Our research and remediation teams have noticed an increase in WooCommerce credit card skimmers on client sites over the past few years, as detailed in past blog posts.
Due to the increased number of plugins and components facilitating online payments and its ease of use, WordPress has become a common e-commerce platform — and the frequency in which the popular CMS is being targeted by attackers aiming to steal sensitive personal information and credit card details is also accelerating.
We recently uncovered a case where a credit card swiper had been injected into WordPress’ wp-settings.php file. The only symptom our customer reported was that images were disappearing from the WooCommerce cart almost as soon as they were uploaded.
Examining the Malware
Taking a look at wp-settings.php, we could see the following include statement.
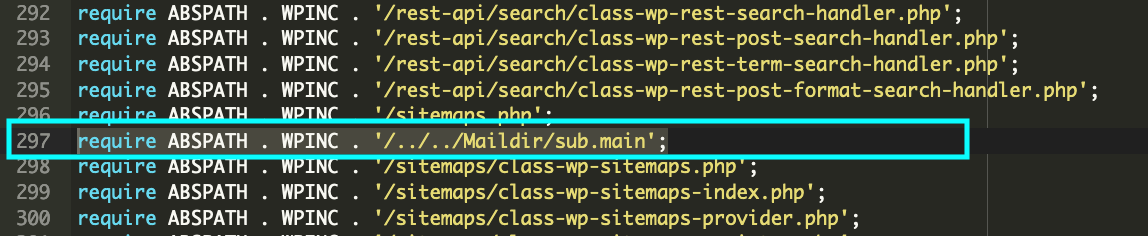
Because the include was buried deep down into the file, it was easy to miss on a casual review. Additionally, because the include itself does not follow any malware patterns, it could be missed by malware scanners looking for specific signatures. Furthermore, because the malicious file being included was located above the site directory, a cursory scan of the site files would have also missed that.
Attackers often like to place malicious content out of the way so it is more difficult to detect. One tactic they use is to create directories that look like system directories, or to place malware in existing core CPanel or other server directories.
Taking a look at ../../Maildir/sub.main, we found over 150 lines of code which had been obfuscated with str_rot13 and base64. Here is an example from the beginning of the file.
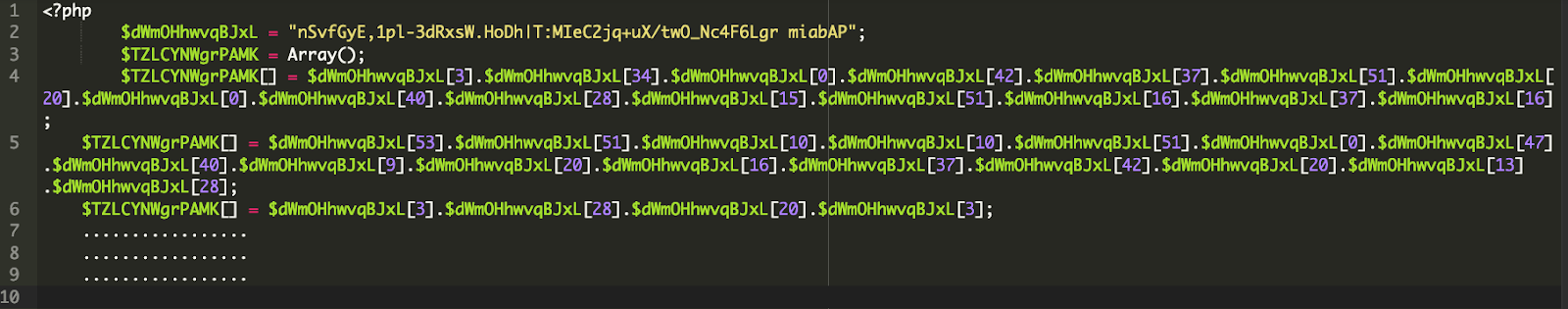
After decoding the entire file, we found additional obfuscated content — most importantly, right at the top of the decoded output, we found functions to store credit card data concealed in the wp-content/uploads/highend/dyncamic.jpg image file.
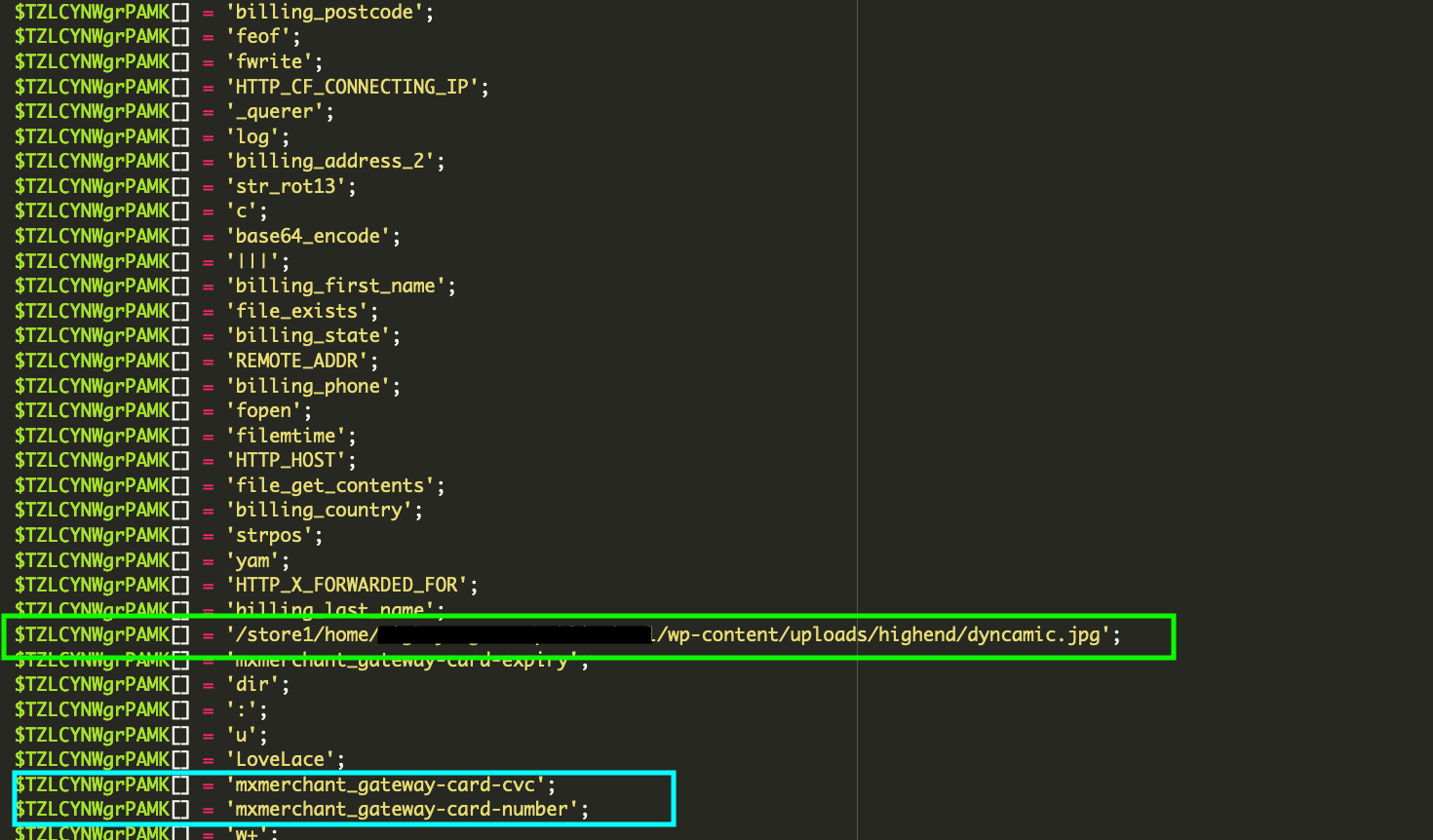
Upon inspection, we could see several additional lines of obfuscated data.

When decoded, that data revealed not only credit card details submitted to the site, but also admin credentials to the site’s backend. We ran a couple of test transactions against the site to confirm the behavior and, sure enough, our test data had been logged in the image file.
This is not the first time that we have seen attackers export stolen credit card details to image files. This begs the question: Why? There are a couple reasons why this is a useful tactic. For starters, it makes it very easy for the attackers to download the stolen details in their browser or a console. Secondly, most website/server malware detection scans focus on website file extensions such as PHP, JS, and HTML. Image files, particularly those in a wp-content/uploads sub-directories, can sometimes be overlooked.
Conclusion & Mitigation Steps
This infection is a great example of the importance of running frequent core file integrity checks, as well as monitoring your environment for any file changes. Most WordPress security plugins will include core file consistency checks. Since most core files shouldn’t change unless you have upgraded your WordPress version, any changes to the core files should be treated as suspicious and could indicate malware. If you don’t have one already, make sure to get file integrity monitoring installed on your site!
It’s also worth noting that you should always keep your plugins and themes up to date. If you have any plugins or themes installed that are not being used you should also remove them, even if they are updated. Attackers are always looking for weak points and just because a vulnerability has not been documented does not mean one does not exist.
By default, WordPress allows the editing of files directly from the wp-admin dashboard. This makes it convenient to modify your website, but makes it equally convenient for attackers to place their payload. Adding some additional authentication requirements on your admin panel is essential for maintaining a secure website.
We encourage you to regularly review the administrators accounts in your site, and change your admin passwords. You can refer to our detailed post which describes password security best practices to protect your website.
If you suspect that your site has been infected, you can sign up for our website firewall and remediation services.
