Malwarebytes Threat Intelligence builds a monthly picture of ransomware activity by monitoring the information published by ransomware gangs on their Dark Web leak sites. This information represents victims who were successfully attacked but opted not to pay a ransom. This article is also available to download as a Malwarebytes Threat Intelligence report.
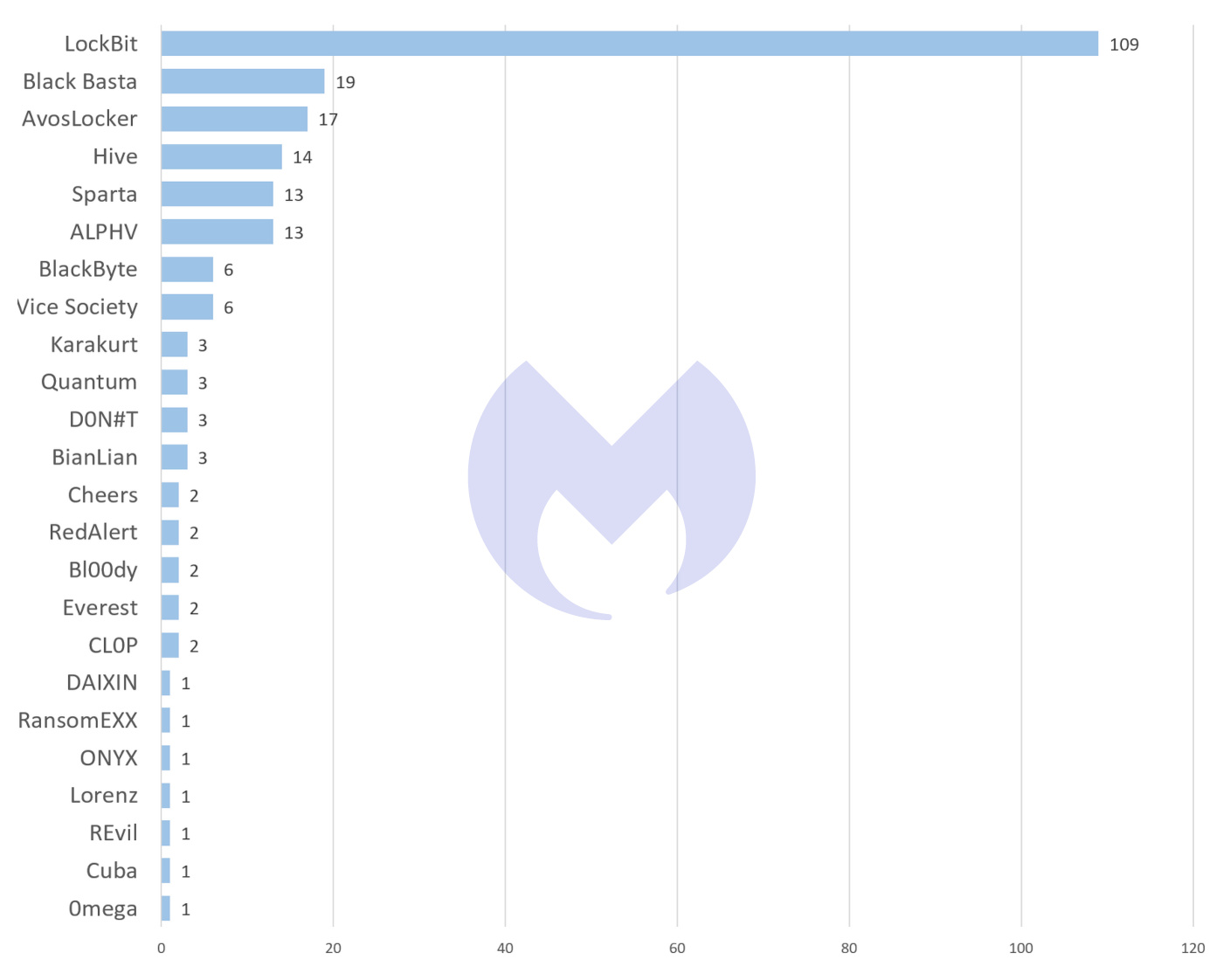
LockBit was the most prevalent ransomware in September, as it has been for all of 2022.

LockBit was involved in almost six times as many attacks as the next most prevalent ransomware, Black Basta, and almost as many attacks as every other variant combined, accounting for 48 percent of known attacks.
While there are a large number of ransomware variants, only a handful accounted for more than two known attacks in September, and only six were involved in more than ten attacks. The gap between LockBit and the its competitors is now huge, which makes us wonder if what we are seeing is consolidation in this criminal space.
It is common for mature software markets to end up with a single dominant player and there is no reason why criminal software markets should be any different. Ransomware-as-a-Service (RaaS) has been effectively "feature complete" for several years, and innovations tend to happen in the tactics used by ransomware operators rather than in the software.

The chart of known ransomware attacks by country for September had a familiar look, with 36 percent of known ransomware attacks happening in the USA, and major European countries featuring prominently, if some way behind.
The presence of Japan and Taiwan in the top 10 is unusual, but only represents a relatively small increase in attacks. A large number of countries receive just a few attacks each month and small, random fluctuations are enough to see them enter and leave our "Other" category.

The chart of attacks by industry sector has a similarly familiar look, with "Services" being the most seriously afflicted sector in September, just as it has been all year.

LockBit 3.0 leak
A few months ago, the LockBit gang released version 3.0 of its ransomware, LockBit 3.0 Black, which was based on source code from BlackMatter ransomware. In September the builder for LockBit 3.0 was leaked by what seems to be a disgruntled developer.
The leak is a double-edged sword. On the one hand, we were happy to get our hands on it, take it for a test drive and learn everything we could. (You can learn more about that in our article A first look at the builder for LockBit 3.0 Black.) On the other hand, anything that makes ransomware even easier to get hold of is likely to make things worse, not better, and we may see new criminal gangs who aren't affiliated with LockBit using it in future. Anyone tempted to try their hand should be warned though—there is no honor among thieves and we fully expect to see fake versions of LockBit's builder that infect would-be criminals running it instead of creating ransomware builds for them.

The BlackMatter source code may have arrived in LockBit's hands courtesy of a developer who "defected" from the ALPHV group (also known as BlackCat), a dangerous ransomware gang that has spent most of 2022 in LockBit's long shadow. ALPHV is a rebrand of the BlackMatter group, which was itself a somewhat botched rebrand of DarkSide, which disappeared following significant law enforcement attention after its attack on the USA's Colonial Pipeline.
Despite a veneer of professionalism, one thing RaaS gangs seem unable to resist for long is the opportunity to boast, grandstand, and fall out. The tiresome gossip and politics of ransomware gangs often takes place on ransomware forums, and last month one of those forums hosted a public spat between ALPHV and LockBit, where the two gangs raked over the BlackMatter rebrand and LockBit's acquisition of its source code.

LockBit is on a bit of a roll with publicity stunts. Having previously grabbed headlines by offering bug bounties, and threatening to add DDoS attacks to its roster, this month it slaked its hunger for publicity by joking that it would give $1,000 to anyone who got a tattoo of the gang's logo.

Incidentally, while the RaaS ecosystem has existed for several years, the gangs within it change regularly and frequently disappear, particularly when they attract the attention of the FBI. We can't help wondering how badly "LockBit is eternal" is going to age.
Speaking of aging badly, it seems that some people either didn't get the joke, or just really, really wanted the money.
— vx-underground (@vxunderground) September 9, 2022Previously, Lockbit ransomware group stated online that they would pay anyone $1,000 if they tattooed the Lockbit ransomware group logo on themselves.
People (more than 1) have done it. pic.twitter.com/PPTtt3ze6g
Off the beaten track
Two new groups emerged in September, and another did something a bit unusual.
FARGO (also known as TargetCompany) has been around since February but made headlines in September by targeting Microsoft SQL servers directly. Files are stolen and encrypted, and leaks are conducted via Telegram rather than through a Dark Web leak site like most RaaS.
The two newcomers, Sparta and Royal, are data leak gangs—groups that don't encrypt data but simply steal it and threaten to leak it. This is no surprise—last month we conjectured that data leakage might be the future of ransomware.