2022-7-1 14:28:58 Author: lab.wallarm.com(查看原文) 阅读量:30 收藏
For tech innovators and security experts, what OWASP Top-10 says or predicts is much attention-worthy as this globally recognized document guide about the hidden and damage-causing security threats.
As the year 2022 has begun, the people willing to learn about the latest security trends and worrisome threats must emphasize on the API security OWASP Top 10 2022. We have done the hard work for this.
Read this article and figure out which cyber threats, as per the Top-10 list of OWASP, are going to stress you out.

OWASP Top 10 – Meaning and Significance
OWASP is a non-profit that came into being to educate software/application developers on which security risks are causing the most harm in the year. By providing detailed information on cyber safety threats of the past and predicting it for the coming months/years. OWASP aims to enhance system security and make virtual resource usage hassle-free.
This open community accepts the contribution of everyone. All their guides, tutorials, and resources are free for use and are accessible to everyone. In a nutshell, OWASP is a platform to learn about web-specific cyber risks at zero cost.
The OWASP Top 10 2022 features the top cyber risks/threats/vulnerabilities from the security perspective on the following basis:
- The frequency
- The intensity of damage caused
- Number of people impacted
- The magnitude of the impact
With AppSec as its main focus, the list is updated every 2 or 3 years. See the timeline summarized below:
- 2003 – Creation
- 2017 – The year of major changes, e.g. 3 categories appended, 4 renamed, and scope was changed for many.
- 2021 – The latest version was released.
Pros and Cons of OWASP Top 10
The list is a mixed bag having pros and cons.
The most common pros are:
- Global acceptance and wide coverage
- Very easy-to-understand and making sense is easier than ever
- The list is community-driven and is based on inputs from real-world professionals who are facing the issues
But, it comes with certain cons as well:
- It’s not certain whether the list talks about the attack or the bypassable implementations. You need to be a cybersecurity master to fully comprehend it.
- As the list is updated after 2-3 years, various latest security risks go unnoticed. Also, this long-duration update makes the data irrelevant.
- It’s not clear why categories are made.
- There is a debate going on about the merger of OWASP Top 10 and the API-specific list.
OWASP Top 10 2021 v/s 2017
Before we talk about the OWASP 2022 AppSec predictions, let’s find out what has changed from 2017 to 2021.
- A01:2017 Injection dropped to 3rd place and became A03:2021 Injection, while cross-site scripting being added to this subset. As per the recent trends, around 94 of 100 apps were spotted with some kind of injection.
- A02:2017 Broken Authentication got the name change and became Identity and Authentication failure. and Featuring CEWs linked with identification failure, this threat has moved down in the 2021 list.
- A03:2017 Sensitive Data Exposure moved up to 2nd place in the 2021 list and went through a name change as well. In 2021, it will become an A02 Cryptographic failure. The core focus now is on the cryptography-related system/transaction/workflow failures that cause known/unknown data leaks or data theft.
- A04:2017 XML External Entities could not make its place in 2021’s list and is integrated into ‘Security Misconfiguration’ (5th place) now.
- A05:2017 Broken Access Control jumped to 1st place in the 2021 list. With 94% of applications impacted by this threat, the jump was justified.
- A06:2017 Security Misconfiguration jumped to 5th place.
- A07:2017 Cross-Site Scripting category got removed and became a part of A03:2021 Injection category.
- A08:2017 Insecure Deserialization category was also removed. In its place, a new category, Software & Data Integrity Failure were added that remained at 8th place.
- A09:2017 is now 6th in thislist. It is named ‘Components With Known Vulnerabilities’.
- A10:2017 Insufficient Logging & Monitoring moved to 10th place.
Read the full report in our previous article – Proposal OWASP Top-10 2021
Other than the above-mentioned changes, OWASP Top 10:2021 list, there were 2 fully new additions:
- Insecure Design (A04:2021) features the security risks happening because of design errors and asks for more usage of practices like highly secured designs, using reference architectures, and threat modeling.
- Server Side Request Forgery or SSRF is in 10th place in the 2021 list. Even though the incident rate of this threat is low, it has the potential to cause serious damage.
Expert’s Take on OWASP Top 10: 2021 List
At Wallarm, there is an extensive and skilled team of web security experts working together to improve security. They took a deep dig on the updated list and figured out certain loopholes.
For instance, Wallarm doesn’t agree to make the “Sensitive Data Exposure” category as a part of “Cryptographic Failures”. These two are entirely different things and merging them doesn’t make sense.
XXE should be a part of Insecure Deserialization rather than of the Misconfigurations.
As the list claims to include 500k data entities while we figured out that there are only 22k entities present on GitHub.
The Data-Driven Predictions For OWASPTop 10 2022
Wallarm conducted a detailed analysis on the efficacy and effectiveness of the OWASP Top 10 2021 list, based on 2.2 million reports collected from 144 sources. Based on the data, we already predicted that the SSRF will be present in the 2021 list and it happened.
This prediction was data-backed as we figured out that:
- SSRF, among the critical-most risks in cybersecurity, was placed at 3rd position.
- Amazon has already figured out its seriousness and has launched a remedial patch for its EC2 meta-data services.
- SSRF has been held responsible for various high-end security risks. For example, a hack on Capital costed more than a billion USD to the company.
- As per the Vulners bulletin data, 900+ bulletins featured the mention of SRF, which was 2.5 times higher than security misconfiguration.
Also, our analysis featured 4.4 times extra data that was used in creating the Top-10 OWASP 2021 list.
The in-use statistical data came from Vulners.com, a highly aggregated database featuring 4+ million bulletins. We use 2,168,521 bulletins to build the 2021 list. The same analysis revealed that security experts and application developers want this list to be updated every year as cyber threats/vulnerabilities are changing like anything.
Maintaining the same level of accuracy and authenticity, we have some expert-backed OWASP Top 10 vulnerabilities 2022.
Special note: We have made the predictions by keeping OWASP Top 10 2017 list as the base.
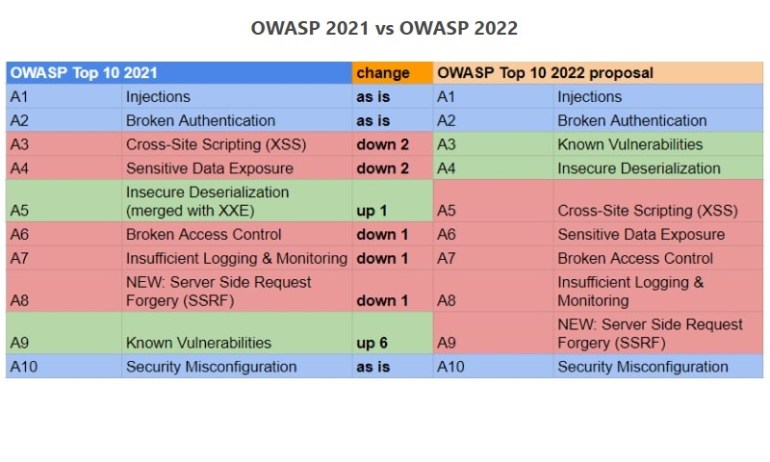
- A1 Injections are likely to remain at the same place and will not go through major changes.
- A2 Broken Authentication will also retain its position and components.
- A3 Sensitive Data Exposure should drop down 3 places and will be at 6th place.
- A4 XML External Entities or XXE will be placed at 8th position as a sub-category of the current A10.
- A5 Broken Access Control will retain its names and included content but the cloud drops down 2 places. In 2022 OWASP Top list, it’s likely to be at 7th place.
- A6 Security Misconfiguration will drop down to 4 places in 2022.
- A7 Cross-Site Scripting will move 2 places up and will be at 5th place in OWASP Top 10 2022 list.
- A8 Insecure Deserialization will move 4 places up and will be given 4th place in the 2022 list.
- A9 Known Vulnerabilities will take a 4 step jump and will be at 3rd place in the 2022 list.
- A10 ‘Insufficient Logging and Monitoring’ should get a promotion from A10 to the 8th position.
An entirely new category, SSRF or Server Side Request Forgery must be added and placed at 9th place in the 2022 list.

Final Say
OWASP Top 10 is a trusted source to know about the upcoming and trending security risks and be ready with remedial strategy ready. However, certain issues like delayed updates and irrelevant categories raise questions on its utility.
At Wallarm, the core focus is on data relevancy and real-time security issues. This is why our 2021 predictions came true. We’re in favor of a yearly update of the list and hence made a few predictions for 2022, mentioned above. Know them in advance, enjoy a better API Security Platform, and be ready to deal with upcoming security hassles.
Watch our webinar
如有侵权请联系:admin#unsafe.sh