2022-1-31 15:5:47 Author: lab.wallarm.com(查看原文) 阅读量:26 收藏
What is a penetration tester?
In the realm of data security, pentesters are the specialists. The reason, likewise with other PI works out, is to recognize hazards before any potential meddling bosses get an opportunity to set up their framework.
Helpless entertainers will endeavor to take advantage of gives up unendingly, which is one of the more huge certifiable components of human drive as a general rule, and set up data structures specifically. Pen analyzers, similar to web programs, search for deficiencies in wired and far off coalition designs to obliterate, reveal, and help repair them.
How much does a penetration tester make?
A penetration tester salary somewhere in the range of $64,000 and $133,000 each year, as per glassdoor.com, with a normal yearly compensation of $82,500. Rewards, commissions, and benefit sharing complete around $17,000 each year by and large.
| New York | Los Angeles | Chicago | Houston | Phoenix |
|---|---|---|---|---|
| $99,907/yr | $95,346/yr | $86,253/yr | $78,919/yr | $87,246/yr |
What does a penetration tester do?
Oftentimes, the terms weakness testing and intrusion testing are mixed. These two association security specialties, in any case, have immense separations. Inadequacy analyzers search for imperfections and issues during the course of action and plan seasons of a security program. Intrusion analyzers look at live constructions for flaws and deficiencies.
Cyberattacks and other security breaks are imitated by attack testing social occasions to gain authorization to delicate, private, or prohibitive data. They join existing hacking contraptions and frameworks with their own appearances. Pen analyzers document their activities by and large through an imitated assault to give genuine reports portraying how they figured out some method for getting around set up security structures.
Intrusion testing bundles help their relationship in keeping away from the negative transparency and loss of customer invest that go with guaranteed hacks and cyberattacks. They besides help tries and relationship in dealing with their robotized security.
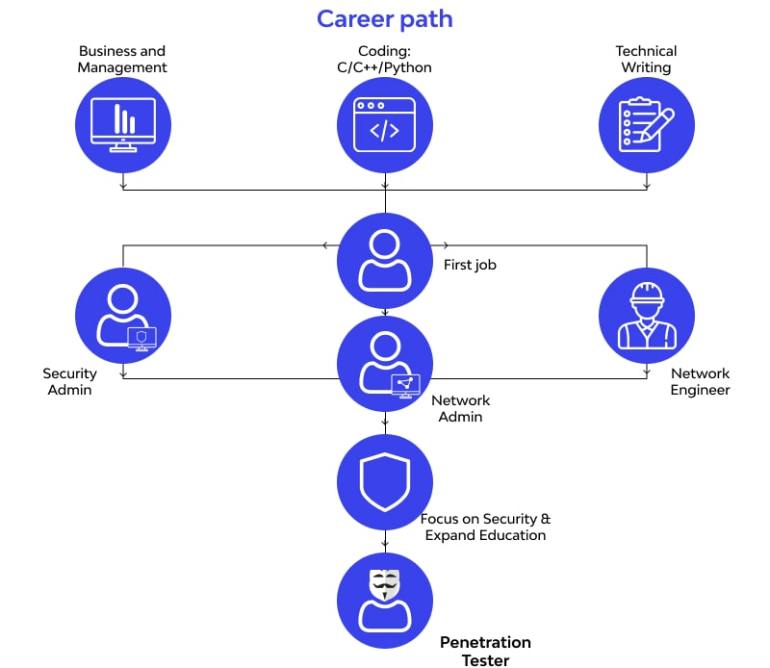
How to become a penetration tester?
- Get educated
Pursuing a specific course or planning program is maybe the best methodology to begin getting the limits you’ll need as an entry analyzer. You can learn in a more coordinated climate while simultaneously making different gifts with these sorts of undertakings.
Ponder the IBM Cybersecurity Analyst Professional Certificate if you’re new to online assurance. It covers a whole unit on entrance testing and event response. The entire program is done totally on the web and at your own speed, allowing you to cultivate occupation arranged capacities while working or rearranging various responsibilities.
- Get Certificates
Accreditations in network security show spotters and utilizing heads that you have the limits expected to win in the field. You can in like manner get affirmed in invasion testing or moral hacking regardless these more far-reaching network security abilities. Contemplate the going with reliable attestations:
- Moral Hacker Certification (CEH)
- PenTest+ by CompTIA
- Entrance Tester for GIAC (GPEN)
- Web Application Penetration Tester by GIAC (GWAPT)
- Insisted Professional in Offensive Security (OSCP)
- Entrance Tester Certification (CPT)
Completing a test is commonly expected to obtain one of these capabilities. Planning for an affirmation test can regularly assist you with growing your range of abilities as well as acquiring an endorsement for your resume where you can tag yourself a certified penetration tester.
- Develop skills
To test for weaknesses, entrance analyzers should have an exhaustive comprehension of data innovation (IT) and security frameworks. Here are a few penetration tester skills:
- API security
- Programming dialects, especially prearranging dialects (Python, BASH, Java, Ruby, Perl)
- Threat modeling
- Conditions like Linux, Windows, and MacOS
- Devices for evaluating security
- Stages for pentest the executives
- Specialized documentation and composing
- Cryptography
- Distributed computing engineering
- Advancements for remote access

- Practice more
Various associations are looking for pentesters with related information. There are a combination of decisions for getting inclination outside of the work space. Dynamic testing in reenacted conditions is significant for some, pen testing getting ready projects.
Partaking in bug overflow programs is another technique to get understanding (and make your resume stick out). Associations typically pay monetary prizes to free pen analyzers and security researchers who find and report security openings or bugs in their code as a component of these undertakings. It’s an extraordinary technique for examining your capacities and meet other security trained professionals. On objections like Bugcrowd and HackerOne, you may find an overview of compensations.
Finally, there are different locales that license invasion analyzers to practice and explore legitimately through gamified experiences.
- Start working as an entry-level specialist
Numerous section inspectors start their vocations in lower-level IT and web security positions prior to climbing to pen testing. Start by accepting the job of an association or structures supervisor or an information security specialist to acquire insight with pen testing. You can also apply for remote penetration tester jobs.
Penetration tester Responsibilities
Pen analyzers work on organizations, frameworks, and electronic applications to attempt danger displaying, security evaluations, and moral hacking. Affirmation approval, specifically, involves some or the accompanying assignments as a whole:
- To find data divulgences, accumulate and assess Open-Source Intelligence (OSINT).
- Give topic aptitude in hostile security testing activities, assisting with testing an association’s defensive measures.
- Direct assessments on a wide scope of innovations and executions utilizing both robotized and human techniques.
- To further develop testing techniques, make contents, devices, and strategies.
- Support with the perusing of expected commitment, just as driving commitment from the start as far as possible.
- Practices in friendly designing and actual infiltration testing ought to be completed.
- Analyze both wired and remote organizations for security defects.
- Break down evaluation results to find discoveries and make an all-encompassing insightful perspective on the framework comparable to its environmental elements.
- Decide the wellspring of both specialized and non-specialized issues.
- Distribute an Assessment Report that subtleties the discoveries and proposes possible arrangements.
- Monitor discoveries that show up in a few evaluations and talk about them.
- Impart the system utilized, discoveries, and investigations when the evaluations are finished.
- Give specialized help to ISOs in settling appraisal issues.
- To help with exhaustive episode taking care of and criminological examination of compromised frameworks, offer specialized help in network abuse and avoidance methodologies.
Requirements for the penetration tester
Get ready and Execute Penetration Tests: Penetration analyzers should devise investigations and reproductions to assess the viability of existing safety efforts.
Execute Tests and Other Simulations: After arranging and making appraisals, entrance testing groups perform examinations and report their discoveries.
Infiltration testing groups plan reports to convey to their managers and other significant chiefs in the association.
These reports might use lay or specialized language, contingent upon the target group.
Senior individuals from infiltration testing groups oftentimes discuss straightforwardly with the board level staff, portraying the degree of peril brought about by explicit weaknesses and offering exhort on the most proficient method to address them.
Coordinated effort with Other Employees to Improve Organizational Cybersecurity: Penetration analyzers work together with other network safety and IT specialists to teach representatives on the best way to work on the association’s online protection.

Penetration tester certificates
Accreditations can affect infiltration analyzers’ compensation and progression in their professions. Confirmation programs for infiltration analyzers are presented from an assortment of sources. Here are some:
- The EC-Council Certified Ethical Hacker (CEH) confirmation covers a wide scope of assault innovations, security regions, and cracking through devices.
- Individuals at the expert level can take the EC-Council Licensed Penetration Tester (LPT) Master test, which assesses their ability to oversee genuine conditions.
- The IACRB Certified Penetration-Tester (CPT) affirmation bases on explicit invasion testing data and capacities in districts including network show assaults and online application shortcomings.
- The IACRB Certified Expert PenTester (CEPT) program is for people who have ace level invasion testing capacities and covers everything from memory debasement to Windows shellcode.
- WAF and adaptable working structures are the subject of the IACRB Certified Mobile and Web App Penetration Tester (CMWAPT).
- The Certified Red Team Operations Professional (CRTOP) is an IACRB-insisted intrusion analyzer who tends to broad master in immense degree, all around entrance testing.
- CompTIA PenTest+ bases on the top tier attack testing test and evaluation limits.
- The GIAC Global Information Assurance Certification (GIAC) Penetration Tester (GPEN) program bases on attack testing best practices and legitimate issues.
- GXPN (GIAC Exploit Researcher and Advanced Penetration Tester) revolves around best in class intrusion testing strategies and the relationship between security issues and business possibilities.
- The Offensive Security Certified Professional (OSCP) is a really powerful, expansive approval acquired by going through a real 24-hour situation.
Benefits of working as a penetration tester
- Every single day is remarkable.
While this could be said to depict all things considered, each work, as an entry testing educated authority, reliably is interesting. Consistently practices fuse hacking (clearly!), making reports, visiting gatherings, giving educational talks, getting additional planning, chatting with past clients, and so forth.
- Each attempt has its own arrangement of obstructions to win.
Each venture is a novel riddle all by itself. You can secure information en route that you should at long last fit together to settle the conundrum.
- The field of data security.
The universe of data security is not normal for some other. There are many individuals that are truly keen on helping other people, organizing, and cooperating.
- An unmistakable inclination of direction and a longing to serve others.
I’ve worked in an assortment of fields, including money, and I really accept that the work I do at an infiltration testing firm has an effect.
如有侵权请联系:admin#unsafe.sh