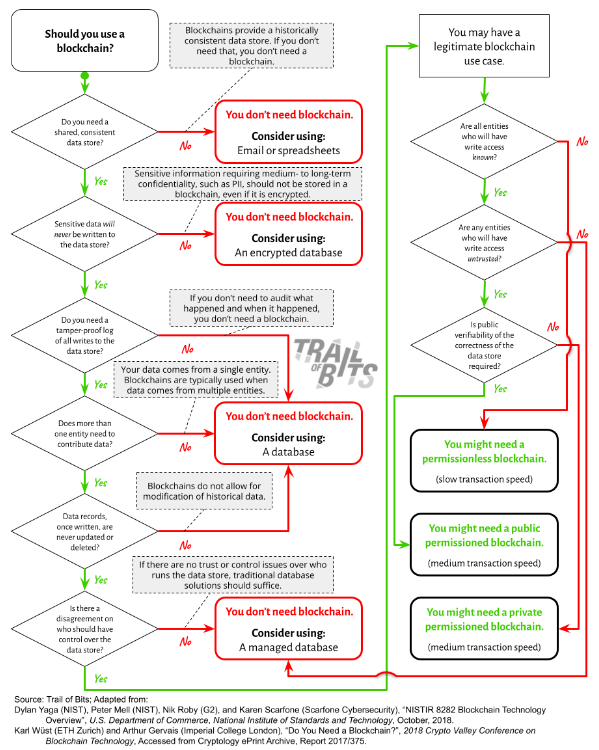
Do you need a blockchain? And if so, what kind?
Trail of Bits has released an operational risk assessment report on blockchain technology. As more businesses consider the innovative advantages of blockchains and, more generally, distributed ledger technologies (DLT), executives must decide whether and how to adopt them. Organizations adopting these systems must understand and mitigate the risks associated with operating a blockchain service organization, managing wallets and encryption keys, relying on external providers of APIs, and many other related topics. This report is intended to provide decision-makers with the context necessary to assess these risks and plan to mitigate them.
In the report, we cover the current state, use cases, and deficiencies of blockchains. We survey the common pitfalls, failures, and vulnerabilities that we’ve observed as leaders in the field of blockchain assessment, security tooling, and formal verification.
Blockchains have significantly different constraints, security properties, and resource requirements than traditional data storage alternatives. The diversity of blockchain types and features can make it challenging to decide whether a blockchain is an appropriate technical solution for a given problem and, if so, which type of blockchain to use. To help readers make such decisions, the report contains written and graphical resources, including a decision tree, comparison tables, and a risk/impact matrix.
Goldman Sachs partnered with Trail of Bits in 2018 to create a Cryptocurrency Risk Framework. This report applies and updates some of the results from that study. It also includes information included in a project that Trail of Bits completed for the Defense Advanced Research Projects Agency (DARPA) to examine the fundamental properties of blockchains and the cybersecurity risks associated with them.
Key insights
Here are some of the key insights from our research:
- Proof-of-work technology and its risks are relatively well understood compared to newer consensus mechanisms like proof of stake, proof of authority, and proof of burn.
- The foremost risk is “the storage problem.” It is not the storage of cryptocurrency, but rather the storage of the cryptographic private keys that control the ownership of an address (account). Disclosure of, or even momentary loss of control over, the keys can result in the complete and immediate loss of that address’s funds.
- Specialized key-storing hardware, either a hardware security module (HSM) or hardware wallet, is an effective security control when designed and used properly, but current hardware solutions are less than perfect.
- Compartmentalization of funds and multisignature wallets are also effective security controls and complement the use of HSMs.
- Security breaches or outages at third-party API providers represent a secondary risk, which is best mitigated by contingency planning.
- Centralization of mining power is a systemic risk whose impact is less clear but important to monitor; it represents a potential for blockchain manipulation and, therefore, currency manipulation.
- Most blockchain software, though open source, has not been formally assessed by reputable application-security teams. Commission regular security reviews to assess blockchain software for traditional vulnerabilities. Use network segmentation to prevent blockchain software from being exposed to potentially exploitable vulnerabilities.
It is our hope that this report can be used as a community resource to inform and encourage organizations pursuing blockchain strategies to do so in a manner that is effective and safe.
This research was conducted by Trail of Bits based upon work supported by DARPA under Contract No. HR001120C0084 (Distribution Statement A, Approved for Public Release: Distribution Unlimited). Any opinions, findings and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the United States Government or DARPA.