2022-4-12 15:30:0 Author: blog.avast.com(查看原文) 阅读量:23 收藏
Exploring concepts and technologies that are harbingers for a new way of protecting identities, data, and online interactions.
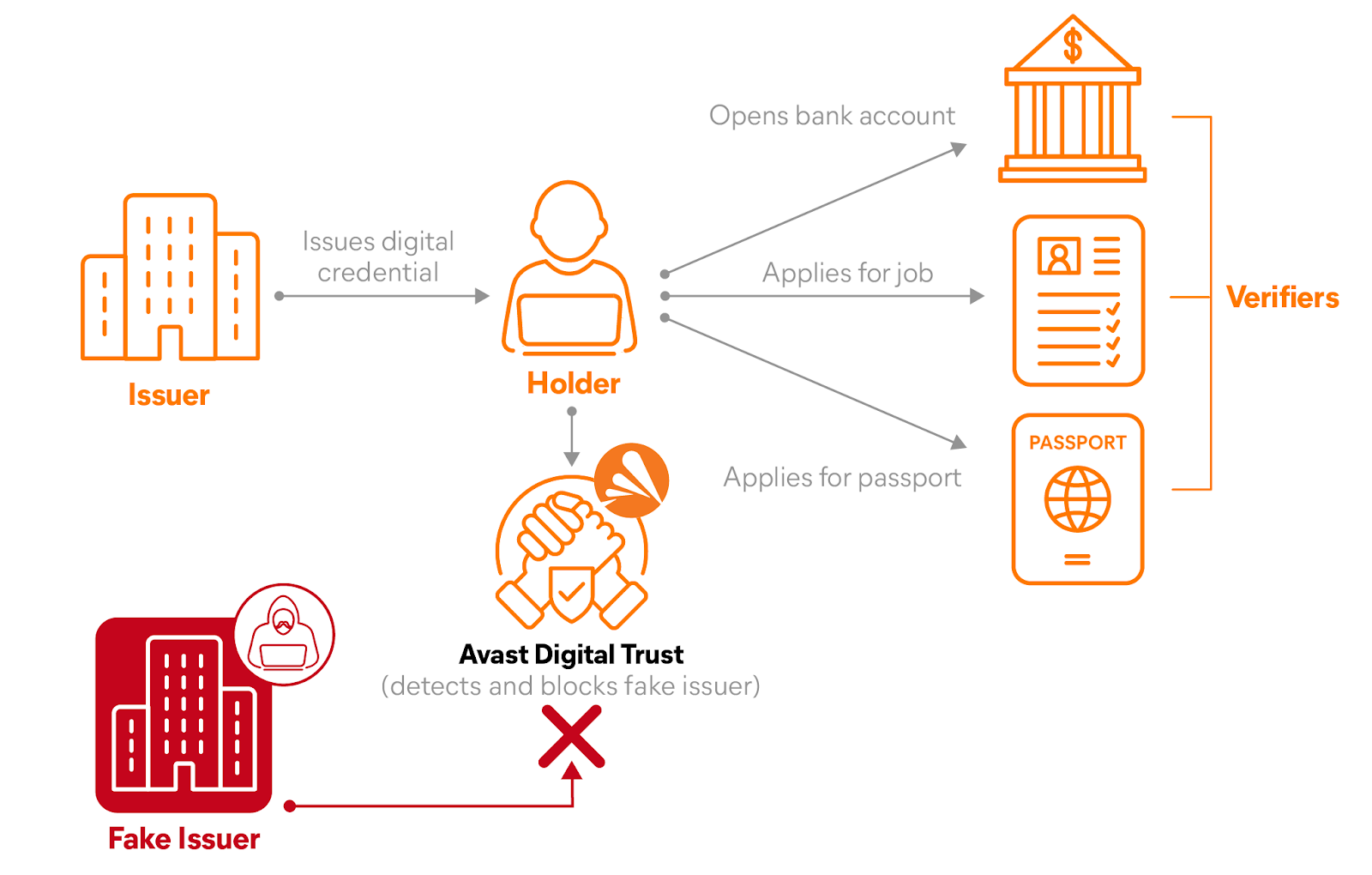
Today, most risks facing consumers from cyber criminals can be tied back to credential or data theft in some form. What if there was a future in which technology stopped this from happening? This blog explores concepts and technologies that are harbingers for a new way of protecting identities, data, and online interactions. Bad actors have spent many years perfecting mechanisms to reach their intended victims via email, messaging, websites, commercial sites hosting relevant private data etc. These various mechanisms, known as Tactics, Techniques and Procedures (TTPs) are increasingly employed to target interest groups, news groups, social media groups, topic level threads or in some cases individuals. As the cybersecurity industry grapples with the increasing sophistication of these targeting techniques, it feels very much like a whack-a-mole game where new methods of compromising accounts, stealing data, or defrauding individuals require security solutions to continuously adapt both where they’re employed but also the level of sophistication required to analyze and detect bad actor TTPs in action. Can self-sovereign identity infrastructure come to the rescue? Most definitely YES. First, let’s consider what self-sovereign identity is and some of its key benefits. Self-sovereign identity is not a single technology but a set of technologies and policies that are being introduced to allow individuals or businesses to take control of their data. For example, self-sovereign identity (SSI) technologies let you control what data to share with whom and how to share that data in a secure and private manner. In its most basic form, self-sovereign identity technology consists of 3 key elements: Figure 1 – Simplified Self-Sovereign Identity Roles The technology stack supporting self-sovereign identity architecture comprises decentralized identification and verifiable credentials specifications and standards such as those being designed at the Trust Over IP Foundation, World Wide Web Consortium, Hyperledger Foundation and the Decentralized Identity Foundation. Figure 1 highlights a future idealistic view of self-sovereign identity where compliance and trust between the issuers, holders and verifiers work seamlessly without having a centralized trust role being established. A more pragmatic and important role for SSI success will be the Legal, Compliance & Trust role as shown in Figure 2 below. Figure 2 - Self-Sovereign Identity Trust Architecture The key addition of the Trust & Compliance roles to the SSI architecture ensures that several important security functions can be supported including authorization of issuers and verifiers; validation and enforcement of legal compliance requirements across the ecosystem; and validation and security threat support across all entities within the architecture. The introduction of the governance authority is best depicted by the so-called Trust Diamond (shown below in Figure 3) where Issuer and Verifier rely on the authority to document the policies and rules that each agrees to follow in order to achieve their trust objectives. Figure 3 – Self-Sovereign Identity Trust Diamond With the introduction of a governance framework, an important role of Trust Registry, (shown in Figure 4), provides the vital interconnect between issuer and verifier. By registering qualified issuers, the trust registry provides an efficient mechanism for a verifier to confirm that an issuer is authorized to issue a specific type of credential or data. Conversely, by registering qualified verifiers, the trust registry provides a mechanism for holders to ensure they are sharing credentials or data with legitimate organizations (and not phishers). Figure 4 – Self-Sovereign Identity with Trust Registry & Governance Authority Without this key role of the SSI architecture, verifiers may be left exposed to threats from issuers acting outside of the governance framework. It also creates a strong incentive for organizations to comply with the governance framework’s policies to ensure correct treatment and handling of the holder’s data. Clearly, trust in such a distributed system as SSI portrayed in Figure 4 requires robust security mechanisms and systems to support it. In the remainder of this blog, we will look at how the SSI trust ecosystem can be attacked and how it can be protected. Typically, the technology under-pinning SSI supports secure, 1-1 communication channels between peers and organizations; prevents tracking and correlation of data by intermediaries or parties not involved in an exchange; and increases the confidence, security and privacy of the exchange by ensuring liveness, accuracy and verifiability of the data being exchanged. Self-sovereign identity has the promise to revolutionize how we protect data (= our lives) by significantly increasing the difficulty for bad actors to get to data or use data in a malicious act. How does this change the world of cybersecurity protection? Typically, bad actors approach cybersecurity attacks by developing solutions that exploit the attack vectors of their target victims. There are 4 attack vector categories to self-sovereign identity that map directly to each element: Issuer, Holder, Trust Registry and Verifier. “Illegal Passport Office A issues a new passport to Legitimate Joe who intends to use that passport for travel”. Figure 5 – Attack Vector Fake Issuer “Legitimate Passport Office B has been compromised and issues a legitimate passport for Bad Jack”. Figure 6 – Attack Vector Compromised Issuer “Legitimate Joe has a credit card credential that is stolen by Bad Jack”. Figure 7 – Attack Vector Stolen Data “Legitimate Joe has his birth date modified by Bad Jack so that when Legitimate Joe provides that information to another party it contains the modified date not the original date”. Figure 8 – Attack Vector Compromised Data “Bad Issuer stands up fake trust registry and redirects legitimate verifiers to their fake trust registry so that when verifiers check credentials issued can be verified as ‘trusted’” Figure 9 – Fake Trust Registry “Bad Jack compromises legitimate trust registry and adds a fake Issuer under their control to the list of approved issuers so that legitimate verification accepts the fake issuer” Figure 10 – Compromised Trust Registry “Bad Jack compromises a verifier site so that they can use the legitimate connection to the trust registry to learn about legitimate issuers to attack in a future campaign” Figure 11 – Fake or Compromised Verifier Profiling Legitimate Issuers “Illegal Business A asks to verify Legitimate Joe’s credit card information for the purposes of using it to make illegal purchases”. Figure 12 – Attack Vector Fake Verifier Compromising a legitimate verifier to learn or steal data “Legitimate Business A has been compromised by Bad Jack such that Bad Jack learns all legitimate data information from all customers doing business with Legitimate Business A”. Figure 13 – Attack Vector Compromised Verifier Before we cover each attack vector and the solution to those threats represented by the attack vectors, it’s important to highlight some of the Avast key technological capabilities supporting this architecture. The Avast Digital Identity capabilities include: In addition, this trust system allows Avast security capabilities to bring to bear the threat intelligence, threat analysis and threat mitigation across all aspects of consumer threat to supporting the security of the ecosystem. Figure 14 – Self-Sovereign Identity with Avast Digital Identity 1.a Fake Issuer Fake Data Avast Digital Trust – Web Guardian acting as a Trust verification system checks the certificates, checks the domain registration, checks the history, checks the privacy rule assessment of the site and the content interactions matching this role of issuer. Any risk associated with this assessment is flagged and mitigation becomes possible guided by the results of the risk assessment. Figure 15 – Solving Fake Issuer Fake Data Attacks 1.b Legitimate Issuer, Fake Data Avast Digital Trust – Web Guardian provides validated issuer information to verifiers such that they can determine when a credential is submitted to their service, they are able to check the validity of both the issuer and the credential being submitted. Figure 16 – Solving Compromised Issuer Attacks 2.a Legitimate Data, Fake Holder Avast Digital Trust - Identity Wallet is required to be part of the verification of data from the holder of the wallet and therefore data outside of the digital wallet is rendered useless to a bad actor. Figure 17 – Solving Digital Data Theft Attacks 2.b Legitimate Holder, Fake Data Avast Digital Trust - Identity Wallet receives data signed by the issuer such that data contained within the wallet and shared with verifiers cannot be changed without being flagged as an error by the digital signing infrastructure. Figure 18 – Solving Data Theft Attacks 3.a Fake Trust Registry, Fake Issuer Avast Digital Trust – Secure Domain Guardian checks ensures that the Verifier is provided a validated and verified domain resolution for the trust registry to ensure the verified is not being redirected by malicious DNS resolutions. Figure 19 – Solving Fake Trust Registry Attacks 3.b Compromised Trust Registry, Fake Issuer Avast Digital Trust - Web Guardian checks <same stuff as 1.a> and provides this information of validated and known bad issuers to verifiers so that they can double-check with results from the Trust Registry that the registry itself is not issuing compromised information. Figure 20 – Solving Compromised Trust Registry Attacks 3.c Compromised Verifier, Legitimate Trust Registry Avast Digital Trust – Threat Intelligence provides alerts on active threat actor campaigns targeting known issuers providing the Trust Registry provider with the ability to correlate lookups by verifiers on those issuers to assist in incident investigation of likely undetected verifier compromises. Figure 21 – Solving Compromised Verifiers Used as Attack Infrastructure 4.a Fake Verifier, Legitimate Data Avast Digital Trust - Web Guardian checks <same stuff as 1.a> and provides this information of validity to Avast Digital Identity where it determines whether to allow the digital wallet exchange to occur with this site. Figure 22 – Solving Fake Verifier Attacks 4.b Legitimate Verifier, Exposed Data Avast Digital Trust - Identity Wallet remains encrypted at rest as well as in motion. Without the keys to this encrypted data wallet, the data is not accessible outside of the holder<->verifier exchange. Figure 23 – Solving Compromised Verifier Attacks In summary, self-sovereign identity solutions are key elements of a future that provides increased security and risk protection for identities, data and online interactions. Subsequently, one of today’s biggest risks facing consumers from cyber criminals will be successfully mitigated. If you’d like to learn more about Avast’s vision for self-sovereign identity, please visit our website.
#1 - Attack vectors targeting data issuance
#2 - Attack vectors targeting data holders
#3 - Attack vectors targeting trust registry
#4 - Attack vectors targeting data verification
How does Avast solve these challenges?
如有侵权请联系:admin#unsafe.sh