What are DDOS attack tools?
DDOS attacks are cyber- attacks targeted at rendering certain computers, network systems and servers non-functional. The processes involved in its execution can be however complicated. Attackers have to carry out a long series of actions that involve social engineering, data breaches and sometimes even system testing. Due to the sophistication of these activities, tools have been developed to facilitate DDOS attacks for pen testers. Although, it is kind of two sided, DDOS attacks tools are important for system admin and pen testers to use. It helps them carry out faster attacks to determine the strength of their server or framework security. On the other hand, hackers can also use these tools to execute their own attacks. In fact, DDOS tools are primarily used by cyber attackers against very complex security frameworks.
These tools make them more intense, efficient and less time consuming than more manual approaches. There are different types of the tools and each has its own level of sophistication. Depending on the kind of DDOS in question, these tools come in pretty handy to speed up the process of the attacks. As system administrators and ethical hackers, it is an added advantage if you are aware of these tools and the way to use them. It gives you an insight into what to take precautions against in your security framework.
Why DDOS attacks dangerous?
To understand the threats DDOS tools may pose to you, you may need a good grasp on what the possible effects of DDOS attack on any framework, server or computer.
-
- THEY COULD COST THE COMPANY SENSITIVE CUSTOMER INFORMATION – Depending on the sort of attack perpetrated. Attackers may have access to the company database and steal sensitive customer information. This places the company on a spot, they automatically lose customer trust and support and it is very bad for brand reputation. This also affects sales and business health, since they are directly connected to what customers think of the business.
- THESE ATTACKS TRIGGER AN INACTIVTY TIME – Successful attacks cause the website or the servers to suffer a downtime. During this period of inactivity, depending on the scale of the company, the effect of that inactivity time may be catastrophic. Consider for instance, financial institutions. When organizations like this experience such attacks, they cause a great deal of loss to the institution and to the customer base.
- THE COST OF REPAIR IN CASH AND DATA IS USUALLY LARGE – Depending on the extent of the attack, the cost of repair in cash could actually make some organizations go bankrupt. Aside the amount of money lost during the period of inactivity, re-routing a server or rebuilding a non-functional framework is usually cost intensive.
What are the best DDOS attack tools in 2022?
There are different types of these tools available. Let’s check out the best 16. This list is based on a couple of criteria that include efficiency, speed and attack sophistication.
LOIC
LOIC – This attack tool is fully called Low orbit icon. It happens to be very useful in DDOS attacks that use large volumes to their advantage. Simply put, it focuses the network connections of computers towards specific server frameworks. Since under normal circumstances, no computer can send requests powerful enough to overwhelm server bandwidths, they prompt computer networks to send unnecessary packets to the servers that have been preselected.
HOIC
HOIC – Of course, they are certain limitations to the functions of LOIC in terms of volume. For more refined attacks and for more bulk, hackers created the high orbit icon to replace LOICs. What this means is that, HOICs can generate more requests at whim more than LOICs can. This makes it easy to execute large scale volume based attacks in a lesser time. HOICs are known to be able to generate as high as 250 garbage packets and send them as requests to servers. Just as mentioned earlier, attacks with this tool does not generate more bulk, those attacks become harder to detect with increasing sophistication. Essentially, some firewall systems (especially the traditional ones), would not be able to filter out these attacks.
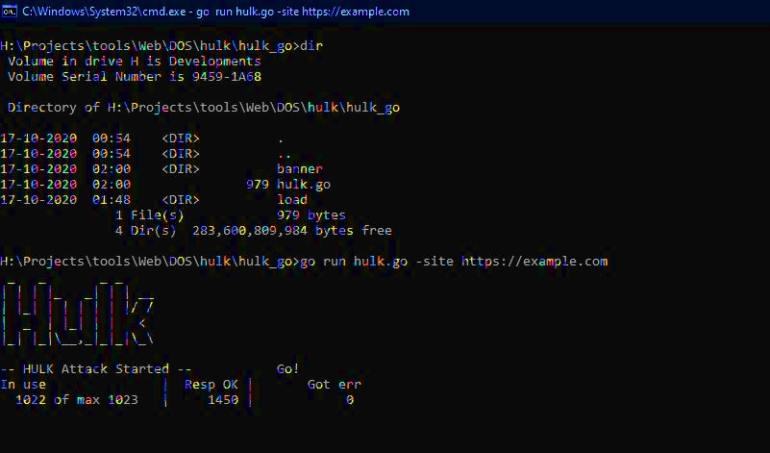
HULK
HULK – This is like an acronym for HTTP unbearable load king. In this age where transfer protocols are the conventional means through which computer communicate with servers, it would be smooth for attacks to overload servers with many of such apparently legitimate requests. That is exactly what HULK does. They happen to be very efficient in executing denial attacks. Finally, these tools can be used to generate attacks that can be quite difficult (and sometimes) to detect. Of course, that is to be expected since the vehicle of execution is HTTP.

Solarwinds security management system
SOLARWINDS SECURITY MANAGEMENT SYSTEM – Unlike all other tools on the list that help you test by initiating attacks, these systems are directly involved in protection. Instead of relying solely on your local firewalls and conventional IP filters, you could use this system to monitor traffic flow and mitigate the said attacks. The system works by creating logs from requests, strengthening the logs records to create some sort of filter algorithm, constantly review the requests to a server and block off requests when it detects an alteration. This system is capable of sending emergency alerts when it discovers garbage traffic, block off the requests and stabilize traffic flow to servers. For the purpose of security, the server log in a read only format.
PyLoris
PYLORIS – This tool type is very effective for carrying out for stealth DDOS attacks. It is another tool that is used for pen-testing by executing slow and hidden attacks. It is used to execute denial attacks directly against the service. It takes advantage of certain server communications frameworks that use encryption and anonymity. Notable among these are SSL and SOCK proxies. It uses these means to popular server protocols like HTTP, UDP and so on.

Tors hammer
TORS HAMMER – Just as the name suggests, it is an attack that takes advantage of the Tor network. However, instead of a crushing action like the literal Thor hammer, it is specialized for anonymous attacks. The tool is built in a way that uses anonymity as a leverage to evade firewalls and security mitigations. It is also used to carry out demo attacks on security structures by pen testers. There is a downside to this tool however; the primary network (Tor) is usually very slow. This speed limit automatically limits how effective these tools can be.

SLOWLORIS
SLOWLORIS – This tool is one of the best ways to carry out DDOS attacks. It is even dubbed the most effective of the tools available. It works by sending out legitimate HTTP requests albeit incompletely. That way, with a limited bandwidth, it gets the server overburdened with requests. Also, this tool allows attackers create a connection with the victim server and keep these connections open for as long as they are needed. The server are left anticipating several uncompleted HTTP requests, hence they have limited or no space to attend to the users. It is especially effective because the HTTP requests are not spoofed, they are legitimate.
DDOSIM
DDOSIM – This tool is used predominantly to carry out application layer DDOS attacks against targeted servers in a simulation. This tool creates several non-existent hosts and uses them to execute layer 7 attacks against these servers. The strength of the server security framework is evaluated upon the response to this attack. Although, the tool is adapted to function on other operating systems, it is written using C ++ and it functions optimally on LINUX. It works in a way that it carries out different methods of attacks, to show the diversity of approach and the vastness of a hacker’s thought process.
RUDY
RUDY – This stands for R U Dead Yet? It uses long forms to overwhelm servers in a slow and coordinated stream of denial attack. RUDY is used in some conjunction with some other tools. First, servers with web forms embedded in them are sourced out. When these servers are found and the forms have been noted, the RUDY attack tool is used to send hypertext transfer protocol requests with extremely long content.
PRTG
PRTG – This is tool that is not directly involved in carrying out attacks. It could however be useful in mitigating DDOS attacks through its operation. PRTG is the synonym for Paessler router Traffic grapher. It is used to as a stat tool to gauge server traffic, the extent of bandwidth usage and to send notification in the case of any detected abnormality in these activities. Just as the name imply, it is a monitoring tool that could give the user access to the state of the components of your network or your server or computer. It has an easy to use interface and it can function on pretty much any type of operating (OS). It is especially effective in volume based denial attacks
OWAS DDOS HTTP POST
OWAS DDOS HTTP POST – This tool can be used to examine how stable the security of your web application would be against popular DDOS forms like Slowloris attacks and SLL renegotiations. It is very effective as a simulator against website applications and in actual attack depending on who uses it.
DAVOSET
DAVOSET – This tool is used to execute attacks on websites by gaining access through other sites. This method of attack has gained notoriety over time in the hacking space. The structures exploited in this context are often used in website to website interaction. It leverages on the loopholes of XML external entities among other structures.
APACHE BENCHMARK TOOL
APACHE BENCHMARK TOOL – Just as the name implies, it serves as a benchmark for servers (particularly HTTP servers). It is a tool that can be used to send out http requests to many servers at the same time. This makes it easily adaptable for Distributed attacks from a single source.
HYENAE
HYENAE – This is also another attack simulation tool. However, it is known to be very versatile and ubiquitous. It could be used to perform different types of DDOS attacks in a simulated environment. This often makes it the ideal tool for carrying out Pen tests

GOLDEN EYE
GOLDEN EYE – This is another tool designed specifically for simulations. It can be used to put the servers in different situations of attempted distributed denial of service. The tester then observes the method of security system’s response and how to fix the loopholes that present themselves. This tool is designed specifically for servers. It is written for servers as a test tool, but hackers have been able to take advantage and can use it in large scale DDOS attacks.

HPING 3
HPING 3 – This tool can send pretty much any type of protocol packets out to targeted servers. It is even effective in executing a three way server network response attack. It is especially known for showing the response of the targets to an attack situation. Therefore, it would be brilliant for simulations too.

Conclusion
These tools are selected as the top 16 based on their functionality and how popular they are among hackers. There are other tools out there that are dangerous and would be effective in carrying out simulations. As cyber-security personnel, it is beneficial that you know as much of these tools as possible to forestall attacks against your framework security.
如有侵权请联系:admin#unsafe.sh