The criminal crypto world combines old and new ways to manipulate markets.
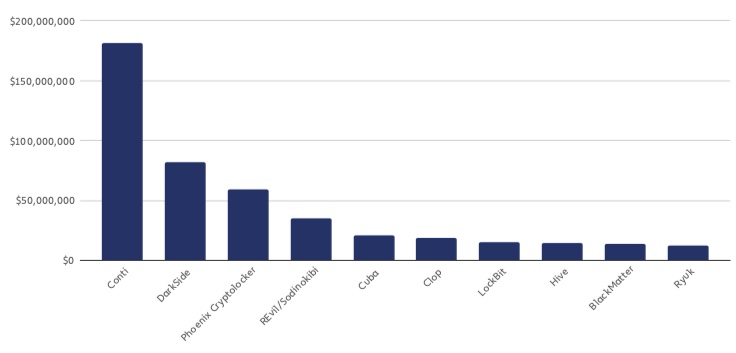
US President Joe Biden recently issued an executive order that will oversee various cryptocurrency efforts, including a study of whether there should be a virtual dollar-based cryptocoin, the efficacy of various future banking regulations for the Federal Reserve, and the roles for executive agencies including Treasury, Justice and Homeland Security on how to best manage crypto markets. Additionally, those of you who have already begun doing your US federal taxes might have noticed that the IRS now wants you to document your crypto holdings for the past year. These moves show that crypto is moving quickly into the mainstream. And with mainstream acceptance also comes the criminal element. Cryptocurrency-based crime hit new levels last year, doubling the amount collected from 2020 to $14 billion. According to a new report by Chainalysis, 2021 criminal crypto transaction volumes skyrocketed by more than six times what was seen in 2020. At the end of 2021, “criminals held $11 billion worth of funds with known illicit sources, compared to just $3 billion at the end of 2020.” What is interesting is that these transactions are originating from legitimate crypto addresses. Chainalysis might not be a familiar name, but their report is a detailed examination of how crypto crime does pay. The company also makes blockchain tracking tools: in one instance, their tool played a role in the FBI’s recovery of funds stolen during the Colonial Pipeline attack from last year, a story they describe in detail in their report. North Korean cybercriminals launched at least seven attacks using cryptocurrency platforms and extracted nearly $400 million worth of digital assets last year. These were carried out with various crypto laundering schemes that eventually moved the funds into hard currencies that were used to fund its weapons program. The report calls out two notable categories: Scamming revenue rose 82% in 2021 to $7.8 billion worth of cryptocurrency from victims, and outright theft brought in $3.2 billion worth of cryptocurrency in 2021, which was more than a six-times increase compared to 2020. The report documents a wide variety of techniques to steal these funds, including phishing private wallet keys, compromising various API keys to allow for malicious software injections, and diverting funds to criminal accounts. The criminal crypto world combines both old and new ways to manipulate markets, such as pump and dump techniques where exchange rates quickly rise and then fall. But there are some new techniques to note as well: But the crypto criminals can’t operate completely anonymously. The IRS Criminal Investigations unit announced that it had seized over $3.5 billion worth of cryptocurrency in 2021 — all from non-tax investigations. This points out that crypto is quite traceable and law enforcement can figure out the movement of funds from the blockchain and smart contract details, which aid in its recapture. This is true even for criminals that exploit “. In a case involving Manchester UK police, “officers used digital forensic analysis to discover a cryptocurrency nexus, and from there were able to analyze transactions on the blockchain to gain an understanding of the drug traffickers’ money laundering scheme, leading to successful prosecutions.” Not all criminals are alike in how long they hold onto their crypto funds: ransomware actors move their funds on average of 65 days, while darknet marketplaces tend to hold their funds for more than 250 days. We've written about various ransomware trends earlier: in this post, we documented how quickly the government responded to the Colonial Pipeline attack. One section of the Chainalysis report deals with the intersection of crypto and ransomware. Here you can see the most profitable ransom strains by the crypto revenue they have collected, where the Russian Conti group is far ahead of others. Security researcher Brian Krebs paints an almost-intimate portrait of the workers in the Russian Conti ransomware organization, how they evaded detection and capture by law enforcement and how they secured their various digital weapons. In this final of four posts on the group, he describes how they invested their ill-gotten gains and used additional schemes such as pump-and-dump and fake social media sites to manipulate crypto markets to increase their haul. At least 140 ransomware strains received payments from victims at any point in 2021, compared to 119 in 2020, and 79 in 2019. Iran and Russia-based groups have the largest collection of strains: 21 and 16, respectively. About 74% of ransomware revenue in 2021 — over $400 million worth of cryptocurrency — went to strains we can say are highly likely to be affiliated with Russia in some way (for example, Hackboss). The report found that 56% of funds sent from ransomware addresses since 2020 have wound up at one of six cryptocurrency businesses: While the 140-page report is a lengthy read, it's a great collection of data and a resource for IT and security professionals who want to learn more about these exploits.Destination of funds leaving illicit addresses by crime type in 2021
Ransomware trends
Top 10 ransomware strains by revenue in 2021
如有侵权请联系:admin#unsafe.sh