2022-9-9 23:55:5 Author: derflounder.wordpress.com(查看原文) 阅读量:30 收藏
Home > Mac administration, macOS > Microsoft Defender and tamper protection
Microsoft Defender and tamper protection
One of the features of Microsoft Defender for macOS is tamper protection. This option is designed to prevent Defender or its settings from being removed or changed.
As of posting date, Defender’s tamper protection has three associated topics:
- Disabled: Tamper protection is completely off.
- Audit: Tampering operations are logged, but not blocked.
- Blocked: Tamper protection is on, tampering operations are blocked.
Microsoft has documentation regarding Defender’s tamper protection for macOS, available via the link below:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/tamperprotection-macos
For more details, please see below the jump.
You can manage tamper protection via running commands via the command line, or via management profiles. The commands shown below allow tamper protection to be disabled completely, set to audit mode, or set to full tamper protection where Defender or its settings can’t be removed or changed.
To disable tamper protection, run the following command with root privileges:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
To set tamper protection to audit mode, run the following command with root privileges:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
To set tamper protection to full tamper protection mode, run the following command with root privileges:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
If management via profiles is desired, the example profiles below will set Defender to audit mode or to full tamper protection.
Audit mode:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| <?xml version="1.0" encoding="UTF-8"?> | |
| <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> | |
| <plist version="1"> | |
| <dict> | |
| <key>PayloadUUID</key> | |
| <string>05F0ADFE-8BE0-4C43-BACB-BD0DE6272306</string> | |
| <key>PayloadType</key> | |
| <string>Configuration</string> | |
| <key>PayloadOrganization</key> | |
| <string>Company Name</string> | |
| <key>PayloadIdentifier</key> | |
| <string>com.microsoft.wdav</string> | |
| <key>PayloadDisplayName</key> | |
| <string>Enabling Tamper Protection for Microsoft Defender</string> | |
| <key>PayloadDescription</key> | |
| <string>Microsoft Defender tamper protection configuration settings</string> | |
| <key>PayloadVersion</key> | |
| <integer>1</integer> | |
| <key>PayloadEnabled</key> | |
| <true /> | |
| <key>PayloadRemovalDisallowed</key> | |
| <true /> | |
| <key>PayloadScope</key> | |
| <string>System</string> | |
| <key>PayloadContent</key> | |
| <array> | |
| <dict> | |
| <key>PayloadUUID</key> | |
| <string>977D6F1E-E6C1-4BD2-96C5-D4FFCEAE92BB</string> | |
| <key>PayloadType</key> | |
| <string>com.microsoft.wdav</string> | |
| <key>PayloadOrganization</key> | |
| <string>Microsoft</string> | |
| <key>PayloadIdentifier</key> | |
| <string>com.microsoft.wdav</string> | |
| <key>PayloadDisplayName</key> | |
| <string>Microsoft Defender tamper protection configuration settings</string> | |
| <key>PayloadDescription</key> | |
| <string /> | |
| <key>PayloadVersion</key> | |
| <integer>1</integer> | |
| <key>PayloadEnabled</key> | |
| <true /> | |
| <key>tamperProtection</key> | |
| <dict> | |
| <key>enforcementLevel</key> | |
| <string>audit</string> | |
| </dict> | |
| </dict> | |
| </array> | |
| </dict> | |
| </plist> |
Full tamper protection:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| <?xml version="1.0" encoding="UTF-8"?> | |
| <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> | |
| <plist version="1"> | |
| <dict> | |
| <key>PayloadUUID</key> | |
| <string>E21D6405-FA0F-46D2-84DE-33775762DD7E</string> | |
| <key>PayloadType</key> | |
| <string>Configuration</string> | |
| <key>PayloadOrganization</key> | |
| <string>Company Name</string> | |
| <key>PayloadIdentifier</key> | |
| <string>com.microsoft.wdav</string> | |
| <key>PayloadDisplayName</key> | |
| <string>Enabling Tamper Protection for Microsoft Defender</string> | |
| <key>PayloadDescription</key> | |
| <string>Microsoft Defender tamper protection configuration settings</string> | |
| <key>PayloadVersion</key> | |
| <integer>1</integer> | |
| <key>PayloadEnabled</key> | |
| <true /> | |
| <key>PayloadRemovalDisallowed</key> | |
| <true /> | |
| <key>PayloadScope</key> | |
| <string>System</string> | |
| <key>PayloadContent</key> | |
| <array> | |
| <dict> | |
| <key>PayloadUUID</key> | |
| <string>C3934617-C698-4A88-819D-47377A35D4F3</string> | |
| <key>PayloadType</key> | |
| <string>com.microsoft.wdav</string> | |
| <key>PayloadOrganization</key> | |
| <string>Microsoft</string> | |
| <key>PayloadIdentifier</key> | |
| <string>com.microsoft.wdav</string> | |
| <key>PayloadDisplayName</key> | |
| <string>Microsoft Defender tamper protection configuration settings</string> | |
| <key>PayloadDescription</key> | |
| <string /> | |
| <key>PayloadVersion</key> | |
| <integer>1</integer> | |
| <key>PayloadEnabled</key> | |
| <true /> | |
| <key>tamperProtection</key> | |
| <dict> | |
| <key>enforcementLevel</key> | |
| <string>block</string> | |
| </dict> | |
| </dict> | |
| </array> | |
| </dict> | |
| </plist> |
To check the current Defender configuration, the following command can be run:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
That should return output which looks similar to what’s shown below:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| healthy : true | |
| health_issues : [] | |
| licensed : true | |
| engine_version : "1.1.18900.4" | |
| app_version : "101.78.13" | |
| org_id : "…" | |
| log_level : "info" | |
| machine_guid : "…" | |
| release_ring : "Production" | |
| product_expiration : Feb 05, 2023 at 06:24:12 AM | |
| cloud_enabled : true | |
| cloud_automatic_sample_submission_consent : "safe" | |
| cloud_diagnostic_enabled : false | |
| passive_mode_enabled : true [managed] | |
| real_time_protection_enabled : false [managed] | |
| real_time_protection_available : true | |
| real_time_protection_subsystem : "endpoint_security_extension" | |
| network_events_subsystem : "network_filter_extension" | |
| device_control_enforcement_level : "audit" | |
| tamper_protection : "audit" | |
| automatic_definition_update_enabled : true | |
| definitions_updated : Sept 08, 2022 at 01:57:03 PM | |
| definitions_updated_minutes_ago : 27712166 | |
| definitions_version : "1.355.2589.0" | |
| definitions_status : "update_failed" | |
| edr_early_preview_enabled : "enabled" | |
| edr_device_tags : [] | |
| edr_group_ids : "" | |
| edr_configuration_version : "20.199999.main.2022.09.08.01-10dcd7fedfed0c7a1c3bbf153ba3c9b0d0f36239" | |
| edr_machine_id : "…" | |
| conflicting_applications : [] | |
| network_protection_status : "stopped" | |
| network_protection_enforcement_level : "disabled" | |
| data_loss_prevention_status : "disabled" |
To check specifically for the tamper protection configuration, the following command can be run to check its status:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
You should see the following output depending on the configuration:
Tamper protection disabled:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
Tamper protection set to audit mode:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
Tamper protection set to full tamper protection:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
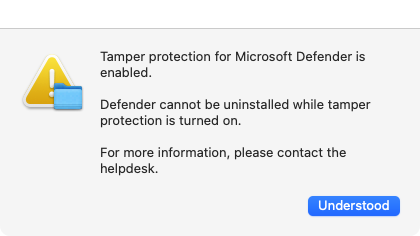
For folks with uninstall scripts for Microsoft Defender, they won’t be able to successfully uninstall Defender or its settings with tamper protection enabled. One way to address this is to add a section at the beginning of the uninstall script which can detect if full tamper protection is enabled and stop the script if it is. An example of this is shown below:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #!/bin/bash | |
| ERROR=0 | |
| # Check to see if Microsoft Defender's tamper protection is enabled. | |
| # | |
| # If tamper protection is turned on, a message will be displayed followed | |
| # by the script exiting before proceeding to the uninstall functions of | |
| # the script. | |
| # Verify that the following tool is installed and executable: | |
| # | |
| # /usr/local/bin/mdatp | |
| if [[ -x "/usr/local/bin/mdatp" ]]; then | |
| # If the mdatp is installed, Defender's Tamper protection's | |
| # status is checked by running the following command: | |
| # | |
| # /usr/local/bin/mdatp" health –field tamper_protection | |
| # | |
| # The output of this command will then be checked against the value stored | |
| # in the tamper_protection_enabled_keyword variable. | |
| # | |
| # There are three possible keywords that can be returned by this command: | |
| # | |
| # disabled – tamper protection is completely off. | |
| # audit – tampering operations are logged, but not blocked. | |
| # blocked – tamper protection is on, tampering operations are blocked. | |
| # | |
| # The tamper_protection_enabled_keyword variable will store the keyword | |
| # currently being used by Defender, in case Microsoft chooses to change | |
| # the keywords in future versions of Defender. | |
| tamper_protection_enabled="$("/usr/local/bin/mdatp" health –field tamper_protection | awk '{print $1}' | tr -d '"')" | |
| tamper_protection_enabled_keyword="audit" | |
| if [[ "$tamper_protection_enabled" == "$tamper_protection_enabled_keyword" ]]; then | |
| /usr/bin/osascript -e 'display dialog "Tamper protection for Microsoft Defender is enabled." & "\n" & "\nDefender cannot be uninstalled while tamper protection is turned on."& "\n" & "\nFor more information, please contact the helpdesk."buttons {"Understood"} default button 1 with icon Caution' | |
| exit "$ERROR" | |
| fi | |
| fi |
If full tamper protection is enabled, this example script will take the following actions:
1. Display the following message using osascript.

2. Exit after displaying the message.
如有侵权请联系:admin#unsafe.sh