Introduction
Are you an organization that manages or hosts a huge pool of resources on remote locations/servers? Well, host-based authority-validation technique is the most-suited way to manage the access and control rights related to your hardware and applications. Once implemented, this identity verification method applies to all the users.
Do not know much about this method? No worries. Detailed insights about the host-based process are provided the next.
A Quick Glimpse of Host-Based Authentication
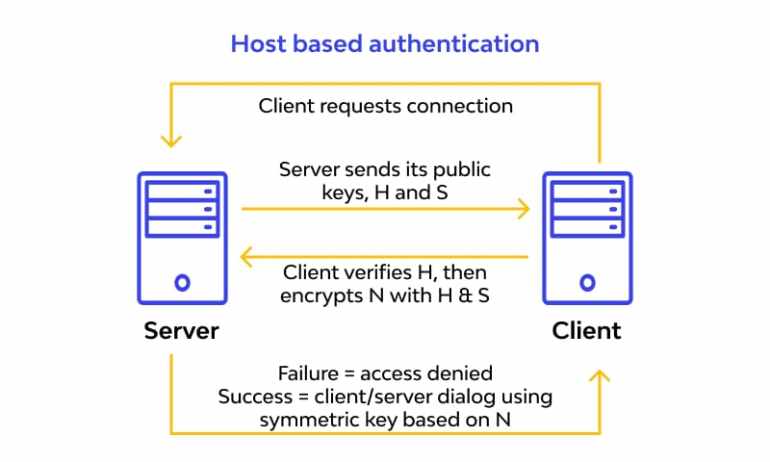
By definition, it refers to the default validation method of a single host or server preventing other users to go for checking the individual details.
One host can initiate and finish the identity-verification process requirements on the behalf of a few or all of the hosts. Once it’s done, the rest of the server users won’t need any key or other proofs to get authorized for utilizing a resource.
The host accounts to be verified in this process could be built either on a system or on the Match directive-driven subsets.
Most commonly, this mode of checking access rights is used where there are extensive clusters of computing resources.
A few host-based type identity-verification method details are:
- Occurs on both the client and server-side.
- Could be called a close native of Rhosts RSA method. Administrators can set its configuration for locally hosted clients.
- You need to specify if the process will allow public-key authentication usage for it. By default, the answer is set as ‘no’.
- When it’s taking place on the client, two files (in the etc/ssh/ location), ssh_known_hosts and ssh_config, should be prepared to complete the process.
- When it is for the server-side, besides the above 2 files, the etc/shosts.equiv file must also be properly prepared.

Comparing the Authentication Methods – Host Vs. Public key Based
These two methods mainly differ on one front, which is – their method of configuring. The major differences are as listed as under:
| Host Based | Public Key Based |
| It is for every user, unless a restriction is imposed | Individual public-private key pair is created for every user |
| Initiates at its default layer, i.e. the host layer. | Works at the user layer, as specified in its default settings. |
| Public key is duplicated using ssh-keyscan | Public key is duplicated using ssh-copy-id |
| The key storage location: Private – ~/.ssh Public – /etc/ssh/ssh. |
The key storage location: Private – /etc/ssh Public – authorized_keys file |
| /etc/ssh holds the public-private key pair | ssh-keygen generates the pair of keys in this scenario |
| ssh-keysign is used for fetching Local host key data | Public-private key combination is used |
So, that’s all about differences between these 2 famous techniques of verifying users’ identity. However, if keeping the above-mentioned differences aside, these two authentication processes have few resemblances too. For instance, both can use the public-private keys combination for added safety of connections.
SSH host-based Authentication
SSH is an approvingly famed protocol meant for securing the machines in remote environments and for hybrid networks. Designed for the client-server model, it features three layers for carrying out its process:
-
- Transport Layer – It is accountable for data compression as well as caching. It takes care of safe data transactions between clients and servers.
- The connection layer – The one, liable for taking forward the information exchange or ‘talks’ after the validation of identity/rights.
- Authentication – Client’s trustworthiness is ensured on this layer.
SSH protocol is used broadly as it proffers various authentication approaches, backed by potent encryption. Owing to its ability to preserve the data integrity throughout the process, this protocol is considered as the apt alternative to customary and less protected login protocols and file transfer procedures like telnet and FTP.
Along with creating a safe ecosystem for remote resources to communicate, SSH is responsible for other tasks like performing port forwarding and working as a proxy server, when the situation demands so.
The most customary use of SSH is in data centers wherein it handles the job of securing all kins of remote access rights.
The simple functionality and the plentiful security implications has made SSH a good choice for barricading remote hosts, mirroring files via SFTP, tunneling of data, etc. for the Windows environment.
Understanding SSH from the Security Viewpoint
While one thinks of implementing the SSH protocol, understanding its security aspects is crucial. Gladly, this protocol is amazingly safe on the cybersecurity front. However, the increased API security risks and vulnerabilities compelled SSH users to remain a bit more aware of implementing adequate security strategies.
In their absence, SSH servers are prone to Brute Force attacks. In this type of attacker, threat actors use common login input pairs to target the large SSH server pools. Once they gain access, they are allowed to enjoy admin-like control over root accounts and can consume the resources.
Another problem is, organizations or employees miss out the fact that SSH keys should be managed properly and kept carefully. If not saved and managed in secure ecosystems, bad actors can use these kyes and exploit the remote resource.
Lastly, we have exposed SSH ports as a major security concern. Some notorious malware can attack devices using exposed SSH ports and consume the resources or corrupt the system.
The above dangers force SSH protocol clients to adopt robust and viable security deployments.
Host-based authentication is a commonly used verifying SSH processes.
SSH users are guided to utilize authentication keys before connecting with remote servers. Also, only the permitted hosts must be connecting in this case.

How to Implement SSH?
To begin implementing host-based authentication on SSH, one has to start with creating specific configuration. Both the server and the client-side machines would be part of this configuration alteration.
The needed configuration on the client-side is editing the /etc/ssh/sshd_config file. The lines to enter here are:
- HostbasedAuthentication yes
- EnableSSHKeySign yes
To enable the authentication method on the server-side, three files should be modified. These files (in the Folder etc > ssh) are:
- shosts.equiv
- ssh_known_hosts
- sshd_config
In the sshd_config file, one has to do the following:
- Add the value for HostbasedAuthentication as ‘yes’
- Add the value for IgnoreRhosts as ‘no’
After adding these two lines, the next step is adding the hostname of the client PC in the shosts.equiv file. The file is server-hosted.
The Final Word
Keeping the focus on the host, host-based method for authentication is here to make machinery and computing devices cluster management easier than ever. Hope this article has helped you understand this authentication method thoroughly.
如有侵权请联系:admin#unsafe.sh