You need a Wireshark tutorial? What do the data packets in the network mean?
The Wireshark hacking tool translates the code into readable parts, which this tutorial will bring you closer to.

Reading passwords with Wireshark
The Wireshark Network Sniffer is a network analysis tool that gives the network administrator deep insight into network activity. This tutorial is intended to explain to you bit by bit what you can read out of an Ethernet frame (file packet of the Internet).
What is Wireshark?
Wireshark is a network sniffer, Sniffing means “monitoring”, “investigating” or “spying”. Wireshark records every Internet packet (no matter what protocol or size) that arrives at your Ethernet connection. Network protocols are e.g. B.
- ICMP – exchange error messages in the network
- UDP – Fast packets for video and audio (streaming)
- TCP – HTML web pages
- RDP – Remote Desktop protocol for the transmission of screens
- ARP – Address Resolution Protocol for MAC resolution on the router
- NTP – time synchronization
- etc.
The protocols are necessary so that the recipient understands the user data and the communication works uniformly and independently of the platform.
Wireshark basics: ISO / OSI explained
Frame: The packet of 0s and 1s
If you look at an Ethernet frame in Wireshark, you will see the following text:

(Picture above) Let’s look at level 2 of the OSI model: The Frame tab shows information about the data packet that went over the line. The encapulation type is the type of “packet” that the PC received.
The receiver recognizes the frame with the frame number . In addition to this information, the protocol also contains the size of the packet ( frame length ) and the size it contains ( capture length ) .
The protocols are in frames such as e.g. B. IP, TCP, HTTP and urlencoded-form included. Wireshark visualizes the types of the application layer protocol with different colors: Green means that an HTTP protocol is present (HTTP port 80).
The physical MAC address from the screenshot indicates that the receiver and the transmitter must have an Asus motherboard (more precisely: BaseBoard Manufactur ASUSTeK COMPUTER INC. )
The first three octets of the MAC address are reserved for the manufacturer ( organizationally unique identifier ) and the last three octets are reserved for the network interface controller .
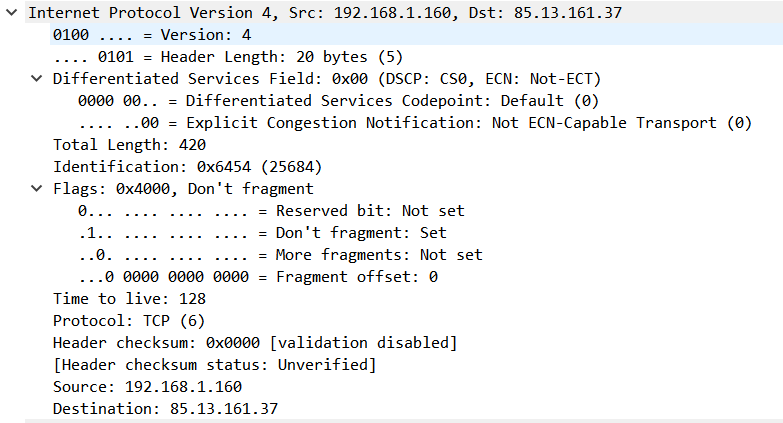
IP – The house number of your PC
This frame uses the legacy Internet Protocol (IP) version 4:

Version 4 has reached its limit of available addresses (4.2 billion addresses). In the early days of IP allocation, some organizations were given huge address spaces that were ” wasted ” in the process. Instead, version 6 uses the longer 128-bit addresses, which allow for a larger address space.
The number for Time To Live indicates the number of routers (hops or in seconds) that an IP packet is allowed to traverse. When the Time To Live has reached 0, the packet is deleted. The header checksum is a checksum that the network card can use to verify the correct transmission of the IP header.
The source and destination IP addresses (receiver and sender) are specified in the Source and Destination fields.
TCP – pays attention to completeness, sequence and correctness
The TCP contains functions that are used to…
- security
- integrity
- reliability
are used for transmission. The TCP begins with the port numbers (compare to a house with multiple front doors) and the sequence numbers of the TCP packet.

The transmitter split a frame into many pieces ( sequences ).
In order to assign them correctly, the recipient must assemble the TCP packets according to the order of the sequence number. The TCP packet confirms receipt of a packet with the Piggy-Backing ( Acknowledgment Number ) from the receiver.
To verify that the recipient received the frame correctly , a checksum verifies the packet (similar to a hash value) for correctness.
HTTP – Oh! The user sees something
The HTTP protocol is part of the application layer of the ISO/OSI model.
This request shows a POST request . The browser sends form data to the server. The admin-ajax.php processes the data on the server.

Under Host you will find the called DNS server . The User-Agent field contains the essential information about the browser used that made the request.
The transmission of the browser is important so that the server should transmit a web page without JavaScript with an old Internet Explorer . Microsoft suppresses client script language execution in older versions of Internet Explorer.
The content type tells the server how to encode or understand the user data. If this line is missing, a CORS problem can quickly arise.
UTF-8 represents the character set for this document. The widespread character set UTF-8 consists of up to four-byte codes with e.g. B. the characters like a,+,&,ö,p.
User data – The golden core of every package
This section displays the data of a form .
X-www-form-urlencoded is a MIME type. The Multi-Internet-Mail-Extensions (MIME) are the extensions of the classic mail. The sender can attach MIME videos, images and other attachments to an email.

sniffing passwords with Wireshark
The analysis options shown leave room for hackers to attack .
For example, hackers can read passwords and usernames via HTTP. The password strings are masked with Base64 only. Any browser can convert these strings.
The hacker learns a lot about the technologies used and can test a known vulnerability on the victim. The sniffer learns the following about the internet user:
- The user uses Mozilla as Firefox ,…
- which runs on Windows 10
- and has an Asus motherboard
- likes to call up page X, Y, Z
- etc.
Security: Don’t give sniffers a chance
Every user should pay attention to an encrypted connection . This is a good security against nosy sniffers. These can only recognize a salad of characters that cannot be converted into plain text.
Encryptions come to the rescue
Use a VPN
Use TSL (formerly SSL)!
Avoid using a banking app on your phone and instead use your laptop/desktop PC with its own internet connection and an antivirus sandbox .