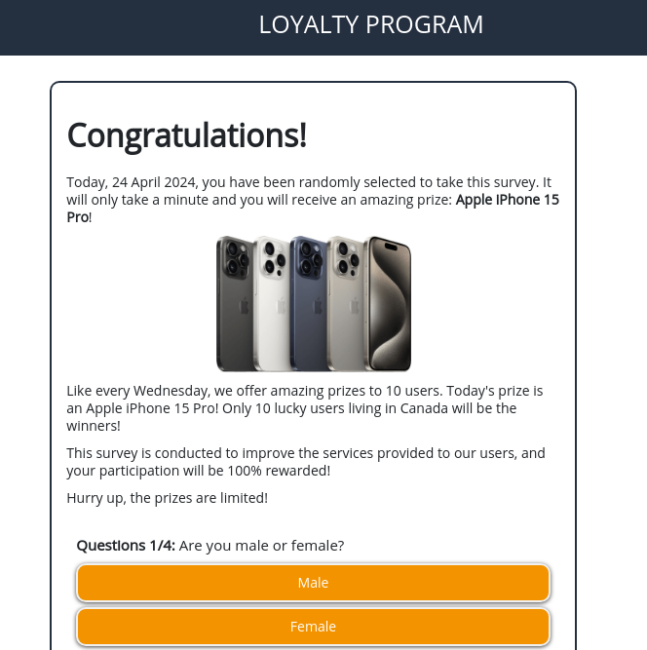
Other attempts at initiating the redirect chain landed us at bogus cryptocurrency online gambling sites:

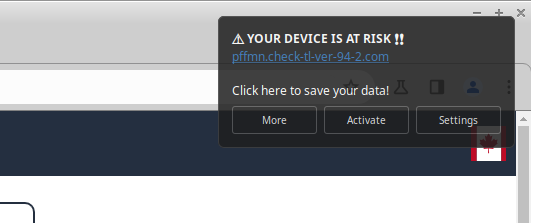
These scammy pop-ups also yield additional browser notifications which send the users to even more bogus websites:
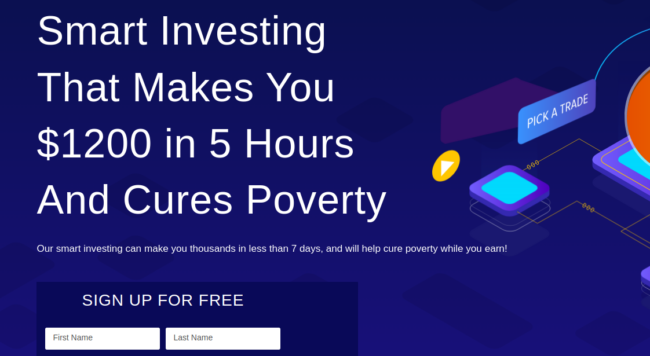
This one here tries to lure users into a “get rich quick” money making scheme with the added benefit of “curing poverty”:
In any event, we could chase these redirects all day and there is really no end to the number of bogus websites that victims could end up at.
Be smart — and patch your software!
There’s a lesson to be learned here for both website administrators and web users alike: Be smart, practice safe browsing habits, and keep your software up to date!
WordPress website owners may want to consider enabling automatic updates for core files, plugins, and themes. And if you’re not able to patch in a timely manner, consider using a web application firewall that can virtually patch your site against known vulnerabilities!
Regular users of the web should also be wary of clicking on links that seem out of place or suspicious, and if you suddenly find yourself at a website that you didn’t intend on visiting, think twice, and exit out of your browser!
If you’ve recently encountered spammy banners or unexpected redirects to scammy domains on your website, we can help. Our experienced security analysts are available 24/7 to help fix hacked websites and clean up infections. Reach out on chat if you need a hand!
Ben Martin is a security analyst and researcher who joined the company in 2013. Ben's main responsibilities include finding new undetected malware, identifying trends in the website security world, and, of course, cleaning websites. His professional experience covers more than a decade of working with infected websites of every variety with a special focus on eCommerce / credit card theft malware. When Ben isn't slaying malware you might find him producing music, gardening, or skateboarding around Victoria.