2022-1-17 19:2:9 Author: lab.wallarm.com(查看原文) 阅读量:23 收藏
Fuzz testing, regularly known as fuzzing, is a product testing procedure that incorporates embedding flawed or arbitrary information (FUZZ) into a product framework to recognize coding issues and security issues. Fuzz testing involves infusing information into a framework utilizing robotized or semi-computerized procedures and investigating the framework for different exemptions, for example, framework crashes or implicit code disappointment.
Brief History
Fuzz testing was created at the University of Wisconsin Madison in 1989 by Professor Barton Miller and some undergraduates. Their (proceeded) discovery can be found at http ://www.cs.wisc.edu/~bart/fuzz/; it’s principally arranged towards order line and UI fuzzing, and shows that cutting edge working frameworks are powerless against even straightforward fuzzing.
What is fuzzing used to test for?
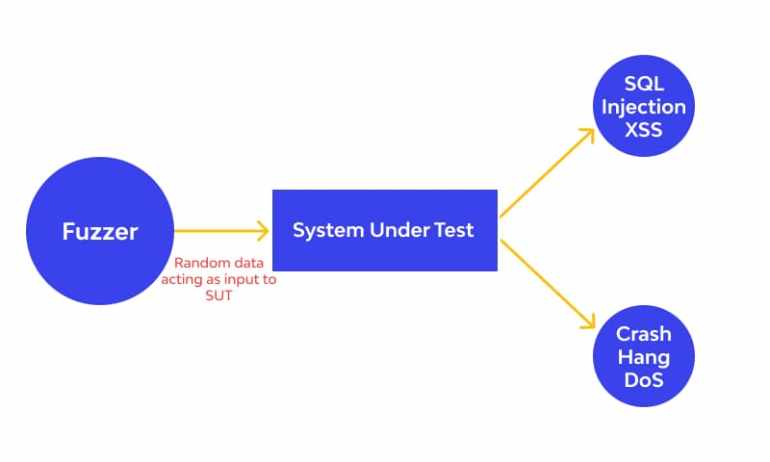
A fuzzer is a program that distinguishes issues by infusing semi-arbitrary information into a program or stack.
Generators are utilized to create information, and troubleshooting devices are utilized to distinguish weaknesses. Blends of static fuzzing vectors (known-to-be-hazardous qualities) or totally arbitrary information are generally utilized by generators. Hereditary calculations are utilized by new age fuzzers to connect infused information to noticed effect. Such instruments are not yet accessible to the overall population.

Types of fuzz testing
A fuzzer would give blends of assaults a shot:
- numbers (marked/unsigned numbers/float… )
- burns (urls, order line inputs)
- metadata : client input text (id3 tag)
- unadulterated binary arrangements
A typical way to deal with fuzzing is to characterize arrangements of “known-to-be-perilous qualities” (fuzz vectors) for each kind, and to infuse them or recombinations.
- for whole numbers: zero, perhaps negative or exceptionally large numbers
- for roasts: got away, interpretable characters/directions (ex: For SQL Requests, quotes/orders… )
- for paired: arbitrary ones
Conventions and record designs infer standards, which are once in a while foggy, extremely convoluted or seriously carried out: that is the reason engineers here and there mess up in the execution interaction (in view of time/cost requirements). That is the reason it tends to be intriguing to adopt the contrary strategy: take a standard, check out every single required component and limitations, and attempt every one of them; illegal/held qualities, connected boundaries, field sizes. That would be conformance trying focused fuzzing.
Application fuzzing
Whatever the fuzzed framework is, the assault vectors are inside it’s I/O. For a work area application:
the UI (testing every one of the buttons successions/text inputs)
the order line choices
the import/send out capacities (see record design fuzzing underneath)
For a web application: urls, structures, client produced content, RPC demands, …
Convention fuzzing
A show fuzzer either gives formed packages to the attempted application or goes about as a middle, changing and replaying sales in a hurry.
Fuzzing the plan of archives
A record plan fuzzer produces a progression of twisted occurrences, which are then opened individually. At the point when a product crashes, investigating information is put away for additional examination.
One can assault:
- report plan goals, structure, shows, field sizes, pennants, and so forth are totally dealt with by the parser layer (holder layer).
- lower-level attacks on the codec/application layer, focusing on the program’s more essential internals
MS04-028 is an illustration of a blemish in the record configuration process (KB833987) A zero assessed comment field with no substance was an imperfection in Microsoft’s JPEG GDI+.
Shockingly, report plan fuzzers are not unreasonably normal, in spite of the fact that they in all actuality do show up rather every now and again of late; a couple of models are accessible:
- Ilja van Sprundel’s mangle.c is a standard record plan fuzzer “Its use is very straightforward; it just requires a filename and headersize as info. It will adjust approximatively somewhere close to 0 and 10% of the header with irregula at that point “”Bits.” (made by the creator)
- http ://sam.zoy.org/zzuf/ – Zzuf can be utilized as a fuzzed record generator. For record plan fuzzer improvement, gadgets like Hachoir could be utilized as a customary parser.
Types of errors detected by Fuzz Testing
Dissatisfactions in statements and memory discharges.
This hypothesis is regularly utilized for huge API security where weaknesses are influencing memory wellbeing, which is a not kidding blemish.
Mistaken data.
Fuzz testing utilizes fuzzers to create mistaken information, which is then used to test planning blunders, which is significant for an item that doesn’t have command over its criticism. Direct fuzzing is a method for mechanizing negative testing.
Rightness bugs.
Fuzzing can likewise be utilized to recognize particular sorts of “exactness” issues. For example, a polluted information base, defenseless rundown things, and many more.

How to do Fuzz Testing?
The strategies for fuzzy testing incorporate all of the vital testing steps:
- Stage 1: Define the objective structure
- Stage 2: Determine the sources of info
- Stage 3: Create fuzzed information
- Stage 4: Run the test with equivocal information.
- Stage 5: Keep an eye on the structure’s exhibition.
- Stage 6: Log deserts
Fuzz testing tools
Web security devices like Burp Suite, Peach Fuzzer, and others can be utilized for fuzz testing also.
Peach Fuzzer.
Peach Fuzzer beats scanners as far as versatility and security. Peach Fuzzer permits clients to observe both known and obscure strings, dissimilar to other testing gadgets that can track down known strings.

Spike in Proxy.
It’s an expert grade device that outputs web applications for application-level issues. SPIKE Proxy contains the essential highlights as a whole, like SQL Injection and cross-site arrangement, yet it depends on an open Python stage. Linux and Windows clients can use SPIKE Proxy.
Webscarab
Webscarab is written in Java to make it more straightforward to use at different levels. The Webscarab framework is utilized to deconstruct the application, which communicates utilizing HTTP and HTTPS conventions.
Webscarab, for instance, capacities as a getting middle of the road, permitting the manager to review and revise demands sent by the program before they are gotten by the server. Permits you to review and refresh the server’s reaction before it is gotten by the program. Thus, in the event that web scarab sees any break statements, it will create a full rundown of the blunders.
WSFuzzer by OWASP
WSFuzzer is a Python-based GPL-authorized application. At present, a program that has been GPL’d is focused on Web Services. HTTP-based SOAP organizations are the essential objective of the current variant of OWASP WSFuzzer.
Advantages and disadvantages of Fuzz Testing
Pros of Fuzz Testing
- Fuzz testing is a stage forward in the improvement of programming security testing.
- Fuzzing bugs are periodically huge and are much of the time utilized by developers, for example, crashes, memory spill, unhandled exception, etc.
- In the event that any of the bugs are missed by the analyzers in light of the fact that to an absence of time or assets, the bugs are likewise found during Fuzz testing.
Cons of Fuzz Testing
- Fuzz testing alone can’t give a total image of a security danger or blemishes.
- Fuzz testing is less viable in identifying security dangers that don’t cause programming disappointments, like contaminations, worms, Trojans, and other malware.
- Fuzz testing can recognize principal defects or dangers.
- It will require some investment to perform well.
Deciding a cutoff regard condition with unpredictable information sources is extremely troublesome, yet most analyzers currently handle this issue by utilizing deterministic calculations in view of customer inputs.
Fuzz testing is a kind of PC programming that decides whether an application is liberated from deserts. Fuzzing doesn’t guarantee that each of a program’s bugs are found. Applying evaluating fuzz testing, then again, guarantees that the product is both strong and protected, as it assists with uncovering most of incessant issues.
Also you can use our free WAF testing tool – GoTestWAF
如有侵权请联系:admin#unsafe.sh