平时接触到的 python 项目并不多,对 python 的代码审计更是没有接触,偶然朋友发来了一个漏洞 Flask send_file函数导致的绝对路径遍历 ,感觉打开了新世界的大门,于是就以一个初学者的角度,进行复现分析一下。详情也可以根据 Python : Flask Path Traversal Vulnerability 进行分析学习
from flask import Flaskfrom flask import send_fileapp = Flask(__name__)@app.route('/download')def downloadFile():path = "test.txt"return send_file(path)if __name__ == '__main__':app.run()
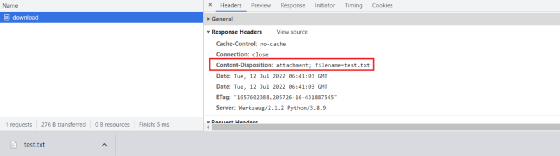
from flask import Flaskfrom flask import send_fileapp = Flask(__name__)@app.route('/download')def downloadFile():path ="test.txt"return send_file(path, as_attachment=True)if__name__=='__main__':app.run()
当下载的文件名是中文时
from flask import Flaskfrom flask import send_fileapp = Flask(__name__)@app.route('/download')def downloadFile():path ="测试.txt"return send_file(path, as_attachment=True)if__name__=='__main__':app.run()
我们在本地构造一个简单的语句进行尝试
>>>import os.path>>> _root_path ="path/to/mySafeStaticDir">>> path_or_file ="/../../../../../../../etc/passwd">>> os.path.join(_root_path,path_or_file)'/../../../../../../../etc/passwd'
from flask import Flask, requestfrom flask import send_fileapp = Flask(__name__)@app.route('/download')def downloadFile():filename = request.args.get('filename')return send_file(filename, as_attachment=True)if__name__=='__main__':app.run()
通过控制 filename 为绝对路径,就实现了目录穿越漏洞
征集原创技术文章中,欢迎投递
投稿邮箱:[email protected]
文章类型:黑客极客技术、信息安全热点安全研究分析等安全相关
通过审核并发布能收获200-800元不等的稿酬。
文章来源: http://mp.weixin.qq.com/s?__biz=MjM5MTYxNjQxOA==&mid=2652889114&idx=1&sn=5148e94127c2bca1bf5093f7a8c079fd&chksm=bd599cd78a2e15c11b645c7396d0976e87fb647106e48e50af6f5a55f2b509c002c89c368201#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh