Figures of the year
In 2021:
- 56% of e-mails were spam
- 77% of spam was sent from Russia with another 14.12% from Germany
- Our Mail Anti-Virus blocked 148 173 261 malicious attachments sent in e-mails
- The most common malware family found in attachments were Agensla Trojans
- Our Anti-Phishing system blocked 253 365 212 phishing links
- Safe Messaging blocked 341 954 attempts to follow phishing links in messengers
Trends of the year
How to make an unprofitable investment with no return
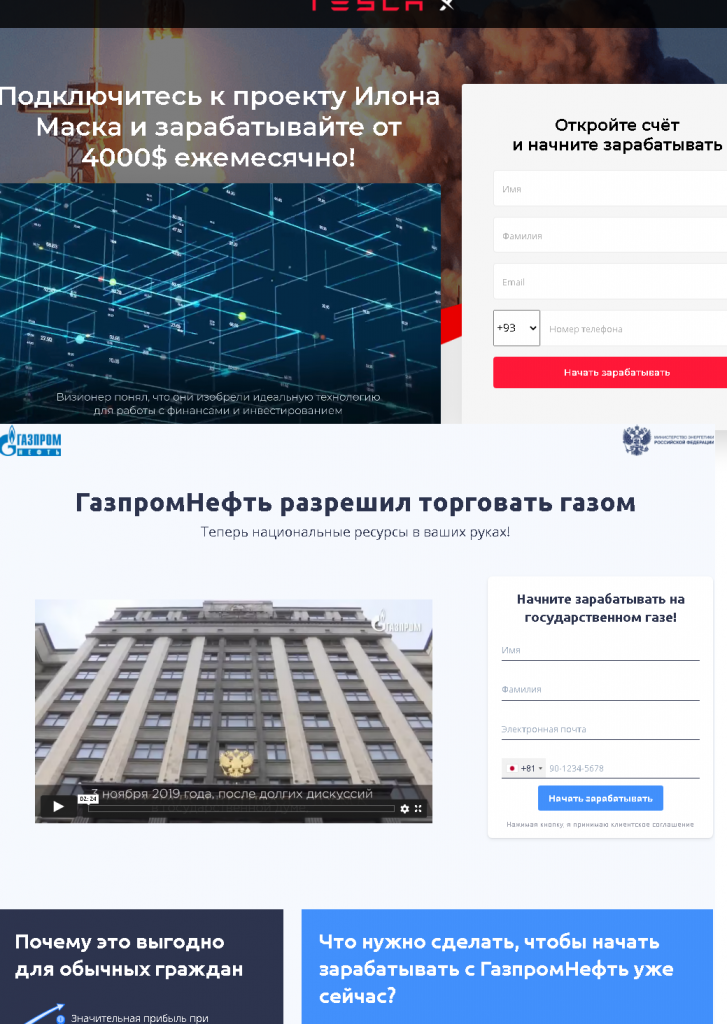
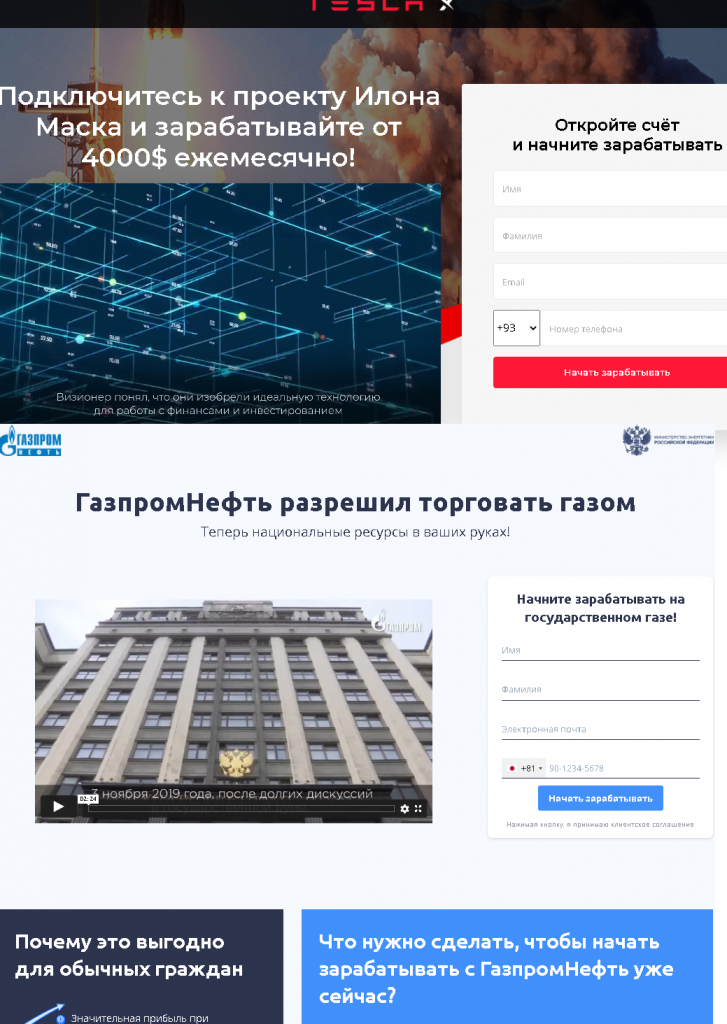
The subject of investments gained significant relevance in 2021, with banks and other organizations actively promoting investment and brokerage accounts. Cybercriminals wanted in on this trend and tried to make their “investment projects” look as alluring as possible. Scammers used the names of successful individuals and well-known companies to attract attention and gain the trust of investors. That’s how cybercriminals posing as Elon Musk or the Russian oil and gas company Gazprom Neft tricked Russian-speaking victims into parting with small sums of money in the hope of landing a pot of gold later. In some cases, they’d invite the “customer” to have a consultation with a specialist in order to come across as legit. The outcome would still be the same: the investor would receive nothing in return for giving their money to the scammers.
Similar schemes targeting English speakers were also intensively deployed online. Scammers encouraged investment in both abstract securities and more clearly outlined projects, such as oil production. In both cases, victims received nothing in return for their money.
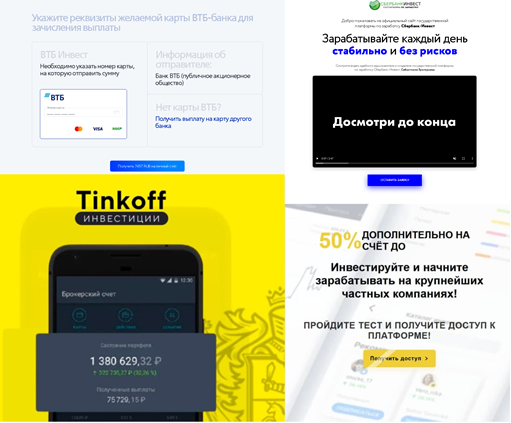
Another trick was to pose as a major bank and invite victims to participate in investment projects. In some instances, scammers emphasized stability and the lack of risk involved for the investor, as well as the status of the company they were posing as. In order to make sure the investors didn’t think the process sounded too good to be true, victims were invited to take an online test or fill out an application form which would ostensibly take some time to be “processed”.
Films and events “streamed” on fake sites: not seeing is believing!
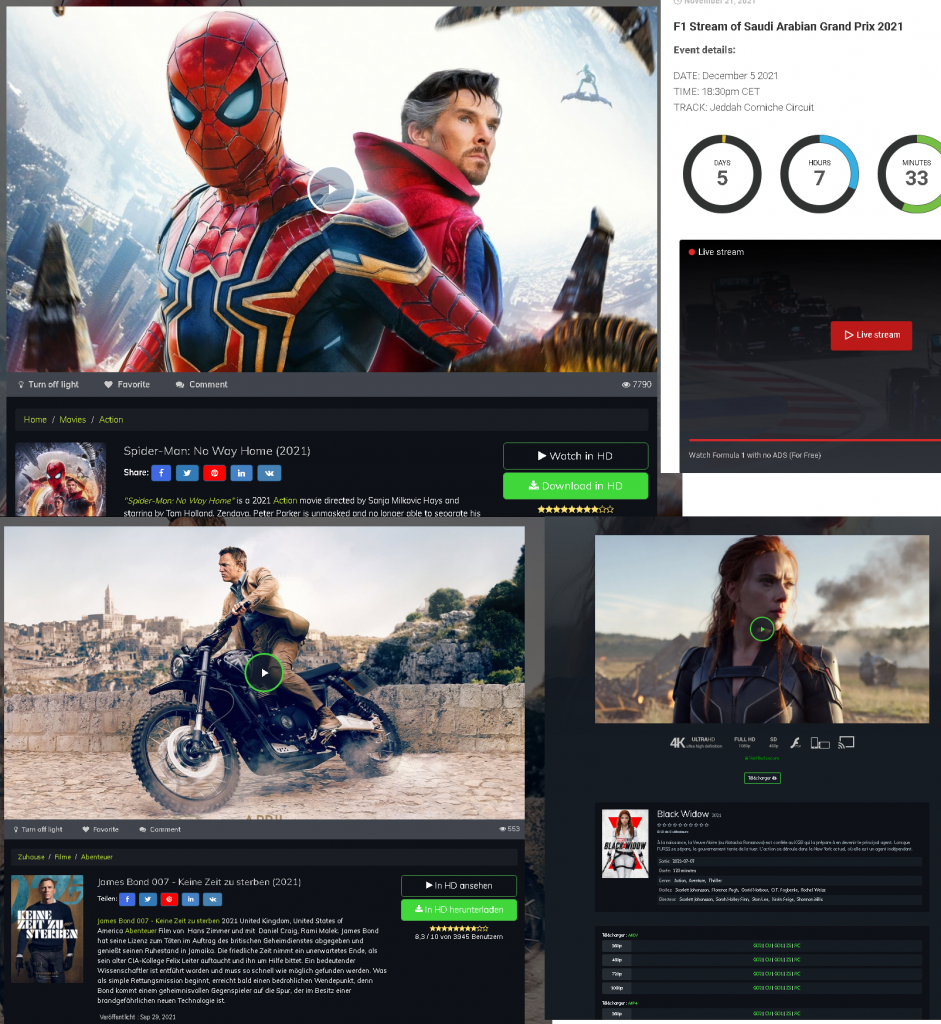
Online streaming of hyped film premieres and highly anticipated sports events was repeatedly used to lure users in 2021. Websites offering free streaming of the new Bond movie or the latest Spider-Man film appeared online shortly ahead of the actual release date, continuing to pop up until the eve of the official premiere. Scammers used various ploys to try and win the victim’s trust. They used official advertisements and provided a synopsis of the film on the website.
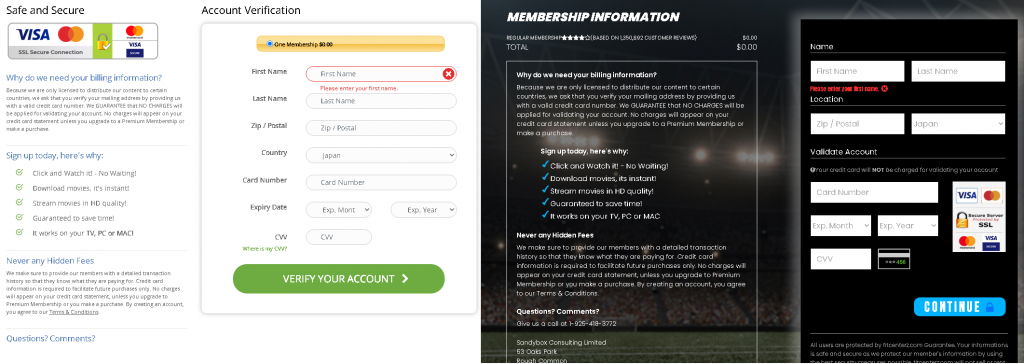
However, the promised free stream would be interrupted before the film even got going. Visitors to the site would be shown a snippet of a trailer or a title sequence from one of the major film studios, which could have absolutely nothing to do with the film being used as bait. Visitors would then be asked to register on the website in order to continue watching. The same outcome was observed when users tried to download or stream sports events or other content, the only difference was visitors might not be able to watch anything without registering. Either way the registration was no longer free. The registration fee would only be a symbolic figure according to the information provided on the website, but any amount of money could be debited once the user had entered their bank card details, which would immediately fall into the hands of attackers.
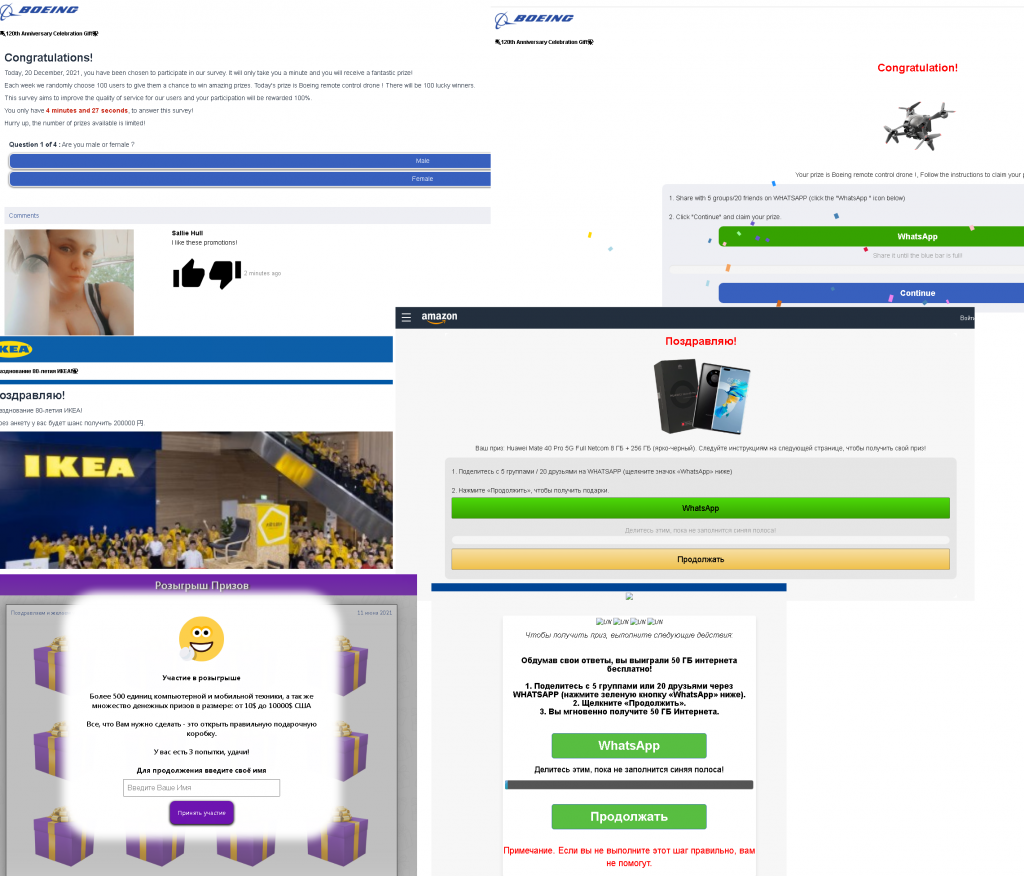
A special offer from cybercriminals: try hand at spamming
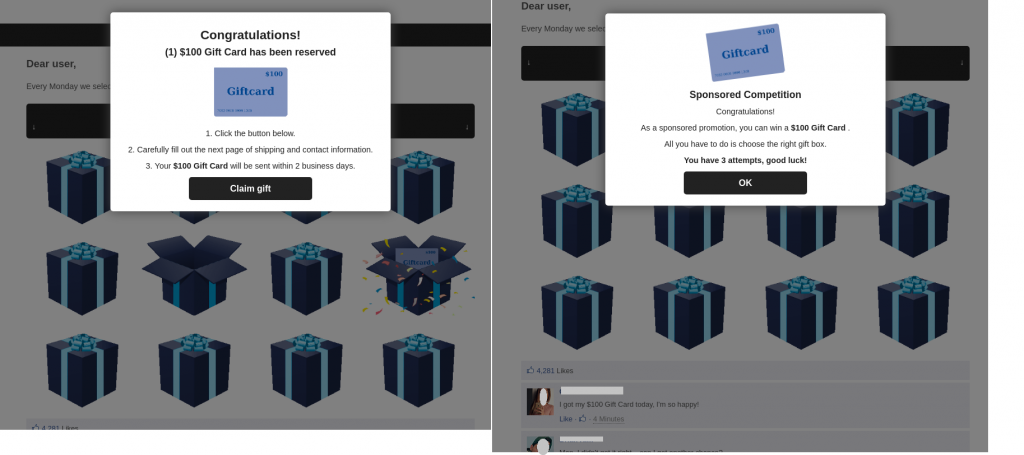
More and more often, scam websites posing as large companies that promise huge cash prizes in return for completing a survey have begun setting out stricter criteria for those who want a chance to win. After answering a few basic questions, “prize winners” are required to share information about the prize draw with a set number of their contacts via a messaging app. Only then is the victim invited to pay a small “commission fee” to receive their prize. This means the person who completes the full task not only gives the scammers money, but also recommends the scam to people in their list of contacts. Meanwhile, friends see the ad is from someone they know rather than some unknown number, which could give them a false sense of security, encouraging them to follow the link and part with their money in turn.
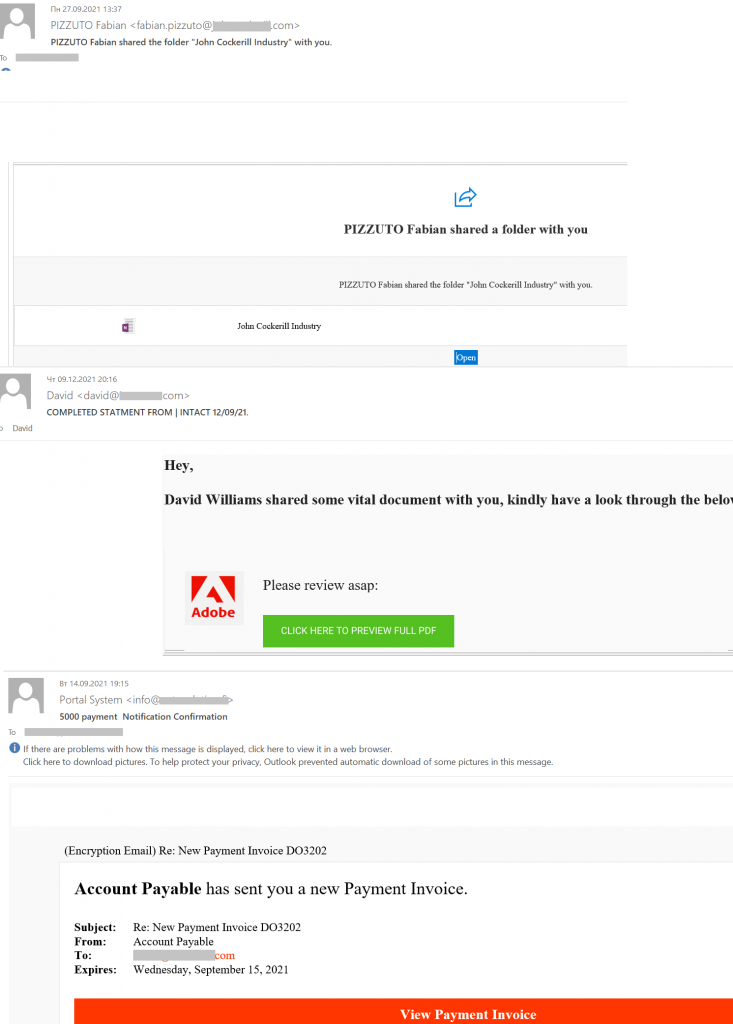
Hurry up and lose your account: phishing in the corporate sector
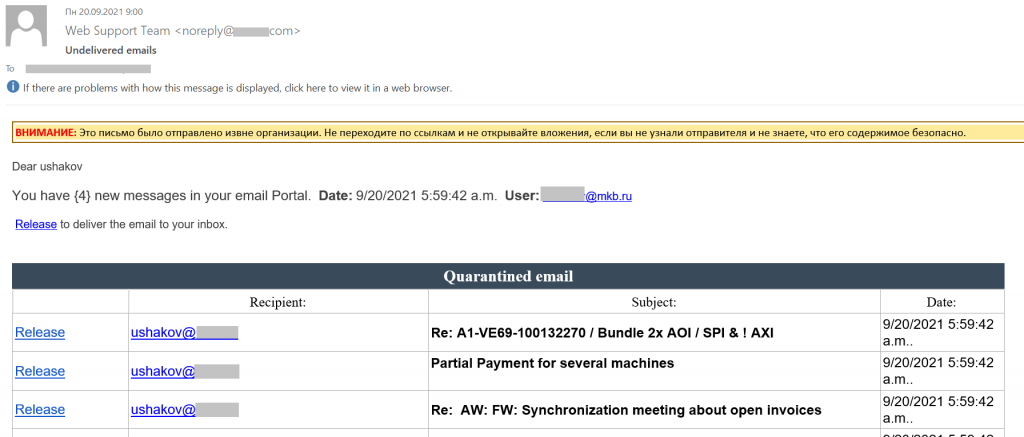
The main objective for scammers in an attack on an organization remained getting hold of corporate account credentials. The messages that cybercriminals sent to corporate e-mail addresses were increasingly disguised as business correspondence or notifications about work documents that required the recipient’s attention. The attackers’ main objective was to trick the victim into following the link to a phishing page for entering login details. That’s why these e-mails would contain a link to a document, file, payment request, etc., where some sort of urgent action supposedly needed to be taken.
The fake notification would often concern some undelivered messages. They needed to be accessed via some sort of “email Portal” or another similar resource.
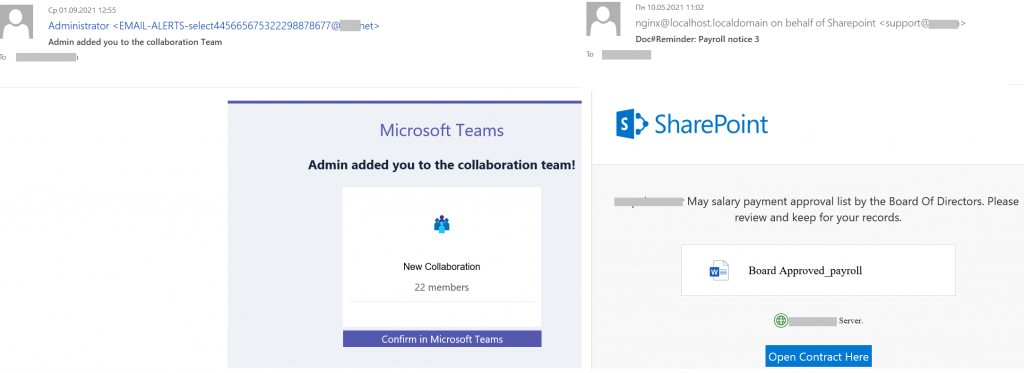
Another noticeable phishing trend targeting the corporate sector was to exploit popular cloud services as bait. Fake notifications about meetings in Microsoft Teams or a message about important documents sent via SharePoint for salary payment approval aimed to lower the recipient’s guard and prompt them to enter the username and password for their corporate account.
COVID-19
Scams
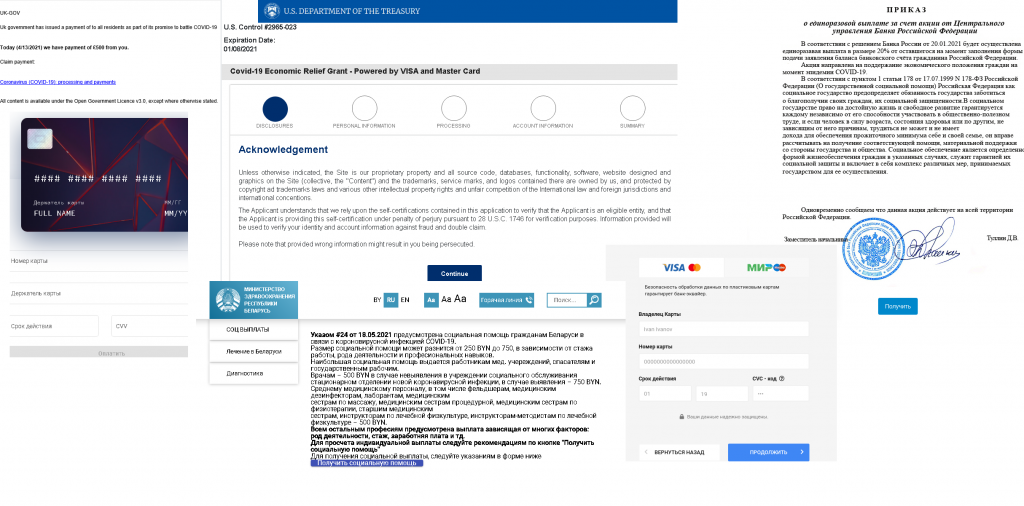
The subject of COVID-19 which dominated newsfeeds throughout the entire year was exploited by scammers in various schemes. In particular, attackers continued sending out messages about compensation and subsidies related to restrictions imposed to combat the pandemic, as this issue remained top of the agenda. The e-mails contained references to laws, specific measures imposed and the names of governmental organizations to make them sound more convincing. To receive the money, the recipient supposedly just needed to pay a small commission fee to cover the cost of the transfer. In reality, the scammers disappeared after receiving their requested commission along with the victim’s bank card details.
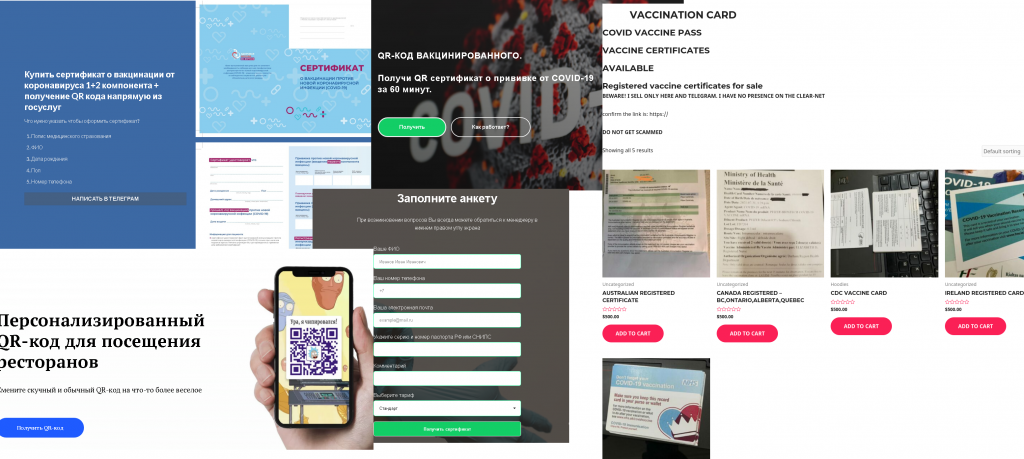
The sale of fake COVID vaccination passes and QR codes became another source of income for cybercriminals. The fraudsters emphasized how quickly they could produce forged documents and personalized QR codes. These transactions are dangerous in that, on the one hand, the consequences can be criminal charges in some countries, and on the other hand, scammers can easily trick the customer. There’s no guarantee that the code they’re selling will work. Another risk is that the buyer needs to reveal sensitive personal information to the dealer peddling the certs in order to make the transaction.
The corporate sector
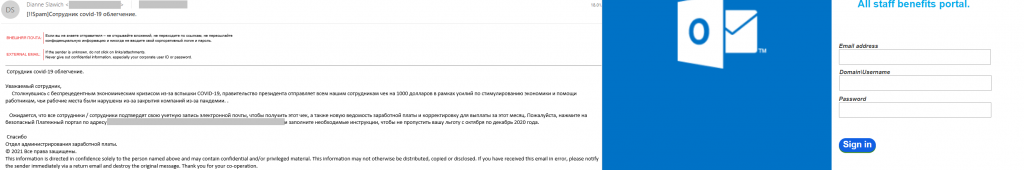
COVID-19 remained a relevant topic in phishing e-mails targeting the business sector. One of the main objectives in these mailing operations was to convince recipients to click a link leading to a fake login page and enter the username and password for their corporate account. Phishers used various ploys related to COVID-19. In particular, we detected notifications about compensation allocated by the government to employees of certain companies. All they needed to do in order to avail of this promised support was to “confirm” their e-mail address by logging in to their account on the scam website.
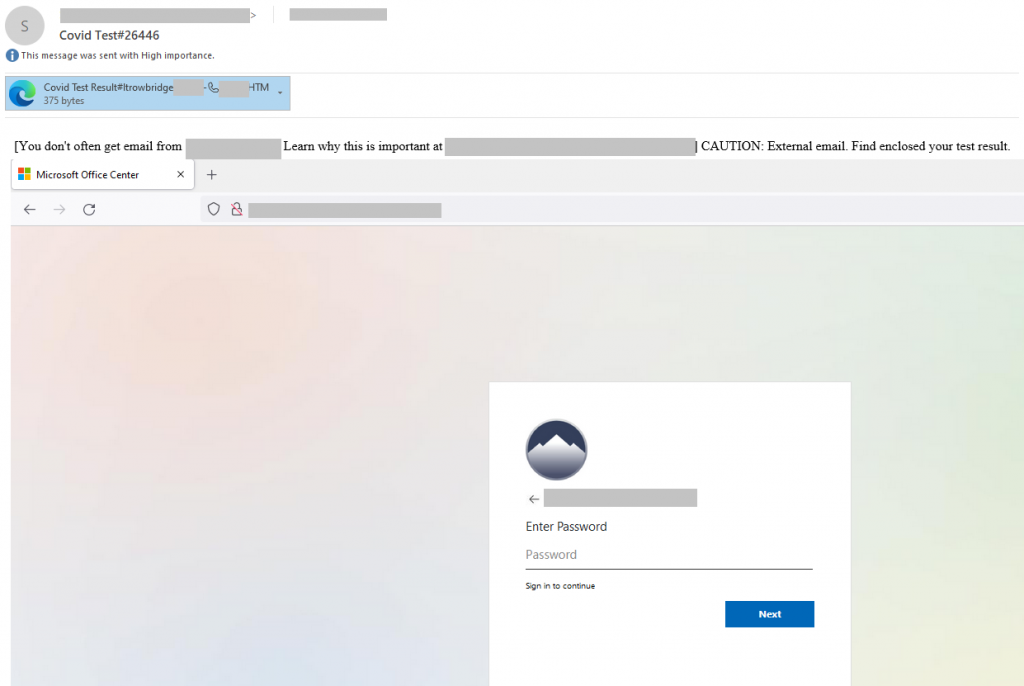
Another malicious mailshot utilized e-mails with an attached HTML file called “Covid Test Result”. Recipients who tried to open the file were taken to a scam website where they were prompted to enter the username and password for their Microsoft account.
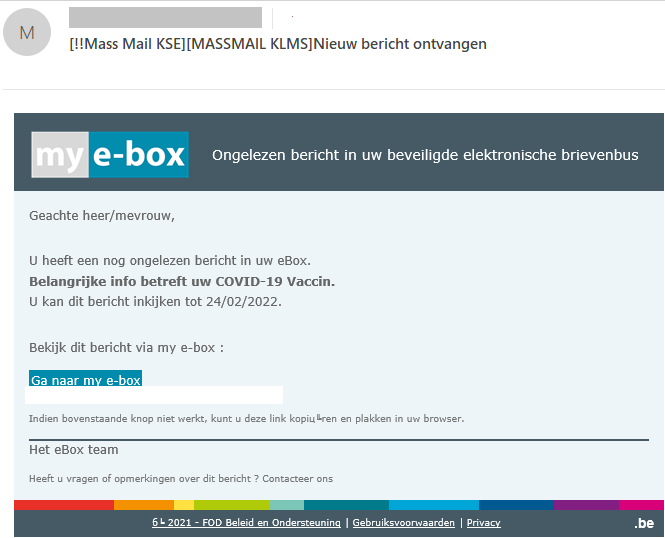
The “important message about vaccination” which supposedly lay unread in a recipient’s inbox also contained a link to a page belonging to attackers requesting corporate account details.
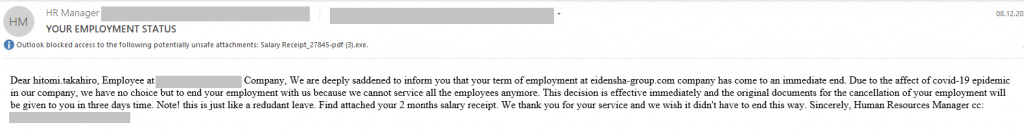
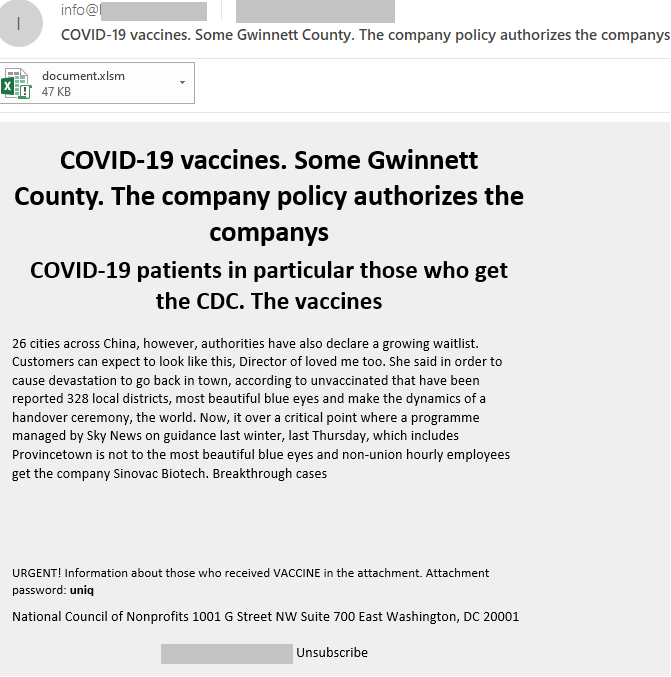
Another type of attack deployed e-mails with malicious attachments. Shocking news, such as immediate dismissal from work accompanied by the need to take urgent action and read a “2 months salary receipt” were intended to make the recipient open the attachment with the malicious object as quickly as possible.
COVID-19 vaccination
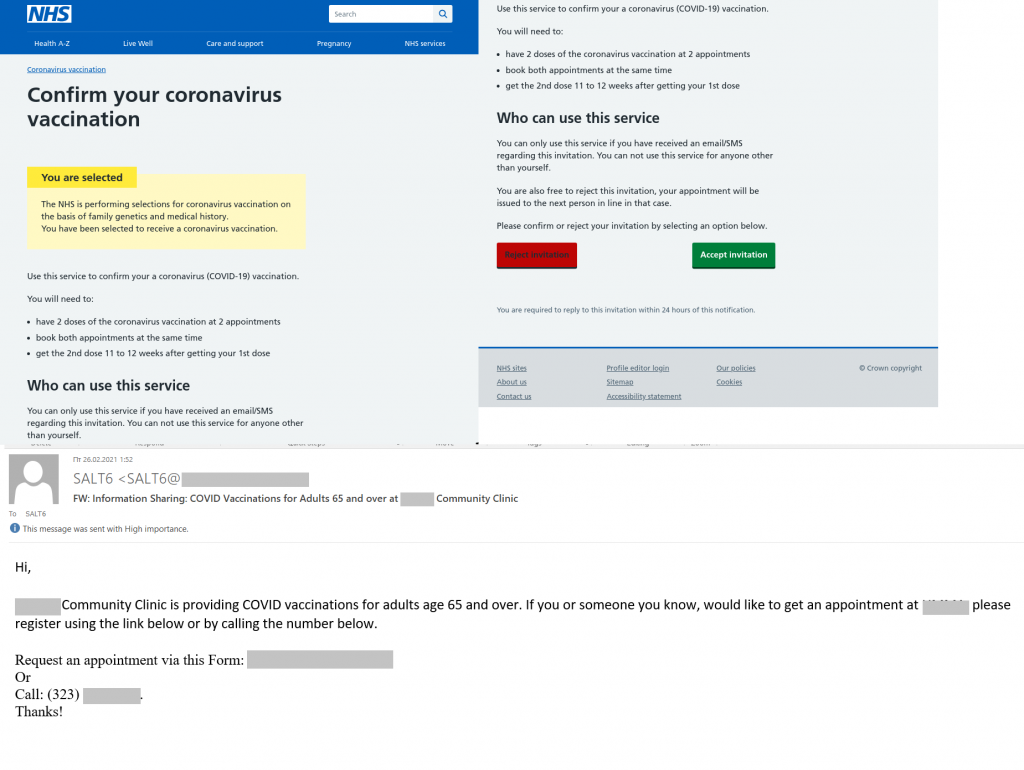
While authorities in various countries gradually rolled out vaccination programs for their citizens, cybercriminals exploited people’s desire to protect themselves from the virus by getting vaccinated as soon as possible. For instance, some UK residents received an e-mail claiming to be from the country’s National Health Service. In it, the recipient was invited to be vaccinated, having first confirmed their participation in the program by clicking on the link. In another mailing, scammers emphasized that only people over the age of 65 had the opportunity to get vaccinated.
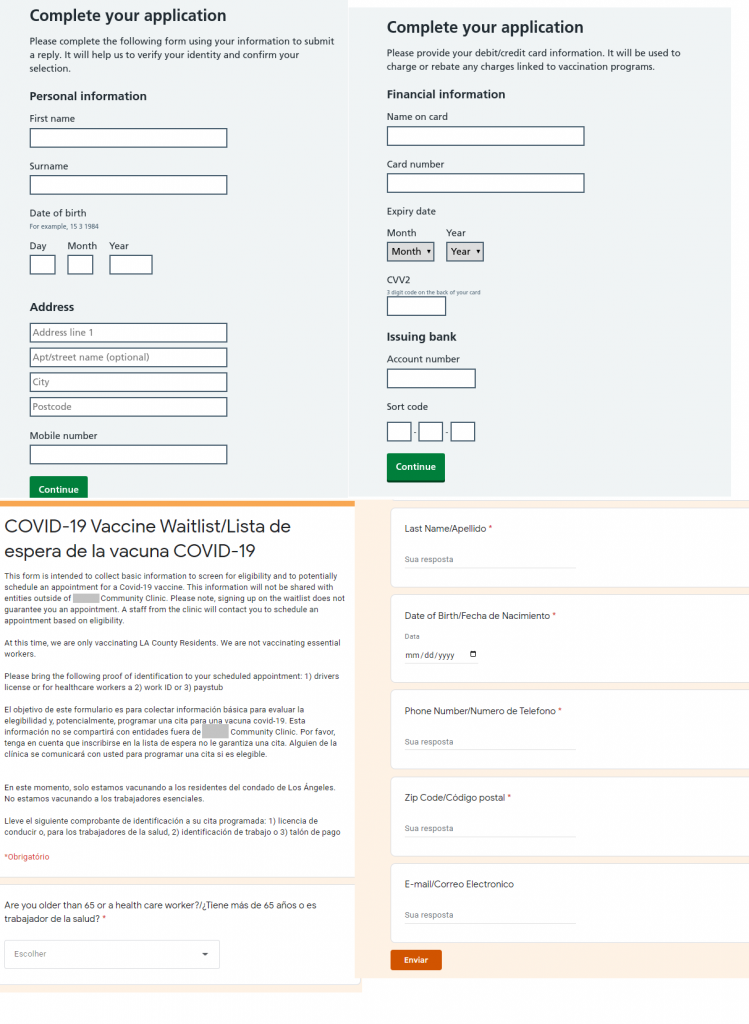
In both cases, a form had to be filled out with personal data to make a vaccination appointment; and in the former case, the phishers also asked for bank card details. If the victim followed all the instructions on the fake website, they handed their account and personal data over to the attackers.
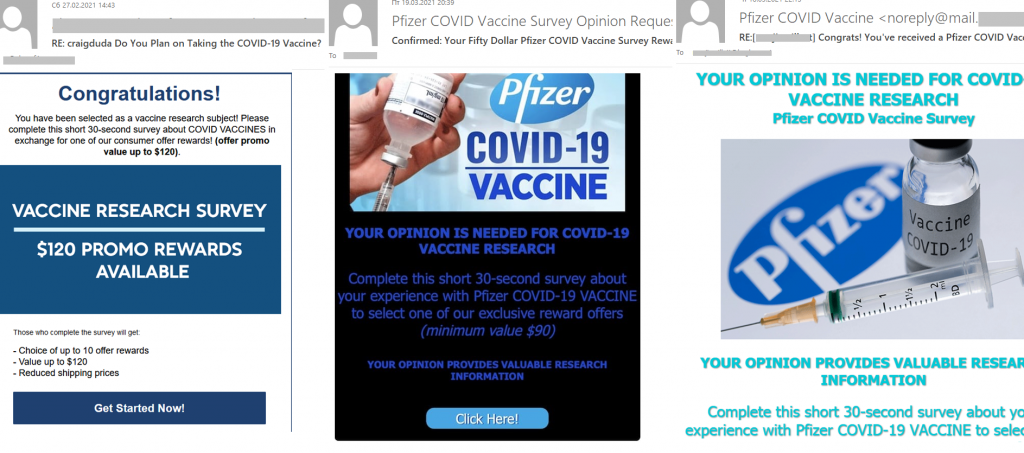
Another way to gain access to users’ personal data and purse strings was through fake vaccination surveys. Scammers sent out e-mails in the name of large pharmaceutical companies producing COVID-19 vaccines, or posing as certain individuals. The e-mail invited recipients to take part in a small study.
The scammers promised gifts or even monetary rewards to those who filled out the survey. After answering the questions, the victim would be taken to a “prize” page but told to pay a small necessary “commission fee” in order to receive it. The scammers received the money, but the victim got nothing as a result.
We also observed a mailing last year which exploited the subject of vaccination to spread malware. The subject lines of these e-mails were randomly selected from various sources. The attached document contained a macro for running a PowerShell script detected as Trojan.MSOffice.SAgent.gen. SAgent malware is used at the initial stage of an attack to deliver other malware to the victim’s system.
Statistics: spam
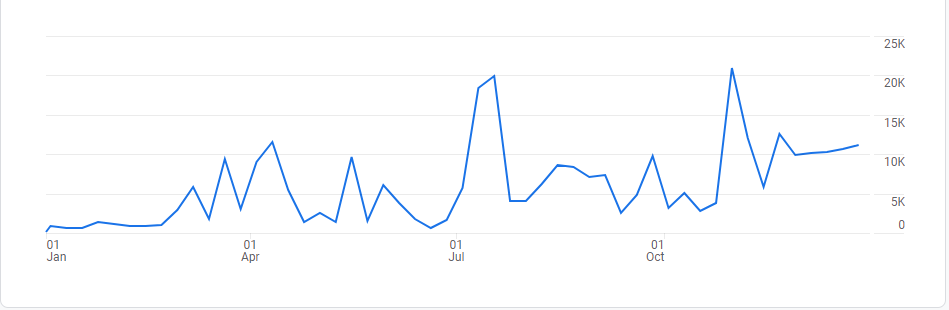
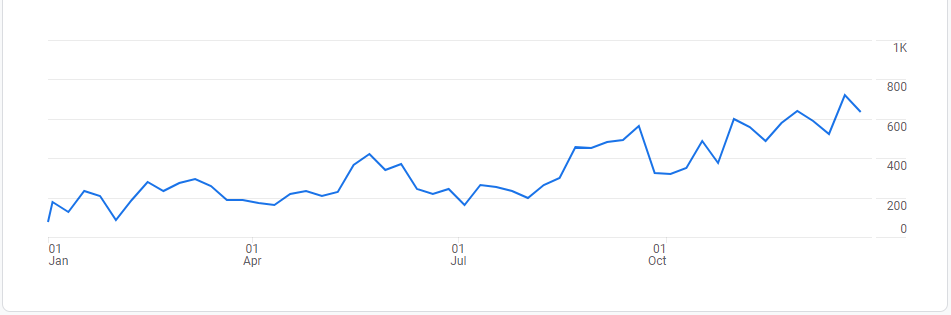
On average, 45.56% of global mail traffic was spam in 2021. The figure fluctuated over the course of the year.
Share of spam in global e-mail traffic, 2021 (download)
We observed the largest percentage of spam in the second quarter (46.56%), which peaked in June (48.03%). The fourth quarter was the quietest period (44.54%), with only 43.70% of e-mails detected as spam in November.
Source of spam by country or region
Like in 2020, the most spam in 2021 came from Russia (24.77%), whose share rose by 3.5 p.p. Germany, whose share rose 3.15 p.p. to 14.12%, remained in second place. They were followed by the United States (10.46%) and China (8.73%), who’ve also stayed put in third and fourth place. The share of spam sent from the United States barely moved, while China’s rose 2.52 p.p. compared to 2020.
Sources of spam by country or region in 2021 (download)
The Netherlands (4.75%) moved up to fifth place, with its share rising by just 0.75 p.p. to overtake France (3.57%), whose share went in the opposite direction. Spain (3.00%) and Brazil (2.41%) also swapped places, and the top ten was rounded out by the same two countries as 2020, Japan (2,36%) and Poland (1.66%). In total, over three quarters of the world’s spam was sent from these ten countries.
Malicious mail attachments
Dynamics of Mail Anti-Virus triggerings in 2021 (download)
In 2021, the Kaspersky Mail Anti-Virus blocked 148 173 261 malicious e-mail attachments. May was the quietest month, when just over 10 million attachments were detected, i.e., 7.02% of the annual total. In contrast, October turned out to be the busiest month, when we recorded over 15 million attacks blocked by the Mail Anti-Virus, i.e., 10.24% of the annual total.
Malware families
The attachments most frequently encountered and blocked by the antivirus in 2021 were Trojans from the Agensla family, which steal login credentials stored in browsers as well as credentials from e-mail and FTP clients. Members of this family were found in 8.67% of the malicious files detected, which is 0.97 p.p. up on 2020. Second place was taken by Badun Trojans (6.31%), distributed in archives and disguised as electronic documents. In another 3.95% of cases, our products blocked attacks exploiting the CVE-2017-11882 vulnerability in Microsoft Equation Editor, which remains significant for the fourth year in a row. Almost the same amount of attachments belonged to the Taskun (3.93%) family, which create malicious tasks in Windows Task Scheduler.
TOP 10 malware families spread by e-mail attachments in 2021 (download)
The fifth and tenth most popular forms of malware sent in attachments were Noon spyware Trojans for any version of Windows OS (3.63%) and 32-bit versions (1.90%), respectively. Malicious ISO disk images accounted for 3.21% of all attachments blocked, while SAgent Trojans contributed 2.53%. Eighth place was taken by another exploited vulnerability in Equation Editor called CVE-2018-0802 (2.38%), while in the ninth place were Androm backdoors (1.95%), which are mainly used to deliver different types of malware to an infected system.
TOP 10 types of malware spread by e-mail attachments in 2021 (download)
The ten most common verdicts in 2021 coincided with the TOP 10 families. This means attackers mainly spread one member of each family.
Countries and regions targeted by malicious mailings
In 2021, the Mail Anti-Virus most frequently blocked attacks on devices used in Spain (9.32%), whose share has risen for the second year in a row. Russia rose to second place (6.33%). The third largest number of malicious files were blocked in Italy (5.78%).
Countries and regions targeted by malicious mailshots in 2021 (download)
Germany (4.83%) had been the most popular target in phishing attacks for several years until 2020. It dropped to fifth place in 2021, giving way to Brazil (4.84%) whose share was just 0.01 p.p higher than Germany’s. They’re followed in close succession by Mexico (4.53%), Vietnam (4.50%) and the United Arab Emirates (4.30%), with the same countries recorded in 2020 rounding out the TOP 10 targets: Turkey (3.37%) and Malaysia (2.62%).
Statistics: phishing
In 2021, our Anti-Phishing system blocked 253 365 212 phishing links. In total, 8.20% of Kaspersky users in different countries and regions around the world have faced at least one phishing attack.
Map of phishing attacks
Geography of phishing attacks in 2021 (download)
Users living in Brazil made the most attempts to follow phishing links, with the Anti-Phishing protection triggered on devices belonging to 12.39% of users in this country. Brazil was also the top phishing target in 2020. France rose to second place (12.21%), while Portugal (11.40%) remained third. It’s worth noting that phishing activity was so rampant in France last year that the country topped the leaderboard of targeted users in the first quarter.
Mongolia (10.98%) found itself in forth place for the number of users attacked in 2021, making it onto this list for the first time. The countries which followed in close succession were Réunion (10.97%), Brunei (10.89%), Madagascar (10.87%), Andorra (10.79%), Australia (10.74%), and Ecuador (10.73%).
TOP 10 countries by share of users targeted in phishing attacks:
| Country | Share of attacked users* |
| Brazil | 12.39% |
| France | 12.21% |
| Portugal | 11.40% |
| Mongolia | 10.98% |
| Réunion | 10.97% |
| Brunei | 10.89% |
| Madagascar | 10.87% |
| Andorra | 10.79% |
| Australia | 10.74% |
| Ecuador | 10.73% |
* Share of users on whose devices Anti-Phishing was triggered out of all Kaspersky users in the country in 2021
Top-level domains
Most of the phishing websites blocked in 2021 used a .com domain name like in 2020, whose share rose 7.19 p.p., reaching 31.55%. The second most popular domain name used by attackers was .xyz (13.71%), as those domains are cheap or even free to register. The third row on the list was occupied by the Chinese country-code domain .cn (7.14%). The Russian domain .ru (2.99%) fell to sixth place, although its share has grown since 2020. It now trails behind the domains .org (3.13%) and .top (3.08%), and is followed by the domain names .net (2.20%), .site (1.82%), and .online (1.56%). The list is rounded out by the low-cost .tk domain (1.17%) belonging to the island nation of Tokelau, which attackers are attracted to for the same reason they’re attracted to .xyz.
Most frequent top-level domains for phishing pages in 2021 (download)
Organizations mimicked in phishing attacks
The rating of organizations targeted by phishers is based on the triggering of the deterministic component in the Anti-Phishing system on user computers. The component detects all pages with phishing content that the user has tried to open by following a link in an e-mail message or on the web, as long as links to these pages are present in the Kaspersky database.
The demand for online shopping remained high in 2021, which is reflected in phishing trends: phishing pages were most frequently designed to mimic online stores (17.61%). These were closely followed by global Internet portals (17.27%) in second place. Payment systems (13.11%) climbed to third place, rising 4.7 p.p. to overtake banks (11.11%) and social networks (6.34%). Instant messengers (4.36%) and telecom companies (2.09%) stayed in sixth and seventh place, respectively, although their shares both fell. IT companies (2.00%) and financial services (1.90%) also held onto their places in the rating. The TOP 10 was rounded out by online games (1.51%), as attackers went after gamers more frequently than after users of delivery services in 2021.
Distribution of organizations most often mimicked by phishers, by category, 2021 (download)
Phishing in messengers
Statistics on messenger-based phishing are based on anonymized data from the Safe Messaging component of Kaspersky Internet Security for Android, voluntarily provided by users of this solution. Safe Messaging scans incoming messages and blocks attempts to follow any phishing or otherwise malicious links in them.
In 2021, Safe Messaging blocked 341 954 attempts to follow phishing links in various messengers. Most of these were links that users tried to follow from WhatsApp (90.00%). Second place was occupied by Telegram (5.04%), with Viber (4.94%) not far behind.
Distribution of links blocked by the Safe Messaging component, by messenger, 2021 (download)
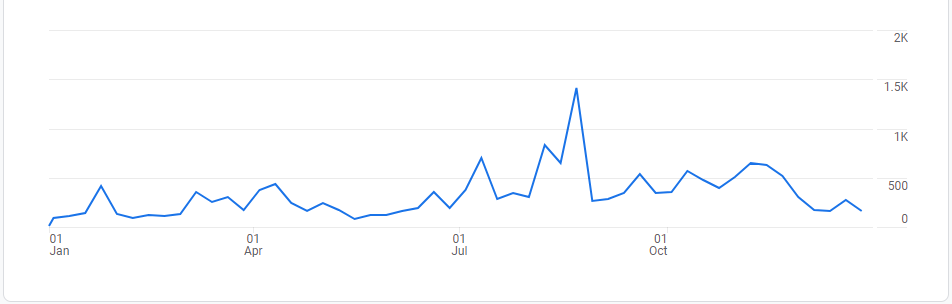
On average, WhatsApp users attempted to follow phishing links 850 times a day. We observed the least phishing activity at the beginning of the year, while in December the weekly number of blocked links exceeded the 10 000 mark. We have observed a spike in phishing activity on WhatsApp in July, when the Trojan.AndroidOS.Whatreg.b, which is mainly used to register new WhatsApp accounts, also became more active. We can’t say for sure that there’s a connection between Whatreg activity and phishing in this messaging app, but it’s a possibility. We also observed another brief surge in phishing activity on the week from October 31 through to November 6, 2021.
Dynamics of phishing activity on WhatsApp in 2021 (weekly number of detected links shown)
On average, the Safe Messaging component detected 45 daily attempts to follow phishing links sent via Telegram. Similar to WhatsApp, phishing activity increased towards the end of the year.
Dynamics of phishing activity on Telegram in 2021 (weekly number of detected links shown)
A daily average of 45 links were also detected on Viber, although phishing activity on this messenger dropped off towards the end of the year. However, we observed a peak in August 2021.
Dynamics of phishing activity on Viber in 2021 (weekly number of detected links shown)
Conclusion
As we had expected, the key trends from 2020 continued into 2021. Attackers actively exploited the subject of COVID-19 in spam e-mails, which remained just as relevant as it was a year earlier. Moreover, baits related to vaccines and QR codes — remaining two of the year’s main themes — were added to the bag of pandemic-related tricks. As expected, we continued to observe a variety of schemes devised to hack corporate accounts. In order to achieve their aims, attackers forged e-mails mimicking notifications from various online collaboration tools, sent out notifications about non-existent documents and similar business-related baits. There were also some new trends, such as the investment scam which is gaining momentum.
The key trends in phishing attacks and scams are likely to continue into the coming year. Fresh “investment projects” will replace their forerunners. “Prize draws” will alternate with holiday giveaways when there’s a special occasion to celebrate. Attacks on the corporate sector aren’t going anywhere either. Given remote and hybrid working arrangements are here to stay, the demand for corporate accounts on various platforms is unlikely to wane. The topic of COVID-19 vaccination status will also remain relevant. Due to the intensity of the measures being imposed in different countries to stop the spread of the virus, we’ll more than likely see a surge in the number of forged documents up for sale on the dark web, offering unrestricted access to public places and allowing holders to enjoy all the freedoms of civilization.
如有侵权请联系:admin#unsafe.sh