The AnonymousFox hack targets insecure websites and actively exploits them to spread phishing, spam, and other malware. A major nuisance for website owners, it also happens to be one of the more prevalent types of malware seen on client sites in the past two years.
In this post we’ll describe what AnonymousFox is and how it works, describe common indicators of compromise, and outline the steps you can take to mitigate risk of an infection.
What is AnonymousFox?
The name AnonymousFox is used to describe a suite of automated tools used by hackers to target and exploit victim’s websites — and also happens to belong to the threat actor group that develops and distributes it.
The AnonymousFox tool kit is packed with a plethora of features that make it easy for attackers to identify potential victims, compromise website environments, and exploit resources.
A number of complex tools are available for the kit, including those used to identify targets, exploit vulnerable access points, reinfect compromised environments, and make removal more challenging for website owners.
Who is a target for AnonymousFox?
The tools found in AnonymousFox are designed to target a wide range of known vulnerabilities and insecure default configurations found in popular CMS’ and hosting software — which may help explain why it’s become so successful.
Since WordPress happens to be the most popular platform for developing websites, it is targeted and affected by this malware the most. But regardless of whether you’re an avid WordPress, Joomla, Opencart, or Drupal user — it’s quite likely that your website has already been probed by this malware many times in the past year in search of potential vulnerabilities.
How does the AnonymousFox attack work?
There’s a variety of ways that AnonymousFox can target and exploit an environment, but since WordPress happens to be the most popular CMS, we’ll describe one of many possible scenarios for a typical insecure WordPress website.
- Attacker uses AnonymousFox tools to scan millions of websites for plugin vulnerabilities or insecure admin panels.
- Target is identified.
- Attack is launched against the target website to exploit a known vulnerability.
- Unauthorized access is gained.
- File manager plugin is installed and malicious web shell uploaded to compromised website.
- The /home/user/.cpanel/contactinfo and /home/user/.contactemail files are modified to include the attacker’s email address.
- Password reset is sent to the attacker’s account.
- Unauthorized access is obtained to cPanel.
- Secondary accounts get created.
This is only just the beginning. Once the website is compromised, attackers regularly sell the hacked website resources on marketplaces — allowing other attackers to also access these compromised cPanels, webshells, and SMTPs or PHP mailers.
Our next step is to examine some of the common ways attackers exploit the environments using AnonymousFox.
What are the signs of an AnonymousFox infection?
AnonymousFox infections are most commonly associated with phishing payloads, spam, and redirects to scam or malware sites. That being said, there are a couple of key indicators to look out for.
Let’s dive into some common signs of an AnonymousFox infection.
Malicious plugins
Attackers regularly install malicious plugins using compromised admin accounts.
These plugins often have randomized names and contain malicious scripts for backdoors, web shells, and automated attacks to distribute malware throughout the rest of the environment and maintain unauthorized access.
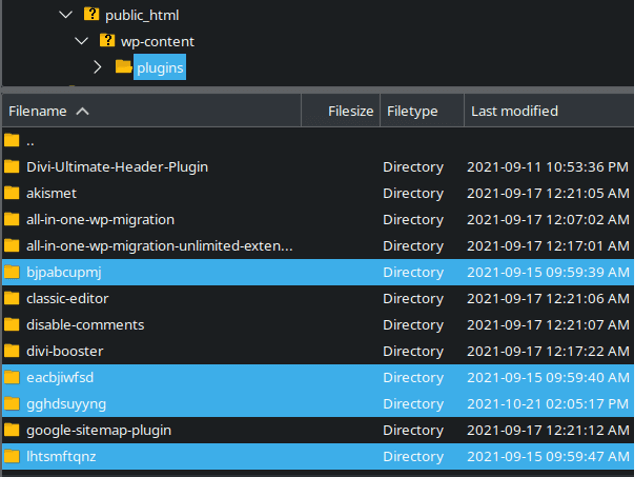
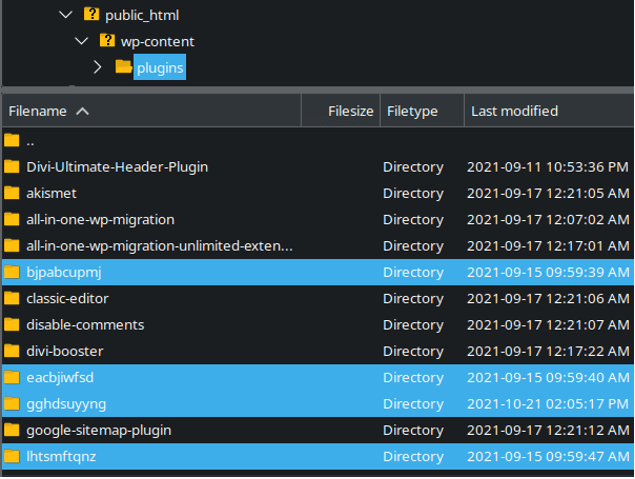
Some examples of malicious plugin filenames include:
- ./wp-content/plugins/bjpabcupmj
- ./wp-content/plugins/eacbjiwfsd
- ./wp-content/plugins/gghdsuyyng
- ./wp-content/plugins/lhtsmftqnz
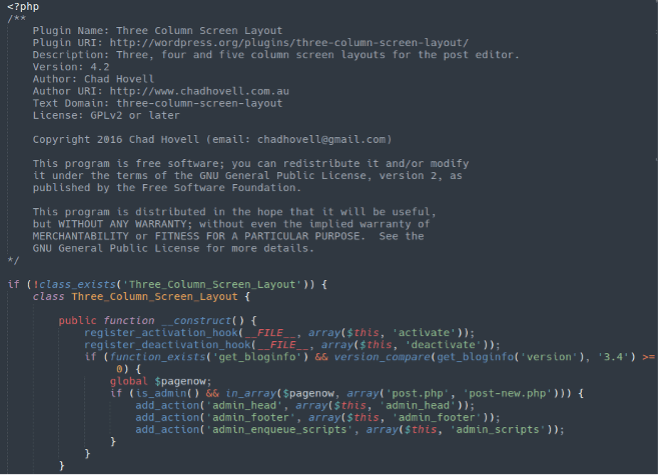
Attackers may even add comments and benign code in an attempt to conceal the malicious contents from a cursory review.
If your CMS suddenly contains new, unfamiliar components, extensions, plugins or themes, remove them and check for malware or other indicators of compromise.
Symlink bombs
If an attacker is able to establish cPanel access and the server doesn’t happen to be using the “symlink protection” feature, symlinks can be used to move laterally through the server environment. The attacker can then exploit the symlink vulnerability to infect as many websites as possible.
If you notice that your website has unrecognizable symlinks to other websites, you may have an infection that needs to be cleaned up.
Symlinks can be sent to the trash using the cPanel file manager without trouble.
Modified login credentials
The AnonymousFox infection is notorious for changing the login credentials of the victim’s websites, preventing them from logging in to their admin panels or editing content on their websites.
In some cases, the primary wp-admin account is renamed to something like [email protected]!UmYvba!0X — essentially the word AnonymousFox with an @sign and the password following afterwards.
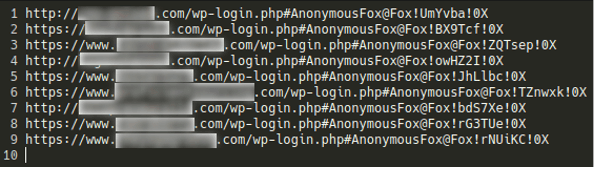
Once the primary admin account has been modified, the hacker then changes the admin passwords for all other affected websites and stores them in the panels.txt file for future reference.
This panels.txt file ends up coming in handy for other AnonymousFox features. For example, when attackers run the FoxAuto tool, they can simply include credentials from this file to quickly backdoor or create new SMTP from the already compromised logins.
So — if you’re suddenly unable to log in to your admin account and password resets are no longer being sent to your admin email address, this should be considered a major red flag.
Malicious server processes
Some AnonymousFox tools create malicious server processes that constantly reinfect files until they are killed off.
Most commonly, the malware chmod’s the ./index.php and ./.htaccess files to 444 to prevent them from being modified. We often find the processes referencing an obscure PHP file in the compromised environment.
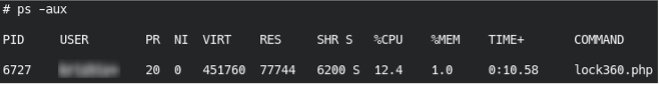
If a number of unknown or suspicious processes are running on your server and they respawn shortly after clearing them, this may be an indication that you’ve been infected by AnonymousFox.
You’ll want to exercise caution when killing off processes. If commands are run as the root user, they can potentially bring down the website or server. This is where assistance from your hosting provider can come in handy.
Once the processes have been successfully removed, you can proceed with removing the malware from any affected files in your environment.
.htaccess malware
AnonymousFox infections commonly include hundreds — or even thousands — of .htaccess files which serve to disrupt the normal function of the website.
This .htaccess malware can be found littered throughout the website environment to deny PHP execution and disrupt access to files — and, depending on the location, can prevent website admins from performing basic updates, post modifications, or even regular maintenance tasks.
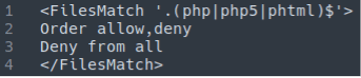
If you’re suddenly unable to edit posts or pages on your website, perform simple tasks, or update themes or plugins on your website, your website may have been infected with the AnonymousFox malware.
You’ll want to check for and remove all of the malicious .htaccess files from your environment, ensuring not to remove your primary .htaccess file at the website root in the process — but, definitely make sure it’s clean.
Malicious email addresses
Once an attacker has access to a compromised environment’s file system, a simple change to the /home/user/.cpanel/contactinfo and /home/user/.contactemail files to update them with their own email address coupled with a password reset on the cPanel login page is enough to establish full administrative control of the cPanel account. This essentially sends the reset password email to the account the attacker set on those files.
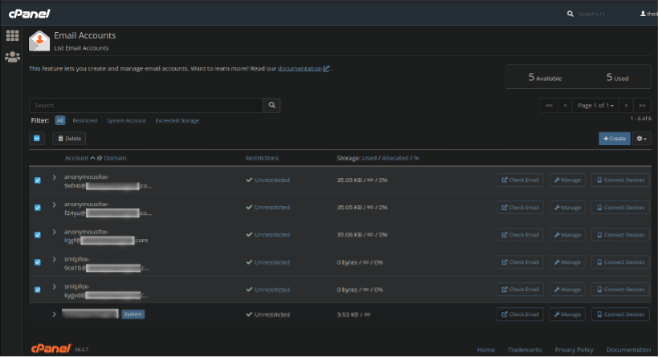
However — there’s another way that hackers are using email addresses in compromised environments.
Once a foothold has been established in cPanel, the AnonymousFox FoxAuto tool can easily create email accounts that can use the standard SMTP to send out emails. These can be sold on the black market and used to distribute spam or phishing for compromised email lists.
If you find new and unfamiliar email accounts in your cPanel account, this is a red flag that your environment could have been compromised and should be investigated as soon as possible.
How to clean up an AnonymousFox hack
According to malware researcher Luke Leal, AnonymousFox is responsible for sending out tens of millions of malicious requests to publicly accessible websites every month — which demonstrates the massive impact of the tool.
Since AnonymousFox offers a wide range of tools for attackers, cleaning up an infection can be a difficult, labor-intensive and daunting task.
There are a number of key items you’ll want to address when investigating and cleaning up an AnonymousFox infection:
- Check access to cPanel / WebHost Manager and reset the contact email.
- Delete unfamiliar or unused plugins, themes, and other extensible components.
- Check for and safely remove unrecognized symlinks, then enable symlink protection if it hasn’t already. (You may need to check with your hosting provider on this matter.)
- Remove suspicious admin accounts in the database, update your usernames and passwords.
- Check for and remove any unrecognizable email accounts.
- Search for and remove bogus .htaccess files from your environment.
- Kill off spawning malicious processes.
- Check for and remove malicious cron jobs.
Always be sure to make a backup of your files and database for making any changes. You may also want to temporarily take your website offline for the remediation process to help troubleshoot the issues.
You can find extensive instructions on how to clean up a hacked WordPress website in our guides, and we’re always available to help clean up a website that’s been infected with AnonymousFox if you need a hand.
How to protect your site against AnonymousFox
If you’ve already been hacked before, you likely already understand the importance of securing and protecting your website and traffic.
But regardless of whether you’re just cleaning up an infection or are simply taking a proactive approach to security, you’ll want to follow these hardening recommendations for your website:
- Secure and restrict access to your admin panels.
- Keep all software up to date with the latest patches — including core CMS, plugins, themes, Apache, PHP, WHM/cPanel, and other extensible components.
- Remove unused software and components to create fewer entry points.
- Use secure passwords and multi-factor authentication.
- Isolate your website to prevent cross-site contamination.
- Create and set up an automatic backup schedule for your website.
- Use a web application firewall to block brute force attacks, virtually patch known vulnerabilities, and mitigate DDoS.