While Windows 11 requires a Trusted Platform Module (TPM), older versions of Windows can do without while still using PIN-based Windows Hello sign-in. We prove that all-digit PINs are a serious security risk on systems without a TPM, and can be broken in a matter of minutes.
Traditionally, Windows accounts are protected with a password, which is used to sign-in to the computer and unlock protected items (such as authentication credentials, browser stored passwords or file system encryption). Resetting the account password, while granting access to the user’s account, would also invalidate such protected credentials, rendering encrypted files inaccessible and effectively blocking access to the user’s stored passwords. Accessing such protected items would require recovering the original password.
Starting with Windows 8, Microsoft introduced a new way to sign-in by using the online credentials to the user’s Microsoft Account. To help secure the user’s account, Microsoft developed an additional authentication system, Windows Hello. In Windows 8, Windows 10 and Windows 11 users are encouraged to set up a PIN and use it instead of a password. Microsoft even goes as far as claiming that the PIN is more secure than a traditional password. In Why a PIN is better than an online password (Windows), Microsoft states the following:
PIN is tied to the device
One important difference between an online password and a Hello PIN is that the PIN is tied to the specific device on which it was set up. That PIN is useless to anyone without that specific hardware.
PIN is backed by hardware
The Hello PIN is backed by a Trusted Platform Module (TPM) chip, which is a secure crypto-processor that is designed to carry out cryptographic operations. The chip includes multiple physical security mechanisms to make it tamper resistant, and malicious software is unable to tamper with the security functions of the TPM. Many modern devices have TPM. Windows 10, on the other hand, has a defect of not linking local passwords to TPM. This is the reason why PINs are considered more secure than local passwords.
This information suggests that the PIN code is always protected by a Trusted Platform Module (TPM) chip, is always tied to the device, and is inherently more secure than the password. These claims are misleading in a way that they are only true if the computer is equipped with a Trusted Platform Module (TPM) module (or emulation), and the TPM is configured to be used in Windows. This is not always the case. Older computers (especially desktop computers) equipped with 7th generation and older Intel Core processors typically do not have a TPM or its emulation, while many newer systems (including many mainboards supporting the 9th generation Intel Core CPUs) come with TPM emulation turned off in UEFI BIOS by default.
While Windows 11 won’t run without a TPM for good reasons, Windows 8 and Windows 10 happily do. These older systems do not report the presence of the TPM to the user when setting up Windows Hello yet still allowing (and even encouraging) using Windows Hello and the PIN code. This in turn is a serious vulnerability that affects users who choose simple all-digit PINs.
When setting up Windows Hello, the system suggests using an all-digit PIN, with alphanumeric PINs being an option. Users commonly choose 4-digit and 6-digit PINs.
To prove this statement, we’ll use the recently updated Elcomsoft System Recovery 8.30. Note that one can only break Windows Hello PIN codes on systems without a TPM.
First, boot the target computer from the USB drive made by Elcomsoft System Recovery. If you have not done it already, here’s how to make the bootable USB drive with Elcomsoft System Recovery: A Bootable Flash Drive to Extract Encrypted Volume Keys, Break Full-Disk Encryption.
Once you boot the computer into Elcomsoft System Recovery and accept the license agreement, you will see the program’s main window. Click SAM – Local User Database:
Then select the target computer’s system drive:
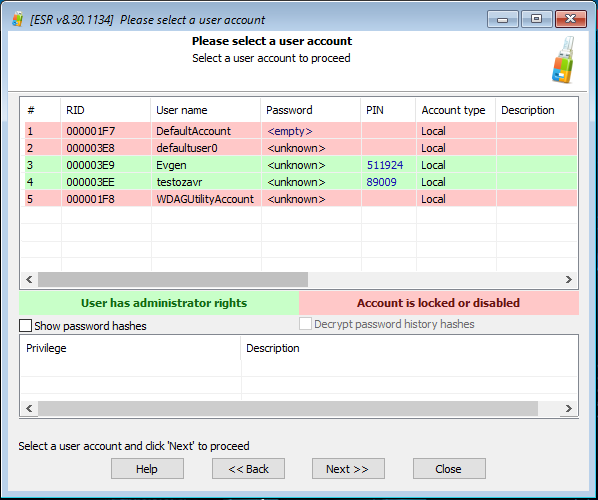
Click Change local user account:
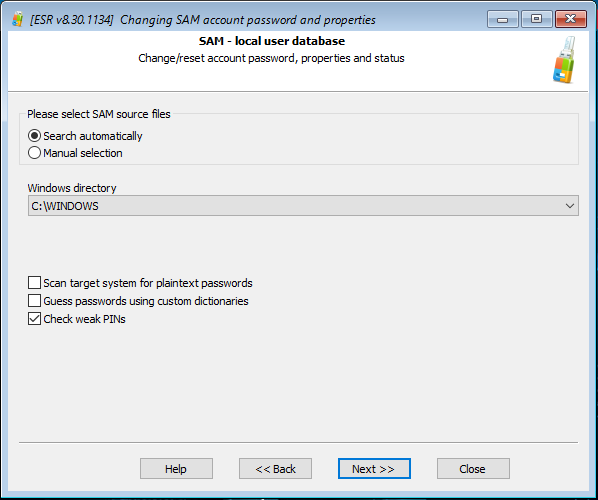
Set up the attack as shown on the screen shot below (the “Check weak PINs” option must be selected):
The tool will then detect user accounts protected with PIN codes, and automatically run a brute-force attack. Once the PINs are discovered, they will be shown in the corresponding window:
Here’s how long it takes us to enumerate all-digit PINs on a 7 year old Intel Core i7-5930K CPU @3.5GHz:
- All 4 digit PINs: 2 seconds
- All 5 digit PINs: 18 seconds
- All 6 digit PINs: 2 minutes
Checking all 4-digit, 5-digit and 6-digit combinations takes up to 2:20 min. If there more than one PIN-enabled account is present, the attacks will be performed separately on all accounts – quite unlike the attack on NTLM hashes, which can be recovered all at once due to shared salt. Interestingly, we discovered that even deleted accounts leave enough traces to launch a PIN attack.
Alphanumeric PIN codes and all-digit PINs that contain more than 6 characters must be attacked offline with Elcomsoft Distributed Password Recovery (update required).
Conclusion
Windows Hello is a great authentication system when used in combination with a TPM. If the computer is not equipped with a TPM chip or firmware-based emulation, or if the TPM is not configured, the use of PIN-based authentication poses a serious security risk if a weak PIN is used.
REFERENCES:
![]()
Elcomsoft Distributed Password Recovery
Build high-performance clusters for breaking passwords faster. Elcomsoft Distributed Password Recovery offers zero-overhead scalability and supports GPU acceleration for faster recovery. Serving forensic experts and government agencies, data recovery services and corporations, Elcomsoft Distributed Password Recovery is here to break the most complex passwords and strong encryption keys within realistic timeframes.
Elcomsoft Distributed Password Recovery official web page & downloads »
![]()
Elcomsoft System Recovery
Reset passwords to local Windows accounts and Microsoft Account and perform a wide range of administrative tasks. Assign administrative privileges to any user account, reset expired passwords or export password hashes for offline recovery, and create forensic disk images. Elcomsoft System Recovery is ready to boot thanks to the licensed Windows PE environment, allowing administrators to access locked computers.
如有侵权请联系:admin#unsafe.sh