
2022-10-6 13:59:32 Author: infosecwriteups.com(查看原文) 阅读量:14 收藏

To fulfill the expectations of growing organizations, new frameworks are being launched into the market, increasing the complexity of current web applications. Even though these frameworks are capable of mitigating attacks such as XSS to a certain extent, there are still design, management, and misconfiguration issues that can be exploited by attackers to gain access to accounts that are hidden behind an authentication page and even escalate their privileges if they are successful.
As a result of these problems, Authentication and Authorization difficulties arise, which present an entirely new class of defects and vulnerabilities, ranging from information leaks to privilege escalation and beyond.

Web application management and design is a complicated topic in today’s world of web-based apps. It is possible to fix a problem and believe it has been resolved, yet this could open the door to an entirely new problem.
Authorization is the process of verifying whether a resource can be accessed by a user or not. It is sometimes also referred to as applying restraints on who can access what resources and actions a user can take based on his profile or role.
Consider a File Server hosted on a military base. There might be various roles depending upon various factors. For the sake of this argument, let’s consider that there are 3 roles, namely, guest, admin, and super admin, and there are files grouped into public, confidential, and top secret groups.
Understandably, the guest user should only have access to the public documents, while the admin and super admin should have access to confidential and top-secret documents, respectively.
When these conditions aren’t enforced properly, it is referred to as Broken Access Control or Broken Authorization.
Due to the frightening consequences that it can have, it becomes extremely important to enforce Authorization Properly.
- Enforce the principle of Least Privileges
It refers to only providing the user the privileges required to complete his/her day-to-day job. This is done to ensure confidentiality. You never know what a person might have in his/her mind at any time. So, he/she should only have access to the information required to complete his job.
Some organizations maintain user roles. In case a user requires additional permissions, temporary access should have to be provided to the user so that he can access the restricted functionality. Once he completes his work, his privileges can be modified to the normal ones.
2. Deny by Default
In other words, unless you explicitly grant access to something, you will always be denied access. It can be thought of as being synonymous with the process of whitelisting a resource. This method ensures that no one will be granted access to a certain resource by default. The resource can only be seen by those who have been authorized access by an administrator.
3. Log everything
The only way to determine whether or not your systems have been compromised after or during the earliest phases of an attack is to examine logs. Logs serve as a kind of window into the history of a company. They provide you with precise information about what occurred and when it occurred.
It is frequently recommended that businesses maintain a separate log server that does not allow creating new log files. This will ensure that even if an attacker has gained access to the network, he will not be able to remove the logs in order to keep his or her identity. All-access to a file should be logged, and the logs should be checked regularly to ensure that no one is abusing the privilege of accessing the file regularly.
4. Ensure that no backup or .git files are on the server.
Web developers frequently publish their applications to GitHub or keep an offline copy of the application on their computer. They frequently mistake forgetting to remove these files from the directory during the deployment process. Any user with access to a directory brute-force tool, such as gobuster, can locate and copy the files in question. Having downloaded all the files, they will be able to examine every commit that has been made. These commits could include sensitive information such as the credentials of critical apps.
Different types of Access Control Concepts
- Mandatory Access Control
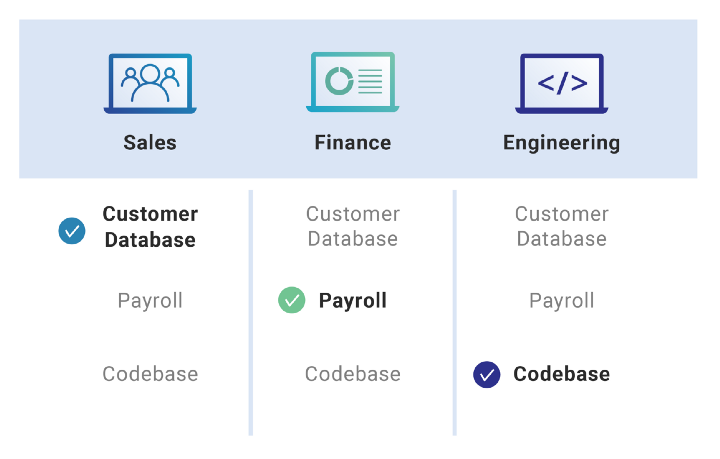
In information security, mandatory access control refers to restricting access to resources based on the sensitivity of the information inside the resource and the authority of the user to access information with that level of sensitivity. For example, if a person only has a public level clearance, that user will only be able to see the documents associated with that level of clearance.
2. Discretionary Access Control

Discretionary access control (DAC) is a type of security access control that gives or restricts object access based on an access policy set by the object’s owner group and/or subjects. It is used to protect sensitive information. The controls of the DAC mechanism are determined by the identification of the user with credentials submitted during authentication, such as a username and password. DACs are discretionary in the sense that the subject (owner) has the ability to transfer authenticated objects or information access to other users at his or her choice. In other words, object access privileges are determined by the object’s owner.
Broken Access Control concerns are so widespread that they have risen from the fourth position in the OWASP’s basket of Top 10 Vulnerabilities in 2017 to the top spot in 2018.
Given the varied responsibilities and user privileges in an application or a corporate or enterprise-level network, it is very easy to become perplexed and entangled in the web of things. Therefore, it is recommended to organize items according to their functions and maintain an appropriate network or application architecture. This will also ensure that whoever takes over as administrator will have fewer difficulties carrying out his or her responsibilities.
From Infosec Writeups: A lot is coming up in the Infosec every day that it’s hard to keep up with. Join our weekly newsletter to get all the latest Infosec trends in the form of 5 articles, 4 Threads, 3 videos, 2 GitHub Repos and tools, and 1 job alert for FREE!
如有侵权请联系:admin#unsafe.sh