On May 5, 2022, MITRE published CVE-2022-1388, an authentication bypass vulnerability in the BIG-IP modules affecting the iControl REST component. The vulnerability was assigned a CVSSv3 score of 9.8
The vulnerability was discovered internally by the F5 security team and there is no evidence of whether it’s exploited publicly. There is no publicly available proof of concept at the time of writing this blog post. Newly discovered BIG-IP vulnerability affects the following product and versions:
BIG-IP (all modules):
- 16.1.0 – 16.1.2
- 15.1.0 – 15.1.5
- 14.1.0 – 14.1.4
- 13.1.0 – 13.1.4
- 12.1.0 – 12.1.6 (Won’t fix)
- 11.6.1 – 11.6.5 (Won’t fix)
F5 Big-IP Remote Code Execution Detection
Do you want to find out if you are vulnerable to CVE-2022-1388? You might want to take a look at some of the tools we will mention below:
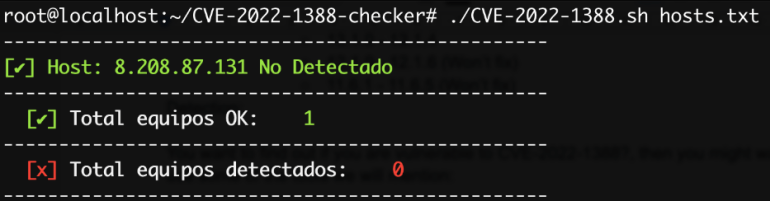
Bash script that checks for the existence of CVE-2022-1388 (https://github.com/jheeree/CVE-2022-1388-checker):

Nuclei template to detect CVE-2022-1388 (https://github.com/MrCl0wnLab/Nuclei-Template-CVE-2022-1388-BIG-IP-iControl-REST-Exposed)

Patches for the CVE-2022-1388 have been published on F5’s website. You can fix the vulnerability by installing a version listed on the website.
If it’s not possible for you to install a fix, for now, you can instructions listed on the F5’s website in the Mitigation part.
When using Wallarm in blocking mode, these attacks will be automatically blocked. No actions are required.
When using a monitoring mode, we suggest creating a virtual patch. Feel free to reach out to [email protected] if you need assistance.
Subscribe for the latest news