本文为看雪论坛优秀文章
看雪论坛作者ID:顾言庭
实验目的
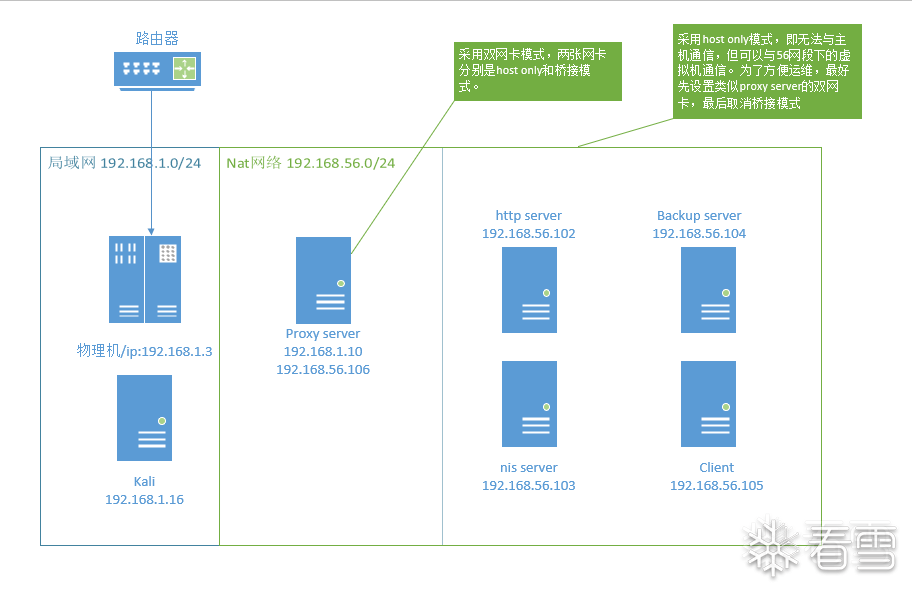
网络拓扑
场景介绍
Nat网络下含有HTTP server、Backup server、nis server、Client主机。此网络模拟的是公司内网环境。
主机介绍
Proxy server:关停一切不必要的端口,伪装ssh端口为1022,需要重点考虑防火墙的设置,检测日志信息,短时间内登录ssh超过一定失败次数则给root用户发邮件提醒,提供squid代理服务。
Http server:架设由https协议保护的门户网站,并提供rsync服务,需要考虑防火墙的设置,设置iptables,仅仅让proxy server访问80、443端口。
Backup server:rsync保存http server的日志信息。
Nis server:为client、backup server这两个服务器提供账号管理服务。
client:配置简易防火墙。
详细配置
特殊配置
# ban 物理机iptables -A INPUT -p TCP -i enp0s8 -s 192.168.56.1 -j DROP# 只允许同网段的ip连接iptables -A INPUT -p TCP -i enp0s8 -s 192.168.56.0/24 -j ACCEPT
Proxy server
# 清空原有配置iptables -Fiptables -Xiptables -Z# input 表默认策略 丢弃iptables -P INPUT DROPiptables -P OUTPUT ACCEPTiptables -P FORWARD ACCEPT# -A 增加规则,-i 指定网卡,-j 指示动作,-m 模组,-p 协议# --dport 目标端口,--sport 源端口#-m state --state RELATED,ESTABLISHED 指定要匹配包的的状态,当前有4种状态可用:INVALID,ESTABLISHED,NEW和RELATED。 INVALID意味着这个包没有已知的流或连接与之关联,也可能是它包含的数据或包头有问题。ESTABLISHED意思是包是完全有效的,而且属于一个已建立的连接,这个连接的两端都已经有数据发送。NEW表示包将要或已经开始建立一个新的连接,或者是这个包和一个还没有在两端都有数据发送的连接有关。RELATED说明包正在建立一个新的连接,这个连接是和一个已建立的连接相关的。iptables -A INPUT -i lo -j ACCEPTiptables -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPTiptables -A INPUT -p TCP -i enp0s3 --dport 111 --sport 1024:65534 -j ACCEPTiptables -A INPUT -p TCP -i enp0s3 --dport 1022 --sport 1024:65534 -j ACCEPTiptables -A INPUT -p TCP -i enp0s3 --dport 3128 --sport 1024:65534 -j ACCEPTiptables-save > /home/dc/iptables.mysettings
ELL=/bin/bashPATH=/sbin:/bin:/usr/sbin:/usr/binMAILTO=root# For details see man 4 crontabs# Example of job definition:# .---------------- minute (0 - 59)# | .------------- hour (0 - 23)# | | .---------- day of month (1 - 31)# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat# | | | | |# * * * * * user-name command to be executed# apply my iptables from file per minute.* * * * * root /sbin/iptables-restore /home/dc/iptables.mysettings
[[email protected] dc]# vim /etc/sysctl.conf[[email protected] dc]# cat /etc/sysctl.conf# sysctl settings are defined through files in# /usr/lib/sysctl.d/, /run/sysctl.d/, and /etc/sysctl.d/.## Vendors settings live in /usr/lib/sysctl.d/.# To override a whole file, create a new file with the same in# /etc/sysctl.d/ and put new settings there. To override# only specific settings, add a file with a lexically later# name in /etc/sysctl.d/ and put new settings there.## For more information, see sysctl.conf(5) and sysctl.d(5).# Turn on syncookies for SYN flood attack protection#net.ipv4.tcp_syncookies = 1# Avoid a smurf attack#net.ipv4.icmp_echo_ignore_broadcasts = 1# Turn on reverse path filtering#net.ipv4.conf.all.rp_filter = 1net.ipv4.conf.default.rp_filter = 1net.ipv4.conf.enp0s8.rp_filter = 1net.ipv4.conf.lo.rp_filter = 1# Turn on and log spoofed, source routed, and redirect packetsnet.ipv4.conf.all.log_martians = 1net.ipv4.conf.default.log_martians = 1net.ipv4.conf.enp0s8.log_martians = 1net.ipv4.conf.lo.log_martians = 1# Make sure no one can alter the routing tables#net.ipv4.conf.all.accept_redirects = 0net.ipv4.conf.default.accept_redirects = 0net.ipv4.conf.enp0s8.accept_redirects = 0net.ipv4.conf.lo.accept_redirects = 0# redirects projectnet.ipv4.conf.all.send_redirects = 0net.ipv4.conf.default.send_redirects = 0net.ipv4.conf.enp0s8.send_redirects = 0net.ipv4.conf.lo.send_redirects = 0[[email protected] dc]# sysctl -p
查看开启的端口发现这一项:
[[email protected] dc]# netstat -tulnptcp6 0 0 ::1:631 :::* LISTEN 1267/cupsd
/etc/ssh/sshd_config:
```Port 1022#AddressFamily any#ListenAddress 0.0.0.0#ListenAddress ::HostKey /etc/ssh/ssh_host_rsa_key#HostKey /etc/ssh/ssh_host_dsa_keyHostKey /etc/ssh/ssh_host_ecdsa_keyHostKey /etc/ssh/ssh_host_ed25519_key# Ciphers and keying#RekeyLimit default none# Logging#SyslogFacility AUTHSyslogFacility AUTHPRIV#LogLevel INFO# Authentication:#LoginGraceTime 2mPermitRootLogin no#StrictModes yes#MaxAuthTries 6#MaxSessions 10```
[[email protected] dc]# semanage port -a -t ssh_port_t -p tcp 1022[[email protected] dc]#[[email protected] dc]# semanage port -l | grep sshssh_port_t tcp 1022, 22
使用kali测试爆破ssh端口
date ; hydra -l dc -P /usr/share/wordlists/fasttrack.txt -v ssh://192.168.1.10:1022 ; date2022年 07月 29日 星期五 22:23:15 CST[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4[ERROR] could not connect to target port 1022: Socket error: Connection reset by peer[ERROR] ssh protocol error[ERROR] could not connect to target port 1022: Socket error: Connection reset by peer[ERROR] ssh protocol error2022年 07月 29日 星期五 22:25:26 CSTcat /usr/share/wordlists/fasttrack.txt | wc -l222>>> (222/(2*60+10))1.7076923076923076
编写自动化工具智能探测是否被爆破ssh密码,立即封禁可疑ip、发邮件给系统管理员。
import os,datetimedef is_this_ip_in_field(ip,field):in_field = Falsefor element in field:if element[0] == ip:in_field = Truereturn in_fieldreturn in_fielddef compose_time_str(date_time_t):month_str = date_time_t.strftime("%b")day_str = date_time_t.strftime("%d").replace('0','')time_str = date_time_t.strftime("%H:%M")date_str = month_str+'-'+day_str+'-'+time_strreturn date_strnow_time = datetime.datetime.now()month_str = now_time.strftime("%b")current_time_1_min_ago = now_time-datetime.timedelta(minutes=1)current_time_2_min_ago = now_time-datetime.timedelta(minutes=2)current_time_3_min_ago = now_time-datetime.timedelta(minutes=3)current_time_1_min_ago_str = compose_time_str(current_time_1_min_ago)current_time_2_min_ago_str = compose_time_str(current_time_2_min_ago)current_time_3_min_ago_str = compose_time_str(current_time_3_min_ago)time_str_list = [current_time_1_min_ago_str,current_time_2_min_ago_str,current_time_3_min_ago_str]#print(time_str_list)cmdline = "lastb | awk \'{printf \"%s-%s-%s %s\\n\",$5,$6,$7,$3}\' | less"a = os.popen(cmdline)login_failed_infomation = a.read().split('\n')suspect_ip_and_attack_time_dict = {}# { time:{ip:number,ip2:number},time2:{ip:number} }for line in login_failed_infomation:if not line.startswith(month_str):continuedetail_time,ip = line.split(' ')#print(detail_time)if detail_time in time_str_list:# has detail time segemnt.if suspect_ip_and_attack_time_dict.has_key(detail_time):time_dict = suspect_ip_and_attack_time_dict[detail_time]if time_dict.has_key(ip):time_dict[ip] += 1else:time_dict[ip] = 1else:# add iptmp_dict = {}tmp_dict[ip] = 1suspect_ip_and_attack_time_dict[detail_time] = tmp_dictreport_message = ""black_list = []message = ""for keys,values in suspect_ip_and_attack_time_dict.items():for ip,failed_times in values.items():if failed_times > 60:black_list.append(ip)format_str = "{} attacked {} times at {}\n"message += format_str.format(ip,failed_times,keys)#print(message)black_list = list(set(black_list))ban_ip_list = []tmp_list = []f = open("black_list.txt","r")for line in f:ban_ip_list.append(line)f.close()for element in black_list:if element not in ban_ip_list:tmp_list.append(element)black_list = tmp_listf = open("black_list.txt","a")#iptables -I INPUT 3 -i enp0s3 -s 192.168.1.1 -j DROPfor ip in black_list:ban_cmd = "iptables -I INPUT 3 -i enp0s3 -s " + ip + " -j DROP"f.write(ip+'\n')os.popen(ban_cmd)f.close()os.popen("iptables-save > /home/dc/iptables.mysettings")if message != "":mail_cmd = "echo \"" + message + "\" | mail -s \"security report\" [email protected]"os.system(mail_cmd)
ELL=/bin/bashPATH=/sbin:/bin:/usr/sbin:/usr/binMAILTO=root# For details see man 4 crontabs# Example of job definition:# .---------------- minute (0 - 59)# | .------------- hour (0 - 23)# | | .---------- day of month (1 - 31)# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat# | | | | |# * * * * * user-name command to be executed# apply my iptables from file per minute.* * * * * root /sbin/iptables-restore /home/dc/iptables.mysettings# detect attack beheviour every 3 minutes.*/3 * * * * root /usr/bin/python /root/detect_ssh_port_hacking.py
date ; hydra -l dc -P /usr/share/nmap/nselib/data/passwords.lst -v ssh://192.168.1.10:1022 ; date
[[email protected] ~]# cat /var/spool/mail/rootFrom [email protected] Thu Aug 4 10:33:02 2022Return-Path: <[email protected]>X-Original-To: [email protected]Delivered-To: [email protected]Received: by localhost.localdomain (Postfix, from userid 0)id 130BE12010FD; Thu, 4 Aug 2022 10:33:02 -0400 (EDT)Date: Thu, 04 Aug 2022 10:33:02 -0400To: [email protected]Subject: security reportUser-Agent: Heirloom mailx 12.5 7/5/10MIME-Version: 1.0Content-Type: text/plain; charset=us-asciiContent-Transfer-Encoding: 7bitMessage-Id: <[email protected]>From: [email protected] (root)192.168.1.3 attacked 142 times at Aug-4-10:30192.168.1.16 attacked 142 times at Aug-4-10:30192.168.1.3 attacked 146 times at Aug-4-10:31192.168.1.16 attacked 96 times at Aug-4-10:31192.168.1.3 attacked 64 times at Aug-4-10:32
┌──(root㉿kali)-[/usr/share/nmap/nselib/data]└─# date ; hydra -l dc -P /usr/share/nmap/nselib/data/passwords.lst -v ssh://192.168.1.10:1022 ; date2022年 08月 04日 星期四 22:32:55 CSTHydra v9.2 (c) 2021 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-08-04 22:32:55[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore[DATA] max 16 tasks per 1 server, overall 16 tasks, 5010 login tries (l:1/p:5010), ~314 tries per task[DATA] attacking ssh://192.168.1.10:1022/[VERBOSE] Resolving addresses ... [VERBOSE] resolving done[INFO] Testing if password authentication is supported by ssh://[email protected]:1022[ERROR] could not connect to ssh://192.168.1.10:1022 - Timeout connecting to 192.168.1.102022年 08月 04日 星期四 22:33:37 CST
[email protected]:/usr/share/nmap/nselib/data$ wc -l /usr/share/nmap/nselib/data/passwords.lst5084 /usr/share/nmap/nselib/data/passwords.lst
[[email protected] ~]# iptables -L --line-numberChain INPUT (policy DROP)num target prot opt source destination1 ACCEPT all -- anywhere anywhere2 ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED3 DROP all -- 192.168.1.16 anywhere4 DROP all -- 192.168.1.3 anywhere5 ACCEPT tcp -- anywhere anywhere tcp spts:1024:65534 dpt:sunrpc6 ACCEPT tcp -- anywhere anywhere tcp spts:1024:65534 dpt:exp27 ACCEPT tcp -- anywhere anywhere tcp spts:1024:65534 dpt:squidChain FORWARD (policy ACCEPT)num target prot opt source destinationChain OUTPUT (policy ACCEPT)num target prot opt source destination[[email protected] ~]#
yum install squidvim /etc/squid/squid.conf:Uncomment and adjust the following to add a disk cache directory.cache_dir ufs /var/spool/squid 100 16 256
[[email protected] ~]# systemctl start squid.service[[email protected] ~]# systemctl enable squid.service
iptables -Fiptables -Xiptables -Ziptables -P INPUT DROPiptables -P OUTPUT ACCEPTiptables -P FORWARD ACCEPTiptables -A INPUT -i lo -j ACCEPTiptables -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPTiptables -A INPUT -p TCP -i enp0s3 --dport 111 --sport 1024:65534 -j ACCEPTiptables -A INPUT -p TCP -i enp0s3 --dport 1022 --sport 1024:65534 -j ACCEPTiptables -A INPUT -p TCP -i enp0s3 --dport 3128 --sport 1024:65534 -j ACCEPTiptables-save > /home/dc/iptables.mysettingsiptables -L --line-number
client
iptables -Fiptables -Xiptables -Ziptables -P INPUT DROPiptables -P OUTPUT ACCEPTiptables -P FORWARD ACCEPTiptables -A INPUT -i lo -j ACCEPTiptables -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPTiptables -A INPUT -p TCP -i enp0s8 -s 192.168.56.1 -j DROPiptables -A INPUT -p TCP -i enp0s8 -s 192.168.56.0/24 -j ACCEPTiptables-save > /home/dc/iptables.mysettings
[[email protected] dc]# vim /etc/crontab[[email protected] dc]# cat /etc/crontabSHELL=/bin/bashPATH=/sbin:/bin:/usr/sbin:/usr/binMAILTO=root# For details see man 4 crontabs# Example of job definition:# .---------------- minute (0 - 59)# | .------------- hour (0 - 23)# | | .---------- day of month (1 - 31)# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat# | | | | |# * * * * * user-name command to be executed* * * * * root /sbin/iptables-restore /home/dc/iptables.mysettings
iptables -Fiptables -Xiptables -Ziptables -P INPUT DROPiptables -P OUTPUT ACCEPTiptables -P FORWARD ACCEPTiptables -A INPUT -i lo -j ACCEPTiptables -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPTiptables -A INPUT -p TCP -i enp0s8 -s 192.168.56.1 -j DROPiptables -A INPUT -p TCP -i enp0s8 -s 192.168.56.106 --dport 80 --sport 1024:65534 -j ACCEPTiptables -A INPUT -p TCP -i enp0s8 -s 192.168.56.106 --dport 443 --sport 1024:65534 -j ACCEPTiptables -A INPUT -p TCP -i enp0s8 --dport 80 -j DROPiptables -A INPUT -p TCP -i enp0s8 --dport 443 -j DROPiptables -A INPUT -p TCP -i enp0s8 --dport 111 --sport 1024:65534 -j ACCEPTiptables -A INPUT -p TCP -i enp0s8 --dport 22 --sport 1024:65534 -j ACCEPTiptables -A INPUT -p TCP -i enp0s8 --dport 631 --sport 1024:65534 -j ACCEPTiptables -A INPUT -p TCP -i enp0s8 --dport 25 --sport 1024:65534 -j ACCEPTiptables -A INPUT -p TCP -i enp0s8 -s 192.168.56.0/24 -j ACCEPT
iptables-save > /root/my_iptables_seetings.rule/usr/sbin/iptables-restore < /root/my_iptables_seetings.rule[[email protected] html]# cat /etc/crontabSHELL=/bin/bashPATH=/sbin:/bin:/usr/sbin:/usr/binMAILTO=root# For details see man 4 crontabs# Example of job definition:# .---------------- minute (0 - 59)# | .------------- hour (0 - 23)# | | .---------- day of month (1 - 31)# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat# | | | | |# * * * * * user-name command to be executed* * * * * root /usr/sbin/iptables-restore < /root/my_iptables_seetings.rule
yum install httpdsystemctl start httpdsystemctl enable httpdsystemctl status httpd
cd /var/www/html/cat index.htmlThis is my first page.
yum install mod_sslsystemctl restart httpd
1.首先做免密登录http服务器的设置:
[[email protected] ~]$ suPassword:[[email protected] dc]# ssh-keygenGenerating public/private rsa key pair.Enter file in which to save the key (/root/.ssh/id_rsa):Created directory '/root/.ssh'.Enter passphrase (empty for no passphrase):Enter same passphrase again:Your identification has been saved in /root/.ssh/id_rsa.Your public key has been saved in /root/.ssh/id_rsa.pub.The key fingerprint is:SHA256:iQiHtrt1CpVCi/9tUepSWVziMnhw/Zk9CASepiHvr2s [email protected]The key's randomart image is:+---[RSA 2048]----+| .+. || .....+ . || * o++o = = || + B.*+.=.= o ||. + *..BS . || . = = || + oo.. || =E=o || ..==o |+----[SHA256]-----+[[email protected] dc]# scp ~/.ssh/id_rsa.pub [email protected]:~The authenticity of host '192.168.56.102 (192.168.56.102)' can't be established.ECDSA key fingerprint is SHA256:fXKVGvaS/isxJ+u6655e5dyTap2YDAgEgdrbs96gcoU.ECDSA key fingerprint is MD5:6d:28:85:28:3a:2d:2e:be:cb:e9:cd:87:ad:9a:ea:22.Are you sure you want to continue connecting (yes/no)? yesWarning: Permanently added '192.168.56.102' (ECDSA) to the list of known hosts.[email protected]'s password:id_rsa.pub 100% 408 489.5KB/s 00:00
[[email protected] ~]# ls -ld id_rsa.pub .ssh/-rw-r--r--. 1 root root 406 Aug 3 01:38 id_rsa.pubdrwx------. 2 root root 25 Aug 1 03:17 .ssh/[[email protected] ~]# cat id_rsa.pub >> ~/.ssh/known_hosts123.txt .bash_profile .cshrc original-ks.cfg .viminfoanaconda-ks.cfg .bashrc id_rsa.pub .rnd .wireshark/.bash_history .cache/ .lesshst .ssh/ .xauthTIyBog.bash_logout .config/ .local/ .tcshrc[[email protected] ~]# cat id_rsa.pub >> ~/.ssh/authorized_keys[[email protected] ~]# chmod 644 ~/.ssh/authorized_keys
[[email protected] ~]$ ssh [email protected]Last login: Sat Jul 30 06:48:47 2022[[email protected] ~]# exitlogoutConnection to 192.168.32.146 closed.
[[email protected] .ssh]# /usr/bin/rsync -av -e ssh [email protected]:/var/www/html /tmpreceiving incremental file listhtml/html/index.htmlsent 47 bytes received 151 bytes 132.00 bytes/sectotal size is 23 speedup is 0.12
[[email protected] ~]# cat /etc/crontabSHELL=/bin/bashPATH=/sbin:/bin:/usr/sbin:/usr/binMAILTO=root# For details see man 4 crontabs# Example of job definition:# .---------------- minute (0 - 59)# | .------------- hour (0 - 23)# | | .---------- day of month (1 - 31)# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat# | | | | |# * * * * * user-name command to be executed* * * * * root /usr/bin/rsync -av -e ssh [email protected]92.168.56.102:/var/www/html /tmp &> /root/rsync_res.txt
/root/rsync_res.txt/var/log/cron
nis server
yum install yp-toolsyum install ypbindyum install ypservyum install rpcbind
nis 域名 vbirdnis整个内部的信任网络为 192.168.56.0/24nis master server 的ip 为 192.168.56.103,主机名为 www.centos.vbirdnis client 的ip为192.168.56.105,主机名为client.centos.vbirdnis client 2 的ip为192.168.56.104,主机名为backup.centos.vbird
[[email protected] ~]# cat /etc/sysconfig/network# Created by anacondaNISDOMAIN=vbirdnisYPSERV_ARGS="-p 1011"
[[email protected] dc]# cat /etc/ypserv.conf## ypserv.conf In this file you can set certain options for the NIS server,# and you can deny or restrict access to certain maps based# on the originating host.## See ypserv.conf(5) for a description of the syntax.## Some options for ypserv. This things are all not needed, if# you have a Linux net.# How many map file handles should be cached ?files: 30# Should we register ypserv with SLP ?# slp: no# After how many seconds we should re-register ypserv with SLP ?# slp_timeout: 3600# xfr requests are only allowed from ports < 1024xfr_check_port: yes# The following, when uncommented, will give you shadow like passwords.# Note that it will not work if you have slave NIS servers in your# network that do not run the same server as you.# Host : Domain : Map : Security## * : * : passwd.byname : port# * : * : passwd.byuid : port# Not everybody should see the shadow passwords, not secure, since# under MSDOG everbody is root and can access ports < 1024 !!!* : * : shadow.byname : port* : * : passwd.adjunct.byname : port# If you comment out the next rule, ypserv and rpc.ypxfrd will# look for YP_SECURE and YP_AUTHDES in the maps. This will make# the security check a little bit slower, but you only have to# change the keys on the master server, not the configuration files# on each NIS server.# If you have maps with YP_SECURE or YP_AUTHDES, you should create# a rule for them above, that's much faster.* : * : * : none
[[email protected] dc]# cat /etc/hosts127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4::1 localhost localhost.localdomain localhost6 localhost6.localdomain6192.168.56.103 www.centos.vbird192.168.56.105 client.centos.vbird192.168.56.104 backup.centos.vbird
[[email protected] dc]# hostnamelocalhost.localdomain[[email protected] dc]# hostnamectl set-hostname www.centos.vbird[[email protected] dc]# hostnamewww.centos.vbird
[[email protected] dc]# cat /etc/sysconfig/yppasswdd# The passwd and shadow files are located under the specified# directory path. rpc.yppasswdd will use these files, not /etc/passwd# and /etc/shadow.#ETCDIR=/etc# This option tells rpc.yppasswdd to use a different source file# instead of /etc/passwd# You can't mix usage of this with ETCDIR#PASSWDFILE=/etc/passwd# This option tells rpc.yppasswdd to use a different source file# instead of /etc/passwd.# You can't mix usage of this with ETCDIR#SHADOWFILE=/etc/shadow# Additional arguments passed to yppasswdYPPASSWDD_ARGS="--port 1012"[[email protected] dc]# systemctl status ypserv.service● ypserv.service - NIS/YP (Network Information Service) ServerLoaded: loaded (/usr/lib/systemd/system/ypserv.service; disabled; vendor preset: disabled)Active: inactive (dead)[[email protected] dc]# systemctl start ypserv.service[[email protected] dc]# systemctl enable ypserv.serviceCreated symlink from /etc/systemd/system/multi-user.target.wants/ypserv.service to /usr/lib/systemd/system/ypserv.service.[[email protected] dc]# systemctl status ypserv.service● ypserv.service - NIS/YP (Network Information Service) ServerLoaded: loaded (/usr/lib/systemd/system/ypserv.service; enabled; vendor preset: disabled)Active: active (running) since Fri 2022-08-05 08:07:36 EDT; 13s agoMain PID: 32494 (ypserv)Status: "Processing requests..."CGroup: /system.slice/ypserv.service└─32494 /usr/sbin/ypserv -f -p 1011Aug 05 08:07:36 www.centos.vbird systemd[1]: Starting NIS/YP (Network Information Service) Server...Aug 05 08:07:36 www.centos.vbird ypserv[32494]: WARNING: no securenets file found!Aug 05 08:07:36 www.centos.vbird systemd[1]: Started NIS/YP (Network Information Service) Server.[[email protected] dc]# systemctl status yppasswdd.service● yppasswdd.service - NIS/YP (Network Information Service) Users Passwords Change ServerLoaded: loaded (/usr/lib/systemd/system/yppasswdd.service; disabled; vendor preset: disabled)Active: inactive (dead)[[email protected] dc]# systemctl start yppasswdd.service[[email protected] dc]# systemctl enable yppasswdd.serviceCreated symlink from /etc/systemd/system/multi-user.target.wants/yppasswdd.service to /usr/lib/systemd/system/yppasswdd.service.[[email protected] dc]# systemctl status yppasswdd.service● yppasswdd.service - NIS/YP (Network Information Service) Users Passwords Change ServerLoaded: loaded (/usr/lib/systemd/system/yppasswdd.service; enabled; vendor preset: disabled)Active: active (running) since Fri 2022-08-05 08:08:06 EDT; 9s agoMain PID: 32611 (rpc.yppasswdd)Status: "Processing requests..."CGroup: /system.slice/yppasswdd.service└─32611 /usr/sbin/rpc.yppasswdd -f --port 1012Aug 05 08:08:06 www.centos.vbird systemd[1]: Starting NIS/YP (Network Information Service) Users Passwords Change Server...Aug 05 08:08:06 www.centos.vbird yppasswdd-pre-setdomain[32606]: Setting NIS domain: 'vbirdnis' (environment variable)Aug 05 08:08:06 www.centos.vbird systemd[1]: Started NIS/YP (Network Information Service) Users Passwords Change Server.
[[email protected] dc]# rpcinfo -p localhostprogram vers proto port service100000 4 tcp 111 portmapper100000 3 tcp 111 portmapper100000 2 tcp 111 portmapper100000 4 udp 111 portmapper100000 3 udp 111 portmapper100000 2 udp 111 portmapper100004 2 udp 1011 ypserv100004 1 udp 1011 ypserv100004 2 tcp 1011 ypserv100004 1 tcp 1011 ypserv100009 1 udp 1012 yppasswdd[[email protected] dc]# rpcinfo -u localhost ypservprogram 100004 version 1 ready and waitingprogram 100004 version 2 ready and waiting
[[email protected] dc]# useradd -u 1001 nisuser1[[email protected] dc]# useradd -u 1002 nisuser2[[email protected] dc]# useradd -u 1003 nisuser3[[email protected] dc]# vim /etc/passwd[[email protected] dc]# echo password | passwd --stdin nisuser1Changing password for user nisuser1.passwd: all authentication tokens updated successfully.[[email protected] dc]# echo password | passwd --stdin nisuser2Changing password for user nisuser2.passwd: all authentication tokens updated successfully.[[email protected] dc]# echo password | passwd --stdin nisuser3Changing password for user nisuser3.passwd: all authentication tokens updated successfully.[[email protected] dc]# /usr/lib64/yp/ypinit -mAt this point, we have to construct a list of the hosts which will run NISservers. www.centos.vbird is in the list of NIS server hosts. Please continue to addthe names for the other hosts, one per line. When you are done with thelist, type a <control D>.next host to add: www.centos.vbirdnext host to add:The current list of NIS servers looks like this:www.centos.vbirdIs this correct? [y/n: y] yWe need a few minutes to build the databases...Building /var/yp/vbirdnis/ypservers...Running /var/yp/Makefile...gmake[1]: Entering directory `/var/yp/vbirdnis'Updating passwd.byname...Updating passwd.byuid...Updating group.byname...Updating group.bygid...Updating hosts.byname...Updating hosts.byaddr...Updating rpc.byname...Updating rpc.bynumber...Updating services.byname...Updating services.byservicename...Updating netid.byname...Updating protocols.bynumber...Updating protocols.byname...Updating mail.aliases...gmake[1]: Leaving directory `/var/yp/vbirdnis'www.centos.vbird has been set up as a NIS master server.Now you can run ypinit -s www.centos.vbird on all slave server.
iptables -Fiptables -Xiptables -Ziptables -P INPUT DROPiptables -P OUTPUT ACCEPTiptables -P FORWARD ACCEPTiptables -A INPUT -i lo -j ACCEPTiptables -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPTiptables -A INPUT -p TCP -i enp0s8 -s 192.168.56.1 -j DROPiptables -A INPUT -p TCP -i enp0s8 -s 192.168.56.0/24 -j ACCEPTiptables -A INPUT -p UDP -i enp0s8 -s 192.168.56.0/24 -j ACCEPT
iptables-save > /root/my_iptables_seetings.rule/usr/sbin/iptables-restore < /root/my_iptables_seetings.rule[[email protected] html]# cat /etc/crontabSHELL=/bin/bashPATH=/sbin:/bin:/usr/sbin:/usr/binMAILTO=root# For details see man 4 crontabs# Example of job definition:# .---------------- minute (0 - 59)# | .------------- hour (0 - 23)# | | .---------- day of month (1 - 31)# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat# | | | | |# * * * * * user-name command to be executed* * * * * root /usr/sbin/iptables-restore < /root/my_iptables_seetings.rule
[[email protected] dc]# yum install ypbindLoaded plugins: fastestmirror, langpacksLoading mirror speeds from cached hostfile* base: mirrors.nju.edu.cn* extras: mirrors.ustc.edu.cn* updates: mirrors.ustc.edu.cnbase | 3.6 kB 00:00:00extras | 2.9 kB 00:00:00updates | 2.9 kB 00:00:00updates/7/x86_64/primary_db | 16 MB 00:00:03Resolving Dependencies--> Running transaction check---> Package ypbind.x86_64 3:1.37.1-9.el7 will be installed--> Processing Dependency: yp-tools for package: 3:ypbind-1.37.1-9.el7.x86_64--> Running transaction check---> Package yp-tools.x86_64 0:2.14-5.el7 will be installed--> Finished Dependency ResolutionDependencies Resolved=======================================================================================Package Arch Version Repository Size=======================================================================================Installing:ypbind x86_64 3:1.37.1-9.el7 base 62 kInstalling for dependencies:yp-tools x86_64 2.14-5.el7 base 79 kTransaction Summary=======================================================================================Install 1 Package (+1 Dependent package)Total download size: 142 kInstalled size: 299 kIs this ok [y/d/N]: yDownloading packages:warning: /var/cache/yum/x86_64/7/base/packages/ypbind-1.37.1-9.el7.x86_64.rpm: Header V3 RSA/SHA256 Signature, key ID f4a80eb5: NOKEYPublic key for ypbind-1.37.1-9.el7.x86_64.rpm is not installed(1/2): ypbind-1.37.1-9.el7.x86_64.rpm | 62 kB 00:00:00(2/2): yp-tools-2.14-5.el7.x86_64.rpm | 79 kB 00:00:00---------------------------------------------------------------------------------------Total 209 kB/s | 142 kB 00:00Retrieving key from file:///etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-7Importing GPG key 0xF4A80EB5:Userid : "CentOS-7 Key (CentOS 7 Official Signing Key) <[email protected]>"Fingerprint: 6341 ab27 53d7 8a78 a7c2 7bb1 24c6 a8a7 f4a8 0eb5Package : centos-release-7-9.2009.0.el7.centos.x86_64 (@anaconda)From : /etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-7Is this ok [y/N]: yRunning transaction checkRunning transaction testTransaction test succeededRunning transactionInstalling : yp-tools-2.14-5.el7.x86_64 1/2Installing : 3:ypbind-1.37.1-9.el7.x86_64 2/2Verifying : 3:ypbind-1.37.1-9.el7.x86_64 1/2Verifying : yp-tools-2.14-5.el7.x86_64 2/2Installed:ypbind.x86_64 3:1.37.1-9.el7Dependency Installed:yp-tools.x86_64 0:2.14-5.el7Complete![[email protected] dc]# yum install yp-toolsLoaded plugins: fastestmirror, langpacksLoading mirror speeds from cached hostfile* base: mirrors.nju.edu.cn* extras: mirrors.ustc.edu.cn* updates: mirrors.ustc.edu.cnPackage yp-tools-2.14-5.el7.x86_64 already installed and latest versionNothing to do
使用ypwhich检查数据库数量。
使用su - nisuser1 切换身份。
参考
https://blog.csdn.net/m0_55754984/article/details/119177156 kali虚拟机安装教程(超详细)
https://www.junmajinlong.com/virtual/network/virtualbox_net/ 理解VirtualBox网络
《鸟哥的linux私房菜》
http://bbs.chinaunix.net/thread-1990048-1-1.html iptables -m state --state RELATED,ESTABLISHED是什么意思
https://blog.csdn.net/MssGuo/article/details/120604176 hostname hostnamectl 显示、设置主机名
https://blog.csdn.net/qq_39914597/article/details/114369086 天翼云修改SSH默认远程端口
看雪ID:顾言庭
https://bbs.pediy.com/user-home-800468.htm
# 往期推荐
球分享
球点赞
球在看
点击“阅读原文”,了解更多!
文章来源: http://mp.weixin.qq.com/s?__biz=MjM5NTc2MDYxMw==&mid=2458464923&idx=2&sn=23855cc68fcc93c5ad43c41656efe14f&chksm=b18e021186f98b0793796c961a042f090bc6adba0b9b8b751ee18b48227e923836303f8fae5d#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh