The Qualys Research Team has observed a new version of Chaos ransomware in development. This blog reviews the malware’s updated functionality as well as its ongoing evolution.
A ransomware builder called Chaos is still actively under development. The fourth version has recently been observed being improved, as identified in underground forums as well as code leaks in other community sites.
While the builder bills itself as ransomware, its functions are more like wiper malware. Traditional ransomware is used by attackers to encrypt the victim’s file data and then demand a ransom in exchange for its recovery. In recent years widespread examples of ransomware have dominated the threat landscape – and the news headlines – with one memorable example being DarkSide Ransomware.
Unlike most ransomware, wipers overwrite or remove the data from the victim’s systems. An example of a well-known wiper is Shamoon/DistTrack, which was observed being used to target Industrial Control Systems, steal information, and then destroy the victim’s systems.
In our analysis we have seen Chaos encrypting files of less than 2 MB but overwriting larger files with random bytes. Because of this behavior, we believe it is more accurate to call it a wiper.
A History of Chaos
A Trend Micro provides a summary analysis of the development of Chaos, which was first discovered in June 2021. Since its inception four versions have been observed, the latest iteration in August 2021. Even though it has not yet been used for an actual attack, it could be highly disastrous if used in the future.
The four versions of Chaos described by TrendMicro are:
- Version 1.0; released on 9 June 2021: Replaces file data with random bytes and then encodes it with Base-64. From the outset, it has worming capability, distributing itself to all drives.
- Version 2.0; released on 17 June 2021: Administrative privileges are added, along with the ability to delete all of the shadow copies.
- Version 3.0; released on 5 July 2021: Includes encryption of files with AES/RSA algorithms, but only files with a size less than 1MB.
- Version 4.0; released on 5 August 2021: This latest version has put a limit of 2MB on the files that will be encrypted.
Looking at all these versions, we can infer that Chaos remains an in-development ransomware builder that may soon be offered in an underground market on the Dark Web like other well-known ransomware. There is little doubt that attackers will continue developing its capabilities – potentially based on feedback from other forum members where it is being staged.
Technical Details
In the latest version of Chaos, the new extension given to encrypted/affected files is CRYPTEDPAY, as the screenshot below reveals:

Here is a list of extensions targeted by this malware:

First, it checks for any other instance already in execution. If yes, then the malware will terminate itself.
If not already running, it drops a copy at the below location and then executes itself.
“C:\Users\\AppData\Roaming\svchost.exe”
Next, it terminates the current process.
Then the newly created process (i.e svchost.exe) searches for all the drives present and starts encrypting them. It performs encryption only if the extension of the file is present in the list shown above.
As the screen below illustrates, it then checks the file size. Files are encrypted with AES only if the file size is less than ~2MB. The key used for AES encryption is randomly generated for each file, and the key is then encrypted with RSA.

This RSA-encrypted key is then encoded in Base-64 and kept at the start of the file with the tags
<Encryptedkey>…<Encryptedkey>
followed by the encrypted file data.

If the file size is greater than ~2MB and less than ~200MB, random bytes of the length (filesize/4) are generated and written in the encrypted file in Base-64 encoded format. If the file size is greater than ~200MB, random bytes with the length greater than ~200MB and less than ~300MB are generated and kept in the file in Base-64 format. This makes these files completely useless.
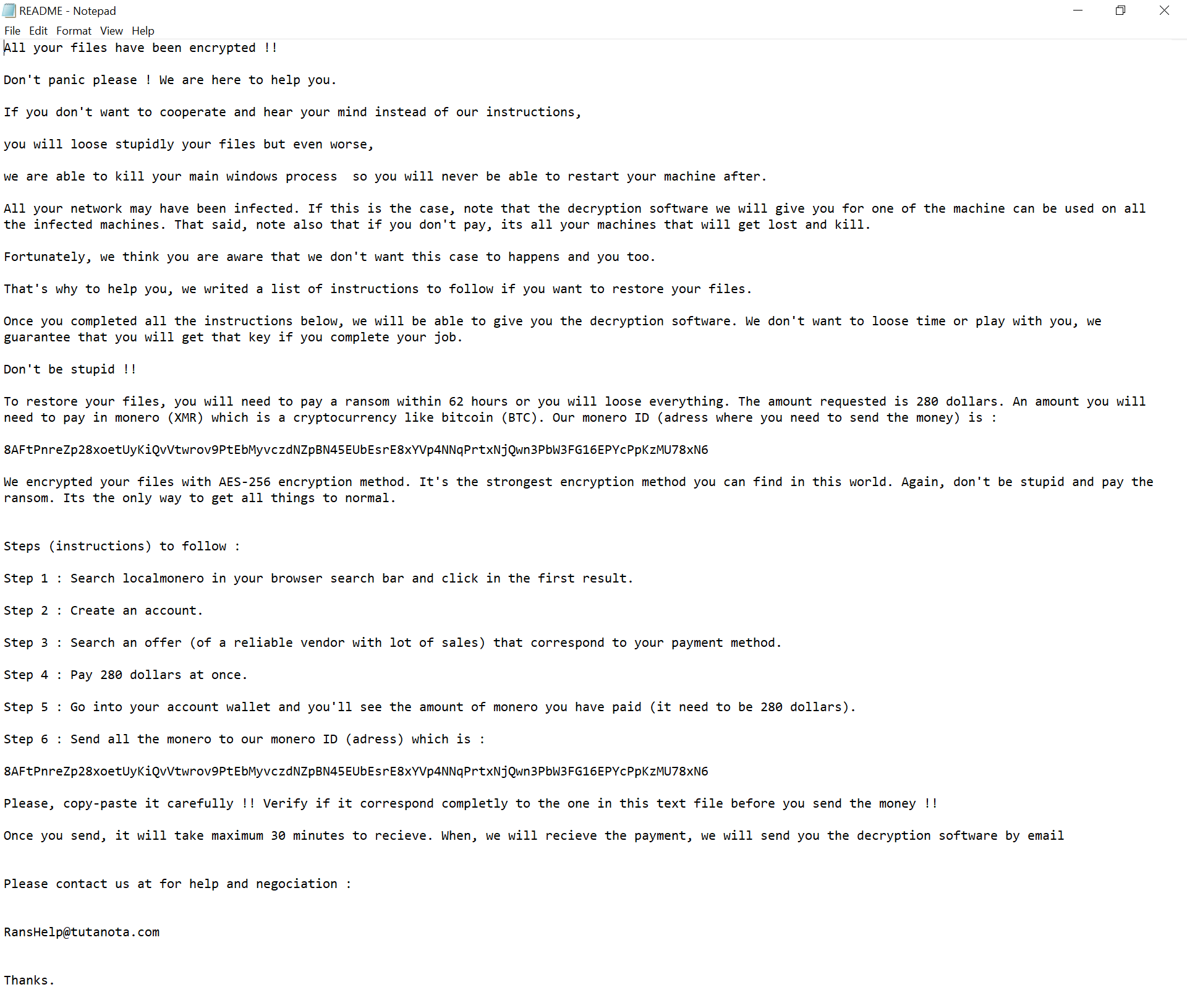
The attacker then has Chaos drop the ransom note, in each encrypted folder as shown in this screenshot:

The victim’s wallpaper is also changed to:

To the victim’s dismay, Chaos takes steps to make recovery impossible by deleting shadow copies, backup catalog, and disabling windows recovery mode by executing the following commands:
“vssadmin delete shadows /all /quiet & wmic shadowcopy delete”
“bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no”
“wbadmin delete catalog -quiet”
Given the rapid and ongoing development of Chaos ransomware’s capabilities, it’s very clear that if this ransomware ever used in cyber-attack, the victims may not be able to recover their important data. Security professionals must take the utmost precaution to protect their organizations from such destructive attackers.
TTP Map:
| Discovery | Collection | Impact |
|---|---|---|
| File and Directory Discovery (T1083) | Data from Local System (T1005) | Data Encrypted for impact (T1486) |
Mitigation or Additional Important Safety Measures:
Network
- Keep strong and unique passwords for login accounts.
- Disable RDP if not used. If required change the RDP port to a non-standard port.
- Configure firewall in the following way,
- Deny access to External IPs trying to connect important ports (in this case RDP port 3389)
- Allow access to only IPs which are under your control.
- Use VPN to access the network, instead of exposing RDP to the Internet. Possibility to implement Two Factor Authentication (2FA).
- Set lockout policy which hinders credentials guessing.
- Create a separate network folder for each user when managing access to shared network folders.
Take regular data backup
- Protect systems from ransomware by periodically backing up important files regularly and keep a recent backup copy offline. Encrypt your backup.
- If your computer gets infected with ransomware, your files can be restored from the offline backup once the malware has been removed.
- Always use a combination of online and offline backup.
- Do not keep offline backups connected to your system as this data could be encrypted when ransomware strike.
Keep software updated
- Always keep your security software (antivirus, firewall, etc.) up to date to protect your computer from new variants of malware.
- Regularly patch and update applications, software, and operating systems to address any exploitable software vulnerabilities.
- Do not download cracked/pirated software as they risk backdoor entry for malware into your computer.
- Avoid downloading software from untrusted P2P or torrent sites. In most cases, they are malicious software.
Having minimum required privileges
Do not assign Administrator privileges to users. Most importantly, do not stay logged in as an administrator unless it is strictly necessary. Also, avoid browsing, opening documents, or other regular work activities while logged in as an administrator.
Indicators of Compromise (IOCs)
1ba5ab55b7212ba92a9402677e30e45f12d98a98f78cdcf5864a67d6c264d053 b103fc649787eb1f6121df8174d0f16aaac736fb53f5f078d312871189285956 17557537bcb33f2a0ad3ff0caf7b084e63468144b2e6cb8180f6598adfdc5c9a 17557537bcb33f2a0ad3ff0caf7b084e63468144b2e6cb8180f6598adfdc5c9a
Contributor
Ganesh Vetal, Senior Threat Research Engineer, Qualys