As attacks increase and become more clever across the web both site owners and visitors alike must understand the risks that come along with using the web in this current generation. In this post we’ll be going over the kinds of sensitive data hackers can obtain on the web, and the best methods to prevent this from both sides. One of the main reasons hackers hack websites is to obtain and abuse the site’s resources. If you’re utilizing WordPress, there are also additional tips provided in our recent post Why are WordPress Websites Targeted by Hackers?
The Impact of Sensitive Information Being Stolen
An attacker can obtain a wide range of information from a person across the web. From credit cards to passwords, the list of sensitive data obtained can be astounding. Hackers can exploit this information by using it for their leisure. Identity theft in today’s world is no joke. The types of attacks capable of retrieving this information can be one of the following:
- Phishing campaigns
- SQL Injections
- Backdoors
- Access Control
- XSS attacks
- Man-in-the-middle-attack (MitM)
- Click-jacking
- Cross-site request forgery (CSRF)
- Session hijacking
- CC Skimming
- Directory traversal
- Brute Force Attack
- Ransomware
SEO Spam
The main purpose behind SEO spam being injected into a website is to prop up their spam sites for profit. This kind of spam is supposed to redirect visitors to their sites instead. This also has a heavy impact on any type of site in terms of traffic and business.
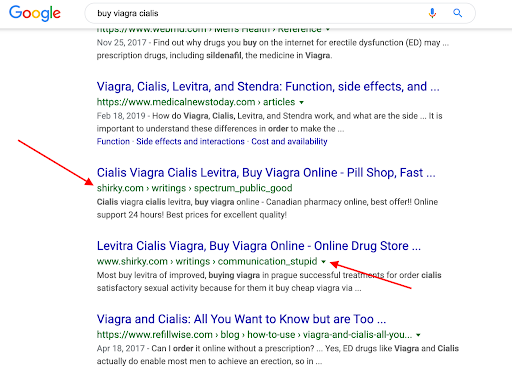
This is one of the most common types of website infections that website administrators face.
Distributed Denial of Service (DDoS) Attacks
These kinds of attacks take sites offline for a few different reasons. It could be politically, financially, personally motivated, or, just for fun. As a side note, this can also apply to defacement types of infections as well. DDoS attacks are essentially multiple devices (the Internet of Things, also known as IoT) or botnets targeting a site’s web server to overwhelm it with fake traffic.
Drive-By Download Attacks
When hackers have the capability of injecting malicious code into a site, they can take advantage of this by deploying malicious file downloads to a client’s operating system without their knowledge. These include some of the following:
- Trojan horses
- Ransomware
- Botnet toolkits
- Droppers
- Man in the Middle (MitM tools)
- Keyloggers
- Data transfer
What are the tips to keep sensitive data secure on the Internet?
First and foremost you’ll want to ensure all logins are secure. How do you create a secure login for your website? You can do this by ensuring administrator login panels aren’t predictable (I.E. using /wp-admin by default or “admin” as the primary username.) Enabling 2FA and CAPTCHAs will always be beneficial as well. Each account on your website should follow the Principle of Least Privilege. Making sure each password is strong and generated will also ensure if your password is ever obtained a hacker can’t use it elsewhere. Keeping these generated passwords in a password generator will also help you keep track of them all.
So what is the most secure way to store sensitive information? An SSL certificate will always be important for not only the site owner but the site visitor as well. Ensuring customer data in transit is encrypted is crucial online these days. However, an SSL isn’t the end all be all. Since it only protects data in transit, it isn’t protecting the data when it finally reaches the site, unlike a Web Application Firewall (WAF).
Scanning the site for malware and backing it up regularly is also important. Keeping up to date with the latest versions of software, themes, and plugins will also help avoid any infections as well. If you’re uncertain if an update is breaking the site, keeping it as a backup prior will also be helpful.
Conclusion
There’s certainly a variety of options a hacker can take advantage of depending on their intentions and motives against said target. With this in mind, it’s important to take proactive measures to avoid the impact on your business’s reputation. As a site visitor/consumer you should become more cautious of the sites you’re accessing in regards to your identity and privacy too.
If you think you’ve been a victim of one of these attacks please don’t hesitate to have it cleaned up as soon as possible. Infections that linger have the potential of not cross-contaminating other sites within the same hosting environment but are also detrimental to the site’s search engine rankings. Our incident response team is here to help if this is the case, providing 24/7 coverage when a malware removal request is submitted.