2022-10-10 19:44:36 Author: www.forcepoint.com(查看原文) 阅读量:24 收藏
As the nation’s cyber defense agency, the Cybersecurity and Infrastructure Security Agency (CISA) leads the national effort to understand, manage, and reduce risk to the digital and physical infrastructure Americans rely on every hour of every day. CISA faces a tough job of working across federal agencies to try to identify all vulnerabilities across federal civilian networks as well as our nation’s critical infrastructure.
In an effort to improve our nation’s cybersecurity posture, Cybersecurity and Infrastructure Security Agency recently issued Binding Operational Directive (BOD) 23-01, Improving Asset Visibility and Vulnerability Detection on Federal Networks, directing agencies to improve accounting for what resides on their networks. While this is mandated for federal civilian agencies, CISA also recommends that private business and state, local, tribal and territorial (SLTT) pay attention to this and prioritize implementation of robust asset and vulnerability management programs.
CISA states the directive supports many other mandates and guidance that has previously been established, including the Executive Order 14028 on Improving the Nation’s Cybersecurity (specifically Sec. 7: Improving Detection of Cybersecurity Vulnerabilities and Incidents on Federal Government Networks), and provides additional clarity in achieving policies set forth in previous OMB Memos, including M-21-02, M-22-05, and M-22-09. Compliance with this Directive also supports BOD 22-01, Managing Unacceptable Risk Vulnerabilities in Federal Enterprise, as it will enable agencies to enhance the management of known exploited vulnerabilities that can be detected using automated tools.
CISA Director Jen Easterly said:
Threat actors continue to target our nation’s critical infrastructure and government networks to exploit weaknesses within unknown, unprotected, or under-protected assets,”
“Knowing what’s on your network is the first step for any organization to reduce risk. While this Directive applies to federal civilian agencies, we urge all organizations to adopt the guidance in this directive to gain a complete understanding of vulnerabilities that may exist on their networks. We all have a role to play in building a more cyber resilient nation.”
Plainly stated, we cannot protect what we don’t know we have. Across government devices running out of date or otherwise unsupported and highly vulnerable operating systems tend to fall in the category of devices that are not accounted for, many of which at the same time are still serving useful or critical roles within agencies. Unaccounted for devices on the network represent risk and a threat surface that hasn’t meet account for or otherwise mitigated. The same is true for data and this will need to be addressed as well.
DHS is taking an important step in making visibility a priority as part of CDM phase 1. During the asset discovery phase of CDM, integrators generally found 30%-100% more IT assets running on the network than were tracked in agency inventories, and sometimes included long since depreciated systems running not just Windows XP, boy also Windows NT 4.0 and Windows 2000. Often these inventories did not cover operations technology such as HVAC, PACS, surveillance systems, etc that are also vulnerable because that often connected to IT networks.
This directive requires all Federal Civilian Executive Branch (FCEB) agencies to identify assets and vulnerabilities on their networks and provide data to CISA on defined intervals. It applies to any FCEB unclassified federal information system, including any federal information system used or operated by another entity on behalf of an agency, that collects, processes, stores, transmits, disseminates, or otherwise maintains agency information, including all servers and workstations, virtual machines, routers and switches, firewalls, network appliances, and network printers — whether in on-premises, roaming, and cloud operated deployment models.
The mandate sets a deadline of April 2, 2023, by which date affected agencies must perform automated asset discovery every 7 days and report on vulnerabilities discovered on all assets at least every 14 days and report the detected vulnerabilities info the CDM Agency Dashboard within 72 hours of discovery. By this date, agencies must also establish capabilities to produce this same data within 7 days of any request made by CISA. Agencies must also update their CDM Dashboard reporting capabilities to be able to report the specifics of vulnerabilities detected for CISA analysts.
This improved agency reporting will enable CISA to provide better support information sharing of vulnerabilities happening across civilian federal networks. This helps our nation to understand the threats and take steps toward improving our national security.
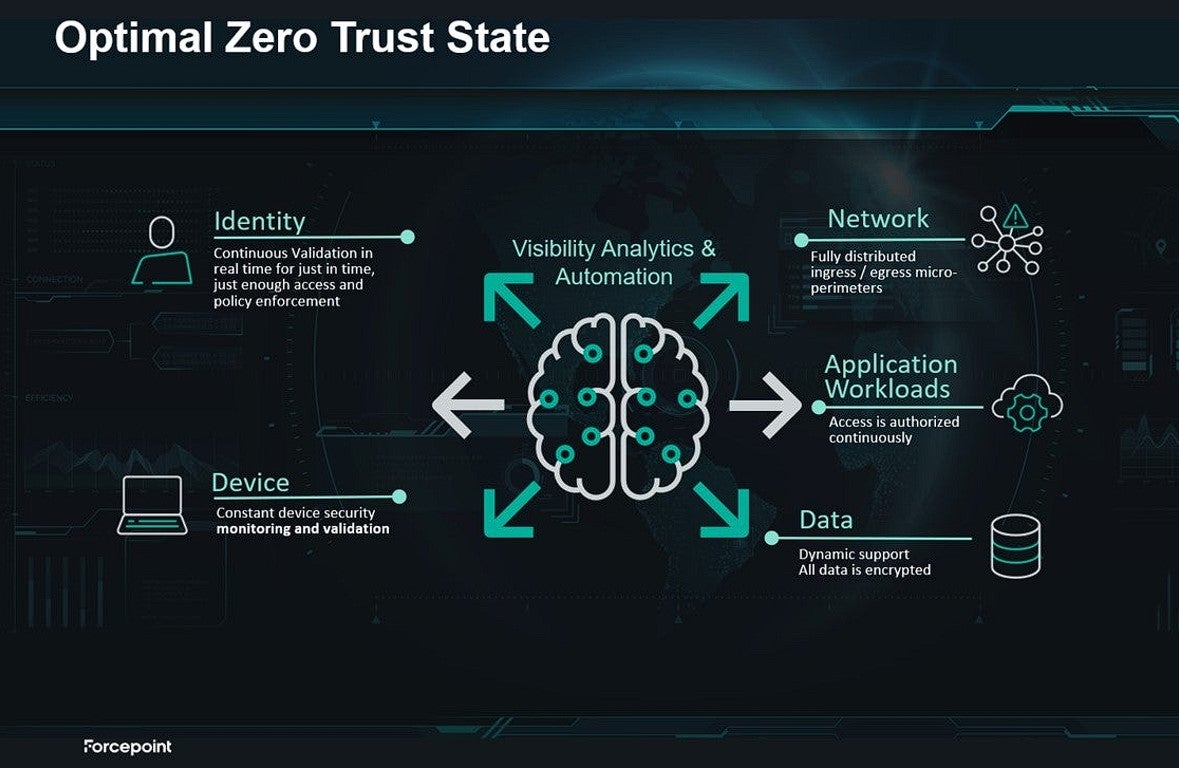
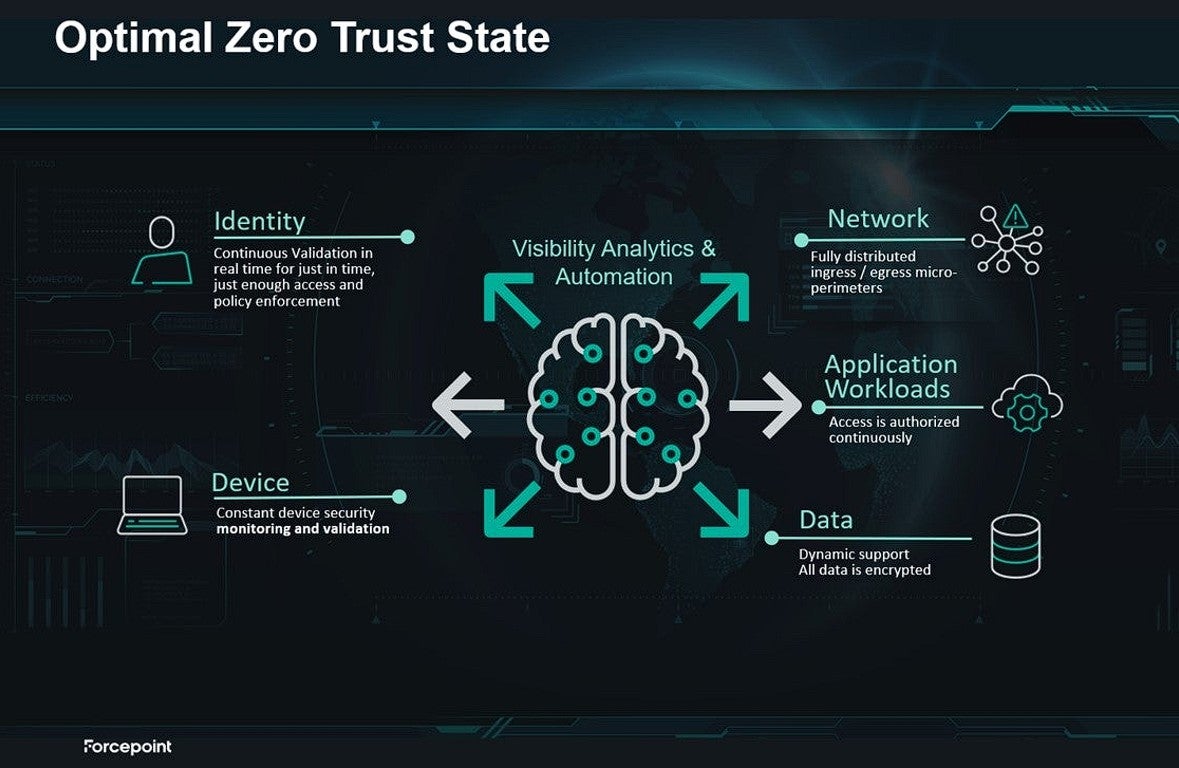
Better understanding and identifying vulnerabilities is only one milestone agencies must take on the road to adopting an optimal Zero Trust security ecosystem. In an optimal state, agencies must adopt more automated and adaptive security and visibility is just the start. Agencies have additional deadline to meet Federal Zero Trust progress goals by 2024 and automation across their ecosystem is an essential component to Zero Trust success. Visibility without a plan for automation is not enough. Agencies must think about the end state they are progressing toward for Zero Trust and ensure that tools and technologies they are adopting today are enabling future Zero Trust success.
Forcepoint Zero Trust Solutions
Forcepoint Zero Trust solutions bring together data, network, cloud and user protection with Zero Trust control to empower agencies to use data where and how your people need it safely. Our mission is to simplify security and protect data wherever it resides. Integrating with your existing security, Forcepoint leverages real-time knowledge of who and what is on your network what they can access, ensuring data on the network is safe and automatically adapting policies to control the risk of individual accounts. This enables Federal leaders implementing Zero Trust to go beyond compliance to achieve centralized visibility, meaningful access controls, and continuous monitoring.
Want to learn more? Schedule a demo today.

Jill Bradshaw
Jill Bradshaw is a Senior Product Marketing Manager with Forcepoint’s Global Government & Critical Infrastructure team. She has more than 15 years of experience in technology industry with focus on security and networks, the majority of that time focusing on solutions for global government...
如有侵权请联系:admin#unsafe.sh