
2022-5-12 16:30:0 Author: tbhaxor.com(查看原文) 阅读量:16 收藏
In this post, you'll learn about the Clair tool, which is used to scan Docker images for vulnerabilities and report them.
Hello World! In my recent post Fixing Misconfiguration using Linter, you have learned how to fix your Dockerfile to build a secure image. Linters are supposed to find the problems in the syntax, not about the contents of the files or changes made in the layers. To solve this issue, the Clair tool is used.
Clair is a static analyzer for finding vulnerabilities in application containers by parsing the images and filesystem layers. This scanning is not done on the container runtime, but on the built images, which means if the running container is compromised and any new vulnerability is added, that will not be detected and reported by the Clair tool.
In the lab, the Clair database is already running which contains all the signatures and vulnerabilities. The Clair server image is provided to you and can be started with the configuration.
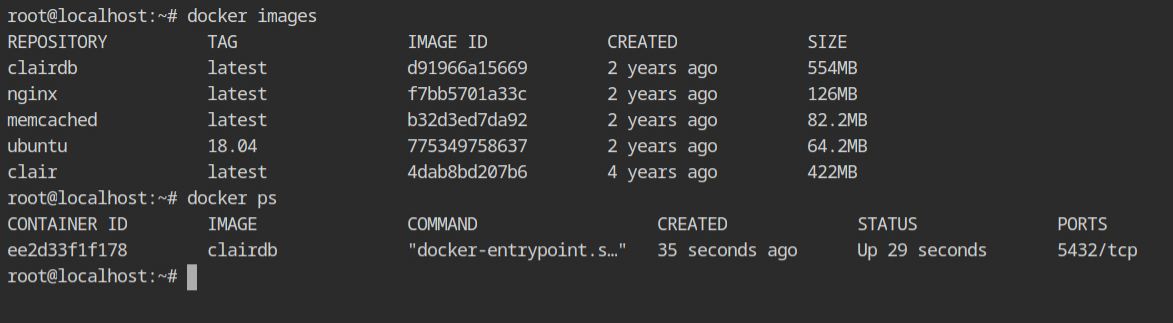
There is a configuration for the Clair service in the clair_config/config.yaml file, where you will see two addresses bind to all the interfaces – Clair server will be hosted on port 6060 and the heath check address will be published on port 6061.
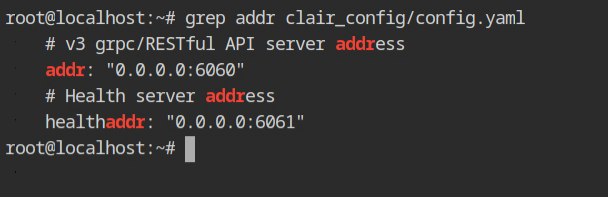
Start the docker container from the clair image with the config in the host file system. I have mounted the config file in /opt/config.yaml, therefore it is required to be mentioned in the -config flag.
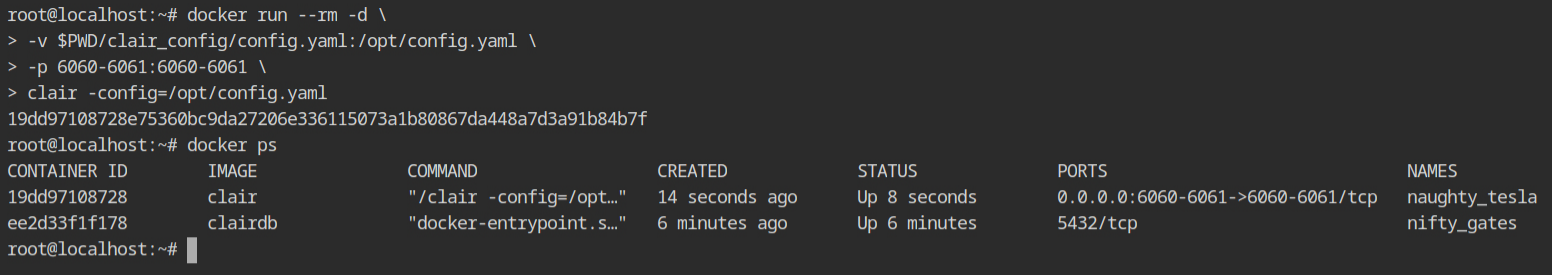
The clair-scanner CLI tool is what you will be interacting with most of the time. It is a client which takes your image as an input and provides it to the server for parsing. This can be installed from arminc/clair-scanner git repository.
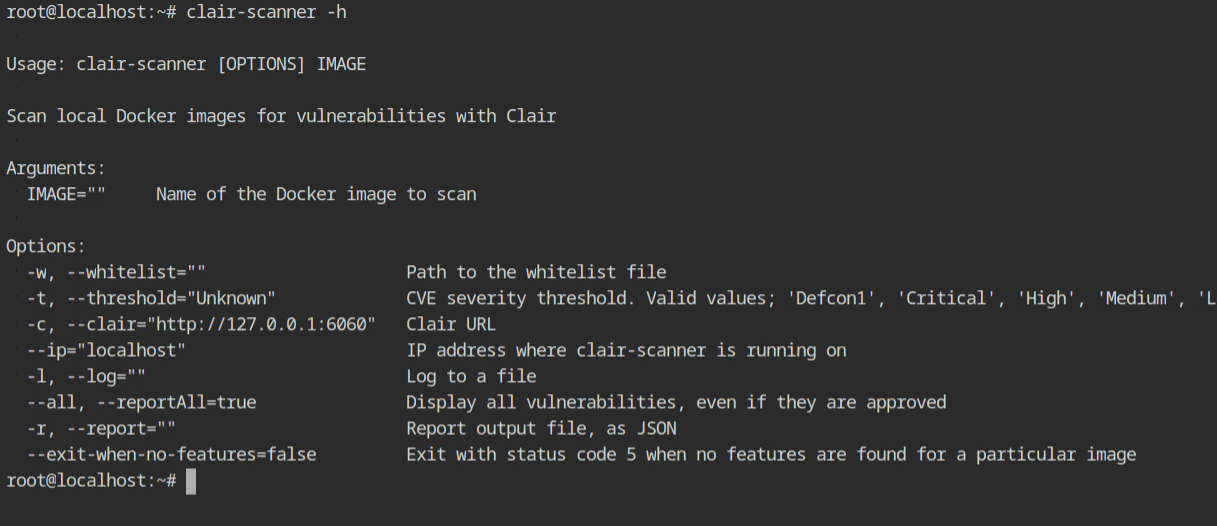
The server runs on a different host and port, so give it to the clair-scanner tool with -c http://localhost:6060, and give the host where clair-scanner is running with --ip 172.17.0.1, which must be the host address of your docker interfaces. Finally, type the name of the image you want to scan.
Here I am scanning the vulnerabilities in the ubuntu image.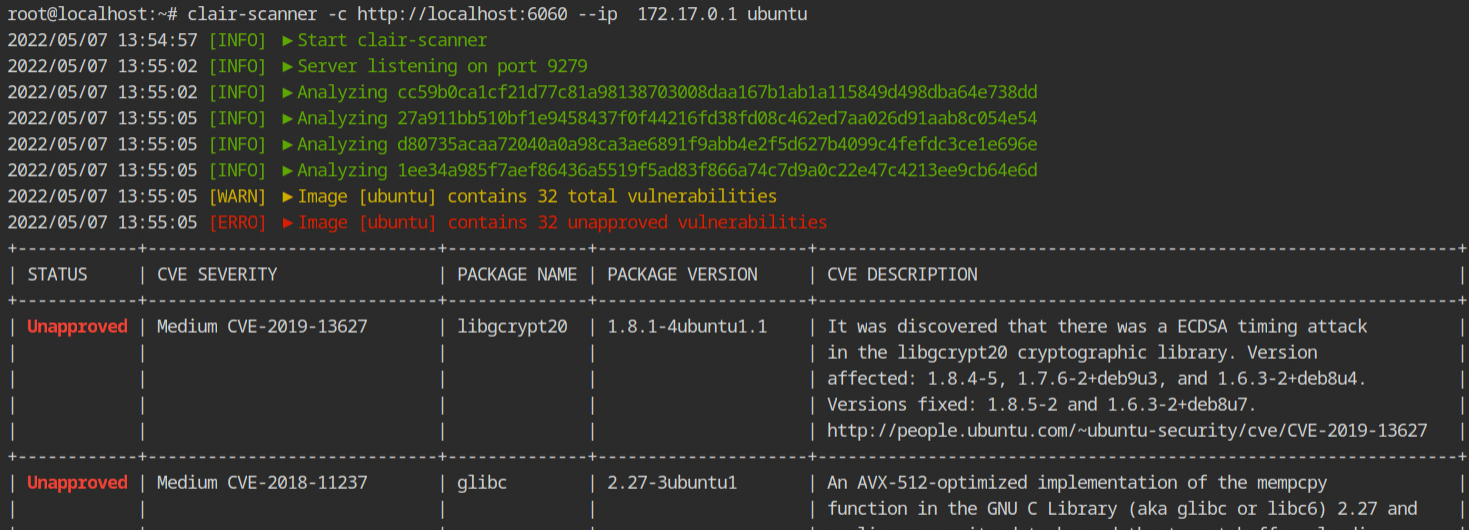
ubuntu imageAs you can see from the output, it is indeed searching for the libraries, programs and configurations that are vulnerable and whose CVEs are public. It will miss all those vulnerabilities that are not in the clair's database.
This is a bonus section, where I will tell how exactly the Clair works. Since clair-scanner is not included in the clair's suite, I will not discuss that.
The clair's architecture can be summarized by the following image.
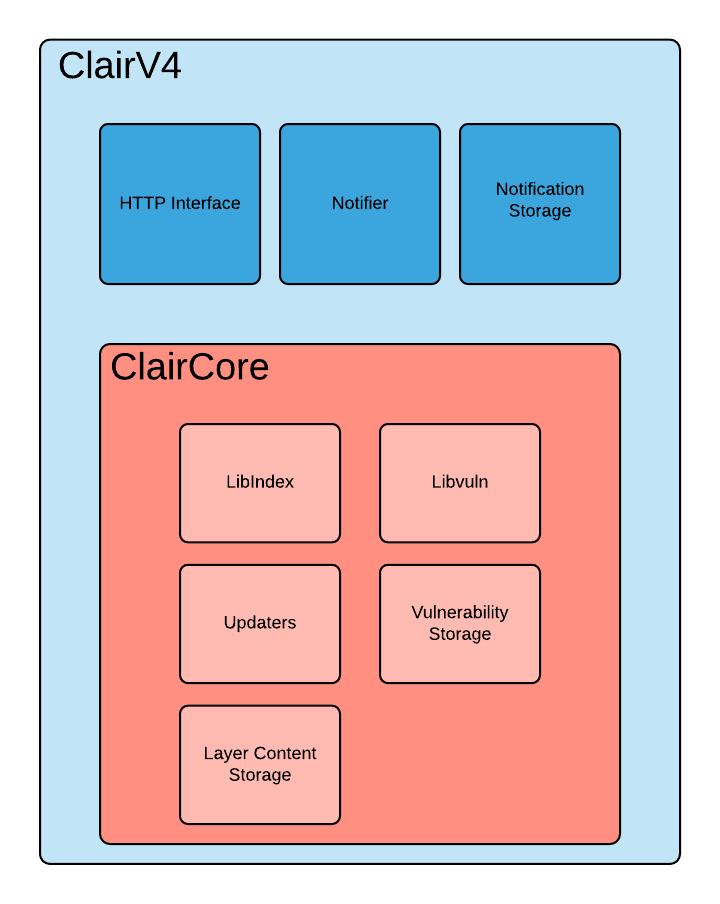
It can be divided into three main modules
- Indexing (in libindex package) is responsible for parsing the image to extract the contents from the layers. This then generates an intermediate report (aka IndexReport) for the next process. Once the layers are indexed, it will be cached in the Layer Content Storage and can be reused in the other images using them as the base layer. This is implemented by the libindex package.
- Matching (in libvuln package) takes the IndexReport from the previous step and performs some queries in the database to find some vulnerability information for that content. This is
- Notifications are then used to identify the user of these vulnerabilities based on their configurations.
Note – Indexing and matching are implemented in the ClairCore.
All these modules are implemented separately in a Golang package, you can run go get .. command to download and use them in your application without using all the modules at once. This could be helpful when you are building a CI pipeline and validating the contents of the image. For more information, check out the Getting Started section in the documentation.
All the vulnerabilities have a Severity index which is mapped with the what CVEs are published. All these will be mapped into the following levels
Unknown
Negligible
Low
Medium
High
Critical- https://github.com/arminc/clair-scanner
- https://www.tbhaxor.com/identify-and-fix-dockerfile-misconfigurations/
- https://github.com/quay/clair
- https://quay.github.io/claircore/what_is.html
- https://quay.github.io/clair/concepts/indexing.html
- https://quay.github.io/claircore/getting_started.html
- https://quay.github.io/claircore/howto/add_dist.html
如有侵权请联系:admin#unsafe.sh