If implemented well, eIDAS 2.0 will transform the online safety, privacy, and user experience of Europe’s citizens.
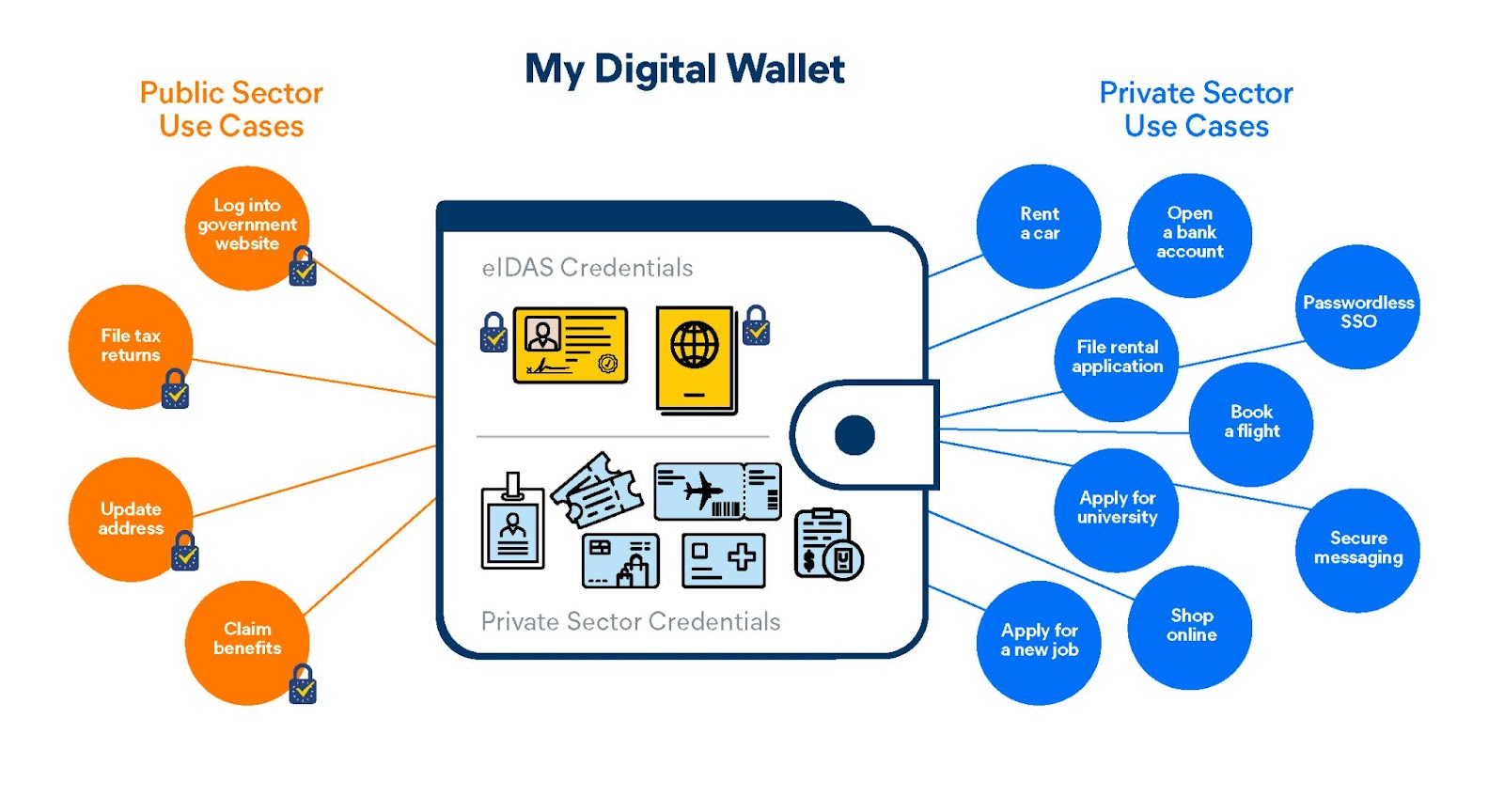
In June 2021, the European Commission proposed an update to its pan-European digital identity framework that will enable every European to have a set of digital identity credentials that are recognized anywhere in the EU. At the core of this new initiative are digital wallets — mobile apps or cloud services that receive and store these digital credentials, and allow them to be used privately and securely for many government and non-government use cases. This proposal (“eIDAS 2.0”) represents an evolution of an existing EU regulation, eIDAS (electronic IDentification, Authentic and trust Services), which was established in 2014. eIDAS 2.0 brings enormous opportunities if implemented well. The potential to rid society of so many of the ills of the Internet is too high to ignore. However if implemented badly, it could squander the enormous potential of digital wallets and digital credentials and set back digital trust infrastructure even further. Realistically, there’s one more chance left to get this right. Big tech looms. Even the more friendly-seeming mega-corporations have shown their hand in opposing open identity ecosystems and the World Wide Web Consortium’s decentralized identifier (DID) specification. Avast supports the directions of the European Commission with this initiative and the motivators and principles behind it. As an organization that provides safety, privacy and convenience for millions and or people in Europe and around the world, we see great importance of a global interoperable digital smart agent service which is consistent with EC requirements. Further, we recognize the necessity of close public-private sector collaboration in the detailed definition of requirements and in the commercial operation of a partner-led network in Europe and beyond. We want to embed eIDAS within the products used by our millions of users across Europe and beyond. But only if it addresses the problems listed below, and maximizes the opportunities that we know are there to be had. Here’s Avast’s view of what to encourage, and what to avoid in eIDAS 2.0. It’s fair to say that the first pan-European digital identity scheme, eIDAS, has not been wildly successful. It joins other first generation nationwide schemes such as the UK’s gov.uk Verity program in missing the intended target. Overly complex technical architecture, restricted private sector use, a horrible user interface, and a small and inflexible data set have all held back widespread adoption. In the European Commission’s own words: “The evaluation of the eIDAS Regulation 2 revealed that the current Regulation falls short of addressing these new market demands, mostly due to its inherent limitations to the public sector, the limited possibilities and the complexity for online private providers to connect to the system, its insufficient availability of notified eID solutions in all Member States and its lack of flexibility to support a variety of use cases.” Additionally, the European Commission is looking to directly address the surveillance capitalism market with this new proposal: “Furthermore, identity solutions falling outside the scope of eIDAS, such as those offered by social media providers and financial institutions, raise privacy and data protection concerns.” Recognizing there is a problem is the first step to fixing it. And fixing it is exactly what the European Commission wants to do with its updated “eIDAS 2.0” proposal. The Commission’s aspiration “for 80% of citizens to use digital ID for public services” is ambitious, and its implementation can provide much needed global leadership and direction. Naturally, this proposal is attracting a lot of interest and attention. A notable early paper on the topic from EDRi, a digital rights association, picks up on a number of important points and possible drawbacks with the proposed approach. Innopay also draws attention to a very important but much overlooked aspect of the proposal - the mandated acceptance of eIDAS 2.0 credentials in the private sector. At Avast, we have been very encouraged by what we have seen so far. Early output from the European Commission’s working groups indicates a real willingness to adopt ground-breaking privacy and security approaches that Avast, via its recent acquisition of Evernym, has pioneered. But we also see problems on the horizon. It would be a disaster if the opportunity was wasted, and it would leave a vacuum to be filled by the ever-hungry big data surveillance capitalists. Here we list the things to watch out for and the things we want to see for the benefit of European users and European business. It has been mooted that each EU Digital Identity Wallet should have a unique identifier. It’s hard to believe that this comes from the same place that has implemented strict laws on tracking cookies. A unique wallet identifier is like a global super-cookie. It would enable everything you do with your EU Digital Identity Wallet to be tracked, correlated, and profiled. It’s a bad idea. It must not happen. It is the wrong solution to a problem that can be rectified in a much better way. The idea for a unique wallet identifier appears to stem from a need to have a remote wallet “kill switch” to allow a wallet provider (e.g., your government or a private sector wallet developer) to lock and burn your wallet if you lose it or if it is stolen, in order to protect the eIDAS credentials within. Given that such a wallet is likely to contain lots of other non-eIDAS credentials (see the “Wallet Content Restrictions” point coming up), this is akin to the government coming into your house and destroying your filing cabinet with all your personal papers in it, just in order to revoke your driving license because you were caught speeding. The proper approach is to revoke the credentials within the wallet that are the cause for concern, rather than killing the whole wallet. To be actually useful to all Europeans, any such eIDAS-capable wallet should be a container that allows users to securely store all sorts of credentials. It should not be restricted to holding just eIDAS credentials from certified “Qualified Trust Service Providers” (QTSPs). Such a restriction would be akin to governments saying to people “you can’t put your physical driving license in your regular wallet, you need to have this special wallet that can only contain your driving license and nothing else, and by the way we may cause it to spontaneously combust if we feel like it”. If I want to book a flight, I can use my eIDAS credential for advance passenger information, my non-eIDAS bank card credential to pay for it, and my non-eIDAS frequent flyer credential to claim my loyalty points. And then why not put my receipt and ticket in my wallet so I can use it for contactless travel at the airport? And when I get to the airport I want to combine my flight ticket (non-EIDAS) with my passport (eIDAS) and my Covid vaccine status (non-eIDAS). This is the reality of the vast majority of online and face-to-face transactions. The EU Digital Identity Wallet must allow people to store and use non-eIDAS credentials, for any use case they want. The wallet must enable attributes from eIDAS and non-eIDAS credentials to be combined in a single transaction (a “compound proof”) and allow subsets of attributes to be shared rather than all attributes in a credential (called “selective disclosure”). If barriers are put in the way of private sector use of eIDAS 2.0, it will struggle just as eIDAS 1.0 has. People don’t deal with their government very frequently. And when they do it is often for something they don’t like, such as paying taxes, fines, or some other bureaucratic task. While important, many government use cases are not exciting or interesting to people. The European Commission should ensure that the private sector is able to use this highly empowering new capability. Something that finally enables people to transact securely online, with a beautiful user experience, and with trust. eIDAS 2.0 breaks the catch-22 of credential ecosystems. Verifiers (organizations looking to request and verify credential data from their customers/users) want issuers to already exist. Issuers (governments and other organizations who issue credentials like banks, airlines, utility companies) want verifiers in place. The eIDAS 2.0 proposal should result in the issuance of the very high quality digital credentials that verifiers/relying parties are all looking for and waiting for. The European Commission should focus on removing barriers to private sector use. The technology exists to prevent the government from tracking what you do with your eIDAS credentials (assuming unique wallet IDs aren’t implemented), and you should be able to use them just as easily as a physical paper or plastic credential. It has been suggested that private sector relying parties (e.g., banks, telcos, retailers) should “register” with their member state to be able to accept eIDAS credentials. Why? Do they need to register in order to look at my passport to verify my age? Of course not. Adding this burdensome step will increase cost and hold back adoption. The credential verification keys of eIDAS issuers should be stored in a publicly accessible verifiable data registry that anyone can access for any use case. Private sector acceptance should not be restricted. The provision of any data will be under the user’s control at all times. In doing so, care should be taken to prevent new methods of phishing (bad actors encouraging users to connect and share data while impersonating a legitimate organization). Users must be able to confirm the legitimacy of an organization they are connecting to. Refer to the section on Trust Lists later in this article. There are lots of upsides to the eIDAS 2.0 proposals. Avast describes four of them that we see as important for widespread adoption by European Union citizens. A “reference wallet architecture” is being produced by the eIDAS 2.0 wallet functionality working group. This will set the baseline for functionality of an eIDAS 2.0-compliant wallet, and much of the infrastructure that issuers and verifiers will need to put in place to interact with one. Offering citizens a selection of identical wallets with identical “basic” level functionality won’t really be offering a choice at all. Wallet developers should be free to add useful functionality around the wallet. This could be automation of some business process, like applying for a bank account. Or it could be to ensure that you have all the credentials required for international travel, as well my complete travel profile to include credentials with air, hotel, car, train providers including preferences. This is where wallets start to become really compelling and useful – in fact a digital smart agent as a super-set of a wallet is the consumer-facing innovation that we see to be most valuable to Europeans interacting in public and private sector use cases. Ensuring that wallet developers can enhance eIDAS 2.0 functions while remaining eIDAS 2.0 certified will drive innovation, competition and uptake. As pointed out in Innopay’s article, EC regulations tend to be looked upon as scary, costly and time consuming. Mandating acceptance of eIDAS 2.0 wallets and credentials by private sector organizations will be sending shudders through the regulatory departments of companies across Europe. But it doesn’t need to be like this. eIDAS 2.0 presents businesses with an opportunity to transform their online user experiences, to replace multi-step form filling with single-step onboarding. For the first time, customers will be arriving armed with verifiable, highly trustworthy government-issued credentials. These can be checked in moments. Checkout abandonment rates will reduce. Onboarding costs will drop. Fraud will plummet. User experience will simplify. Businesses that adopt these new capabilities will out-compete their rivals. And there are other benefits. The underlying technology means you can finally remove not only passwords but also usernames. And multi-factor authentication comes inbuilt by default. The opportunities for businesses to turn the regulations into revenue are too good to ignore. eIDAS 2.0 shouldn’t be only about governments and organizations. It should help people trust each other as well. If used correctly, the tech and protocols that will make eIDAS 2.0 work can be used just as easily for person-to-person verification as they can for person-to-organization verification. When the utilities worker arrives at your door, you should be able to check who they are and that they are properly trained and employed. When you hire a photographer to shoot your children’s birthday party you should be able to check their bonafides and that they are cleared to work with children. The eIDAS specification should include person-to-person verification use cases. An often overlooked capability of the technologies behind digital credentials is that the secure, mutually authenticated connections that they set up between two parties can be used for a lot more than just exchanging credentials. The peer-to-peer encrypted connections can be used for exchanging messages between two parties, without anyone (like WhatsApp/Google/Apple) being in the middle. And to make it even more attractive, you’ll be able to tell instantly if there is a person-in-the-middle attack taking place, if you are being phished, and you'll be in control of who can send you any messages. This presents an excellent opportunity to wrest messaging services away from big tech and put them back into the hands of individuals. As well as the clear problems and clear opportunities listed above, there are a number of areas that straddle both categories. Here Avast lists three topics to pay very close attention to. It is highly likely that the cost of verifying facts about people will drop significantly. As a result, the usual friction associated with verification falls away. What happens then? The danger that this could cascade into the digital equivalent of “Papers please!” is something we have been thinking about for several years now; the negative implications are articulated nicely in this EDRi paper and has been already seen in India, where excessive demands for verification of the Aadhaar digital identity scheme resulted in a Supreme Court judgement restricting the situations where organizations could demand Aadhaar verification Simply put, if verification costs near nothing, it follows that the number of times you’ll be asked to verify yourself will increase. This could lead to uncontrollable “verification-mania” where things that previously could be done without needing an ID check become transformed “just in case”. The unintended consequence will be a nightmare of constantly pinging devices nagging you to verify or authenticate all the time. The result will be a drop in the perceived value of doing so, and a tendency (like with the annoying cookie banners) to just say “OK, OK, I give in, have it”. And once that happens, the floodgates open for abuse and harmful data harvesting. On the positive side, lower costs mean it becomes possible to do things that were previously impossible. This can drastically improve peoples’ online lives. For example, it suddenly becomes trivial to know that the online social group you are involved in is made up of people you can trust. It also opens up the opportunity to transform business processes that were previously too expensive to put in place, bringing about a wave of innovation and new market opportunities. It means banks should be able to clamp down more easily on fraudsters that open accounts to hold scammed money from pensioners. It means international travel can become seamless. Renting a house can (finally) be easier and faster. This will have to be watched very carefully. Attention should be paid to the unintended consequences while opening up the floor to innovation. The beauty of decentralized identity techniques is that it becomes possible for both parties in a connection (e.g., a retailer and their customer, a government and their citizen) to mutually verify each other. This in turn means that it is possible to develop a list of which organizations I should trust. Such a list enables citizens to quickly determine if the organization they are connecting to is legitimate, preventing impersonation via sophisticated techniques, and thus reinforcing overall trust in the whole ecosystem. This is a tremendous opportunity to enable people to quickly understand whether they can trust the owner of whichever QR code they are scanning. Is it really who it purports to be? However, who manages the trust list? Does each member state have its own? How does that work if I travel from Sweden to Belgium? What is considered trustworthy in Finland may be illegal in Spain. The owner of the trust list has the power to render a person’s credentials useless (or “value-less”). They could bankrupt an organization by accidentally flagging them as untrustworthy. A bad actor could have a field day if they get access to the trust list. So trust lists are a blessing and a curse. We recommend considerable effort is put into this area by the European Commission to ensure they are implemented in such a way to avoid the pitfalls listed above. Any digital credential ecosystem needs to have incentives for all participants to take part. To date we have not seen any reference to incentive or revenue models in the eIDAS 2.0 proposals. It will be necessary for such a model to be created, agreed upon and well implemented. Issuers of eIDAS credentials will expend significant effort to create credentials of the required level of assurance. This will be costly. Who pays? Will governments pay 3rd parties to verify paper documents that the government themselves have already issued for example? Verifiers will need incentives to spend the money required to integrate eIDAS 2.0 into their internal systems. Our experience shows that this is not a trivial exercise. What are the incentives for the verifiers (other than legally mandated regulations) to do so? Without such incentives, it will be very difficult to involve the private sector. Lessons learned from eIDAS 1.0 show us that success is highly dependent on private sector involvement. And of course the supporting infrastructure needs to be built, run and paid for by somebody. We encourage the early discussion and definition of the eIDAS 2.0 incentive model at the European Commission level. If implemented well, eIDAS 2.0 will transform the online safety, privacy, and user experience of Europe’s citizens. It will save huge costs in both the public and private sectors. It will drive innovation and enable online experiences that were previously not possible. If implemented badly, it will fail to gain traction, citizens won’t adopt it, and it will be torn to pieces by privacy campaigners. “Big tech” and their surveillance capitalism will fill the vacuum and dominate. Avast looks forward to working closely with the Commission, Member States and the private sector to deliver the vision of secure, private digital identity for all.Situation summary
Problem 1: Unique wallet IDs
Problem 2: Remote wallet kill switches
Problem 3: Wallet content restrictions
Problem 4: Private sector restrictions
Exciting new opportunities for eIDAS 2.0
Opportunity 1: Basic or enhanced wallets
Opportunity 2: Turning regulations into revenue
Opportunity 3: Person-to-person verification
Opportunity 4: Secure messaging
Things that could go either way
Problem & opportunity 1: The impact of lower verification costs
Problem & opportunity 2: Trust lists
Problem & opportunity 3: The incentive model
Conclusion
如有侵权请联系:admin#unsafe.sh