2022-8-1 14:30:0 Author: securitycafe.ro(查看原文) 阅读量:52 收藏
You might not be familiar with this one, but it is a certification offered by Cyberwarfare Labs that is focusing on exploiting infrastructures that combine multiple cloud environments along with on-premises AD. If you’re thinking into taking this certification or you’re just curios to know more about it, you came to the right place. In this article I’ll present you my experience with the certification along with a few tips.

1. What is the certification about?
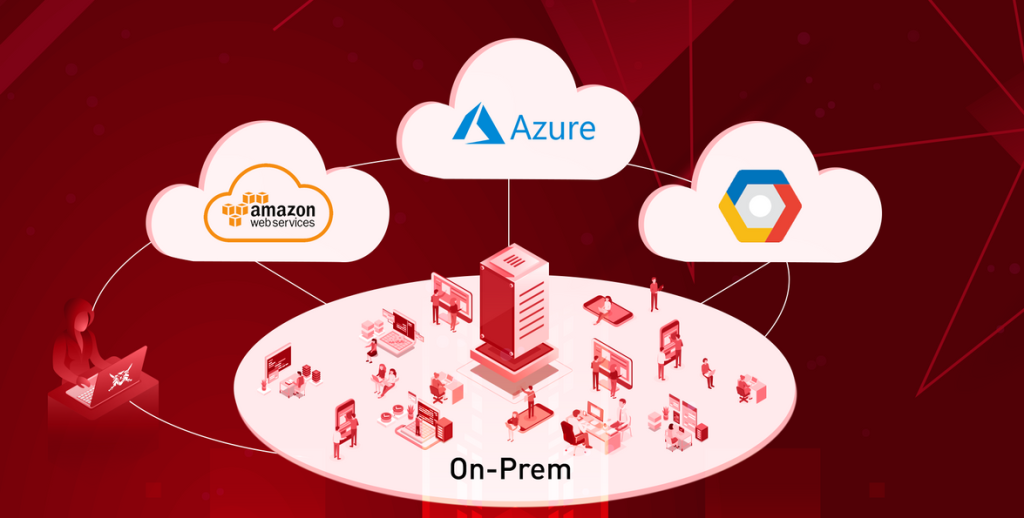
You’ll learn and practice exploitation of various misconfigurations for the next environments: AWS, Azure, GCP and on-premises Active Directory.
Before taking the certification exam, you’ll participate in two training sessions, each session of 6 hours, in which you’ll get an introduction in these technologies and learn (and practice) multiple attack vectors.
For taking the certification, you’ll have to compromise a hybrid multi-cloud infrastructure of a fictive corporation. You’ll receive a form of initial access in one cloud environment and you’ll have to exploit your way up through two other cloud providers, up until you reach the on-premises AD, where the fun continues until you’re domain admin.
We’ll dive in more details on every aspect in the next chapters.
Please check the specific details on the official website as it might become outdated the information presented here.
2. What you get
First off, there are two purchasing options: Community (Free) and Premium (699$). I took the Premium plan because it had included the CHMRTS (Certified Hybrid Multi-cloud Red Team Specialist) certification. This being said, the article is covering only the Premium plan.
Included in this package I got the following:
- Two training sessions, each of 6 hours
- Slides from training sessions
- Terraform scripts for spawning the examples used in training in my own cloud account
- Certificate for completing the training
- 30 day exam for CHMRTS certification, with a free retake
- Support from the staff
3. Other skills required
Even if most the certification is based on cloud, you’ll need some penetration testing skills in order to make it. Nothing too advanced, but the environment is actually build with general vulnerabilities and bad security practices.
You should be familiar with password attacks like credential reuse, lateral movement with SSH tunneling, basic networking knowledge, local privilege escalation, active enumeration, remote code execution, reverse shells and so on.
If you did anything similar to OSCP or compromised some environments with multiple hosts, then it should be enough in terms of prerequisites.
4. The training sessions
The training is fine from an introductory point of view, but is not enough for getting the certification. However, it was nice to see various administrative web platforms that are mostly accessible to organization’s sysadmins and, besides this, you’ll learn some interesting attack vectors.
Before enrolling for this certification, I was familiar with AWS and I studied for a week GCP before starting the exam. Even with my prior knowledge and anything learned from the training sessions, I had to do a lot of research during the exam. Most of the misconfigurations were different than the ones from the training and overall, the training didn’t cover what you needed for the exam, which, of course, makes sense.
Now, I’m not saying that the training is bad. It’s just that you can’t become fluent in 3 cloud providers and AD in 12 hours of learning. My recommendation is to learn about each cloud providers at a basic level (including hacking techniques) before starting the training or, at least, before starting the exam. Same goes for AD.
5. The certification exam
I have to say from the start that was a great experience. One of the things that makes hard to learn cloud offensive security is the fact that the practical available resources online are limited.
I learned multiple new exploitation techniques on each cloud environment and I had the chance to practice them. Most of them were focused on privilege escalation and lateral movement.
I appreciated that, beside the goal of reaching the on-premises AD, there were additional resources that mimicked a real cloud environment. For example, in one of them there was a database with fake credit card data. The information itself didn’t help me in getting closer to the AD network, but it was a nice touch.
Another good aspect was the support from the staff. Along the way I got stuck a few times and I started to wonder if there is anything wrong with the infrastructure. By chatting with one of the trainers I was able to determine if there is really an infrastructure issue that I’m facing.
Talking about issues, there were some, but the staff fixed them quickly. I believe this was the first batch of this training and certification, so the issues I’ve faced might not be there next time.
Was 1 month enough or too much time?
For me was exactly right. I had to balance other things in my day-to-day life and also do the necessary research for the exam, so I liked having this kind of time. I’d say that, if you are experienced in all the technologies involved, you don’t need 1 month. Otherwise, I recommend taking the time to actually learn and practice since you don’t get everyday your hands on a complex cloud environment.
What is the minimum you need to do in order to take the certification?
Well, I don’t know. Remember the additional resources that mimicked a real cloud environment? They are indeed extra and require exploitation, but don’t bring you closer to the AD. So, I don’t know if those resources are balancing something from the AD that you couldn’t do. The best thing is to ask the trainers.
What attests your exam completion?
You’ll have to make a write-up of the exploitation process and send it for review. In my report I made multiple headings with each attack vector I accomplished, where I included relevant commands, screenshots and shortly detailed the process and reasoning behind it.
5. Tips
5.1 Enumeration
First and most important in my opinion is enumeration. What I did was to enumerate absolutely everything I could with my level of access. Only then I was able to properly analyze the environment and identity attack vectors.
For some scenarios, you will not be able to make a plan for getting from the initial access to the next cloud environment. It is required to take one step at a time, redo the enumeration and identify a new attack path.
Enumeration tools will help you in terms of information gathering, but they might not be complete. My advice is to perform manual enumeration and complementary use tools to see if there is something you missed.
5.2 Documentation
You might not know everything and that’s fine. Here comes the vendor’s documentation. Especially when it comes to granular permissions, you should check exactly what actions they grant by reading about them. This will give you some ideas on what you can accomplish with them.
Both GCP and AWS have great documentations with examples, so don’t hesitate to access them. Azure on the other hand might lack the useful information you need, depending on what you are looking for.
5.3 Notes
This is one month journey in 3 cloud environments and one on-premises AD. Take notes and screenshot of each step along the way that should be in the final write-up. It would be hard at the end to go back and perform again each step.
Another thing to consider is that the environment is shared with other students. This means that it exists the possibility that when you go back to take notes of something, the environment will be altered.
5.4 Respect other students
The environment is shared with other students and, depending on your approaches, you might need to move a set of credentials on some compromised VMs. Make sure to revoke any given access once you’re done since other students can’t know that those credentials are from you and they will believe that are intentionally put there by the staff.
5.4 Get sanity checks
If you think something is not working, but it should, make sure to write the trainers. It might be something wrong with the environment or maybe a student broke something. Additionally, if you’re stuck it helps to get a sanity check to make sure that is just something that you missed and everything is working as expected.
6. Final thoughts
I had a great experience with this certification and I learned a lot. Cloud security is a domain that we, the KPMG Romania team, saw rising fast in the last years. Being able to perform a security cloud configuration review or a penetration testing against the 3 biggest cloud providers is surely a skill that comes in hand.
I recommend anyone that want to gain this skill to take the certification as it provides good knowledge on how to identify security misconfigurations and perform attacks against multiple cloud providers.
如有侵权请联系:admin#unsafe.sh