2022-8-16 15:55:52 Author: blog.elcomsoft.com(查看原文) 阅读量:22 收藏
Modern versions of Windows have many different types of accounts. Local Windows accounts, Microsoft accounts, and domain accounts feature different types of protection. There is also Windows Hello with PIN codes, which are protected differently from everything else. How secure are these types of passwords, and how can you break them? Read along to find out!
The classic passwords
When attacking Windows account passwords, one has to deal with several different ways the password hashes are produced, protected, and stored.
LM hashes are the oldest types of passwords used since the original version of Windows was released. Microsoft discontinued the use of LM hashes quite some time ago in Windows Vista/Server 2008, but you may still encounter one of those in an older system. LM hashes are stored locally in the SAM database, or the NTDS database on the Domain Controller.
NTLM hashes are the modern replacement of LM. Microsoft still uses the NTLM mechanism to store passwords in modern versions of Windows. These passwords are also stored in the SAM database, or in the NTDS database on the domain controller. Surprisingly, NTLM hashes are even faster to break than LM due to the way the algorithm is implemented.
NTLM hashes protect local Windows accounts as well as the newer types of accounts introduced in Windows 8: the Microsoft Account sign-in. Windows caches the password hash and stores it locally on the computer. This allows users to log in to their computer while using it offline. On another hand, this also allows extracting the cached hash file and running an offline attack to recover the original password. The hashed Microsoft Account passwords are stored locally in the SAM database along with the rest of NTLM hashes. Technically, the locally cached Microsoft Accounts passwords are protected with the same NTLM mechanism as other types of cached credentials, which makes them just as easy and as fast to attack as local Windows passwords.
NTLM hashes are poorly salted. Microsoft uses cryptographic salt to protect LM and NTLM password hashes. However, the same salt is used to protect all LM and all NTLM passwords, which allows attacking all user accounts that present on a certain computer simultaneously. This only changed in Windows Hello PINs.
Windows also has DCC, which stands for Domain Cached Credentials. These are locally stored, cached password hashes that are used to log in to the domain. Domain Cached Credentials are protected differently compared to all other types of credentials, and feature a significantly stronger protection compared to LM and NTLM passwords.
Microsoft Account passwords
In Windows 8, Microsoft introduced a different authentication system, Windows Hello. Users of Windows 8, 10 and Windows 11 are encouraged to set up a PIN and use it instead of their account password. Microsoft claims that the PIN is more secure than a traditional password, which is generally true only if the user’s computer is equipped with a configured TPM module. Without a TPM, the PIN becomes just another password – and a very weak one if the user follows Microsoft’s defaults and sets up a 4-digit or 6-digit PIN. If, however, the user configures an alphanumerical PIN (which, basically, is yet another name for the password), the situation changes.
Windows Hello PIN codes
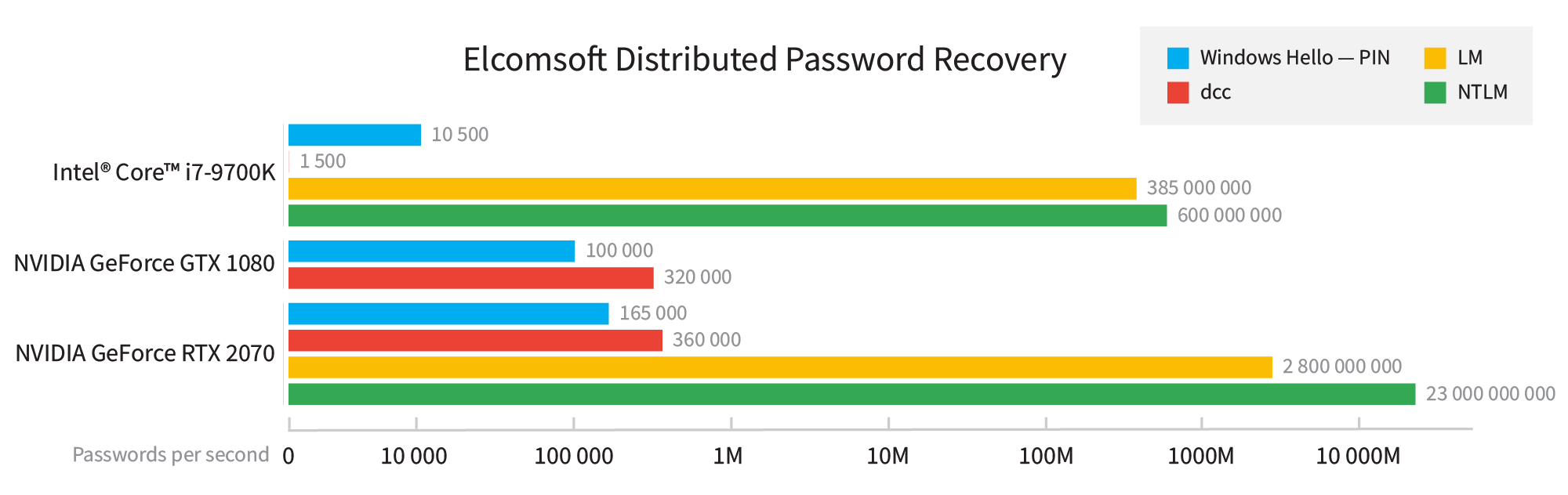
Attacking Windows Hello PIN codes is significantly slower compared to NTLM attacks. According to the table below, the attack on an alphanumerical Windows Hello PIN with Elcomsoft Distributed Password Recovery can be some 50,000 to about 150,000 times slower compared to the attack on the NTLM hash. In addition, Windows Hello PINs are individually salted, which means that all PIN-protected accounts must be attacked in sequence.
What do the numbers mean?
What does a brute force rate of 23 billion passwords per second (for NTLM hashes) really mean? Let us take an 8-character password consisting of a random set of numbers and Latin letters in both cases (95^8 possible combinations). At a rate of 32 billion passwords per second, you will need about 80 hours to break that password. Recovering a 7-digit alphanumerical password will take less than an hour, while shorter or less complex passwords can be cracked in negligible time. A 9-character password, however, will take almost a year to break; accordingly, cracking 9-character alphanumeric passwords will require the use of high-quality dictionaries and smart attacks.
What about the PIN codes, which have a 165 thousand passwords per second rate? At this speed, you’ll need some 1300 years to break the common 8-digit password, or about 13 years for a 7-character password, or about 50 days to break a 6-character alphanumerical password. This means that you’ll already require a dictionary and smart attacks to break even a relatively short 6-character password.
Conclusion
We compared the different types of cached account credentials in Windows. Of those compared, Windows Hello PINs are among the most secure, but only if the user configures a long alphanumerical PIN. Without a TPM, all-digit PIN codes are insecure and can be broken in minutes.
REFERENCES:
![]()
Elcomsoft Distributed Password Recovery
Build high-performance clusters for breaking passwords faster. Elcomsoft Distributed Password Recovery offers zero-overhead scalability and supports GPU acceleration for faster recovery. Serving forensic experts and government agencies, data recovery services and corporations, Elcomsoft Distributed Password Recovery is here to break the most complex passwords and strong encryption keys within realistic timeframes.
Elcomsoft Distributed Password Recovery official web page & downloads »
![]()
Elcomsoft Forensic Disk Decryptor
Elcomsoft Forensic Disk Decryptor offers forensic specialists an easy way to obtain complete real-time access to information stored in popular crypto containers. Supporting desktop and portable versions of BitLocker, FileVault 2, PGP Disk, TrueCrypt and VeraCrypt protection, the tool can decrypt all files and folders stored in crypto containers or mount encrypted volumes as new drive letters for instant, real-time access.
Elcomsoft Forensic Disk Decryptor official web page & downloads »
![]()
Elcomsoft System Recovery
Reset passwords to local Windows accounts and Microsoft Account and perform a wide range of administrative tasks. Assign administrative privileges to any user account, reset expired passwords or export password hashes for offline recovery, and create forensic disk images. Elcomsoft System Recovery is ready to boot thanks to the licensed Windows PE environment, allowing administrators to access locked computers.
如有侵权请联系:admin#unsafe.sh