Be aware of dangerous phishing scams, including sugar daddy scams, sextortion emails, and more.
With more people looking to cash in on hype surrounding the cryptocurrency market than ever before and an increasing digital workforce which may lack awareness of network security set-ups, cybercriminal activity remains rampant. Bitcoin’s enduring popularity and peak valuation in 2021 has only encouraged heists on crypto exchanges, the use of cryptomining malware, cryptocurrency-related scams, and malware targeting cryptocurrency wallets. From fans of the K-Pop band BTS being tricked into following crypto-related Twitter handles to fake initial coin offerings (ICOs), the popularity of cryptocurrency provides scammers with many opportunities. With global ransomware attacks up 32% on businesses and 38% on individuals from last year, companies that fail to use security tools like two-factor authentication or properly configure their VPNs could be especially at risk. Compared to past scattershot approaches, there is a concerted effort by cybercriminals to go after larger, more valuable targets by using advanced techniques like deepfaking audio from employees, managers, and executives. Other examples of trending cybercrime include fake parcel delivery services to acquire personal information, sextortion scams that prey on the target’s guilt and social standing, and ever-classic tech support scams. However, what many of these techniques effectively boil down to is an ever-evolving family of hacking strategies known as phishing. Similar to the outdoor sport that it’s named after, phishing describes a set of activities in which a scam artist attempts to get you to divulge sensitive personal information through various forms of deception. Once obtained, the scam artist will use or sell your information to enrich themselves or use it to bolster more advanced scamming strategies. Thankfully, phishing scams and their most popular variations can be recognized and prevented with knowledge and awareness. Avast can help by keeping you up to date on the most popular types of phishing, other prominent phishing scams, what to look for, and how to keep yourself and your data safe. Our Global PC Risk Report examines threats from a range of sources, both at home and in the workplace. Phishing scams are often focused on a large group because at least one member will be tricked into placing themselves on the “hook”. However, rather than focusing on a particular target, basic phishing casts a vast net by using tools such as emails with malicious attachments included, social media messages, SMS, phone calls, and even creating fake websites for companies and organizations. Once the prospective victim opens the corrupted file or link, the scammer uses this opportunity to obtain personal or financial information, download malware onto their PC, steal their identity, and so on. Much like the previous analogy on phishing, spear phishing requires a lot of dedication and a single-minded focus on your target. Ideally, by the time your quarry is aware of your intentions, it's already far too late to react. However, as opposed to the comprehensive approach taken by generic phishing, spear phishing involves an extraordinarily realistic and well-crafted effort to compromise the information security of specific individuals or organizations. Furthermore, spear phishing scams can be challenging to detect and prevent because of the effort to make them appear as plausible and credible as possible. Targets of whaling tend to be figures of immense political, financial, and social status. When considering the level of wealth and influence of a given whale, it is improbable that even more technologically advanced tactics like faking email addresses or creating a fake website will be successful. So instead, a common tactic is getting the whale to submit an artificial tax form full of priceless information, including Social Security numbers, bank account details, addresses, legal names, and much more. A new update to a classic scam, vishing involves using Voice Over Internet Protocol (VoIP) to spoof phone numbers from family, friends, loved ones, businesses, government officials, and more. Through impersonating such figures, scammers will attempt to get the victim to divulge valuable information, purchase gift cards or money orders, raise bail money, collect on owed back taxes, or any number of other pretenses. Unfortunately, many victims of this tactic tend to be either in their advanced years or simply unfamiliar with cutting-edge technology, leaving them vulnerable to phishing scams that rely on their emotional connections. This tactic is commonly used for short-term financial gain and long-term projects like identity theft, making vishing a valuable tool in the scam artist's toolbox. For those unfamiliar, the phrase "sugar daddy" refers to the act of an older and wealthier individual effectively purchasing the love and affection of a younger partner. Sugar daddy scams are designed to exploit young women in precarious financial situations or those looking to achieve an otherwise unobtainable standard of living. Primarily carried out on social media platforms, these cybercriminals open conversations with prospective victims by offering a weekly or monthly allowance for companionship. However, before they can begin to receive such an allowance, the victim must first share information for their Venmo, PayPal or other online payment accounts and deposit a sum in the scammer's account for "verification." This scam can be especially devastating for the victims who may not seek any assistance due to the illicit or embarrassing nature of such relationships. Much like the previous category of scams, sextortion is notorious for the disastrous real-world consequences it can wreak, including several cases of suicide involving victims of just such a blackmail scheme. Like vishing, sextortion depends on the victim not being familiar with technology and relies on social engineering techniques to intimidate victims into giving up valuable information or making regular payments. This scam generally starts with an email containing digital footage or images of the victim using their webcam, screenshots of their computer screen, and other compromising pictures and information. Schemers convince the victim that they own the photos or recordings and threaten to send them to their friends, family, and employers or start spreading them across various social media platforms. Such scammers are almost always bluffing, but many victims are unwilling to risk refusing their demands when facing 48-hour deadlines to pay blackmail or be exposed. Regardless of the long-term performance of the cryptocurrency market, one indisputable fact is that scammers will not be far behind where cryptocurrency goes. Prominent examples of cryptocurrency scams include spoofing tweets from major crypto promoters to infiltrating entire communities built around cryptocurrency before robbing them blind. Fortunately, one of the easiest (and cheapest) ways to avoid falling for a cryptocurrency scam is to use your best judgment. If it sounds too good to be true, it probably is.. Other effective scam prevention methods include the use of multi-factor authentication services for online crypto wallets and avoiding conducting trades via your mobile device. As antivirus and anti-malware protections continue to strengthen and improve, phishing scammers are forced into becoming equally creative in their attempts to separate you from money, valuable data, and even your identity. Although the exact methods vary from scammer to scammer, there are commonly used tricks that phishers will employ though both email and SMS: Fortunately, there are things you can do in your daily online activities to help prevent yourself from being phished, including: Like many forms of intimidation, scams like these are most effective when their victims are too afraid or embarrassed to speak out. However, by having the courage and bravery to share your story with others, you can help prevent it from happening to someone else. If you have been a victim of cybercriminals or online scammers, Avast has excellent resources to help you report the scam to the relevant authorities in both the U.S. and U.K. so you can get the help you deserve. Depending on the type and scale of a phishing scam, it will likely be necessary to involve the relevant authorities by officially reporting the fraud. In the United States, you should start by reporting a phishing scam to your local police department to determine if a particular region is being targeted. Additionally, you should also avail yourself of resources such as your State Consumer Protection Office to file an official complaint. Finally, there are several federal agencies to contact based on the severity of the scam’s impact, including the FTC, DOJ, BBB, ICCC, and even the FBI.Phishing
Spear phishing
Whaling
Vishing
Sugar daddy scams
Sextortion email scams
Cryptocurrency scams
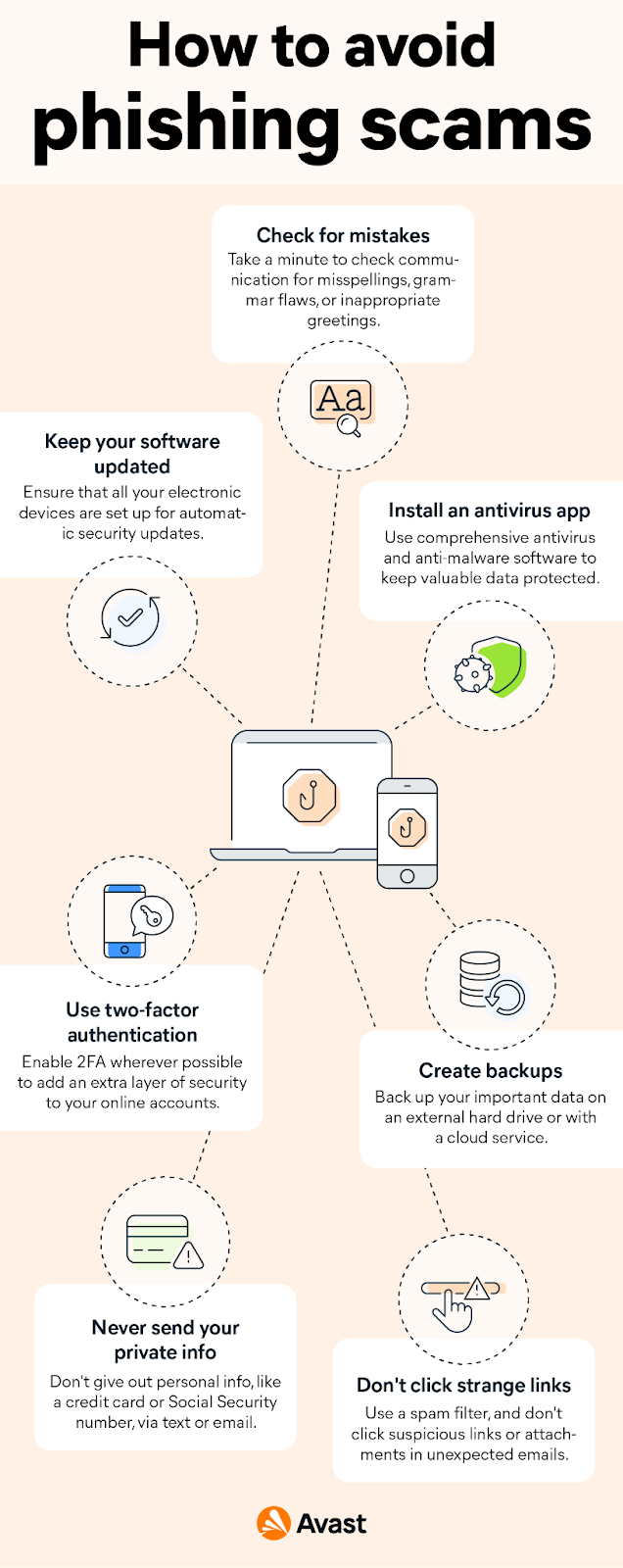
Tips for avoiding phishing scams
How to report scams
如有侵权请联系:admin#unsafe.sh