The FBI has published its annual report on Internet crime. Qualys has analyzed its trends and statistics. In this post, we review our findings, especially with regards to the prevalence of Ransomware, and our recommendations for actions that enterprises should take to mitigate their risk.
Every year the U.S. Federal Bureau of Investigation publishes an Internet crime report which summarizes its insights on trends and threats from cybercriminals based on all cybercrimes reported to the FBI by the American public. This annual report provides fascinating insights into the threat landscape, key trends, statistics on types of crimes, the real losses resulting from them, and perhaps most importantly, key insights into how cybercriminals operate so that we can better prepare to guard against them.
For 2021 the FBI reported 5 key threats:
- Business Email Compromise (BEC)
- Confidence Fraud / Romance Scams
- Cryptocurrency
- Ransomware
- Tech Support Fraud
Of these threats, only ransomware complaints continue to rise. Ransomware reports increased by almost 51% compared to 2020.
These complaints resulted in a total of $50 million in losses in 2021, compared to $30 million in 2020—a 66% rise in total losses. Ransomware attacks hit more than 290 enterprises in 2021, including major organizations like Colonial Pipeline, Accenture, Acer, and others.
Top Ransomware Attack Vectors of 2021
Ransomware tactics and techniques are evolving continuously, allowing attackers to make their exploits more sophisticated, resulting in an increasing ransomware threat to organizations globally. Although cybercriminals use a variety of techniques to infect victims with ransomware, the top three initial infection vectors reported remain phishing emails, Remote Desktop Protocol (RDP) exploitation, and software vulnerabilities.
Get instant visibility into ransomware exposure with Qualys Cloud Platform
Top Ransomware Variants Exploited Vulnerabilities
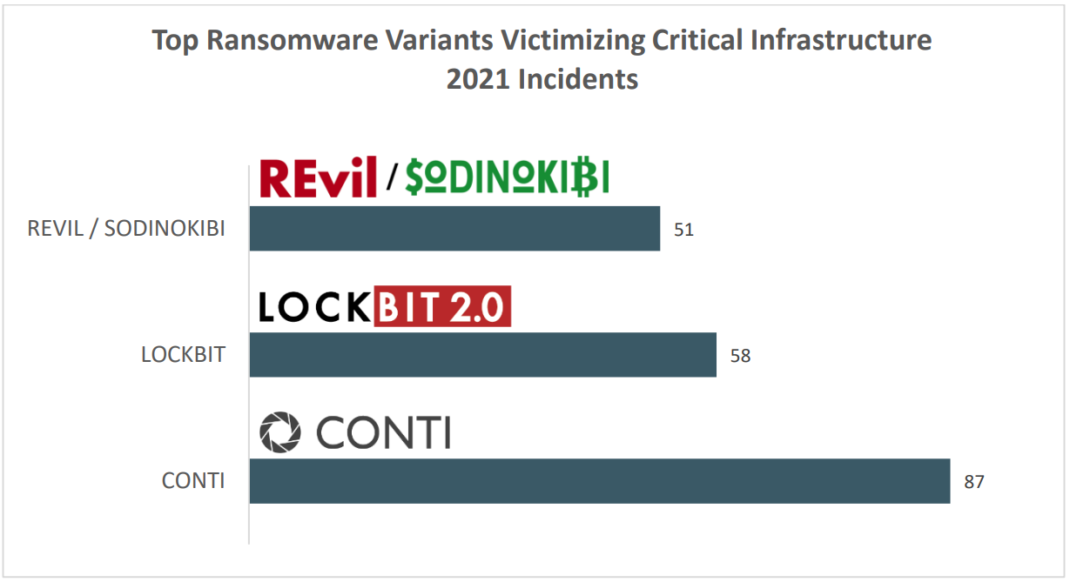
The FBI’s investigations isolated the top 3 ransomware variants that victims suffered: CONTI, LockBit, and REvil/Sodinokibi. The chart below tallies the number of incidents reported for each variant:

The report states, “According to information submitted to the Internet Crime Complaint Center (IC3), CONTI most frequently victimized the Critical Manufacturing, Commercial Facilities, and Food and Agriculture sectors. LockBit most frequently victimized the Government Facilities, Healthcare/Public Health, and Financial Services sectors. REvil/Sodinokibi most frequently victimized Financial Services, Information Technology, and Healthcare/Public Health sectors.“
The increase in remote work due to the Pandemic made four specific infection vectors more popular. Typical delivery methods for these ransomware variants were:
- Spear phishing – campaigns using tailored emails that contain malicious attachments or malicious links
- Remote Desktop Protocol (RDP) credentials that are either stolen or weak
- Fake software promoted via search engine optimization that tempts users to install
- Common vulnerabilities exploited in external IT assets
Here are a few examples of vulnerabilities exploited in 2021 to launch successful ransomware attacks.
Conti
- “PrintNightmare” vulnerability (CVE-2021-34527) in Windows Print spooler service
- “Zerologon” vulnerability (CVE-2020-1472) in Microsoft Active Directory Domain Controller systems
LockBit
- CVE-2021-22986 is a critical unauthenticated, remote code execution vulnerability in the iControl REST interface, affecting BIG-IP and BIG-IQ products. It was used in the Accenture attack.
REvil/Sodinokibi
- CVE-2018-8453 vulnerability is exploited to elevate privileges
Recommended Ransomware Mitigations
Update your operating system and software
Internet-facing servers should be patched for known vulnerabilities regularly, as well as software processing internet data such as web browsers, browser plugins, and document readers. Software and operating systems should be upgraded regularly to the latest available version. The highest priority should be patching software and operating systems running versions that vendors no longer support.
Implement user training and phishing exercises to raise awareness about the risks of suspicious links and attachments. Do not click on suspicious links!
User training has been proven to teach employees to avoid ransomware attacks from phishing and fake software.
If you use Remote Desktop Protocol (RDP), secure and monitor it
Limit access to resources over internal networks and monitor RDP access logs. Ensure devices are properly configured, and security features are enabled.
Make an offline backup of your data
Regularly run and maintain offline encrypted backups, then test them. Review the backup schedule of your organization and consider the possible backup disruption risk during weekends and holidays.
Use strong passwords
Ensure you have a strongly defined password policy, and ensure it is followed across the organization.
Use multi-factor authentication
Apply multi-factor authentication (MFA) for all services to the extent possible, particularly for remote access, virtual private networks, and accounts that access critical systems.
Secure your network(s): implement segmentation, filter traffic, and scan ports
The most critical communications should be occurring in the most secure and reliable layer. Filter network traffic to prohibit ingress and egress communications with known malicious IP addresses.
Blacklist the malicious URLs/websites. Scan networks for open and listening ports regularly and close those that are unnecessary.
How Can Qualys Help?
Comprehensive Visibility into Critical Ransomware Risk Exposure
Getting a complete view of your ransomware risk exposure is a big challenge. Qualys VMDR helps you gain comprehensive visibility into the vulnerabilities, misconfiguration postures, and unauthorized software installed on all assets across your enterprise. Along with that, you gain visibility into available patches and can deploy these patches on the assets impacted. Our dashboard provides a glimpse of critical ransomware risk exposure across your enterprise in one unified console.

Continuous Detection & Prioritization for Ransomware-specific Vulnerabilities
The first step toward securing your devices from ransomware is to get complete visibility of all assets in your organization. Qualys CSAM provides “single pane of glass” visibility of all asset types and helps to eliminate any blind spots. You also get visibility into unmanaged assets
The FBI’s 2021 report clarifies that exploitation of software vulnerabilities remains one of the top three initial infection vectors for ransomware incidents. Most noteworthy is that the top vulnerabilities are exploited using fake software and/or software versions no longer supported by the vendor. CSAM provides visibility into unauthorized and end-of-life software. An unauthorized software list helps you identify fake software that has been installed from unknown sources.
Get instant visibility into ransomware exposure with Qualys Cloud Platform
Qualys VMDR helps you to monitor and detect ransomware vulnerabilities continuously. You can view the ransomware vulnerabilities detected on assets on which unauthorized software is running using Qualys Query Language (QQL):
Asset dropdown -software:(authorization:Unauthorized)
Vulnerability dropdown -vulnerabilities.vulnerability.threatIntel.ransomware:true

You can also identify all of the assets on which 2021’s top three ransomware variants are detected: CONTI, LockBit, and REvil/Sodinokibi.
QQL details are:
(vulnerabilities.vulnerability.threatIntel.ransomware:true)and (vulnerabilities.vulnerability.ransomware.name:[REvil/Sodinokibi,Ryuk/Conti,lockBit])

Using Qualys VMDR prioritization, ransomware vulnerabilities can be easily prioritized by using “Ransomware” in the Real-Time Threat Indicator (RTI) filter section:

Along with vulnerabilities, Qualys VMDR also keeps you up to date on evolving threats via its ‘Live Threat Feed’, which can help with prioritization. The “Live Threat Feed” provides visibility of high, medium, and low-rate feeds along with a count of the impacted assets. Click on the count to view more details about the impacted assets.
In the “Threat Feed” tab, search using
contents:ransomware
to find all threats associated with ransomware.

Discover and Mitigate Ransomware Misconfigurations
Misconfigurations often play a vital role in ransomware attacks, as they might help the attacker gain access to your assets. Qualys Policy Compliance provides comprehensive visibility into ransomware misconfigurations. The Ransomware Best Practices policy contains the critical controls mapped to MITRE ATT&CK mitigations as well as tactics recommended by CISA and best practices published by Fireye Mandiant. These mitigations are effective across top techniques and can potentially reduce the risk of ransomware attacks. These critical controls can limit attackers’ initial access and lateral movement around your network.
Apply this ransomware policy to all assets across your enterprise to ensure that all assets are correctly configured. You can automate the configurations assessment and apply this to the golden images to confirm your security baselines before distribution.
Qualys Policy Compliance helps you to configure the recommended mitigations for the password, RDP, network security policy, and software update by applying the ransomware policies on the impacted assets.

Automated Effortless Patching for Ransomware Vulnerabilities
Qualys zero-touch patching helps you automatically patch new ransomware-related vulnerabilities that are being actively exploited in attacks. It is faster and more accurate than manual patching and helps to patch up to 97% of ransomware vulnerabilities.
Qualys Patch Management provides a more efficient and effective way to proactively patch detected ransomware vulnerabilities. Qualys VMDR helps prioritize the ransomware vulnerabilities that Qualys PM executes. This tight integration enables you to initiate patch jobs directly from the Prioritization tab. Quick patching of critical ransomware vulnerabilities reduces ransomware risk. Auto-correlation of patches against the ransomware vulnerabilities detected reduces your overall remediation time and makes the IT team’s job easier.

Ready to hear more? For more details, watch this video on our Ransomware offering. Then try out our Ransomware Risk Assessment & Remediation Service at no cost for 60 days. Uncover your organization’s level of exposure and create a prescribed patch plan to reduce your ransomware risk.
Get instant visibility into ransomware exposure with Qualys Cloud Platform